SAE Technical Papers
Cutting-edge & historical research articles for both industry & educational use.
Supporting the automotive, aerospace, and commercial vehicle sectors, SAE Technical Papers provide professionals and students with the latest advances in mobility research.
SAE Technical Papers help guide engineers through their project challenges and establish leadership in a competitive landscape. Reference current and historical research to define best practices and strategies. From combustions processes to simulation & modeling to test procedures, Technical Papers contain in-depth test results, comparative studies, and methodologies on a variety of topics. SAE's Technical Papers are all peer-reviewed by leading industry experts to ensure high quality and dependable information.
Powerful, industry-leading data made available with a range of custom pricing options.
Contact Sales

Research Breakdown
80,000+ Automotive
19,400+ Aerospace
7,900+ Commercial Vehicle
Featured Papers
Additional resources.
Technical Paper Subscriptions
Technical Papers - Historical Back Files
MOBILUS Techselect
Cutting-Edge Articles from AEROTECH
Showcase Your Expertise & Become an Author
Grow your profile and gain citations. Submit your technical research today. SAE accepts technical papers for presentation at SAE conferences, as well as written-only non-event papers.
SAE Event Papers
SAE Non-Event Papers
Support Your Team with Technical Research
Access subscriptions via sae mobilus® technical resource platform, contact our sales team for our subscription options..
Tips for Writing Technical Papers
Jennifer widom , january 2006, running example, paper title, the abstract, the introduction, related work, performance experiments, the conclusions, future work, the acknowledgements, grammar and small-scale presentation issues, versions and distribution.

is Mainsite

- Search all IEEE websites
- Mission and vision
- IEEE at a glance
- IEEE Strategic Plan
- Organization of IEEE
- Diversity, Equity, & Inclusion
- Organizational Ethics
- Annual Report
- History of IEEE
- Volunteer resources
- IEEE Corporate Awards Program
- Financials and Statistics
- IEEE Future Directions
- IEEE for Industry (Corporations, Government, Individuals)
IEEE Climate Change
- Humanitarian and Philanthropic Opportunities
- Select an option
- Get the latest news
- Access volunteer resources (Code of Ethics, financial forms, tools and templates, and more)
- Find IEEE locations
- Get help from the IEEE Support Center
- Recover your IEEE Account username and password
- Learn about the IEEE Awards program and submit nomination
- View IEEE's organizational structure and leadership
- Apply for jobs at IEEE
- See the history of IEEE
- Learn more about Diversity, Equity & Inclusion at IEEE
- Join an IEEE Society
- Renew your membership
- Member benefits
- IEEE Contact Center
- Connect locally
- Memberships and Subscriptions Catalog
- Member insurance and discounts
- Member Grade Elevation
- Get your company engaged
- Access your Account
- Learn about membership dues
- Learn about Women in Engineering (WIE)
- Access IEEE member email
- Find information on IEEE Fellows
- Access the IEEE member directory
- Learn about the Member-Get-a-Member program
- Learn about IEEE Potentials magazine
- Learn about Student membership
- Affinity groups
- IEEE Societies
- Technical Councils
- Technical Communities
- Geographic Activities
- Working groups
- IEEE Regions
- IEEE Collabratec®
- IEEE Resource Centers
IEEE DataPort
- See the IEEE Regions
- View the MGA Operations Manual
- Find information on IEEE Technical Activities
- Get IEEE Chapter resources
- Find IEEE Sections, Chapters, Student Branches, and other communities
- Learn how to create an IEEE Student Chapter
- Upcoming conferences
- IEEE Meetings, Conferences & Events (MCE)
- IEEE Conference Application
- IEEE Conference Organizer Education Program
- See benefits of authoring a conference paper
- Search for 2025 conferences
- Search for 2024 conferences
- Find conference organizer resources
- Register a conference
- Publish conference papers
- Manage conference finances
- Learn about IEEE Meetings, Conferences & Events (MCE)
- Visit the IEEE SA site
- Become a member of the IEEE SA
- Find information on the IEEE Registration Authority
- Obtain a MAC, OUI, or Ethernet address
- Access the IEEE 802.11™ WLAN standard
- Purchase standards
- Get free select IEEE standards
- Purchase standards subscriptions on IEEE Xplore®
- Get involved with standards development
- Find a working group
- Find information on IEEE 802.11™
- Access the National Electrical Safety Code® (NESC®)
- Find MAC, OUI, and Ethernet addresses from Registration Authority (regauth)
- Get free IEEE standards
- Learn more about the IEEE Standards Association
- View Software and Systems Engineering Standards
- IEEE Xplore® Digital Library
- Subscription options
- IEEE Spectrum
- The Institute
Proceedings of the IEEE
- IEEE Access®
- Author resources
- Get an IEEE Xplore Digital Library trial for IEEE members
- Review impact factors of IEEE journals
- Request access to the IEEE Thesaurus and Taxonomy
- Access the IEEE copyright form
- Find article templates in Word and LaTeX formats
- Get author education resources
- Visit the IEEE Xplore digital library
- Find Author Digital Tools for IEEE paper submission
- Review the IEEE plagiarism policy
- Get information about all stages of publishing with IEEE
- IEEE Learning Network (ILN)
- IEEE Credentialing Program
- Pre-university
- IEEE-Eta Kappa Nu
- Accreditation
- Access continuing education courses on the IEEE Learning Network
- Find STEM education resources on TryEngineering.org
- Learn about the TryEngineering Summer Institute for high school students
- Explore university education program resources
- Access pre-university STEM education resources
- Learn about IEEE certificates and how to offer them
- Find information about the IEEE-Eta Kappa Nu honor society
- Learn about resources for final-year engineering projects
- Access career resources
Publications
Ieee provides a wide range of quality publications that make the exchange of technical knowledge and information possible among technology professionals..
Expand All | Collapse All
- > Get an IEEE Xplore Digital Library trial for IEEE members
- > Review impact factors of IEEE journals
- > Access the IEEE thesaurus and taxonomy
- > Find article templates in Word and LaTeX formats
- > Get author education resources
- > Visit the IEEE Xplore Digital Library
- > Learn more about IEEE author tools
- > Review the IEEE plagiarism policy
- > Get information about all stages of publishing with IEEE

Why choose IEEE publications?
IEEE publishes the leading journals, transactions, letters, and magazines in electrical engineering, computing, biotechnology, telecommunications, power and energy, and dozens of other technologies.
In addition, IEEE publishes more than 1,800 leading-edge conference proceedings every year, which are recognized by academia and industry worldwide as the most vital collection of consolidated published papers in electrical engineering, computer science, and related fields.
Spotlight on IEEE publications
Ieee xplore ®.

- About IEEE Xplore
- Visit the IEEE Xplore Digital Library
- See how to purchase articles and standards
- Find support and training
- Browse popular content
- Sign up for a free trial
IEEE Spectrum Magazine

- Visit the IEEE Spectrum website
- Visit the Institute for IEEE member news
IEEE Access

- Visit IEEE Access

- See recent issues
Benefits of publishing
Authors: why publish with ieee.

- PSPB Accomplishments in 2023 (PDF, 228 KB)
- IEEE statement of support for Open Science
- IEEE signs San Francisco Declaration on Research Assessment (DORA)
- Read about how IEEE journals maintain top citation rankings
Open Access Solutions

- Visit IEEE Open

Visit the IEEE Author Center
Find author resources >
- > IEEE Collabratec ®
- > Choosing a journal
- > Writing
- > Author Tools
- > How to Publish with IEEE (English) (PPT, 3 MB)
- > How to Publish with IEEE (Chinese) (PPT, 3 MB)
- > Benefits of Publishing with IEEE (PPT, 7 MB)
- > View author tutorial videos
- Read the IEEE statement on appropriate use of bibliometric indicators
Publication types and subscription options
- Journal and magazine subscriptions
- Digital library subscriptions
- Buy individual articles from IEEE Xplore
For organizations:
- Browse IEEE subscriptions
- Get institutional access
- Subscribe through your local IEEE account manager
Publishing information
IEEE publishing makes the exchange of technical knowledge possible with the highest quality and the greatest impact.
- Open access publishing options
- Intellectual Property Rights (IPR)
- Reprints of articles
- Services for IEEE organizations
Contact information
- Contact IEEE Publications
- About the Publication Services & Products Board
Related Information >
Network. collaborate. create with ieee collabratec®..
All within one central hub—with exclusive features for IEEE members.
- Experience IEEE Collabratec

Join/Renew IEEE or a Society
Receive member access to select content, product discounts, and more.
- Review all member benefits

Try this easy-to-use, globally accessible data repository that provides significant benefits to researchers, data analysts, and the global technical community.
- Start learning today

IEEE is committed to helping combat and mitigate the effects of climate change.
- See what's new on the IEEE Climate Change site
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
How to write a technical paper or a research paper
By michael ernst, april, 2005 last updated: august 18, 2023, which details to include, make the organization and results clear, getting started: overcoming writer's block and procrastination, writing style, computer program source code, numbers and measurements, processing data, related work, when to submit your paper for publication, responding to conference reviews, norman ramsey's advice, other resources, introduction.
This document describes several simple, concrete ways to improve your writing, by avoiding some common mistakes. The end of this document contains more resources for improving your writing.
Some people believe that writing papers, giving talks , and similar “marketing” activities are not part of research, but an adjunct to it or even an undesirable distraction. This view is inaccurate. The purpose of research is to increase the store of human knowledge, and so even the very best work is useless if you cannot effectively communicate it to the rest of the world. If a paper is poorly written, then readers might conclude you spent as little effort on the research that it describes.
Equally importantly, writing papers and giving talks will clarify your thinking and thereby improve your research. You may be surprised how difficult it is to clearly communicate your ideas and contributions; doing so will force you to understand them more deeply and enable you to improve them.
Know your message, and stay on message
The goal of writing a paper is to change people's behavior: for instance, to change the way they think about a research problem or to convince them to use a new approach. Determine your goal (also known as your thesis), and focus the paper around that goal.
As a general rule, your paper needs to convince the audience of three key points. If any of these is missing or unclear, the paper will not be compelling.
- The problem is important . The problem has a significant impact and consequences. You can buttress your argument by showing that others consider the problem important.
- The problem is hard . Explain that obvious techniques and existing approaches do not suffice. Showing what others have tried can be effective here.
- You have solved the problem. This is often demonstrated via experiments. Keep in mind how you expect the behavior of readers to change once they appreciate your contributions. You'll also need to convince readers that your contributions are novel. When expressing this, it is helpful to explain why no one else thought of your approach before (or why, if they thought of it, they would have rejected the approach) , and whether similar insights apply to other problems.
Before you write your paper, you need to understand your audience. Who will read your paper? What are their backgrounds, motivations, interests, and beliefs? What are the key points you want a reader person to take away from your paper? Once you know the thesis and audience, you can determine what points your document should make to achieve its purpose.
For each point in your paper, you need to explain both what and why . Start with what, but don't omit why. For example, it is not enough to state how an algorithm works; you should explain why it works in that way, or why another way of solving the problem would be different. Similarly, it is not sufficient to present a figure or facts. You must also ensure that reader understands the significance or implications of the figure and what parts of it are most important.
Your purpose is to communicate specific ideas, and everything about your paper should contribute to this goal. If any part of the paper does not support your main point, then delete or change that part. You must be ruthless in cutting every irrelevant detail, however true it may be. Everything in your paper that does not support your main point distracts from it.
Write for the readers, rather than writing for yourself. In particular, think about what matters to the intended audience, and focus on that. It is not necessarily what you personally find most intriguing.
A common mistake is to focus on what you spent the most time on. Do not write your paper as a chronological narrative of all the things that you tried, and do not devote space in the paper proportionately to the amount of time you spent on each task. Most work that you do will never show up in any paper; the purpose of infrastructure-building and exploration of blind alleys is to enable you to do the small amount of work that is worth writing about. Another way of stating this is that the purpose of the paper is not to describe what you have done, but to inform readers of the successful outcome or significant results, and to convince readers of the validity of those conclusions.
Likewise, do not dwell on details of the implementation or the experiments except insofar as they contribute to your main point. This is a particularly important piece of advice for software documentation, where you need to focus on the software's benefits to the user, and how to use it, rather than how you implemented it. However, it holds for technical papers as well — and remember that readers expect different things from the two types of writing!
The audience is interested in what worked, and why, so start with that. If you discuss approaches that were not successful, do so briefly, and typically only after you have discussed the successful approach. Furthermore, the discussion should focus on differences from the successful technique, and if at all possible should provide general rules or lessons learned that will yield insight and help others to avoid such blind alleys in the future.
Whenever you introduce a strawman or an inferior approach, say so upfront. A reader will (and should) assume that whatever you write in a paper is something you believe or advocate, unless very clearly marked otherwise. A paper should never first detail a technique, then (without forewarning) indicate that the technique is flawed and proceed to discuss another technique. Such surprises confuse and irritate readers. This mistake is often called “leading the reader down the garden path”.
When there are multiple possible approaches to a problem, it is preferable to give the best or successful one first. Oftentimes it is not even necessary to discuss the alternatives. If you do, they should generally come after, not before, the successful one. Your paper should give the most important details first, and the less important ones afterward. Its main line of argument should flow coherently rather than being interrupted. It can be acceptable to state an imperfect solution first (with a clear indication that it is imperfect) if it is a simpler version of the full solution, and the full solution is a direct modification of the simpler one. Less commonly, it can be acceptable to state an imperfect solution first if it is an obvious solution that every reader will assume is adequate; but use care with this rationalization, since you are usually wrong that every reader will jump to the given conclusion.
A paper should communicate the main ideas of your research (such as the techniques and results) early and clearly. Then, the body of the paper can expand on these points; a reader who understands the structure and big ideas can better appreciate the details. Another way of saying this is that you should give away the punchline. A technical paper is not a joke or a mystery novel. The reader should not encounter any surprises, only deeper explanations of ideas that have already been introduced. It's particularly irritating when an abstract or introduction states, “We evaluated the relationship between baldness and beekeeping”, with the key results buried pages later. A better abstract would say, “Male beekeepers are 25% more likely to be bald (p=.04), but there is no statistically significant correlation for female beekeepers.”
The same advice applies at the level of sections and paragraphs. It is a bad approach to start with a mass of details and only at the end tell the reader what the main point was or how the details related to one another. Instead, state the point first and then support it. The reader is more likely to appreciate which evidence is important and why, and is less likely to become confused or frustrated.
For each section of the paper, consider writing a mini-introduction that says what its organization is, what is in each subpart, and how the parts relate to one another. For the whole paper, this is probably a paragraph. For a section or sub-section, it can be as short as a sentence. This may feel redundant to you (the author), but readers haven't spent as much time with the paper's structure as you have, so they will truly appreciate these signposts that orient them within your text.
Some people like to write the abstract, and often also the introduction, last. Doing so makes them easier to write, because the rest of the paper is already complete and can just be described. However, I prefer to write these sections early in the process (and then revise them as needed), because they frame the paper. If you know the paper's organization and outlook, then writing the front matter will take little effort. If you don't, then it is an excellent use of your time to determine that information by writing the front matter. To write the body of the paper without knowing its broad outlines will take more time in the long run. Another way of putting this is that writing the paper first will make writing the abstract faster, and writing the abstract first will make writing the paper faster. There is a lot more paper than abstract, so it makes sense to start with that and to clarify the point of the paper early on.
It is a very common error to dive into the technical approach or the implementation details without first appropriately framing the problem and providing motivation and background. Readers need to understand what the task is before they are convinced that they should pay attention to what you are saying about it. You should first say what the problem or goal is, and — even when presenting an algorithm — first state what the output is and probably the key idea, before discussing steps. Avoid providing information that isn't useful to readers/users. It just distracts from the important content.
Some writers are overwhelmed by the emptiness of a blank page or editor buffer, and they have trouble getting started with their writing. Don't worry! Here are some tricks to help you get started. Once you have begun, you will find it relatively easier to revise your notes or first draft. The key idea is to write something , and you can improve it later.
Start verbally . Explain what the paper needs to say to another person. After the conversation is over, write down what you just said, focusing on the main points rather than every word you spoke. Many people find it easier to speak than to write. Furthermore, getting feedback and giving clarifications will help you discover problems with your argument, explanation, or word choice.
Outline . You may not be ready to write full English paragraphs, but you can decide which sections your paper will have and give them descriptive titles. Once you have decided on the section structure, you can write a little outline of each section, which indicates the subsection titles. Now, expand that into a topic sentence for each paragraph. At this point, since you know the exact topic of each paragraph, you will find the paragraph easy to write.
Stream-of-consciousness notes . Write down everything that you know, in no particular order and with no particular formatting. Afterward, organize what you wrote thematically, bringing related points together. Eventually, convert it into an outline and proceed as above. While writing notes, use phrases/keywords, not complete sentences. The phrases are quicker to write and less likely to derail your brainstorming; they are easier to organize; and you will feel less attached to them and more willing to delete them.
Divide and conquer . Rather than trying to write your entire document, choose some specific part, and write just that part. Then, move on to another part.
Re-use . Find other text that you have written on the topic and start from that. An excellent source is your progress reports — you are writing them, aren't you? This can remind you what was hard or interesting, or of points that you might otherwise forget to make. You will rarely want to re-use text verbatim, both because you can probably convey the point better now, and also because writing for different audiences or in different contexts requires a different argument or phrasing. For example, a technical paper and a technical talk have similar aims but rather different forms.
You must be willing to delete and/or rewrite your notes and early drafts. If you wrote something once, you can write it again (probably better!). Early on, the point is to organize your ideas, not to create finished sentences.
Be brief. Make every word count. If a word does not support your point, cut it out, because excess verbiage and fluff only make it harder for the reader to appreciate your message. Use shorter and more direct phrases wherever possible.
Make your writing crisp and to the point. Eliminate any text that does not support your point. Here is one way you might go about this; it is time-consuming but extremely effective. First, examine each section of the paper in turn and ask what role it serves and whether it contributes to the paper's main point. If not, delete it. Next, within each section, examine each paragraph. Ask whether that paragraph has a single point. If not, rewrite the paragraph. Also ask whether that point contributes to the goals of the section. If not, then delete the paragraph. Next, within each paragraph, examine each sentence. If it does not make a single, clear point that strengthens the paragraph, delete or rewrite it. Finally, within each sentence, examine each word, and delete or replace those that do not strengthen their point. You will need to repeat this entire process multiple times, keeping a fresh perspective on the paper.
Some people find it easier to follow this approach bottom-up, first cutting/rewriting words, then sentences, etc.
Passive voice has no place in technical writing. It obscures who the actor was, what caused it, and when it happened. Use active voice and simple, clear, direct phrasing.
First person is rarely appropriate in technical writing.
- First person is appropriate when describing something that the author of the paper did manually. Recall that your paper should not be couched as a narrative.
- Do not use “we” to mean “the author and the reader” or “the paper”. For example, do not write “In this section, we ...”.
- Do not use “we” to describe the operation of a program or system. “We compute a graph” makes it sound like the authors did it by hand. As a related point, do not anthropomorphize computers: they hate it. Anthropomorphism, such as “the program thinks that ...”, is unclear and vague.
Avoid puffery, self-congratulation, superlatives, and subjective or value judgments: give the objective facts and let the reader judge. Avoid vague terms like “sizable” and “significant” (which are also subjective). Don't overuse the word “novel”.
Do not use words like “clearly”, “easily”, “obviously”, and “trivially”, as in “Obviously, this Taylor series sums to π.” If the point is really obvious, then you are just wasting words by pointing it out. And if the point is not obvious to readers who are not intimately familiar with the subject matter the way you are, then you are offending readers by insulting their intelligence, and you are demonstrating your own inability to communicate the intuition.
Prefer singular to plural number. In “sequences induce graphs”, it is not clear whether the two collections are in one-to-one correspondence, or the set of sequences collectively induces a set of graphs; “each sequence induces a graph” avoids this confusion. Likewise, in “graphs might contain paths”, it is unclear whether a given graph might contain multiple paths, or might contain at most one path.
When describing an experiment or some other event or action that occurred in the past, use past tense . For example, the methodology section might say “We ran the program”. It would be ungrammatical and confusing to use present tense, as in “We run the program”. Present tense is for ongoing events (“I write this letter to inform you...”) or regular events (“I brush my teeth each day”), but not past events (“Yesterday, I eat dinner with my family”). It is also correct to say “Our methodology was to run the program”, where you use past tense “was” and the infinitive “to run”.
When describing the paper itself, use present tense . “This paper shows that ...”. The reason for this is that the reader is experiencing the paper in real time.
Avoid gratuitous use of the future tense “will ...”, as in, “switching the red and green wires will cause the bomb to explode”. It is unclear when the action will occur. If it is an immediate effect, use the shorter and more direct “switching the red and green wires causes the bomb to explode”.
Use “previous work” instead of “existing work”. Your work exists, so “existing work” would refer to it as well.
In a list with 3 or more elements list, put a serial comma between each of the items (including the last two). As a simple example of why, consider this 3-element grocery list written without the clarifying last comma: “milk, macaroni and cheese and crackers”. It's not clear whether that means { milk, macaroni and cheese, crackers } or { milk, macaroni, cheese and crackers }. As another example, “I would like to thank my parents, Rene Descartes and Ayn Rand,” suggests rather unusual parentage, whereas “I would like to thank my parents, Rene Descartes, and Ayn Rand,” shows a debt to four people. I've seen real examples that were even more confusing than these.
In English, compound adjectives are hyphenated but compound nouns are not. Consider “the semantics provide name protection” versus “the name-protection semantics”.
Prefer unambiguous words to ambiguous ones. Do not use “as” or “since” to mean “because”. Do not use “if” to mean “whether”.
Use quotations sparingly. A clear paraphrase of the points that are relevant to your own work (along with a proper citation) is usually better than a long quotation from a previous publication.
Avoid third-person pronouns when you can. The old standard was “he”, which is masculine chauvinist. The new standard is “he or she”, which can be viewed as heteronormative and which some people find clumsy. An emerging standard is “they” as a first-person singular pronoun, which is inclusive but grammatically incorrect and confusing (see comments above about singular vs. plural number).
Some of the suggestions in this document are about good writing, and that might seem secondary to the research. But writing more clearly will help you think more clearly and often reveals flaws (or ideas!) that had previously been invisible even to you. Furthermore, if your writing is not good, then either readers will not be able to comprehend your good ideas, or readers will be (rightly) suspicious of your technical work. If you do not (or cannot) write well, why should readers believe you were any more careful in the research itself? The writing reflects on you, so make it reflect well.
Use figures! Different people learn in different ways, so you should complement a textual or mathematical presentation with a graphical one. Even for people whose primary learning modality is textual, another presentation of the ideas can clarify, fill gaps, or enable the reader to verify his or her understanding. Figures can also help to illustrate concepts, draw a skimming reader into the text (or at least communicate a key idea to that reader). Figures make the paper more visually appealing.
It is extremely helpful to give an example to clarify your ideas: this can make concrete in the reader's mind what your technique does (and why it is hard or interesting). A running example used throughout the paper is also helpful in illustrating how your algorithm works, and a single example permits you to amortize the time and space spent explaining the example (and the reader's time in appreciating it). It's harder to find or create a single example that you re-use throughout the paper, but it is worth it.
A figure should stand on its own, containing all the information that is necessary to understand it. Good captions contain multiple sentences; the caption provides context and explanation. For examples of good, informative captions, see the print editions of magazines such as Scientific American and American Scientist . The caption should state what the figure illustrates or what conclusion a reader should draw from it. Don't write an obvious description of what the figure is, such as "Code example". Never write a caption like “The Foobar technique”; the caption should also say what the Foobar technique is, what it is good for, or how it works. The caption may also need to explain the meaning of columns in a table or of symbols in a figure. However, it's even better to put that information in the figure proper; for example, use labels or a legend. When the body of your paper contains information that belongs in a caption, there are several negative effects. The reader is forced to hunt all over the paper in order to understand the figure. The flow of the writing is interrupted with details that are relevant only when one is looking at the figure. The figures become ineffective at drawing in a reader who is scanning the paper — an important constituency that you should cater to!
As with naming , use pictorial elements consistently. Only use two different types of arrows (or boxes, shading, etc.) when they denote distinct concepts; do not introduce inconsistency just because it pleases your personal aesthetic sense. Almost any diagram with multiple types of elements requires a legend (either explicitly in the diagram, or in the caption) to explain what each one means; and so do many diagrams with just one type of element, to explain what it means.
Some writers label all the types of figures differently — some as “figure”, others as “table” or “graph” or “picture”. This differentiation has no benefits, but it does have a drawback: it is very hard for a reader to find “table 3”, which might appear after “figure 7” but before “freehand drawing 1”. You should simply call them all figures and number them sequentially. The body of each figure might be a table, a graph, a diagram, a screenshot, or any other content.
Put figures at the top of the page, not in the middle or bottom. If a numbered, captioned figure appears in the middle or at the bottom of a page, it is harder for readers to find the next paragraph of text while reading, and harder to find the figure from a reference to it.
Avoid bitmaps, which are hard to read. Export figures from your drawing program in a vector graphics format. If you must use a bitmap (which is only appropriate for screenshots of a tool), then produce them at very high resolution. Use the biggest-resolution screen you can, and magnify the portion you will capture.
Don't waste text in the paper (and tax the reader's patience) regurgitating information that is expressed more precisely and concisely in a figure. For example, the text should not repeat the numbers from a table or graph. Text in the paper should add insight or explanations, or summarize the conclusions to be drawn from the data in the figure.
Your code examples should either be real code, or should be close to real code. Never use synthetic examples such as procedures or variables named foo or bar . Made-up examples are much harder for readers to understand and to build intuition regarding. Furthermore, they give the reader the impression that your technique is not applicable in practice — you couldn't find any real examples to illustrate it, so you had to make something up.
Any boldface or other highlighting should be used to indicate the most important parts of a text. In code snippets, it should never be used to highlight syntactic elements such as “public” or “int”, because that is not the part to which you want to draw the reader's eye. (Even if your IDE happens to do that, it isn't appropriate for a paper.) For example, it would be acceptable to use boldface to indicate the names of procedures (helping the reader find them), but not their return types.
Give each concept in your paper a descriptive name to make it more memorable to readers. Never use terms like “approach 1”, “approach 2”, or “our approach”, and avoid acronyms when possible. If you can't think of a good name, then quite likely you don't really understand the concept. Think harder about it to determine its most important or salient features.
It is better to name a technique (or a paper section, etc.) based on what it does rather than how it does it.
Use terms consistently and precisely. Avoid “elegant variation”, which uses different terms for the same concept to avoid boredom on the part of the reader or to emphasize different aspects of the concept. While elegant variation may be appropriate in poems, novels, and some essays, it is not acceptable in technical writing, where you should clearly define terms when they are first introduced, then use them consistently. If you switch wording gratuitously, you will confuse the reader and muddle your point. A reader of a technical paper expects that use of a different term flags a different meaning, and will wonder what subtle difference you are trying to highlight. Thus, don't confuse the reader by substituting “program”, “library”, “component”, “system”, and “artifact”, nor by conflating “technique”, “idea”, “method” and “approach”, nor by switching among “program”, “code”, and “source”. Choose the best word for the concept, and stick with it.
Do not use a single term to refer to multiple concepts. If you use the term “technique” for every last idea that you introduce in your paper, then readers will become confused. This is a place that use of synonyms to distinguish concepts that are unrelated (from the point of view of your paper) is acceptable. For instance, you might always use “phase” when describing an algorithm but “step” when describing how a user uses a tool.
When you present a list, be consistent in how you introduce each element, and either use special formatting to make them stand out or else state the size of the list. Don't use, “There are several reasons I am smart. I am intelligent. Second, I am bright. Also, I am clever. Finally, I am brilliant.” Instead, use “There are four reasons I am smart. First, I am intelligent. Second, I am bright. Third, I am clever. Fourth, I am brilliant.” Especially when the points are longer, this makes the argument much easier to follow. Some people worry that such consistency and repetition is pedantic or stilted, or it makes the writing hard to follow. There is no need for such concerns: none of these is the case. It's more important to make your argument clear than to achieve “elegant variation” at the expense of clarity.
Choose good names not only for the concepts that you present in your paper, but for the document source file. Don't name the file after the conference to which you are submitting (the paper might be rejected) or the year. Even if the paper is accepted, such a name won't tell you what the paper is about when you look over your files in later years. Instead, give the paper or its folder/directory a name that reflects its content. Another benefit is that this will also lead you to think about the paper in terms of its content and contributions.
Here is a piece of advice that is specific to computing: do not use the vague, nontechnical term “bug”. Instead, use one of the standard terms fault, error, or failure. A fault is an underlying defect in a system, introduced by a human. A failure is a user-visible manifestation of the fault or defect. In other circumstances, “bug report” may be more appropriate than “bug”.
Digits of precision:
- Don't report more digits of precision than the measurement process reliably and reproducibly produces. The 3rd or 4th digit of precision is rarely accurate and generalizable; if you don't have confidence that it is both repeatable and generalizable to new experiments, omit it. Another way to say this is that if you are not confident that a different set of experiments would produce all the same digits, then don't report so much precision.
- Don't report more digits of precision than needed to convey your message. If the difference between 4.13 and 4 will not make a difference in convincing readers, then don't report the extra digits. Reporting extra digits can distract readers from the larger trends and the big picture. Including an inappropriate number of digits of precision can cast suspicion on all of your results, by giving readers the impression that you are statistically naive.
- Use a consistent number of digits of precision. If the measured data are 1.23, 45.67, and 891.23, for example, you might report them as 1.23, 45.7, and 891, or as 1.2, 46, and 890, or as 1, 50, and 900. (An exception is when data are known to sum to a particular value; I would report 93% and 7% rather than either 93% and 7.4% or 90% and 7%. Often it's appropriate to report percentages as whole numbers rather than using the same precision.)
- If you do any computations such as ratios, your computations should internally use the full precision of your actual measurements, even though your paper reports only a limited number of digits of precision.
- If a measurement is exact, such as a count of items, then it can be acceptable to give the entire number even if it has many digits; by contrast, timings and other inexact measurements should always be reported with a limited number of digits of precision.
Do not confuse relative and absolute measurements. For instance, suppose your medicine cures 30% of patients, and the placebo cures 25% of patients. You could report that your medicine's cure rate is .3, the placebo's cure rate is .25, and your medicine's cure rate is either .05 greater or 20% greater. (Other correct, but less good, ways to say the same thing are that it cures 20% more, 120% as many, or 1.2 times as many patients.) It would be inaccurate to state that your medicine cures 5% more patients or your medicine cures 120% more patients. Just as you need to correctly use “120% more” versus “120% as many”, you need to correctly use “3 times faster than” versus “3 times as fast as”. A related, also common, confusion is between “3 times faster than and 3 times as fast as”. And, “2 times fewer” makes absolutely no sense. I would avoid these terms entirely. “Half as many” is a much better substitute for “2 times fewer”.
Given the great ease of misunderstanding what a percentage means or what its denominator is, I try to avoid percentages and focus on fractions whenever possible, especially for base measurements. For comparisons between techniques, percentages can be acceptable. Avoid presenting two different measurements that are both percentages but have different denominators.
Your paper probably includes tables, bibliographies, or other content that is generated from external data. Your paper may also be written in a text formatting language such as LaTeX. In each of these cases, it is necessary to run some external command to create some of the content or to create the final PDF.
All of the steps to create your final paper should be clearly documented — say, in comments or in a notes file that you maintain with the paper. Preferably, they should be automated so that you only have to run one command that collects all the data, creates the tables, and generates the final PDF.
If you document and automate these steps, then you can easily regenerate the paper when needed. This is useful if you re-run experiments or analysis, or if you need to defend your results against a criticism by other researchers. If you leave some steps manual, then you or your colleagues are highly likely to make a mistake (leading to a scientific error) or to be unable to reproduce your results later.
One good way to automate these tasks is by writing a program or creating a script for a build system such as Ant, Gradle, Make, Maven, etc.
A related work section should not only explain what research others have done, but in each case should compare and contrast that to your work and also to other related work. After reading your related work section, a reader should understand the key idea and contribution of each significant piece of related work, how they fit together (what are the common themes or approaches in the research community?), and how your work differs. Don't write a related work section that is just a list of other papers, with a sentence about each one that was lifted from its abstract, and without any critical analysis nor deep comparison to other work.
Unless your approach is a small variation on another technique, it is usually best to defer the related work to the end of the paper. When it comes first, it gives readers the impression that your work is rather derivative. (If this is true, it is your responsibility to convey that clearly; if it is not true, then it's misleading to intimate it.) You need to ensure that readers understand your technique in its entirety, and also understand its relationship to other work; different orders can work in different circumstances.
Just as you should generally explain your technique first, and later show relationships with other work, it is also usually more effective to defer a detailed discussion of limitations to a later section rather than the main description of your technique. You should be straightforward and honest about the limitations, of course (do mention them early on, even if you don't detail them then), but don't destroy the coherence of your narrative or sour the reader on your technique.
Get feedback ! Finish your paper well in advance, so that you can improve the writing. Even re-reading your own text after being away from it can show you things that you didn't notice. An outside reader can tell you even more.
When readers misunderstand the paper, that is always at least partly the author's fault! Even if you think the readers have missed the point, you will learn how your work can be misinterpreted, and eliminating those ambiguities will improve the paper.
Be considerate to your reviewers, who are spending their time to help you. Here are several ways to do that.
As with submission to conferences, don't waste anyone's time if there are major flaws. Only ask someone to read (a part of) your paper when you think you will learn something new, because you are not aware of serious problems. If only parts are ready, it is best to indicate this in the paper itself (e.g., a TODO comment that the reader will see or a hand-written annotation on a hardcopy) rather than verbally or in email that can get forgotten or separated from the paper.
Sometimes you want to tell a colleague who is giving you feedback that some sections of your draft are not ready to be read, or to focus on particular aspects of the document. You should write such directions in the paper, not just in email or verbally. You will then update them as you update the paper, and all relevant information is collected together. By contrast, it's asking for trouble to make your colleague keep track of information that is in multiple places.
It is most effective to get feedback sequentially rather than in parallel. Rather than asking 3 people to read the same version of your paper, ask one person to read the paper, then make corrections before asking the next person to read it, and so on. This prevents you from getting the same comments repeatedly — subsequent readers can give you new feedback rather than repeating what you already knew, and you'll get feedback on something that is closer to the final version. If you ask multiple reviewers at once, you are de-valuing their time — you are indicating that you don't mind if they waste their time saying something you already know. You might ask multiple reviewers if you are not confident of their judgment or if you are very confident the paper already is in good shape, in which case there are unlikely to be major issues that every reviewer stumbles over.
It usually best not to email the document, but to provide a location from which reviewers can obtain the latest version of the paper, such as a version control repository or a URL you will update. That way, you won't clutter inboxes with many revisions, and readers can always get the most recent copy.
Be generous with your time when colleagues need comments on their papers: you will help them, you will learn what to emulate or avoid, and they will be more willing to review your writing.
Some of your best feedback will be from yourself, especially as you get more thoughtful and introspective about your writing. To take advantage of this, start writing early. One good way to do this is to write a periodic progress report that describes your successes and failures. The progress report will give you practice writing about your work, oftentimes trying out new explanations.
Whereas you should start writing as early as possible, you don't need to put that writing in the form of a technical paper right away. In fact, it's usually best to outline the technical paper, and get feedback on that, before you start to fill in the sections with text. (You might think that you can copy existing text into the paper, but it usually works out better to write the information anew. With your knowledge of the overall structure, goals, and audience, you will be able to do a much better job that fits with the paper's narrative.) When outlining, I like to start with one sentence about the paper; then write one sentence for each section of the paper; then write one sentence for each subsection; then write one sentence for each paragraph (think of this as the topic sentence); and at that point, it's remarkably easy just to flesh out the paragraphs.
You should not submit your paper too early, when it does not reflect well on you and a submission would waste the community's reviewing resources. You should not submit your paper too late, because then the community is deprived of your scientific insights. In general, you should err on the side of submitting too late rather than too early.
A rule of thumb is to submit only if you are proud for the world to associate your name with the work, in its current form . If you know of significant criticisms that reviewers might raise, then don't submit the paper.
Submitting your paper prematurely has many negative consequences.
- You will waste the time of hard-working reviewers, who will give you feedback that you could have obtained in other ways.
- You will get a reputation for shoddy work.
- You will make the paper less likely to be accepted in the future. Oftentimes the same reviewers may serve two different venues. Reviewing a paper again puts a reviewer in a negative state of mind. I have frequently heard reviewers say, “I read an earlier version of this paper, it was a bad paper, and this version is similar.” (This is unethical because reviewers are not supposed to talk about papers they have reviewed, but nonetheless it is very common.) Now the paper will likely be rejected again, and the whole committee gets a bad impression of you. A reviewer who has read a previous version of the paper may read the resubmission less carefully or make assumptions based on a previous version. To sum up: it's harder to get a given paper accepted on its second submission, than it would have been to get the identical paper accepted on its first submission.
Here are some bad reasons to submit a paper.
It's true that the feedback from reviewers is extraordinarily valuable to you and will help you improve the paper. However, you should get feedback from other scientists (your friends and colleagues) before submitting for publication.
Those are true facts, and some people do “salami-slice” their research into as many papers as possible — such papers are called a “least publishable unit”. However, doing so leads to less impact than publishing fewer papers, each one with more content. If a paper contains few contributions, it is less likely to make a big impression, because it is less exciting. In addition, readers won't enjoy reading many pages to learn just a few facts.
Note: This point refers to taking a single research idea or theme and splitting it into multiple publications. When there are multiple distinct research contributions, it can be appropriate to describe them in different papers.
The reviewing process can be frustrating, because it contains a great deal of randomness: the same paper would be rejected by some reviewers and accepted by others. However, all great papers are accepted and all bad papers are rejected. For mediocre papers, luck plays a role. Your goal should not be to write great papers, not mediocre ones. Find a way to improve your paper. Recognize the great value of reviews: they provide a valuable perspective on your work and how to improve it, even if you feel that the reviewer should have done a better job.
If you aren't excited about the paper, it is unlikely that other people will be. Furthermore, the period after submitting the paper is not a time to take a break, but an opportunity to further improve it.
After you submit a paper, don't stop working on it! You can always improve the research. For instance, you might expand the experiments, improve the implementation, or make other changes. Even if your paper is accepted, you want the accepted version to be as impressive as possible. And if the paper is rejected, you need to have a better paper to submit to the next venue.
(This section is most relevant to fields like computer science where conferences are the premier publication venue. Responding to journal reviews is different.)
Many conferences provide an author response period: the authors are shown the reviews and are given limited space (say, 500 words) to respond to the reviews, such as by clarifying misunderstandings or answering questions. The author response is sometimes called a “rebuttal”, but I don't like that term because it sets an adversarial tone.
Your paper will only be accepted if there is a champion for the paper: someone who is excited about it and will try to convince the rest of the committee to accept the paper. Your response needs to give information to your champion to overcome objections. If there isn't a champion, then the main goal of your response is to create that champion. Your response should also give information to detractors to soften their opposition.
After reading the reviews, you may be disappointed or angry. Take a break to overcome this, so that you can think clearly.
For every point in the reviews, write a brief response. Do this in email-response style, to ensure that you did not miss any points. You will want to save this for later, so it can be better to do this in the paper's version control repository, rather than in a WYSIWYG editor such as Google Docs. (This assumes you have a version control repository for the paper, which you should!) Much of this text won't go in your response, but it is essential for formulating the response.
Summarize (in 5 or so bullet points, however many make sense) the key concerns of the reviewers. Your review needs to focus on the most important and substantive critiques. The authors of the paper should agree on this structure before you start to write the actual response.
Your response to each point will be one paragraph in your response. Start the paragraph with a brief heading or title about the point. Do not assume that the reviewers remember everything that was written by every reviewer, nor that they will re-read their reviews before reading your response. A little context will help them determine what you are talking about and will make the review stand on its own. This also lets you frame the issues in your own words, which may be clearer or address a more relevant point than the reviews did.
Organize your responses thematically. Group the paragraphs into sections, and have a small heading/title for each section. If a given section has just one paragraph, then you can use the paragraph heading as the section heading. Order the sections from most to least important.
This is better than organizing your response by reviewer, first addressing the comments of reviewer 1, then reviewer 2, and so forth. Downsides of by-reviewer organization include:
- It can encourage you not to give sufficient context.
- It does not encourage putting related information together nor important information first.
- You want to encourage all reviewers to read the entire response, rather than encouraging them to just look at one part.
- When multiple reviewers raised the same issue, then no matter where you address it, it's possible for a reviewer to overlook it and think you failed to address it.
- You don't want to make glaringly obvious which issues in a review you had to ignore (for reasons of space or other reasons).
- You don't want to make glaringly obvious that you spent much more time and space on one reviewer than another.
In general, it's best not to mention reviewer names/numbers in your response at all. Make the response be about the science, not about the people.
In your responses, admit your errors forthrightly. Don't ignore or avoid key issues, especially ones that multiple reviewers brought up.
Finally, be civil and thankful the reviewers. They have spent considerable time and energy to give you feedback (even if it doesn't seem to you that they have!), and you should be grateful and courteous in return.
If you submit technical papers, you will experience rejection. In some cases, rejection indicates that you should move on and begin a different line of research. In most cases, the reviews offer an opportunity to improve the work, and so you should be very grateful for a rejection! It is much better for your career if a good paper appears at a later date, rather than a poor paper earlier or a sequence of weak papers.
Even small flaws or omissions in an otherwise good paper may lead to rejection. This is particularly at the elite venues with small acceptance rates, where you should aim your work. Referees are generally people of good will, but different referees at a conference may have different standards, so the luck of the draw in referees is a factor in acceptance.
The wrong lesson to learn from rejection is discouragement or a sense of personal failure. Many papers — even papers that later win awards — are rejected at least once. The feedback you receive, and the opportunity to return to your work, will invariably improve your results.
Don't be put off by a negative tone in the reviews. The referees are trying to help you, and the bast way to do that is to point out how your work can be improved. I often write a much longer review, with more suggestions for improvement, for papers that I like; if the paper is terrible, I may not be able to make as many concrete suggestions, or my high-level comments may make detailed comments moot.
If a reviewer didn't understand something, then the main fault almost always lies with your writing. If you blame a lazy or dumb reviewer, you are missing the opportunity to improve. Reviewers are not perfect, but they work hard to give you helpful suggestions, so you should give them the benefit of the doubt. Remember that just as it is hard to convey technical ideas in your paper (and if you are getting a rejection, that is evidence that you did not succeed!), it is hard to convey them in a review, and the review is written in a few hours rather than the weeks you spent on the paper (not to mention months or years of understanding the concepts). You should closely attend to both the explicit comments, and to underlying issues that may have led to those comments — it isn't always easy to capture every possible comment in a coherent manner. Think about how to improve your research and your writing, even beyond the explicit suggestions in the review — the prime responsibility for your research and writing belongs with you.
Norman Ramsey's nice Teach Technical Writing in Two Hours per Week espouses a similar approach to mine: by focusing on clarity in your writing, you will inevitably gain clarity in your thinking.
Don't bother to read both the student and instructor manuals — the student one is a subset of the instructor one. You can get much of the benefit from just one part, his excellent “principles and practices of successful writers”:
- Correctness. Write correct English, but know that you have more latitude than your high-school English teachers may have given you.
- Consistent names. Refer to each significant character (algorithm, concept, language) using the same word everywhere. Give a significant new character a proper name.
- Singular. To distinguish one-to-one relationships from n-to-m relationships, refer to each item in the singular, not the plural.
- Subjects and verbs. Put your important characters in subjects, and join each subject to a verb that expresses a significant action.
- Information flow. In each sentence, move your reader from familiar information to new information.
- Emphasis. For material you want to carry weight or be remembered, use the end of a sentence.
- Coherence. In a coherent passage, choose subjects that refer to a consistent set of related concepts.
- Parallel structure. Order your text so your reader can easily see how related concepts are different and how they are similar.
- Abstract. In an abstract, don't enumerate a list of topics covered; instead, convey the essential information found in your paper.
- Write in brief daily sessions. Ignore the common myth that successful writing requires large, uninterrupted blocks of time — instead, practice writing in brief, daily sessions.
- Focus on the process, not the product. Don't worry about the size or quality of your output; instead, reward yourself for the consistency and regularity of your input.
- Prewrite. Don't be afraid to think before you write, or even jot down notes, diagrams, and so on.
- Use index cards. Use them to plan a draft or to organize or reorganize a large unit like a section or chapter.
- Write a Shitty First Draft™. Value a first draft not because it's great but because it's there.
- Don't worry about page limits. Write the paper you want, then cut it down to size.
- Cut. Plan a revision session in which your only goal is to cut.
- Norman Ramsey's advice , excerpted immediately above .
- “Hints on writing an M.Eng. thesis” , by Jeremy Nimmer
- my notes on reviewing a technical paper , which indicate how to recognize — and thus produce — quality work
- my notes on choosing a venue for publication
- my notes on giving a technical talk : a talk has the same goal as a paper, namely to convey technical ideas
- my notes on making a technical poster
- Ronald B. Standler's advice on technical writing
- Dave Patterson's Writing Advice
- Advice on SIGPLAN conference submissions (at bottom of page)
- The Elements of Style , William Strunk Jr. and E. B. White, is classic book on improving your writing. It focuses at a low level, on English usage.
- Style: Toward Clarity and Grace , by Joseph M. Williams, is another general-purpose writing guide, with a somewhat higher-level focus than that of Strunk & White.
- The Sense of Style: The Thinking Person's Guide to Writing in the 21st Century , by Steven Pinker, is an excellent guide to writing. It gives reasons (from psychology and other scientific fields) for its advice, making it more authoritative than someone's opinion.
Back to Advice compiled by Michael Ernst .
Basics of scientific and technical writing
- Career Central
- Published: 01 March 2021
- Volume 46 , pages 284–286, ( 2021 )
Cite this article

- Morteza Monavarian 1 , 2
5728 Accesses
2 Citations
6 Altmetric
Explore all metrics
Avoid common mistakes on your manuscript.
Introduction to scientific/technical writing
Scientific/technical writing is an essential part of research. The outcome of a research activity should be shared with others in the form of scientific paper publications; some ideas require a patent to reserve the implementation rights; and almost any research activity requires a funding source, for which a grant proposal is necessary. Therefore, it is crucial to know the differences among writing papers, patents, and grant proposals and how to prepare them in a research environment ( Figure 1 ).

Three major types of scientific/technical writing covered in the three-part series.
The publication of papers is a standard way to share knowledge and transfer methods in scientific communities, thus a pivotal part of any research activity, especially in an academic environment. In industry, where financial profit is a key factor, patents are possibly more favorable.
Types of paper publications
There are different types of paper publications, depending on the content, audience, purpose, length, and scope: original research, review articles, invited articles, conference proceedings, comments/errata, and press releases ( Figure 2 ).
Original research articles may be published in journals or conference proceedings (or preprints in arXiv) and target specific audiences within a field of research. Journal research papers require peer review that typically involves an editor and two reviewers. For conference proceedings, there is usually no direct peer-review process, but the work has to be presented in the corresponding conference to be eligible for publication.
In contrast to original research articles, which are written on special topics within a field of research, review articles normally cover an overview of research and tend to be longer. Review articles do not necessarily reflect on novel data or ideas and could be similar to a book chapter. However, unlike review articles, book chapters or books are usually written when the target field of research is fully established. In a review paper, figures are typically not original and reprinted from other publications, for which a copyright permission from the original publishing journal is required.
Invited articles are written in response to an invitation by a journal editor or a conference organizer in a specific field of research or for a special issue. An invited article could be a review article or original research. Invited articles are normally written by peers or researchers with significant contributions to a field of research.
Other items published include comments or errata. The purpose of a comment on a published article is to bring points of criticism to the attention of the readers as well as the authors of the original article. The comments can be published in the same journal as the original paper. Errata correct mistakes in an article after publication.
Finally, press releases target a more general audience and normally report on a review/overview of recently published research. The author of the press release is not the same as that of the original article. Unlike peer-reviewed research articles, press release articles are usually not citable.
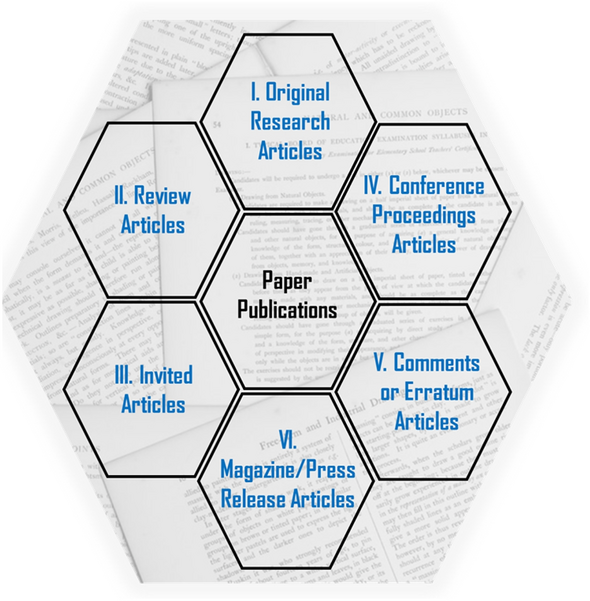
Six major types of paper publications.
Writing structures and styles
Different articles have different structures. A research article typically consists of a title, author list and affiliations, abstract, main body, conclusions, acknowledgments, and references.
A good title should be concise, to the point, and free of abbreviations. Author lists and affiliations include whoever has intellectually contributed to the paper (identifying at least one corresponding author and email address), with the order approved by all of the co-authors. A good abstract should give a full, but short, overview of the work with both qualitative and quantitative data summaries. An abstract should be self-contained, meaning it should not require a referral to a reference or figure. Abstracts are usually written in the present tense and have an active voice.
Unlike letters with no sections within the main body, the main body of research articles normally contains several sections (e.g., introduction, methods and approach, results, and discussions). The introduction should contain a deep literature review of the field as the basis for motivating the current work. The last paragraph of the introduction usually summarizes what to expect from the article. The following sections will demonstrate study methods, results, and discussions/interpretations of the results, including plots, tables, and figures.
Conclusions summarize the findings of the paper and may point out any future directions. The acknowledgment lists all funding support and gratitude toward anyone who helped with the work, not including those listed as co-authors. The reference section lists all references in a format described in the journal submission guidelines. Using reference management software (such as Zotero, Mendeley, BibTex) makes organizing the references less cumbersome. A good scholarly research article should have citations for almost any claims made within the main body, to ensure proper connections to the prior research in the field.
Unlike patents, papers require a deep scientific background and should be straight to the point. While patents include all aspects of the idea, papers typically have space limitations, so should therefore be concise. The data in research articles should speak for itself. The language of a research paper should be clear and simple and not include metaphors or slang.
Where to submit
The submission target depends on several factors: (1) scope of the journal, (2) length of the paper (letters versus regular length articles), (3) access (regular versus open access), and (4) impact factor (IF). The scope of the journal is probably the first thing to consider; you cannot publish a biological paper in a humanity journal. Regarding length, a letter is much shorter and usually does not have section headings. It depends on the discipline, but sometimes letters are more favorable because of the shorter publication time, preparation simplicity, and more readability (takes less time to read, which may also improve the visibility of the paper). In terms of access, you may pay publication charges to receive open access, or some journals charge publication fees upon acceptance. Open access papers could potentially get more visibility than normal publications.
IF is a specific journal parameter indicating the average number of citations per published article over a certain period of time. Paying serious attention to IF could oppose the mission of science itself, as it could mean that you judge a paper only by where it is being published and not by its intrinsic values (also called high IF syndrome).
Submission, peer-review, and decisions
Your article will enter the peer-review process upon submission. If done properly, the peer-review process not only avoids false or inconsistent data from being published (and helps science in this regard), but also improves your paper and removes any potential errors/issues or vague discussion. During submission, some journals may ask you to include/exclude reviewers. If there are researchers who may have a direct conflict with your work, you may list them as excluded reviewers. You may also suggest to include reviewers who have relevant experience.
Serving as a reviewer may help you with your own writing, as it assists in developing critical thinking. However, for the sake of science, try peer-reviewing for lesser-known journals (the high-impact journals already have many reviewers). Decisions on your article could be (1) reject: cannot be accepted to this journal; (2) referral to other journals; submit to another journal; (3) accept: accepted as is; (4) major revisions: not accepted, but could be accepted upon significant improvement (upon approval from reviewers); and (5) minor revision: accept but needs slight revisions (no need to go through a peer review again).
Copyrights and archiving
Most journals obtain copyrights from the authors before submission via a copyright transfer form. Hence, re-publishing the same data and plots in another journal is often forbidden. Also, the language of a paper should have a significant difference from an already published paper to avoid plagiarism. In the case where some content (e.g., figure or table) needs to be re-published in another paper (e.g., for review articles or thesis/dissertations), one can request a copyright permission from the original publishing journal. Also, archiving of one’s published papers in personal profile websites (e.g., Researchgate or LinkedIn) is usually forbidden, unless the paper is published as open access.
Final tips for paper publication
Read, read, read! There is probably no better way of improving writing skills than reading other articles and books.
Make illustrative and self-contained figures that can stand on their own.
Know your audience when selecting a journal. Find out which journals are normally targeted by people in your research community.
Protect yourself from high impact factor (IF) syndrome. Journals with a high IF may have very subjective decision criteria. It is sometimes more important to have your paper published than to spend a couple of years waiting for publication in a high-impact journal.
Serve as a reviewer. Get a sense of how a peer-review process feels in order to establish critical thinking. Before submitting your article, self-review.
Look forward to a constructive peer review. It definitely improves your paper (always good to have a view from different perspective).
Enjoy your publications!
Author information
Authors and affiliations.
Materials Department, University of California Santa Barbara, Santa Barbara, CA, USA
Morteza Monavarian
Solid State Lighting & Energy Electronics Center, University of California Santa Barbara, Santa Barbara, CA, USA
You can also search for this author in PubMed Google Scholar
Additional information
This article is the first in a three-part series in MRS Bulletin that will focus on writing papers, patents, and proposals.
Rights and permissions
Reprints and permissions
About this article
Monavarian, M. Basics of scientific and technical writing. MRS Bulletin 46 , 284–286 (2021). https://doi.org/10.1557/s43577-021-00070-y
Download citation
Published : 01 March 2021
Issue Date : March 2021
DOI : https://doi.org/10.1557/s43577-021-00070-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Find a journal
- Publish with us
- Track your research
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
Technology articles from across Nature Portfolio
Latest research and reviews.
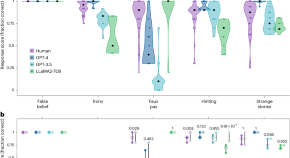
Testing theory of mind in large language models and humans
Testing two families of large language models (LLMs) (GPT and LLaMA2) on a battery of measurements spanning different theory of mind abilities, Strachan et al. find that the performance of LLMs can mirror that of humans on most of these tasks. The authors explored potential reasons for this.
- James W. A. Strachan
- Dalila Albergo
- Cristina Becchio
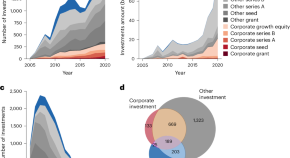
The effects of corporate investment and public grants on climate and energy startup outcomes
Investment in climate and energy startups is growing in the United States. Here the authors show that public grants back high-risk areas, and that publicly funded startups exit at higher rates with corporate backing than with other private investment.
- Kathleen M. Kennedy
- Morgan R. Edwards
- Kavita Surana
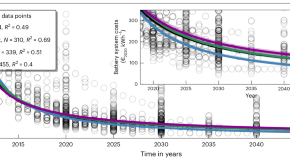
Rapidly declining costs of truck batteries and fuel cells enable large-scale road freight electrification
The costs of battery and fuel cell systems for zero-emission trucks are primed to decline much faster than expected, boosting prospects for their fast global diffusion and electrification of freight transport, with battery-electric trucks probably leading.
- Steffen Link
- Annegret Stephan
- Patrick Plötz
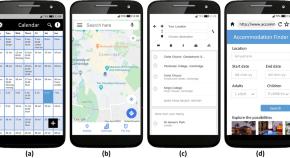
User factors affecting the use of digital services in five European regions and countries
- Joy Goodman-Deane
- Silvia Gaggi

Sync fast and solve things—best practices for responsible digital health
- Constantin Landers
- Alessandro Blasimme
- Effy Vayena
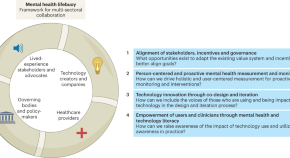
Rethinking technology innovation for mental health: framework for multi-sectoral collaboration
In this Perspective, the authors make recommendations on better aligning stakeholders, including those in technology, practitioners and researchers, to increase collaboration and governance in technology and mental health.
- Sachin R. Pendse
- Mary Czerwinski
News and Comment

How does ChatGPT ‘think’? Psychology and neuroscience crack open AI large language models
Researchers are striving to reverse-engineer artificial intelligence and scan the ‘brains’ of LLMs to see what they are doing, how and why.
- Matthew Hutson

The US Congress is taking on AI — this computer scientist is helping
Kiri Wagstaff, who temporarily shelved her academic career to provide advice on federal AI legislation, talks about life inside the halls of power.
- Nicola Jones

Who’s making chips for AI? Chinese manufacturers lag behind US tech giants
Researchers in China say they are finding themselves five to ten years behind their US counterparts as export restrictions bite.
- Jonathan O'Callaghan
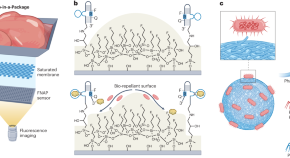
Smart food packaging commercialization
Smart food packaging technologies can actualize real-time, in situ food quality monitoring, increasing food safety and decreasing food waste. Here, we detail challenges that hinder the commercialization of such smart packaging systems and identify opportunities to facilitate their translation from prototype to product.
- Shadman Khan
- Zeinab Hosseinidoust
- Tohid F. Didar

Are robots the solution to the crisis in older-person care?
Social robots that promise companionship and stimulation for older people and those with dementia are attracting investment, but some question their benefits.
- Tammy Worth

NATO is boosting AI and climate research as scientific diplomacy remains on ice
As the military alliance created to counter the Soviet Union expands, it is prioritizing studies on how climate change affects security, cyberattacks and election interference.
- Natasha Gilbert
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
- Publications
- News and Events
- Education and Outreach
Software Engineering Institute
Technical papers.
The SEI Digital Library houses thousands of technical papers and other documents, ranging from SEI Technical Reports on groundbreaking research to conference proceedings, survey results, and source code.
Explainable Verification: Survey, Situations, and New Ideas
April 16, 2024 • white paper, by bjorn andersson, mark h. klein, dionisio de niz.
This report focuses on potential changes in software development practice and research that would help tools used for formal methods explain their output, making software practitioners more likely to trust …
Zero Trust Industry Days 2024 Scenario: Secluded Semiconductors, Inc.
February 27, 2024 • white paper, by rhonda brown.
This scenario guides discussions of solutions submitted to address the challenges of implementing zero trust.
Considerations for Evaluating Large Language Models for Cybersecurity Tasks
February 20, 2024 • white paper, by jeff gennari, shing-hon lau, samuel j. perl, joel parish (openai), girish sastry (openai).
In this paper, researchers from the SEI and OpenAI explore the opportunities and risks associated with using large language models (LLMs) for cybersecurity tasks.
Navigating Capability-Based Planning: The Benefits, Challenges, and Implementation Essentials
February 7, 2024 • white paper, by anandi hira, william nichols.
Based on industry and government sources, this paper summarizes the benefits and challenges of implementing Capability-Based Planning (CBP).
Encoding Verification Arguments to Analyze High-Level Design Certification Claims: Experiment Zero (E0)
January 18, 2024 • white paper, by bjorn andersson, mark h. klein, dionisio de niz, douglas schmidt (vanderbilt university), ronald koontz (boeing company), john lehoczky (carnegie mellon university), george romanski (federal aviation administration), jonathan preston (lockheed martin corporation), daniel shapiro (institute of defense analysis), floyd fazi (lockheed martin corporation), david tate (institute of defense analysis), gordon putsche (the boeing company), hyoseung kim (university of california, riverside).
This paper discusses whether automation of certification arguments can identify problems that occur in real systems.
The Measurement Challenges in Software Assurance and Supply Chain Risk Management
December 22, 2023 • white paper, by nancy r. mead, carol woody, scott hissam.
This paper recommends an approach for developing and evaluating cybersecurity metrics for open source and other software in the supply chain.
Report to the Congressional Defense Committees on National Defense Authorization Act (NDAA) for Fiscal Year 2022 Section 835 Independent Study on Technical Debt in Software-Intensive Systems
December 7, 2023 • technical report, by ipek ozkaya, brigid o'hearn, julie b. cohen, forrest shull.
This independent study of technical debt in software-intensive systems was sent to Congress in December 2023 to satisfy the requirements of NDAA Section 835.
Assessing Opportunities for LLMs in Software Engineering and Acquisition
November 1, 2023 • white paper, by julie b. cohen, james ivers, ipek ozkaya, stephany bellomo, shen zhang.
This white paper examines how decision makers, such as technical leads and program managers, can assess the fitness of large language models (LLMs) to address software engineering and acquisition needs.
Acquisition Security Framework (ASF): Managing Systems Cybersecurity Risk (Expanded Set of Practices)
October 2, 2023 • technical note, by michael s. bandor, charles m. wallen, carol woody, christopher j. alberts.
This framework of practices helps programs coordinate their management of engineering and supply chain risks across the systems lifecycle.
Simulating Realistic Human Activity Using Large Language Model Directives
October 2, 2023 • technical report, by sean huff, thomas g. podnar, dustin d. updyke.
The authors explore how activities generated from the GHOSTS Framework’s NPC client compare to activities produced by GHOSTS’ default behavior and LLMs.
Why Your Software Cost Estimates Change Over Time and How DevSecOps Data Can Help Reduce Cost Risk
September 29, 2023 • white paper, by julie b. cohen.
Early software cost estimates are often off by over 40%; this paper discusses how programs must continually update estimates as more information becomes available.
A Retrospective in Engineering Large Language Models for National Security
By andrew o. mellinger, tyler brooks, shannon gallagher, bryan brown, eric heim, hollen barmer, william nichols, nick winski, nathan m. vanhoudnos, jasmine ratchford, angelique mcdowell, swati rallapalli.
This document discusses the findings, recommendations, and lessons learned from engineering a large language model for national security use cases.
U.S. Leadership in Software Engineering and AI Engineering
August 25, 2023 • white paper, by ipek ozkaya, douglas schmidt (vanderbilt university), forrest shull, john e. robert, erin harper, anita carleton.
A joint SEI/NITRD workshop will advance U.S. national interests through software and AI engineering and accelerate progress across virtually all scientific domains.
A Holistic View of Architecture Definition, Evolution, and Analysis
August 24, 2023 • technical report, by james ivers, sebastián echeverría, rick kazman.
This report focuses on performing architectural decisions and architectural analysis, spanning multiple quality attributes, in a sustainable and ongoing way.
Emerging Technologies: Seven Themes Changing the Future of Software in the DoD
August 24, 2023 • white paper, by scott hissam, shen zhang, michael abad-santos.
This report summarizes the SEI's Emerging Technologies Study (ETS) and identifies seven emerging technologies to watch in software engineering practices and technology.
Demonstrating the Practical Utility and Limitations of ChatGPT Through Case Studies
August 23, 2023 • white paper, by clarence worrell, matthew walsh, alejandro gomez, dominic a. ross.
In this study, SEI researchers conducted four case studies using GPT-3.5 to assess the practical utility of large language models such as ChatGPT.
Software Excellence Through the Agile High Velocity Development℠ Process
July 17, 2023 • technical report, by barti k. perini (ishpi information technologies, inc.), stephen shook (ishpi information technologies, inc.).
The High Velocity Development℠ process earned Ishpi Information Technologies, Inc. the 2023 Watts Humphrey Software Quality Award.
Coding the Future: Recommendations for Defense Software R&D
July 13, 2023 • white paper, by software engineering institute.
This report outlines the key recommendations from the November 2022 workshop "Software as a Modernization Priority."
Engineering of Edge Software Systems: A Report from the November 2022 SEI Workshop on Software Systems at the Edge
June 30, 2023 • white paper, by ipek ozkaya, grace lewis, kevin a. pitstick.
Based on a workshop with thought leaders in the field, this report identifies recommended areas of focus for engineering software systems at the edge.
Software Bill of Materials Framework: Leveraging SBOMs for Risk Reduction
June 14, 2023 • white paper, by carol woody, christopher j. alberts, michael s. bandor, charles m. wallen.
This paper is a Software Bill of Materials (SBOM) Framework that is a starting point for expanding the use of SBOMs for managing software and systems risk.
Generative AI: Key Opportunities and Research Challenges
June 9, 2023 • white paper.
This 2023 workshop report identifies DoD use cases for generative AI and discusses meeting challenges and needs such as investing in guardrails and responsible AI amid a race to capability.
Securing UEFI: An Underpinning Technology for Computing
May 30, 2023 • white paper, by vijay s. sarvepalli.
This paper highlights the technical efforts to secure the UEFI-based firmware that serves as a foundational piece of modern computing environments.
Using Model-Based Systems Engineering (MBSE) to Assure a DevSecOps Pipeline is Sufficiently Secure
May 23, 2023 • technical report, by timothy a. chick, nataliya shevchenko, scott pavetti.
This report describes how analysts can use a model-based systems engineering (MBSE) approach to detect and mitigate cybersecurity risks to a DevSecOps pipeline.
A Strategy for Component Product Lines: Report 2: Specification Modeling for Components in a Component Product Line
May 17, 2023 • special report, by john mcgregor, john j. hudak, sholom g. cohen.
This report introduces the “model chain” concept for specifying a component product line and realizing architecture requirements through the creation–evolution process.
A Strategy for Component Product Lines: Report 3: Component Product Line Governance
May 4, 2023 • special report, by sholom g. cohen, alfred schenker.
This report provides guidance for the community involved with developing and sustaining product lines of components used by the U.S. government.
Program Managers—The DevSecOps Pipeline Can Provide Actionable Data
April 24, 2023 • white paper, by julie b. cohen, bill nichols.
This paper describes the Automated Continuous Estimation for a Pipeline of Pipelines research project, which automates data collection to track program progress.
Zero Trust Industry Day 2022: Areas of Future Research
January 25, 2023 • white paper, by timothy morrow, trista polaski, matthew nicolai.
This paper describes the future research discussed at the 2022 Zero Trust Industry Day event.
Industry Best Practices for Zero Trust Architecture
December 13, 2022 • white paper, by timothy morrow, nathaniel richmond, matthew nicolai.
This paper describes best practices identified during the SEI’s Zero Trust Industry Day 2022, and provides ways to help organizations shift to zero trust.
A Strategy for Component Product Lines: Report 1: Scoping, Objectives, and Rationale
December 8, 2022 • special report, by gabriel moreno, john j. hudak, sholom g. cohen, alfred schenker, john mcgregor.
This report establishes a Component Product Line Strategy to address problems in systematically reusing and integrating components built to conform to component specification models.
Acquisition Security Framework (ASF): Managing Systems Cybersecurity Risk
November 11, 2022 • technical note.
This report provides an overview of the Acquisition Security Framework (ASF), a description of the practices developed thus far, and a plan for completing the ASF body of work.
Zero Trust Industry Day Experience Paper
October 31, 2022 • white paper, by rhonda brown, mary popeck, timothy morrow.
This paper describes the results of the 2022 Zero Trust Industry Day event.
Challenge Development Guidelines for Cybersecurity Competitions
October 27, 2022 • technical report, by dennis m. allen, leena arora, joseph vessella, josh hammerstein, matt kaar, jarrett booz.
This paper draws on the SEI’s experience to provide general-purpose guidelines and best practices for developing effective cybersecurity challenges.
Acquisition Security Framework (ASF): An Acquisition and Supplier Perspective on Managing Software-Intensive Systems’ Cybersecurity Risk
October 4, 2022 • white paper, by carol woody, christopher j. alberts, charles m. wallen, michael s. bandor.
The Acquisition Security Framework (ASF) contains practices that support programs acquiring/building a secure, resilient software-reliant system to manage risks.
Designing Vultron: A Protocol for Multi-Party Coordinated Vulnerability Disclosure (MPCVD)
September 15, 2022 • special report, by allen d. householder.
This report proposes a formal protocol specification for MPCVD to improve the interoperability of both CVD and MPCVD processes.
Common Sense Guide to Mitigating Insider Threats, Seventh Edition
September 7, 2022 • technical report.
The guide describes 22 best practices for mitigating insider threat based on the CERT Division's continued research and analysis of more than 3,000 insider threat cases.
Coordinated Vulnerability Disclosure User Stories
August 25, 2022 • white paper, by art manion, timur d. snoke, vijay s. sarvepalli, jonathan spring, allen d. householder, laurie tyzenhaus, brad runyon, eric hatleback, charles g. yarbrough.
This paper provides user stories to guide the development of a technical protocol and application programming interface for Coordinated Vulnerability Disclosure.
LLVM Intermediate Representation for Code Weakness Identification
July 8, 2022 • white paper, by shannon gallagher, william klieber, david svoboda.
This paper examines whether intermediate representation used in Large Language Models can be useful to indicate the presence of software vulnerabilities.
Digital Engineering Effectiveness
May 19, 2022 • white paper, by alfred schenker, bill nichols, tyler smith (adventium labs, inc.).
This paper explores the reluctance of developers of cyber-physical systems to embrace digital engineering (DE), how DE methods should be tailored to achieve their stakeholders' goals, and how to measure …
A Brief Introduction to the Evaluation of Learned Models for Aerial Object Detection
May 2, 2022 • white paper, by eric heim.
The SEI AI Division assembled guidance on the design, production, and evaluation of machine-learning models for aerial object detection.
Guidance for Tailoring DoD Request for Proposals (RFPs) to Include Modeling
April 27, 2022 • special report, by tom merendino, robert wojcik, julie b. cohen.
This report provides guidance for government program offices that are including digital engineering/modeling requirements into a request for proposal.
Modeling to Support DoD Acquisition Lifecycle Events (Version 1.4)
April 26, 2022 • white paper, by tom merendino, julie b. cohen, robert wojcik.
This document provides suggestions for producing requirement, system, and software models that will be used to support various DoD system acquisition lifecycle events.
Experiences with Deploying Mothra in Amazon Web Services (AWS)
April 26, 2022 • technical report, by daniel ruef, john stogoski, brad powell.
The authors describe development of an at-scale prototype of an on-premises system to test the performance of Mothra in the cloud and provide recommendations for similar deployments.
Extensibility
April 6, 2022 • technical report.
This report summarizes how to systematically analyze a software architecture with respect to a quality attribute requirement for extensibility.
TwinOps: Digital Twins Meets DevOps
March 24, 2022 • technical report, by joe yankel, jerome hugues, anton hristozov, john j. hudak.
This report describes ModDevOps, an approach that bridges model-based engineering and software engineering using DevOps concepts and code generation from models, and TwinOps, a specific ModDevOps pipeline.
March 16, 2022 • Technical Report
By philip bianco, james ivers, sebastián echeverría, rick kazman.
This report summarizes how to systematically analyze a software architecture with respect to a quality attribute requirement for robustness.
An Analysis of How Many Undiscovered Vulnerabilities Remain in Information Systems
March 9, 2022 • white paper, by jonathan spring.
This paper examines the paradigm that the number of undiscovered vulnerabilities is manageably small through the lens of mathematical concepts from the theory of computing.
Using XML to Exchange Floating Point Data
February 10, 2022 • white paper, by john klein.
This paper explains issues of using XML to exchange floating point values, how to address them, and the limits of technology to enforce a correct implementation.
Using Machine Learning to Increase NPC Fidelity
December 1, 2021 • technical report, by dustin d. updyke, thomas g. podnar, geoffrey b. dobson, john yarger.
The authors describe how they used machine learning (ML) modeling to create decision-making preferences for non-player characters (NPCs).
A Prototype Set of Cloud Adoption Risk Factors
October 27, 2021 • white paper, by christopher j. alberts.
Alberts discusses the results of a study to identify a prototype set of risk factors for adopting cloud technologies.
Cloud Security Best Practices Derived from Mission Thread Analysis
September 2, 2021 • technical report, by timothy morrow, donald faatz, nathaniel richmond, angel luis hueca, vincent lapiana.
This report presents practices for secure, effective use of cloud computing and risk reduction in transitioning applications and data to the cloud, and considers the needs of limited-resource businesses.
Accenture: An Automation Maturity Journey
July 29, 2021 • technical report, by rajendra t. prasad (accenture).
This paper describes work in the area of automation that netted Accenture the 2020 Watts Humphrey Software Process Achievement Award.
Planning and Design Considerations for Data Centers
July 19, 2021 • technical note, by lyndsi a. hughes, david sweeney, mark kasunic.
This report shares important lessons learned from establishing small- to mid-size data centers.
Integrating Zero Trust and DevSecOps
July 5, 2021 • white paper, by timothy morrow, geoff sanders, nathaniel richmond, carol woody.
This paper discusses the interdependent strategies of zero trust and DevSecOps in the context of application development.
A State-Based Model for Multi-Party Coordinated Vulnerability Disclosure (MPCVD)
July 1, 2021 • special report, by allen d. householder, jonathan spring.
This report discusses performance indicators that stakeholders in Coordinated Vulnerability Disclosure (CVD) can use to measure its effectiveness.
Human-Centered AI
June 25, 2021 • white paper, by jay palat, matt gaston, frank redner, carol j. smith, tanisha smith, hollen barmer, rachel dzombak.
This white paper discusses Human-Centered AI: systems that are designed to work with, and for, people.
Robust and Secure AI
By rachel dzombak, hollen barmer, eric heim, nathan m. vanhoudnos, tanisha smith, frank redner, matt gaston, jay palat.
This white paper discusses Robust and Secure AI systems: AI systems that reliably operate at expected levels of performance, even when faced with uncertainty and in the presence of danger …
Scalable AI
By jay palat, matt gaston, frank redner, tanisha smith, hollen barmer, rachel dzombak, john wohlbier.
This white paper discusses Scalable AI: the ability of AI algorithms, data, models, and infrastructure to operate at the size, speed, and complexity required for the mission.
The Sector CSIRT Framework: Developing Sector-Based Incident Response Capabilities
June 8, 2021 • technical report, by tracy bills, sharon mudd, justin novak, brittany manley, angel luis hueca, david mcintire.
This framework guides the development and implementation of a sector CSIRT.
Foundation of Cyber Ranges
May 19, 2021 • technical report, by bill reed, dustin d. updyke, geoffrey b. dobson, thomas g. podnar.
This report details the design considerations and execution plan for building high-fidelity, realistic virtual cyber ranges that deliver maximum training and exercise value for cyberwarfare participants.
Software Assurance Guidance and Evaluation (SAGE) Tool
May 3, 2021 • white paper, by robert schiela, ebonie mcneil, luiz antunes, hasan yasar.
The Software Assurance Guidance and Evaluation (SAGE) tool helps an organization assess the security of its systems development and operations practices.
Prioritizing Vulnerability Response: A Stakeholder-Specific Vulnerability Categorization (Version 2.0)
April 30, 2021 • white paper, by jonathan spring, allen d. householder, art manion, vijay s. sarvepalli, eric hatleback, laurie tyzenhaus, madison oliver, charles g. yarbrough.
This paper presents version 2.0 of a testable Stakeholder-Specific Vulnerability Categorization (SSVC) that takes the form of decision trees and that avoids some problems with the Common Vulnerability Scoring System …
Modeling and Validating Security and Confidentiality in System Architectures
March 19, 2021 • technical report, by aaron greenhouse, lutz wrage, jörgen hansson (university of skovde).
This report presents an approach for modeling and validating confidentiality using the Bell–LaPadula security model and the Architecture Analysis & Design Language.
Overview of Practices and Processes of the CMMC 1.0 Assessment Guides (CMMC 1.0)
March 3, 2021 • white paper, by douglas gardner.
This document is intended to help anyone unfamiliar with cybersecurity standards get started with the Department of Defense (DoD) Cybersecurity Maturity Model Certification (CMMC).
Zero Trust: Risks and Research Opportunities
March 1, 2021 • white paper, by geoff sanders, timothy morrow.
This paper describes a zero trust vignette and three mission threads that highlight risks and research areas to consider for zero trust environments.
Artificial Intelligence (AI) and Machine Learning (ML) Acquisition and Policy Implications
February 26, 2021 • white paper, by william e. novak.
This paper reports on a high-level survey of a set of both actual and potential acquisition and policy implications of the use of Artificial Intelligence (AI) and Machine Learning (ML) …
Security Engineering Risk Analysis (SERA) Threat Archetypes
December 16, 2020 • white paper, by carol woody, christopher j. alberts.
This report examines the concept of threat archetypes and how analysts can use them during scenario development.
Loss Magnitude Estimation in Support of Business Impact Analysis
December 15, 2020 • technical report, by brett tucker, daniel j. kambic, david tobar, andrew p. moore.
The authors describe a project to develop an estimation method that yields greater confidence in and improved ranges for estimates of potential cyber loss magnitude.
Emerging Technologies 2020: Six Areas of Opportunity
December 14, 2020 • white paper.
This study seeks to understand what the software engineering community perceives to be key emerging technologies. The six technologies described hold great promise and, in some cases, have already attracted …
Maintainability
December 1, 2020 • technical report, by rick kazman, john klein, james ivers, philip bianco.
This report summarizes how to systematically analyze a software architecture with respect to a quality attribute requirement for maintainability.
Advancing Risk Management Capability Using the OCTAVE FORTE Process
November 17, 2020 • technical note, by brett tucker.
OCTAVE FORTE is a process model that helps organizations evaluate their security risks and use ERM principles to bridge the gap between executives and practitioners.
Analytic Capabilities for Improved Software Program Management
November 2, 2020 • white paper, by christopher miller, david zubrow.
This white paper describes an update to the SEI Quantifying Uncertainty in Early Lifecycle Cost Estimation approach.
AI Engineering for Defense and National Security: A Report from the October 2019 Community of Interest Workshop
October 29, 2020 • special report.
Based on a workshop with thought leaders in the field, this report identifies recommended areas of focus for AI Engineering for Defense and National Security.
NICE Framework Cybersecurity Evaluator
August 20, 2020 • white paper, by christopher herr.
This cybersecurity evaluator is designed to assess members of the cyber workforce within the scope of the NICE Cybersecurity Workforce Framework.
Current Ransomware Threats
August 19, 2020 • white paper, by marisa midler, kyle o'meara.
This report by Marisa Midler, Kyle O'Meara, and Alexandra Parisi discusses ransomware, including an explanation of its design, distribution, execution, and business model.
An Updated Framework of Defenses Against Ransomware
August 18, 2020 • white paper, by timur d. snoke, timothy j. shimeall.
This report, loosely structured around the NIST Cybersecurity Framework, seeks to frame an approach for defending against Ransomware-as-a-Service (RaaS) as well as direct ransomware attacks.
Historical Analysis of Exploit Availability Timelines
August 13, 2020 • white paper, by david warren, jeff chrabaszcz (govini), trent novelly, allen d. householder, jonathan spring.
This paper analyzes when and how known exploits become associated with the vulnerabilities that made them possible.
Architecture Evaluation for Universal Command and Control
August 3, 2020 • white paper, by john klein, harry l. levinson, reed little, jason popowski, philip bianco, patrick donohoe.
The SEI developed an analysis method to assess function allocations in existing C2 systems and reason about design choices and tradeoffs during the design of new C2 systems.
A Risk Management Perspective for AI Engineering
June 10, 2020 • white paper.
This paper describes several steps of OCTAVE FORTE in the context of adopting AI technology.
Attack Surface Analysis - Reduce System and Organizational Risk
June 8, 2020 • white paper, by robert j. ellison, carol woody.
This paper offers system defenders an overview of how threat modeling can provide a systematic way to identify potential threats and prioritize mitigations.
Guide to Implementing DevSecOps for a System of Systems in Highly Regulated Environments
April 8, 2020 • technical report, by jose a. morales, peter capell, david james shepard, richard turner, patrick r. place, suzanne miller.
This Technical Report provides guidance to projects interested in implementing DevSecOps (DSO) in defense or other highly regulated environments, including those involving systems of systems.
Integrability
February 7, 2020 • technical report, by rick kazman, john klein, philip bianco, james ivers.
This report summarizes how to systematically analyze a software architecture with respect to a quality attribute requirement for integrability.
Comments on NISTIR 8269 (A Taxonomy and Terminology of Adversarial Machine Learning)
February 4, 2020 • white paper, by jonathan spring, april galyardt, nathan m. vanhoudnos.
Feedback to the U.S. National Institute of Standards and Technology (NIST) about NIST IR 8269, a draft report detailing the proposed taxonomy and terminology of Adversarial Machine Learning (AML).
Penetration Tests Are The Check Engine Light On Your Security Operations
January 7, 2020 • white paper, by dan j. klinedinst, allen d. householder.
A penetration test serves as a lagging indicator of a network security operations problem. Organizations should implement and document several security controls before a penetration test can be useful.
Prioritizing Vulnerability Response: A Stakeholder-Specific Vulnerability Categorization
December 4, 2019 • white paper, by allen d. householder, jonathan spring, art manion, deana shick, eric hatleback.
This paper presents a testable Stakeholder-Specific Vulnerability Categorization (SSVC) that takes the form of decision trees and that avoids some problems with the Common Vulnerability Scoring System (CVSS).
AI Engineering: 11 Foundational Practices
September 12, 2019 • white paper.
This initial set of recommendations can help organizations that are beginning to build, acquire, and integrate artificial intelligence capabilities into business and mission systems.
Machine Learning in Cybersecurity: A Guide
September 5, 2019 • technical report, by ed stoner, joshua fallon, april galyardt, jonathan spring, leigh b. metcalf, angela horneman.
This report suggests seven key questions that managers and decision makers should ask about machine learning tools to effectively use those tools to solve cybersecurity problems.
Operational Test & Evaluation (OT&E) Roadmap for Cloud-Based Systems
September 2, 2019 • white paper, by john klein, christopher j. alberts, carol woody, charles m. wallen.
This paper provides an overview of the preparation and work that the AEC needs to perform to successfully transition the Army to cloud computing.
IEEE Computer Society/Software Engineering Institute Watts S. Humphrey Software Process Achievement Award 2018: U.S. Army Combat Capabilities Development Command Armaments Center, Fire Control Systems and Technology Directorate
August 1, 2019 • technical report, by victor a. elias (u.s. army ccdc armaments center, fire control systems and technology directorate).
This report presents a systemic approach to software development process improvement and its impact for the U.S. Army Combat Capabilities Development Command Armaments Center, Fire Control Systems and Technology Directorate …
Overview of Risks, Threats, and Vulnerabilities Faced in Moving to the Cloud
July 11, 2019 • technical report, by kelwyn pender, carrie lee (u.s. department of veteran affairs), donald faatz, timothy morrow.
This report, updated in October 2020, examines the changes to risks, threats, and vulnerabilities when applications are deployed to cloud services.
Automatically Detecting Technical Debt Discussions
June 24, 2019 • white paper, by robert nord, ipek ozkaya, zachary kurtz, raghvinder sangwan.
This study introduces (1) a dataset of expert labels of technical debt in developer comments and (2) a classifier trained on those labels.
Multi-Method Modeling and Analysis of the Cybersecurity Vulnerability Management Ecosystem
By allen d. householder, andrew p. moore.
This paper presents modeling and analysis of two critical foundational processes of the cybersecurity vulnerability management ecosystem using a combination of system dynamics and agent-based modeling techniques.
SCAIFE API Definition Beta Version 0.0.2 for Developers
June 14, 2019 • white paper, by ebonie mcneil, lori flynn.
This paper provides the SCAIFE API definition for beta version 0.0.2. SCAIFE is an architecture that supports static analysis alert classification and prioritization.
Creating xBD: A Dataset for Assessing Building Damage from Satellite Imagery
May 21, 2019 • white paper.
We present a preliminary report for xBD, a new large-scale dataset for the advancement of change detection and building damage assessment for humanitarian assistance and disaster recovery research.
Integration of Automated Static Analysis Alert Classification and Prioritization with Auditing Tools: Special Focus on SCALe
May 13, 2019 • technical report, by lori flynn, david svoboda, ebonie mcneil, zachary kurtz, derek leung, jiyeon lee (carnegie mellon university).
This report summarizes progress and plans for developing a system to perform automated classification and advanced prioritization of static analysis alerts.
Cybersecurity Career Paths and Progression
May 7, 2019 • white paper, by nicholas giruzzi, marie baker, dennis m. allen, melissa burns.
This paper explores the current state of cybersecurity careers, from the importance of early exposure, to methods of entry into the field, to career progression.
Cybersecurity Talent Identification and Assessment
By dennis m. allen, marie baker, christopher herr.
To help fill cybersecurity roles, this paper explores how organizations identify talent, discusses assessment capabilities, and provides recommendations on recruitment and talent evaluations.
Cybersecurity Careers of the Future
By dennis m. allen.
Using workforce data analysis, this paper identifies key cybersecurity skills the workforce needs to close the cybersecurity workforce gap.
A Targeted Improvement Plan for Service Continuity
April 8, 2019 • technical note, by philip a. scolieri, jeffrey pinckard, robert a. vrtis, andrew f. hoover, gavin jurecko.
Describes how an organization can leverage the results of a Cyber Resilience Review to create a Targeted Improvement Plan for its service continuity management.
Exploring the Use of Metrics for Software Assurance
March 7, 2019 • technical note, by carol woody, robert j. ellison, charlie ryan.
This report proposes measurements for each Software Assurance Framework (SAF) practice that a program can select to monitor and manage the progress it's making toward software assurance.
Common Sense Guide to Mitigating Insider Threats, Sixth Edition
February 27, 2019 • technical report, by sarah miller, tracy cassidy, michael c. theis, daniel l. costa, william r. claycomb, andrew p. moore, randall f. trzeciak.
The guide presents recommendations for mitigating insider threat based on the CERT Division's continued research and analysis of more than 1,500 insider threat cases.
An Approach for Integrating the Security Engineering Risk Analysis (SERA) Method with Threat Modeling
February 6, 2019 • white paper.
This report examines how cybersecurity data generated by a threat modeling method can be integrated into a mission assurance context using the SERA Method.
Infrastructure as Code: Final Report
January 28, 2019 • white paper, by doug reynolds, john klein.
This project explored the feasibility of infrastructure as code, developed prototype tools, populated a model of the deployment architecture, and automatically generated IaC scripts from the model.
Incident Management Capability Assessment
December 19, 2018 • technical report, by samuel j. perl, mark zajicek, robin ruefle, christopher j. alberts, pennie walters, carly l. huth, audrey j. dorofee, david mcintire.
The capabilities presented in this report provide a benchmark of incident management practices.
Program Manager's Guidebook for Software Assurance
December 14, 2018 • special report, by carol woody, timothy a. chick, kenneth nidiffer.
This guidebook helps program managers address the software assurance responsibilities critical in defending software-intensive systems, including mission threads and cybersecurity.
DoD Developer’s Guidebook for Software Assurance
By bill nichols, tom scanlon.
This guidebook helps software developers for DoD programs understand expectations for software assurance and standards and requirements that affect assurance.
Towards Improving CVSS
December 4, 2018 • white paper, by allen d. householder, jonathan spring, deana shick, art manion, eric hatleback.
This paper outlines challenges with the Common Vulnerability Scoring System (CVSS).
GHOSTS in the Machine: A Framework for Cyber-Warfare Exercise NPC Simulation
December 3, 2018 • technical report, by adam d. cerini, benjamin l. earl, thomas g. podnar, geoffrey b. dobson, luke j. osterritter, dustin d. updyke.
This report outlines how the GHOSTS (General HOSTS) framework helps create realism in cyber-warfare simulations and discusses how it was used in a case study.
Composing Effective Software Security Assurance Workflows
October 18, 2018 • technical report, by bill nichols, jim mchale, aaron volkmann, david sweeney, william snavely.
In an effort to determine how to make secure software development more cost effective, the SEI conducted a research study to empirically measure the effects that security tools—primarily automated static …
FedCLASS: A Case Study of Agile and Lean Practices in the Federal Government
October 5, 2018 • special report, by jeff davenport, tamara marshall-keim, linda parker gates, nanette brown.
This study reports the successes and challenges of using Agile and Lean methods and cloud-based technologies in a government software development environment.
Threat Modeling for Cyber-Physical System-of-Systems: Methods Evaluation
September 25, 2018 • white paper, by nataliya shevchenko, carol woody, brent frye.
This paper compares threat modeling methods for cyber-physical systems and recommends which methods (and combinations of methods) to use.
Software Architecture Publications
September 17, 2018 • white paper.
The SEI compiled this bibliography of publications about software architecture as a resource for information about system architecture throughout its lifecycle.
Practical Precise Taint-flow Static Analysis for Android App Sets
August 27, 2018 • white paper, by william klieber, lori flynn, william snavely, michael zheng.
This paper describes how to detect taint flow in Android app sets with a static analysis method that is fast and uses little disk and memory space.
Threat Modeling: A Summary of Available Methods
August 9, 2018 • white paper, by carol woody, nataliya shevchenko, tom scanlon, timothy a. chick, paige o'riordan.
This paper discusses twelve threat modeling methods from a variety of sources that target different parts of the development process.
Navigating the Insider Threat Tool Landscape: Low-Cost Technical Solutions to Jump-Start an Insider Threat Program
July 3, 2018 • white paper, by michael j. albrethsen, derrick spooner, daniel l. costa, george silowash.
This paper explores low cost technical solutions that can help organizations prevent, detect, and respond to insider incidents.
Blacklist Ecosystem Analysis: July - December 2017
April 19, 2018 • white paper, by leigh b. metcalf, eric hatleback.
This short report provides a summary of the various analyses of the blacklist ecosystem performed from July 1, 2017, through December 31, 2017.
ROI Analysis of the System Architecture Virtual Integration Initiative
April 12, 2018 • technical report, by jörgen hansson (university of skovde), steve helton (the boeing company), peter h. feiler.
This report presents an analysis of the economic effects of the System Architecture Virtual Integration approach on the development of software-reliant systems for aircraft compared to existing development paradigms.
Implementing DevOps Practices in Highly Regulated Environments
April 2, 2018 • white paper, by jose a. morales, aaron volkmann, hasan yasar.
In this paper, the authors layout the process with insights on performing a DevOps assessment in a highly regulated environment.
A Mapping of the Health Insurance Portability and Accountability Act (HIPAA) Security Rule to the Cyber Resilience Review (CRR)
March 29, 2018 • technical note, by robert a. vrtis, matthew trevors, greg porter (heinz college at carnegie mellon university).
This technical note describes mapping of HIPAA Security Rule requirements to practice questions found in the CERT Cyber Resilience Review for organizations' use in HIPAA compliance.
A Hybrid Threat Modeling Method
March 27, 2018 • technical note, by krishnamurthy vemuru (university of virginia), ole villadsen (carnegie mellon university), nancy r. mead, forrest shull.
Presents a hybrid method of threat modeling that attempts to meld the desirable features of three methods: Security Cards, Persona non Grata, and STRIDE.
Cyber Mutual Assistance Workshop Report
February 13, 2018 • special report, by katie c. stewart, jonathon monken (pjm interconnection), fernando maymi, phd (army cyber institute), dan bennett, phd (army cyber institute), dan huynh (army cyber institute), blake rhoades (army cyber institute), matt hutchison (army cyber institute), judy esquibel (army cyber institute), bill lawrence (north american electric reliability corporation).
The Army Cyber Institute hosted a Cyber Mutual Assistance Workshop to identify challenges in defining cyber requirements for Regional Mutual Assistance Groups.
Embedded Device Vulnerability Analysis Case Study Using Trommel
December 6, 2017 • white paper, by kyle o'meara, madison oliver.
This document provides security researchers with a repeatable methodology to produce more thorough and actionable results when analyzing embedded devices for vulnerabilities.
2017 Emerging Technology Domains Risk Survey
October 5, 2017 • technical report, by kyle o'meara, dan j. klinedinst, joel land.
This report describes our understanding of future technologies and helps US-CERT identify vulnerabilities, promote security practices, and understand vulnerability risk.
R-EACTR: A Framework for Designing Realistic Cyber Warfare Exercises
September 29, 2017 • technical report, by adam d. cerini, thomas g. podnar, geoffrey b. dobson, luke j. osterritter.
R-EACTR is a design framework for cyber warfare exercises. It ensures that designs of team-based exercises factor realism into all aspects of the participant experience.
Architecture Practices for Complex Contexts
September 26, 2017 • white paper.
This doctoral thesis, completed at Vrije Universiteit Amsterdam, focuses on software architecture practices for systems of systems, including data-intensive systems.
Defining a Progress Metric for CERT-RMM Improvement
September 8, 2017 • technical note, by david tobar, nader mehravari, gregory crabb (united states postal service).
Describes the Cybersecurity Program Progress Metric and how its implementation in a large, diverse U.S. national organization can serve to indicate progress toward improving cybersecurity and resilience capabilities.
Blacklist Ecosystem Analysis: January - June, 2017
August 22, 2017 • white paper, by eric hatleback, leigh b. metcalf.
This short report provides a summary of the various analyses of the blacklist ecosystem performed to date. It also appends the latest additional data to those analyses; the added data …
The CERT Guide to Coordinated Vulnerability Disclosure
August 15, 2017 • special report, by allen d. householder, art manion, christopher king, garret wassermann.
This guide provides an introduction to the key concepts, principles, and roles necessary to establish a successful Coordinated Vulnerability Disclosure process. It also provides insights into how CVD can go …
Systemic Vulnerabilities in Customer-Premises Equipment (CPE) Routers
July 11, 2017 • special report, by joel land.
This report describes a test framework that the CERT/CC developed to identify systemic and other vulnerabilities in CPE routers.
Department of Defense Software Factbook
July 11, 2017 • technical report, by david zubrow, christopher miller, rhonda brown, james mccurley, brad clark, mike zuccher (no affiliation).
In this report, the Software Engineering Institute has analyzed data related to DoD software projects and translated it into information that is frequently sought-after across the DoD.
DidFail: Coverage and Precision Enhancement
July 6, 2017 • technical report, by karan dwivedi (no affiliation), hongli yin (no affiliation), pranav bagree (no affiliation), xiaoxiao tang (no affiliation), william snavely, william klieber, lori flynn.
This report describes recent enhancements to Droid Intent Data Flow Analysis for Information Leakage (DidFail), the CERT static taint analyzer for sets of Android apps.
The Hard Choices Game Explained
June 26, 2017 • white paper, by erin lim, philippe kruchten, robert nord, nanette brown, ipek ozkaya.
The Hard Choices game is a simulation of the software development cycle meant to communicate the concepts of uncertainty, risk, and technical debt.
Federal Virtual Training Environment (FedVTE)
June 5, 2017 • white paper, by april galyardt, dominic a. ross, marie baker.
The Federal Virtual Training Environment (FedVTE) is an online, on‐demand training system containing cybersecurity and certification prep courses, at no cost to federal, state, and local government employees.
Blacklist Ecosystem Analysis: July – December 2016
June 1, 2017 • white paper.
This report provides a summary of various analyses of the blacklist ecosystem performed to date. It also appends the latest additional data to those analyses; the added data in this …
Guide to Software Architecture Tools
May 22, 2017 • white paper.
This document discusses tools and methods for analyzing the architecture, establishing requirements, evaluating the architecture, and defining the architecture.
System-of-Systems Software Architecture Evaluation
May 15, 2017 • white paper.
The SoS Architecture Evaluation Method provides an initial identification of SoS architectural risks and quality attribute inconsistencies across the constituent systems.
IEEE Computer Society/Software Engineering Institute Watts S. Humphrey Software Process Achievement Award
SEI-Certified PSP Developer Examination: Sample Questions
This page contains sample questions similar to those found on the PSP Developer examination.
IEEE Computer Society/Software Engineering Institute Watts S. Humphrey Software Process Achievement Award 2016: Raytheon Integrated Defense Systems
April 28, 2017 • technical report, by neal mackertich (raytheon), peter kraus (raytheon), kurt mittelstaedt (raytheon), brian foley (raytheon), dan bardsley (raytheon), kelli grimes (raytheon), mike nolan (raytheon).
The Raytheon Integrated Defense Systems DFSS team has been recognized with the 2016 Watts Humphrey Software Process Achievement Award.
IEEE Computer Society/Software Engineering Institute Watts S. Humphrey Software Process Achievement (SPA) Award 2016: Nationwide
April 13, 2017 • technical report, by will j.m. pohlman (nationwide it).
This report describes the 10-year history of Nationwide's software process improvement journey. Nationwide received the 2016 Watts Humphrey Software Process Achievement Award from the SEI and IEEE.
Prototype Software Assurance Framework (SAF): Introduction and Overview
April 6, 2017 • technical note.
In this report, the authors discuss the Software Assurance Framework (SAF), a collection of cybersecurity practices that programs can apply across the acquisition lifecycle and supply chain.
15 Tips for Preparing and Delivering a Great Presentation at SATURN
March 14, 2017 • white paper.
You submitted a proposal to SATURN, and it got accepted. Congratulations! Here are 15 tips for creating and giving a great presentation at SATURN.
The CISO Academy
February 23, 2017 • white paper, by pamela d. curtis, summer c. fowler, david tobar, david ulicne.
In this paper, the authors describe the project that led to the creation of the U.S. Postal Service's CISO Academy.
Agile Acquisition and Milestone Reviews
February 15, 2017 • white paper.
Acquisition & Management Concerns for Agile Use in Government Series - 4
Management and Contracting Practices for Agile Programs
Acquisition & Management Concerns for Agile Use in Government Series - 3
Estimating in Agile Acquisition
Acquisition & Management Concerns for Agile Use in Government Series - 5
Agile Development and DoD Acquisitions
Acquisition & Management Concerns for Agile Use in Government Series - 1
Agile Culture in the DoD
Acquisition & Management Concerns for Agile Use in Government Series - 2
Adopting Agile in DoD IT Acquisitions
Acquisition & Management Concerns for Agile Use in Government Series - 6
Supply Chain and Commercial-off-the-Shelf (COTS) Assurance
January 24, 2017 • white paper.
The Software Engineering Institute can help your organization apply techniques to reduce software supply chain risk.
COTS-Based Systems
This paper presents a summary of SEI commercial off-the-shelf (COTS) software documents and COTS tools.
Create a CSIRT
January 18, 2017 • white paper.
This white paper discusses the issues and decisions organizations should address when planning, implementing, and building a CSIRT.
Skills Needed When Staffing Your CSIRT
This white paper describes a set of skills that CSIRT staff members should have to provide basic incident-handling services.
CSIRT Frequently Asked Questions (FAQ)
This FAQ addresses CSIRTS, organizations responsible for receiving, reviewing, and responding to computer security incident reports and activity.
CERT-RMM Capability Appraisals
January 17, 2017 • white paper.
The white paper describe CERT-RMM appraisals and the benefits they offer organizations.
A Technical History of the SEI
January 6, 2017 • special report, by larry druffel.
This report chronicles the technical accomplishments of the Software Engineering Institute and its impact on the Department of Defense software community, as well as on the broader software engineering community.
SQUARE Frequently Asked Questions (FAQ)
January 5, 2017 • white paper.
This paper contains information about SQUARE, a process that helps organizations build security into the early stages of the software production lifecycle.
Common Sense Guide to Mitigating Insider Threats, Fifth Edition
December 21, 2016 • technical report, by tracy cassidy, michael j. albrethsen, michael c. theis, daniel l. costa, jason w. clark, andrew p. moore, randall f. trzeciak, matthew l. collins, jeremy r. strozer.
Presents recommendations for mitigating insider threat based on CERT's continued research and analysis of over 1,000 cases.
Architecture-Led Safety Process
By david p. gluch, julien delange, peter h. feiler, john mcgregor.
Architecture-Led Safety Analysis (ALSA) is a safety analysis method that uses early architecture knowledge to supplement traditional safety analysis techniques to identify faults as early as possible.
The Critical Role of Positive Incentives for Reducing Insider Threats
December 15, 2016 • technical report, by palma buttles-valdez, nathan m. vanhoudnos, samuel j. perl, tracy cassidy, andrew p. moore, daniel bauer, jennifer cowley, jeff savinda, allison parshall, matthew l. collins, elizabeth a. monaco, jamie l. moyes, denise m. rousseau (carnegie mellon university).
This report describes how positive incentives complement traditional practices to provide a better balance for organizations' insider threat programs.
Update 2016: Considerations for Using Agile in DoD Acquisition
December 14, 2016 • technical note, by alfred schenker, mary ann lapham, suzanne miller, ray c. williams, charles (bud) hammons, dan ward (dan ward consulting), daniel burton.
This report updates a 2010 technical note, addressing developments in commercial Agile practices as well as the Department of Defense (DoD) acquisition environment.
Scaling Agile Methods for Department of Defense Programs
December 13, 2016 • technical note, by suzanne miller, mary ann lapham, peter capell, eileen wrubel, will hayes.
This report discusses methods for scaling Agile processes to larger software development programs in the Department of Defense.
Low Cost Technical Solutions to Jump Start an Insider Threat Program
December 12, 2016 • technical note.
This technical note explores free and low cost technical solutions to help organizations prevent, detect, and respond to malicious insiders.
RFP Patterns and Techniques for Successful Agile Contracting
December 2, 2016 • special report, by larri ann rosser (raytheon intelligence information and services), steven martin (space and missile systems center), thomas e. friend (agile on target), greg howard (mitre), michael ryan (btas), john h. norton iii (raytheon integrated defense systems), keith korzec, peter capell, mary ann lapham.
This report discusses request-for-proposal patterns and techniques for successfully contracting a federal Agile project.
Ultra-Large-Scale Systems: Socio-adaptive Systems
December 1, 2016 • white paper, by mark h. klein, gabriel moreno, linda m. northrop, scott hissam, lutz wrage.
Ultra-large-scale systems are interdependent webs of software, people, policies, and economics. In socio-adaptive systems, humans and software interact as peers.
Cyber-Physical Systems
By david kyle, scott hissam, gabriel moreno, jeffrey hansen, john j. hudak, bjorn andersson, mark h. klein, dionisio de niz, sagar chaki.
Cyber-physical systems (CPS) integrate computational algorithms and physical components. SEI promotes the efficient development of high-confidence, distributed CPS.
Pervasive Mobile Computing
By edwin j. morris, grace lewis, james edmondson, william anderson, marc novakouski, jeff boleng, ben w. bradshaw, james root.
Pervasive mobile computing focuses on how soldiers and first responders can use smartphones, tablets, and other mobile/wearable devices at the tactical edge.
Predictability by Construction
By scott hissam, gabriel moreno, linda m. northrop, kurt c. wallnau, sagar chaki.
Predictability by construction (PBC) makes the behavior of a component-based system predictable before implementation, based on known properties of components.
Blacklist Ecosystem Analysis: January – June, 2016
Faa research project on system complexity effects on aircraft safety: testing the identified metrics, november 30, 2016 • white paper, by bill nichols, sarah sheard, michael d. konrad, charles weinstock.
This report describes a test of an algorithm for estimating the complexity of a safety argument.
FAA Research Project on System Complexity Effects on Aircraft Safety: Estimating Complexity of a Safety Argument
By charles weinstock, michael d. konrad, sarah sheard, bill nichols.
This report presents a formula for estimating the complexity of an avionics system and directly connects that complexity to the size of its safety argument.
FAA Research Project on System Complexity Effects on Aircraft Safety: Identifying the Impact of Complexity on Safety
By donald firesmith, sarah sheard, michael d. konrad, charles weinstock.
This report organizes our work on the impact of software complexity on aircraft safety by asking, “How can complexity complicate safety and, thus, certification?”
FAA Research Project on System Complexity Effects on Aircraft Safety: Candidate Complexity Metrics
By sarah sheard, bill nichols.
This special report identifies candidate measures of complexity for systems with embedded software that relate to safety, assurance, or both.
FAA Research Project on System Complexity Effects on Aircraft Safety: Literature Search to Define Complexity for Avionics Systems
By sarah sheard, michael d. konrad.
This special report describes the results of a literature review sampling what is known about complexity for application in the context of safety and assurance.
Seven Proposal-Writing Tips That Make Conference Program Committees Smile
By mike petock, bill pollak.
Writing a great session proposal for a conference is difficult. Here are seven tips for writing a session proposal that will make reviewers go from frown to smile.
Definition and Measurement of Complexity in the Context of Safety Assurance
October 27, 2016 • technical report, by bill nichols, charles weinstock, michael d. konrad, sarah sheard.
This report describes research to define complexity measures for avionics systems to help the FAA identify when systems are too complex to assure their safety.
Establishing Trusted Identities in Disconnected Edge Environments
October 27, 2016 • white paper, by dan j. klinedinst, sebastián echeverría, keegan m. williams.
he goal of this paper is to present a solution for establishing trusted identities in disconnected environments based on secure key generation and exchange in the field.
A Mapping of the Federal Financial Institutions Examination Council (FFIEC) Cybersecurity Assessment Tool (CAT) to the Cyber Resilience Review (CRR)
October 25, 2016 • technical note, by jeffrey pinckard, robert a. vrtis, michael rattigan.
To help financial organizations assess cyber resilience, we map FFIEC Cybersecurity Assessment Tool (CAT) statements to Cyber Resilience Review (CRR) questions.
Managing Third Party Risk in Financial Services Organizations: A Resilience-Based Approach
September 27, 2016 • white paper, by john haller, charles m. wallen.
A resilience-based approach can help financial services organizations to manage cybersecurity risks from outsourcing and comply with federal regulations.
Agile Development in Government: Myths, Monsters, and Fables
September 21, 2016 • white paper, by mary ann lapham, suzanne miller, david j. carney.
This volume is a reflection on attitudes toward Agile software development now current in the government workplace.
Striving for Effective Cyber Workforce Development
September 12, 2016 • white paper, by marie baker.
This paper reviews the issue of cyber awareness and identify efforts to combat this deficiency and concludes with strategies moving forward.
Segment-Fixed Priority Scheduling for Self-Suspending Real-Time Tasks
August 18, 2016 • technical report, by ragunathan (raj) rajkumar, junsung kim, jian-jia chen, wen-hung huang, geoffrey nelissen, bjorn andersson, dionisio de niz.
This report describes schedulability analyses and proposes segment-fixed priority scheduling for self-suspending tasks.
Creating Centralized Reporting for Microsoft Host Protection Technologies: The Enhanced Mitigation Experience Toolkit (EMET)
August 18, 2016 • technical note, by joseph tammariello, craig lewis.
This report describes how to set up a centralized reporting console for the Windows Enhanced Mitigation Experience Toolkit.
The QUELCE Method: Using Change Drivers to Estimate Program Costs
August 17, 2016 • technical note, by sarah sheard.
This technical note introduces Quantifying Uncertainty in Early Lifecycle Cost Estimation (QUELCE), a method for estimating program costs early in development.
Blacklist Ecosystem Analysis: 2016 Update
August 15, 2016 • white paper, by eric hatleback, leigh b. metcalf, jonathan spring.
This white paper, which is the latest in a series of regular updates, builds upon the analysis of blacklists presented in our 2013 and 2014 reports.
Architecture Fault Modeling and Analysis with the Error Model Annex, Version 2
June 22, 2016 • technical report, by peter h. feiler, julien delange, john j. hudak, david p. gluch.
This report describes the Error Model Annex, Version 2 (EMV2), notation for architecture fault modeling, which supports safety, reliability, and security analyses.
A Requirement Specification Language for AADL
By lutz wrage, julien delange, peter h. feiler.
This report describes a textual requirement specification language, called ReqSpec, for the Architecture Analysis & Design Language (AADL) and demonstrates its use.
DMPL: Programming and Verifying Distributed Mixed-Synchrony and Mixed-Critical Software
June 21, 2016 • technical report, by sagar chaki, david kyle.
DMPL is a language for programming distributed real-time, mixed-criticality software. It supports distributed systems in which each node executes a set of periodic real-time threads that are scheduled by priority …
Wireless Emergency Alerts Commercial Mobile Service Provider (CMSP) Cybersecurity Guidelines
June 9, 2016 • special report, by christopher j. alberts, carol woody, audrey j. dorofee.
This report provides members of the Commercial Mobile Service Provider (CMSP) community with practical guidance for better managing cybersecurity risk exposure, based on an SEI study of the CMSP element …
Report Writer and Security Requirements Finder: User and Admin Manuals
June 7, 2016 • special report, by anand sankalp (carnegie mellon university), gupta anurag (carnegie mellon), priyam swati (carnegie mellon university), yaobin wen (carnegie mellon university), walid el baroni (carnegie mellon university), nancy r. mead.
This report presents instructions for using the Malware-driven Overlooked Requirements (MORE) website applications.
Applying the Goal-Question-Indicator-Metric (GQIM) Method to Perform Military Situational Analysis
May 23, 2016 • technical note, by douglas gray.
This report describes how to use the goal-question-indicator-metric method in tandem with the military METT-TC method (mission, enemy, time, terrain, troops available, and civil-military considerations).
An Insider Threat Indicator Ontology
May 10, 2016 • technical report, by matthew l. collins, samuel j. perl, michael j. albrethsen, derrick spooner, daniel l. costa, george silowash.
This report presents an ontology for insider threat indicators, describes how the ontology was developed, and outlines the process by which it was validated.
Using Honeynets and the Diamond Model for ICS Threat Analysis
May 6, 2016 • technical report, by deana shick, kyle o'meara, john kotheimer.
This report presents an approach to analyzing approximately 16 gigabytes of full packet capture data collected from an industrial control system honeynet—a network of seemingly vulnerable machines designed to lure …
April 19, 2016 • White Paper
This report introduces the Quantifying Uncertainty in Early Lifecycle Cost Estimation (QUELCE) method for estimating program costs early in a development lifecycle.
A Unique Approach to Threat Analysis Mapping: A Malware-Centric Methodology
April 19, 2016 • technical report, by kyle o'meara, deana shick.
As they constantly change network infrastructure, adversaries consistently use and update their tools. This report presents a way for researchers to begin threat analysis with those tools rather than with …
On Board Diagnostics: Risks and Vulnerabilities of the Connected Vehicle
April 13, 2016 • white paper, by christopher king, dan j. klinedinst.
This report describes cybersecurity risks and vulnerabilities in modern connected vehicles.
2016 Emerging Technology Domains Risk Survey
April 8, 2016 • technical report, by todd lewellen, dan j. klinedinst, christopher king, garret wassermann.
This 2016 report provides a snapshot of our current understanding of future technologies.
Malware Capability Development Patterns Respond to Defenses: Two Case Studies
March 7, 2016 • white paper, by ed stoner, deana shick, jonathan spring, kyle o'meara.
In this paper, the authors describe their analysis of two case studies to outline the relationship between adversaries and network defenders.
Cyber-Foraging for Improving Survivability of Mobile Systems
February 18, 2016 • technical report, by sebastián echeverría, grace lewis, james root, ben w. bradshaw.
This report presents an architecture and experimental results that demonstrate that cyber-foraging using tactical cloudlets increases the survivability of mobile systems.
CERT-RMM Version 1.2 Release Notes
February 14, 2016 • white paper.
This document contains the release notes for CERT-RMM Version 1.2, released February 2014.
DoD Software Factbook
December 31, 2015 • white paper, by david zubrow, james mccurley, brad clark.
This DoD Factbook is an initial analysis of software engineering data from the perspective of policy and management questions about software projects.
Architecture-Led Safety Analysis of the Joint Multi-Role (JMR) Joint Common Architecture (JCA) Demonstration System
December 31, 2015 • special report, by peter h. feiler.
This report summarizes an architecture-led safety analysis of the aircraft-survivability situation-awareness system for the Joint Multi-Role vertical lift program.
Requirements and Architecture Specification of the Joint Multi-Role (JMR) Joint Common Architecture (JCA) Demonstration System
This report describes a method for capturing information from requirements documents in AADL and the draft Requirement Definition & Analysis Language Annex.
Potential System Integration Issues in the Joint Multi-Role (JMR) Joint Common Architecture (JCA) Demonstration System
By john j. hudak, peter h. feiler.
This report describes a method for capturing information from requirements documents in AADL to identify potential integration problems early in system development.
Extending AADL for Security Design Assurance of Cyber-Physical Systems
December 16, 2015 • technical report, by allen d. householder, rick kazman, john j. hudak, robert j. ellison, carol woody.
This report demonstrates the viability and limitations of using the Architecture Analysis and Design Language (AADL) through an extended example that allows for specifying and analyzing the security properties of …
Cybersecurity Considerations for Vehicles
December 10, 2015 • white paper, by mark sherman, jens palluch (method park).
In this paper the authors discuss the number of ECUs and software in modern vehicles and the need for cybersecurity to include vehicles.
Analytic Approaches to Detect Insider Threats
December 9, 2015 • white paper.
This paper identifies steps that organizations can use to enhance their security posture to detect potential insider threats.
Intelligence Preparation for Operational Resilience (IPOR)
December 7, 2015 • special report.
The author describes Intelligence Preparation for Operational Resilience (IPOR), a framework for preparing intelligence that complements commonly used intelligence frameworks such as Intelligence Preparation of the Battlefield (IPB).
Evaluating and Mitigating the Impact of Complexity in Software Models
December 3, 2015 • technical report, by min-young nam, john j. hudak, julien delange, jim mchale, bill nichols.
This report defines software complexity, metrics for complexity, and the effects of complexity on cost and presents an analysis tool to measure complexity in models.
Cyber + Culture Early Warning Study
November 30, 2015 • special report, by char sample.
This study was designed to profile cyber actors, and to examine the time interval between cyber and kinetic events in order to gain greater insights into nation-state cyber responses to …
Effective Insider Threat Programs: Understanding and Avoiding Potential Pitfalls
October 16, 2015 • white paper, by matthew l. collins, randall f. trzeciak, andrew p. moore, william e. novak, michael c. theis.
In this paper, the authors describe the potential ways an insider threat program (InTP) could go wrong and engage the community to discuss its concerns.
Structuring the Chief Information Security Officer Organization
October 6, 2015 • technical note, by pamela d. curtis, gregory crabb (united states postal service), brendan fitzpatrick, david tobar, nader mehravari, julia h. allen.
The authors describe how they defined a CISO team structure and functions for a national organization using sources such as CISOs, policies, and lessons learned from cybersecurity incidents.
Improving Federal Cybersecurity Governance Through Data-Driven Decision Making and Execution
September 16, 2015 • technical report, by robert w. stoddard, julia h. allen, anne connell, c. aaron cois, douglas gray, michael riley (veris group), brian d. wisniewski, erik ebel (veris group), william gulley (veris group), marie vaughn (veris group).
This technical report focuses on cybersecurity at the indirect, strategic level. It discusses how cybersecurity decision makers at the tactical or implementation level can establish a supportive contextual environment to …
Secure Coding Analysis of an AADL Code Generator's Runtime System
September 12, 2015 • white paper, by david keaton.
This paper describes a secure coding analysis of the PolyORB-HI-C runtime system used by C language code output from the Ocarina AADL code generator.
Contracting for Agile Software Development in the Department of Defense: An Introduction
August 18, 2015 • technical note, by eileen wrubel, jon gross.
This technical note addresses effective contracting for Agile software development and offers a primer on Agile based on a contracting officer's goals.
CND Equities Strategy
July 22, 2015 • white paper, by jonathan spring, ed stoner.
In this paper, the authors discuss strategies for successful computer network defense (CND) based on considering the adversaries' responses.
Comments on Bureau of Industry and Security (BIS) Proposed Rule Regarding Wassenaar Arrangement 2013 Plenary Agreements Implementation for Intrusion and Surveillance Items
By art manion, allen d. householder.
In this paper, CERT researchers comment on the proposed rule, Wassenaar Arrangement 2013 Plenary Agreements Implementation: Intrusion and Surveillance Items.
Enabling Incremental Iterative Development at Scale: Quality Attribute Refinement and Allocation in Practice
June 4, 2015 • technical report, by neil ernst, robert nord, stephany bellomo, ipek ozkaya.
This report describes industry practices used to develop business capabilities and suggests approaches to enable large-scale iterative development, or agile at scale.
State of Practice Report: Essential Technical and Nontechnical Issues Related to Designing SoS Platform Architectures
May 13, 2015 • technical report, by john klein, sholom g. cohen.
This report analyzes the state of the practice in system-of-systems (SoS) development, based on 12 interviews of leading SoS developers in the DoD and industry.
Emerging Technology Domains Risk Survey
April 30, 2015 • technical note, by andrew o. mellinger, christopher king, jonathan chu.
This report provides a snapshot in time of our current understanding of future technologies.
SCALe Analysis of JasPer Codebase
April 1, 2015 • white paper, by david svoboda.
In this paper, David Svoboda provides the findings of a SCALe audit on a codebase.
Model-Driven Engineering: Automatic Code Generation and Beyond
March 25, 2015 • technical note, by harry l. levinson, john klein, jay marchetti.
This report offers guidance on selecting, analyzing, and evaluating model-driven engineering tools for automatic code generation in acquired systems.
Defining a Maturity Scale for Governing Operational Resilience
March 19, 2015 • technical note, by julia h. allen, katie c. stewart, lisa r. young, michelle a. valdez, audrey j. dorofee.
Governing operational resilience requires the appropriate level of sponsorship, a commitment to strategic planning that includes resilience objectives, and proper oversight of operational resilience activities.
SEI SPRUCE Project: Curating Recommended Practices for Software Producibility
March 16, 2015 • white paper, by bill pollak, michael d. konrad, mike petock, tamara marshall-keim, b. craig meyers, gerald w. miller.
This paper describes the Systems and Software Producibility Collaboration Environment (SPRUCE) project and the resulting recommended practices on five software topics.
Improving Quality Using Architecture Fault Analysis with Confidence Arguments
March 10, 2015 • technical report, by peter h. feiler, julien delange, charles weinstock, john b. goodenough, neil ernst, ari z. klein.
The case study shows that by combining an analytical approach with confidence maps, we can present a structured argument that system requirements have been met and problems in the design …
Making DidFail Succeed: Enhancing the CERT Static Taint Analyzer for Android App Sets
March 4, 2015 • technical report, by william snavely, jonathan burket, jonathan lim, wei shen, lori flynn, william klieber.
In this report, the authors describe how the DidFail tool was enhanced to improve its effectiveness.
Eliminative Argumentation: A Basis for Arguing Confidence in System Properties
February 25, 2015 • technical report, by john b. goodenough, charles weinstock, ari z. klein.
This report defines the concept of eliminative argumentation and provides a basis for assessing how much confidence one should have in an assurance case argument.
A Proven Method for Meeting Export Control Objectives in Postal and Shipping Sectors
February 10, 2015 • technical note, by gregory crabb (united states postal service), pamela d. curtis, julia h. allen, nader mehravari.
This report describes how the CERT-RMM enabled the USPIS to implement an innovative approach for achieving complex international mail export control objectives.
Measuring What Matters Workshop Report
February 9, 2015 • technical note, by katie c. stewart, julia h. allen, lisa r. young, michelle a. valdez.
This report describes the inaugural Measuring What Matters Workshop conducted in November 2014, and the team's experiences in planning and executing the workshop and identifying improvements for future offerings.
A Dynamic Model of Sustainment Investment
February 5, 2015 • technical report, by sarah sheard, mike phillips, andrew p. moore, robert ferguson.
This paper describes a dynamic sustainment model that shows how budgeting, allocation of resources, mission performance, and strategic planning are interrelated and how they affect each other over time.
Cybersecurity Assurance
January 15, 2015 • white paper.
This paper describes the SEI research and solutions that help organizations gain justified confidence in their cybersecurity posture.
Blacklist Ecosystem Analysis Update: 2014
January 7, 2015 • white paper, by leigh b. metcalf, jonathan spring.
This white paper compares the contents of 85 different Internet blacklists to discover patterns in shared entries.
Predicting Software Assurance Using Quality and Reliability Measures
December 22, 2014 • technical note, by bill nichols, carol woody, robert j. ellison.
In this report, the authors discuss how a combination of software development and quality techniques can improve software security.
Regional Use of Social Networking Tools
December 17, 2014 • technical report, by kate meeuf.
This paper explores the regional use of social networking services (SNSs) to determine if participation with a subset of SNSs can be applied to identify a user's country of origin.
Domain Parking: Not as Malicious as Expected
December 10, 2014 • white paper, by jonathan spring, leigh b. metcalf.
In this paper we discuss scalable detection methods for domain names parking on reserved IP address space, and then using this data set, evaluate whether this behavior appears to be …
Pattern-Based Design of Insider Threat Programs
December 9, 2014 • technical note, by robin ruefle, dave mundie, andrew p. moore, david mcintire, matthew l. collins.
In this report, the authors describe a pattern-based approach to designing insider threat programs that could provide a better defense against insider threats.
Introduction to the Security Engineering Risk Analysis (SERA) Framework
December 4, 2014 • technical note, by audrey j. dorofee, christopher j. alberts, carol woody.
This report introduces the SERA Framework, a model-based approach for analyzing complex security risks in software-reliant systems and systems of systems early in the lifecycle.
Using Malware Analysis to Tailor SQUARE for Mobile Platforms
November 18, 2014 • technical note, by nancy r. mead, gregory paul alice.
This technical note explores the development of security requirements for the K-9 Mail application, an open source email client for the Android operating system.
A Method for Aligning Acquisition Strategies and Software Architectures
October 29, 2014 • technical note, by david j. carney, cecilia albert, patrick r. place, lisa brownsword.
This report describes the third year of the SEI's research into aligning acquisition strategies and software architecture.
Agile Methods in Air Force Sustainment: Status and Outlook
October 23, 2014 • technical note, by mary ann lapham, eileen wrubel, stephen beck, michael s. bandor, colleen regan.
This paper examines using Agile techniques in the software sustainment arena—specifically Air Force programs. The intended audience is the staff of DoD programs and related personnel who intend to use …
Development of an Intellectual Property Strategy: Research Notes to Support Department of Defense Programs
October 14, 2014 • special report, by charlene gross.
This report is intended to help program managers understand categories of intellectual property, various intellectual property challenges, and approaches to assessing the license rights that the program needs for long-term …
AADL Fault Modeling and Analysis Within an ARP4761 Safety Assessment
October 10, 2014 • technical report, by david p. gluch, peter h. feiler, julien delange, john j. hudak.
This report describes how the Architecture Analysis and Design Language (AADL) Error Model Annex supports the safety-assessment methods in SAE Standard ARP4761.
CERT Resilience Management Model—Mail-Specific Process Areas: International Mail Transportation (Version 1.0)
September 18, 2014 • technical note, by pamela d. curtis, gregory crabb (united states postal service), sam lin, dawn wilkes, nader mehravari, julia h. allen.
This report describes a new process area that ensures that international mail is transported according to Universal Postal Union standards.
CERT Resilience Management Model—Mail-Specific Process Areas: Mail Revenue Assurance (Version 1.0)
By julia h. allen, nader mehravari, david w. white, gregory crabb (united states postal service), pamela d. curtis.
This report describes a new process area that ensures that the USPS is compensated for mail that is accepted, transported, and delivered.
CERT Resilience Management Model—Mail-Specific Process Areas: Mail Induction (Version 1.0)
By pamela d. curtis, gregory crabb (united states postal service), david w. white, nader mehravari, julia h. allen.
This report describes a new process area that ensures that mail is inducted into the U.S. domestic mail stream according to USPS standards and requirements.
Smart Collection and Storage Method for Network Traffic Data
September 15, 2014 • technical report, by angela horneman, nathan dell.
This report discusses considerations and decisions to be made when designing a tiered network data storage solution.
A Systematic Approach for Assessing Workforce Readiness
August 18, 2014 • technical report, by david mcintire, christopher j. alberts.
In this report, the authors present the Competency Lifecycle Roadmap and the readiness test development method, both used to maintain workforce readiness.
Assuring Software Reliability
August 15, 2014 • special report, by robert j. ellison.
This report describes ways to incorporate the analysis of the potential impact of software failures--regardless of their cause--into development and acquisition practices through the use of software assurance.
Patterns and Practices for Future Architectures
August 15, 2014 • technical note, by eric werner, scott mcmillan, jonathan chu.
This report discusses best practices and patterns that will make high-performance graph analytics on new and emerging architectures more accessible to users.
Abuse of Customer Premise Equipment and Recommended Actions
August 7, 2014 • white paper, by jonathan spring, paul vixie, chris hallenbeck.
In this paper, the authors provide recommendations for addressing problems related to poor management of Consumer Premise Equipment (CPE).
Performance of Compiler-Assisted Memory Safety Checking
July 31, 2014 • technical note, by david keaton, robert c. seacord.
This technical note describes the criteria for deploying a compiler-based memory safety checking tool and the performance that can be achieved with two such tools whose source code is freely …
Unintentional Insider Threats: A Review of Phishing and Malware Incidents by Economic Sector
July 18, 2014 • technical note, by cert insider threat team.
This report analyzes unintentional insider threat cases of phishing and other social engineering attacks involving malware.
Evaluation of the Applicability of HTML5 for Mobile Applications in Resource-Constrained Edge Environments
July 2, 2014 • technical note, by grace lewis, bryan yan (carnegie mellon university – institute for software research).
This technical note presents an analysis of the feasibility of using HTML5 for developing mobile applications, for "edge" environments where resources and connectivity are uncertain, such as in battlefield or …
Agile Software Teams: How They Engage with Systems Engineering on DoD Acquisition Programs
July 1, 2014 • technical note, by mary ann lapham, suzanne miller, timothy a. chick, eileen wrubel.
This technical note addresses issues with Agile software teams engaging systems engineering functions in developing and acquiring software-reliant systems.
Improving the Automated Detection and Analysis of Secure Coding Violations
June 27, 2014 • technical note, by daniel plakosh, robert c. seacord, robert w. stoddard, david svoboda, david zubrow.
This technical note describes the accuracy analysis of the Source Code Analysis Laboratory (SCALe) tools and the characteristics of flagged coding violations.
CERT® Resilience Management Model (CERT®-RMM) V1.1: NIST Special Publication Crosswalk Version 2
June 11, 2014 • technical note, by lisa r. young, kevin g. partridge, mary popeck.
This update to Version 1 of this same title (CMU/SEI-2011-TN-028) maps CERT-RMM process areas to certain NIST 800-series special publications.
The Business Case for Systems Engineering: Comparison of Defense Domain and Non-defense Projects
June 10, 2014 • special report, by dennis goldenson, joseph p. elm.
This report analyzes differences in systems-engineering activities for defense and non-defense projects and finds differences in both deployment and effectiveness.
Job Analysis Results for Malicious-Code Reverse Engineers: A Case Study
June 3, 2014 • technical report, by jennifer cowley.
This report describes individual and team factors that enable, encumber, or halt the development of malicious-code reverse engineering expertise.
An Introduction to the Mission Risk Diagnostic for Incident Management Capabilities (MRD-IMC)
May 30, 2014 • technical note, by christopher j. alberts, robin ruefle, mark zajicek, audrey j. dorofee.
The Mission Risk Diagnostic for Incident Management Capabilities revises the Incident Management Mission Diagnostic Method with updated and expanded drivers.
A Taxonomy of Operational Cyber Security Risks Version 2
May 21, 2014 • technical note, by lisa r. young, mary popeck, james j. cebula.
This second version of the 2010 report presents a taxonomy of operational cyber security risks and harmonizes it with other risk and security activities.
An Evaluation of A-SQUARE for COTS Acquisition
May 13, 2014 • technical note, by nancy r. mead, sidhartha mani.
An evaluation of the effectiveness of Software Quality Requirements Engineering for Acquisition (A-SQUARE) in a project to select a COTS product for the advanced metering infrastructure of a smart grid.
Investigating Advanced Persistent Threat 1 (APT1)
May 12, 2014 • technical report, by deana shick, angela horneman.
This report analyzes unclassified data sets in an attempt to understand APT1's middle infrastructure.
Precise Static Analysis of Taint Flow for Android Application Sets
May 9, 2014 • white paper, by amar s. bhosale (no affiliation).
This thesis describes a static taint analysis for Android that combines the FlowDroid and Epicc analyses to track inter- and intra-component data flow.
Data-Driven Software Assurance: A Research Study
May 9, 2014 • technical report, by julia l. mullaney, michael f. orlando, erin harper, michael d. konrad, art manion, bill nichols, andrew p. moore.
In 2012, Software Engineering Institute (SEI) researchers began investigating vulnerabilities reported to the SEI's CERT Division. A research project was launched to investigate design-related vulnerabilities and quantify their effects.
ALTernatives to Signatures (ALTS)
April 30, 2014 • white paper, by george jones, john stogoski.
This paper presents the results of a study of non-signature-based approaches to detecting malicious activity in computer network traffic.
Potential Use of Agile Methods in Selected DoD Acquisitions: Requirements Development and Management
April 29, 2014 • technical note, by david j. carney, kenneth nidiffer, suzanne miller.
This report explores issues that practitioners in the field who are actively adopting Agile methods have identified in our interviews about their experience in defining and managing requirements.
The Readiness & Fit Analysis: Is Your Organization Ready for Agile?
April 28, 2014 • white paper, by suzanne miller.
This paper summarizes the Readiness & Fit Analysis and describes its extension to support risk identification for organizations that are adopting agile methods.
International Implementation of Best Practices for Mitigating Insider Threat: Analyses for India and Germany
April 16, 2014 • technical report, by randall f. trzeciak, george silowash, lori flynn, michael c. theis, tracy cassidy, palma buttles-valdez, carly l. huth, travis wright (carnegie mellon university, master of science in information security policy and management program).
This report analyzes insider threat mitigation in India and Germany, using the new framework for international cybersecurity analysis described in the paper titled “Best Practices Against Insider Threats in All …
Wireless Emergency Alerts (WEA) Cybersecurity Risk Management Strategy for Alert Originators
March 31, 2014 • special report, by the wea project team.
In this report, the authors describe a cybersecurity risk management (CSRM) strategy that alert originators can use throughout WEA adoption, operations, and sustainment, as well as a set of governance …
Maximizing Trust in the Wireless Emergency Alerts (WEA) Service
February 28, 2014 • special report, by carol woody, robert j. ellison.
This 2014 report presents recommendations for stakeholders of the Wireless Emergency Alerts (WEA) service that resulted from the development of two trust models, focusing on how to increase both alert …
Wireless Emergency Alerts: Trust Model Simulations
February 26, 2014 • special report, by timothy morrow, joseph p. elm, robert w. stoddard.
This report presents four types of simulations run on the public trust model and the alert originator trust model developed for the Wireless Emergency Alerts (WEA) service, focusing on how …
Commercial Mobile Alert Service (CMAS) Alerting Pipeline Taxonomy
February 24, 2014 • technical report.
This report presents the Commercial Mobile Alert Service (CMAS) Alerting Pipeline Taxonomy, a hierarchical classification that encompasses four elements of the alerting pipeline, to help stakeholders understand and reason about …
Best Practices in Wireless Emergency Alerts
February 19, 2014 • special report, by elizabeth trocki stark (sra international, inc.), jennifer lavan (sra international, inc.), robert j. ellison, john mcgregor, tamara marshall-keim, rita c. creel, carol woody, christopher j. alberts, joseph p. elm.
This report presents four best practices for the Wireless Emergency Alerts (WEA) service, including implementing WEA in a local jurisdiction, training emergency staff in using WEA, cross-jurisdictional governance of WEA, …
Study of Integration Strategy Considerations for Wireless Emergency Alerts
This report identifies key challenges and offers recommendations for alert originators navigating the process of adopting and integrating the Wireless Emergency Alerts (WEA) service into their emergency management systems.
Results in Relating Quality Attributes to Acquisition Strategies
February 4, 2014 • technical note, by lisa brownsword, cecilia albert, patrick r. place, david j. carney.
This technical note describes the second phase of a study that focuses on the relationships between software architecture and acquisition strategy -- more specifically, their alignment or misalignment.
Agile Metrics: Progress Monitoring of Agile Contractors
January 27, 2014 • technical note, by timothy a. chick, eileen wrubel, will hayes, mary ann lapham, suzanne miller.
This technical note offers a reference for those working to oversee software development on the acquisition of major systems from developers using Agile methods.
Agile Methods and Request for Change (RFC): Observations from DoD Acquisition Programs
January 24, 2014 • technical note, by mary ann lapham, eileen wrubel, michael s. bandor.
This technical note looks at the evaluation and negotiation of technical proposals that reflect iterative development approaches that in turn leverage Agile methods.
Unintentional Insider Threats: Social Engineering
January 21, 2014 • technical note, by cert insider threat center.
In this report, the authors explore the unintentional insider threat (UIT) that derives from social engineering.
Improving the Security and Resilience of U.S. Postal Service Mail Products and Services Using the CERT® Resilience Management Model
January 17, 2014 • technical note.
In this report, the authors describe how to improve the resilience of U.S. Postal Service products and services
A Proven Method for Identifying Security Gaps in International Postal and Transportation Critical Infrastructure
By nader mehravari, julia h. allen, pamela d. curtis, gregory crabb (united states postal service).
In this report, the authors describe a method of identifying physical security gaps in international mail processing centers and similar facilities.
Cloud Service Provider Methods for Managing Insider Threats: Analysis Phase II, Expanded Analysis and Recommendations
January 8, 2014 • technical note, by chas difatta (no affiliation), greg porter (heinz college at carnegie mellon university), lori flynn.
In this report, the authors discuss the countermeasures that cloud service providers use and how they understand the risks posed by insiders.
TSP Symposium 2013 Proceedings
January 8, 2014 • special report, by sergio cardona (universidad del quindío), leticia pérez (universidad de la república), rafael rincón (universidad eafit), joão pascoal faria (university of porto), mushtaq raza (university of porto), pedro c. henriques (strongstep – innovation in software quality), diego vallespir (universidad de la república), fernanda grazioli (universidad de la república), silvana moreno (universidad de la república), bill nichols, jim mchale.
This special report contains proceedings of the 2013 TSP Symposium. The conference theme was “When Software Really Matters,” which explored the idea that when product quality is critical, high-quality practices …
Understanding Patterns for System-of-Systems Integration
December 17, 2013 • technical report, by klaus schmid, claus nielsen (no affiliation), rick kazman.
This report discusses how a software architect can address the system-of-systems integration challenge from an architectural perspective.
Foundations for Software Assurance
December 16, 2013 • white paper, by carol woody, nancy r. mead, dan shoemaker (university of detroit mercy).
In this paper, the authors highlight efforts to address the principles of software assurance and its educational curriculum.
The Topological Properties of the Local Clustering Coefficient
December 9, 2013 • white paper, by leigh b. metcalf.
In this paper, Leigh Metcalf examines the local clustering coefficient for and provides a new formula to generate the local clustering coefficient.
Using Software Development Tools and Practices in Acquisition
December 3, 2013 • technical note, by harry l. levinson, richard librizzi.
This technical note provides an introduction to key automation and analysis techniques.
Spotlight On: Programmers as Malicious Insiders–Updated and Revised
December 2, 2013 • white paper, by andrew p. moore, randall f. trzeciak, dawn cappelli, matthew l. collins, thomas c. caron (john heinz iii college, school of information systems management, carnegie mellon university).
In this paper, the authors describe the who, what, when, where, and how of attacks by insiders using programming techniques and includes case examples.
Software Assurance Measurement – State of the Practice
November 29, 2013 • technical note, by dan shoemaker (university of detroit mercy), nancy r. mead.
In this report, the authors describe the current state of the practice and emerging trends in software assurance measurement.
A Defect Prioritization Method Based on the Risk Priority Number
November 26, 2013 • white paper, by will hayes, julie b. cohen, robert ferguson.
This paper describes a technique that helps organizations address and resolve conflicting views and create a better value system for defining releases.
Agile Security - Review of Current Research and Pilot Usage
November 21, 2013 • white paper, by carol woody.
This white paper was produced to focus attention on the opportunities and challenges for embedding information assurance considerations into Agile development and acquisition.
Cloud Service Provider Methods for Managing Insider Threats: Analysis Phase I
November 15, 2013 • technical note, by greg porter (heinz college at carnegie mellon university).
In this report, Greg Porter documents preliminary findings from interviews with cloud service providers on their insider threat controls.
Mobile SCALe: Rules and Analysis for Secure Java and Android Coding
November 8, 2013 • technical report, by david svoboda, dean sutherland, william klieber, lori flynn, limin jia (carnegie mellon university, department of electrical and computer engineering), lujo bauer (carnegie mellon university, department of electrical and computer engineering), fred long.
In this report, the authors describe Android secure coding rules, guidelines, and static analysis developed as part of the Mobile SCALe project.
Advancing Cybersecurity Capability Measurement Using the CERT-RMM Maturity Indicator Level Scale
November 7, 2013 • technical note, by richard a. caralli, matthew j. butkovic.
In this report, the authors review the specific and generic goals and practices in CERT-RMM to determine if a better scale could be developed.
CERT® Resilience Management Model (CERT®-RMM) V1.1: NIST Special Publication 800-66 Crosswalk
October 28, 2013 • technical note, by ma-nyahn kromah (sungard availability services), lisa r. young.
In this report, the authors map CERT-RMM process areas to key activities in NIST Special Publication 800-66 Revision 1.
Passive Detection of Misbehaving Name Servers
October 4, 2013 • technical report.
In this report, the authors explore name-server flux and two types of data that can reveal it.
Insider Threat Control: Using Plagiarism Detection Algorithms to Prevent Data Exfiltration in Near Real Time
October 3, 2013 • technical note, by todd lewellen, daniel l. costa, george silowash.
In this report, the authors describe how an insider threat control can monitor an organization's web request traffic for text-based data exfiltration.
Introduction to the Mission Thread Workshop
October 1, 2013 • technical report, by william wood, michael j. gagliardi, timothy morrow.
This report introduces the Mission Thread Workshop, a method for understanding architectural and engineering considerations for developing and sustaining systems of systems. It describes the three phases of the workshop …
Parallel Worlds: Agile and Waterfall Differences and Similarities
October 1, 2013 • technical note, by ipek ozkaya, suzanne miller, mary ann lapham, timothy a. chick, steve palmquist.
This report helps readers understand Agile. The report assembles terms and concepts from both the traditional world of waterfall-based development and the Agile environment to show the many similarities and …
Everything You Wanted to Know About Blacklists But Were Afraid to Ask
September 30, 2013 • white paper.
This document compares the contents of 25 different common public-internet blacklists in order to discover any patterns in the shared entries.
Roadmap to Software Assurance Competency
September 23, 2013 • white paper.
This white paper describes the Software Assurance (SwA) Core Body of Knowledge and SwA competency levels.
TSP Performance and Capability Evaluation (PACE): Customer Guide
September 1, 2013 • special report, by mark kasunic, bill nichols, timothy a. chick.
This guide describes the evaluation process and lists the steps organizations and programs must complete to earn a TSP-PACE certification.
TSP Performance and Capability Evaluation (PACE): Team Preparedness Guide
By timothy a. chick, bill nichols, mark kasunic.
This document describes the TSP team data that teams normally produce and that are required as input to the TSP-PACE process.
Best Practices Against Insider Threats in All Nations
August 27, 2013 • technical note, by carly l. huth, palma buttles-valdez, lori flynn, randall f. trzeciak.
In this report, the authors summarize best practices for mitigating insider threats in international contexts.
The Role of Computer Security Incident Response Teams in the Software Development Life Cycle
August 20, 2013 • white paper, by robin ruefle.
In this paper, Robin Ruefle describes how an incident management can provide input to the software development process.
State of Cyber Workforce Development
August 15, 2013 • white paper.
This paper summarizes the current posture of the cyber workforce and several initiatives designed to strengthen, grow, and retain cybersecurity professionals.
Training and Awareness
August 7, 2013 • white paper, by carol sledge, ken van wyk (no affiliation).
In this paper, the authors provide guidance on training and awareness opportunities in the field of software security.
Evidence of Assurance: Laying the Foundation for a Credible Security Case
By howard f. lipson, charles weinstock.
In this paper, the authors provide examples of several of the kinds of evidence that can contribute to a security case.
Security and Project Management
August 6, 2013 • white paper.
In this paper, Robert Ellison explains what project managers should consider because they relate to security needs.
An Evaluation of Cost-Benefit Using Security Requirements Prioritization Methods
August 5, 2013 • white paper, by travis christian, nancy r. mead.
In this paper, the authors provide background information on penetration testing processes and practices.
Unintentional Insider Threats: A Foundational Study
August 1, 2013 • technical note.
In this report, the CERT Insider Threat team examines unintentional insider threat (UIT), a largely unrecognized problem.
Teaching Security Requirements Engineering Using SQUARE
July 31, 2013 • white paper, by nancy r. mead, dan shoemaker (university of detroit mercy), jeff ingalsbe (university of detroit mercy).
In this paper, the authors detail the validation of a teaching model for security requirements engineering that ensures that security is built into software.
Trustworthy Composition: The System Is Not Always the Sum of Its Parts
In this paper, Robert Ellison surveys several profound technical problems faced by practitioners assembling and integrating secure and survivable systems.
Development of a Master of Software Assurance Reference Curriculum - 2013 IJSSE
By julia h. allen, nancy r. mead, mark a. ardis (stevens institute of technology), thomas b. hilburn (embry-riddle aeronautical university), andrew j. kornecki (embry-riddle aeronautical university), richard c. linger (oak ridge national laboratory), james mcdonald (monmouth university).
In this paper, the authors present an overview of the Master of Software Assurance curriculum, including its history, student prerequisites, and outcomes
Strengthening Ties Between Process and Security
In this paper, Carol Woody summarizes recent key accomplishments, including harmonizing security practices with CMMI and using assurance cases.
Estimating Benefits from Investing in Secure Software Development
By ashish arora, rahul telang, steven frank.
In this paper, the authors discuss the costs and benefits of incorporating security in software development and presents formulas for calculating security costs and security benefits.
What Measures Do Vendors Use for Software Assurance?
By jeremy epstein.
In this paper, Jeremy Epstein examines what real vendors do to ensure that their products are reasonably secure.
The Development of a Graduate Curriculum for Software Assurance
By nancy r. mead, mark a. ardis (stevens institute of technology).
In this paper, the authors describe the work of the Master of Software Assurance curriculum project, including sources, process, products, and more.
Secure Software Development Life Cycle Processes
By noopur davis.
In this paper, Noopur Davis presents information about processes, standards, and more that support or could support secure software development.
Applicability of Cultural Markers in Computer Network Attack Attribution
July 11, 2013 • white paper.
In this 2013 white paper, Char Sample discusses whether cultural influences leave traces in computer network attack (CAN) choices and behaviors.
Improving Software Assurance
July 5, 2013 • white paper.
In this paper, the authors discuss what practitioners should know about software assurance, where to look, what to look for, and how to demonstrate improvement.
Scale: System Development Challenges
In this paper, the authors describe software assurance challenges inherent in networked systems development and propose a solution.
Requirements Prioritization Case Study Using AHP
By nancy r. mead.
In this paper, Nancy Mead describes a tradeoff analysis that can select a suitable requirements prioritization method and the results of trying one method.
Arguing Security - Creating Security Assurance Cases
By john b. goodenough, charles weinstock, howard f. lipson.
In this paper, the authors explain an approach to documenting an assurance case for system security.
SQUARE Process
In this paper, Nancy Mead describes the SQUARE process as a means for eliciting, categorizing, and prioritizing security requirements for IT systems.
Requirements Elicitation Case Studies Using IBIS, JAD, and ARM
In this paper, Nancy Mead describes a tradeoff analysis that can be used to select a suitable requirements elicitation method.
The Common Criteria
In this paper, Nancy Mead discusses how Common Criteria is evaluated, it also presents a standard that is related to developing security requirements.
Measures and Measurement for Secure Software Development
July 3, 2013 • white paper, by david zubrow, james mccurley, carol dekkers.
In this paper, the authors discuss how measurement can be applied improve the security characteristics of the software being developed.
Predictive Models for Identifying Software Components Prone to Failure During Security Attacks
By laurie williams, michael gegick, mladan vouk.
In this paper, the authors describes how the presence of security faults correlates strongly with the presence of a more general category of reliability faults.
Measuring the Software Security Requirements Engineering Process
In this paper, Nancy Mead describes a measurement approach to security requirements engineering to analyze projects that were developed with and without SQUARE.
System-of-Systems Influences on Acquisition Strategy Development
July 2, 2013 • white paper, by rita c. creel, robert j. ellison.
In this paper, the authors discuss significant new sources of risk and recommend ways to address them.
Risk-Centered Practices
By julia h. allen.
In this paper, Julia Allen discusses the role that risk management and risk assessment play in choosing which security practices to implement.
Supply-Chain Risk Management: Incorporating Security into Software Development
In this paper, the authors describe practices that address defects and mechanisms for introducing these practices into the acquisition lifecycle.
Prioritizing IT Controls for Effective, Measurable Security
By daniel phelps, kurt milne, gene kim (ip services and itpi).
In this paper, the authors summarize results from the IT Controls Performance Study conducted by the IT Process Institute.
Building Security into the Business Acquisition Process
By dan shoemaker (university of detroit mercy).
In this paper, Dan Shoemaker presents the standard process for acquiring software products and services in business.
Navigating the Security Practice Landscape
In this paper, Julia Allen presents a summary of ten leading sources of security practice definition and implementation guidance.
Assuring Software Systems Security: Life Cycle Considerations for Government Acquisitions
By rita c. creel.
In this paper, Rita Creel identifies acquirer activities and resources necessary to support contractor efforts to build secure software-intensive systems.
Plan, Do, Check, Act
In this paper, Ken van Wyk provides a primer on the most commonly used tools for traditional penetration testing.
Finding a Vendor You Can Trust in the Global Marketplace
By dan shoemaker (university of detroit mercy), art conklin.
In this paper, the authors introduce the concept of standardized third-party certification of supplier process capability.
Results of SEI Line-Funded Exploratory New Starts Projects: FY 2012
July 1, 2013 • technical report, by robert nord, robert w. stoddard, lisa brownsword, dennis goldenson, mary ann lapham, david zubrow, william r. claycomb, lori flynn, peter h. feiler, rick kazman, robert ferguson, stephany bellomo, ipek ozkaya, sagar chaki, arie gurfinkel, julie b. cohen, john j. hudak, jeff havrilla, bjorn andersson, john mcgregor, james mccurley, carly l. huth, david mcintire, david p. gluch, wesley jin, chuck hines, brittany phillips, yuanfang cai (drexel university).
This report describes line-funded exploratory new starts (LENS) projects that were conducted during fiscal year 2012 (October 2011 through September 2012).
Insider Threat Attributes and Mitigation Strategies
July 1, 2013 • technical note, by george silowash.
In this report, George Silowash maps common attributes of insider threat cases to characteristics important for detecting, preventing, or mitigating the threat.
Pointer Ownership Model
June 10, 2013 • white paper.
In this paper, David Svoboda describes the Pointer Ownership Model, which can statically identify classes of errors involving dynamic memory in C/C++ programs.
Common Software Platforms in System-of-Systems Architectures: The State of the Practice
June 6, 2013 • white paper, by rick kazman, sholom g. cohen, john klein.
System-of-systems (SoS) architectures based on common software platforms have been commercially successful, but progress on creating and adopting them has been slow. This study aimed to understand technical issues for …
Software Assurance for Executives: Mapping of Common Topics to Specific Materials
June 3, 2013 • white paper.
In this paper, the authors present common topics, course materials, and resources related to the Software Assurance for Executives course held in June 2013.
Software Assurance for Executives
This legal form was used in the Software Assurance for Executives course that was held in June 2013.
Isolating Patterns of Failure in Department of Defense Acquisition
June 1, 2013 • technical note, by lisa brownsword, patrick r. place, cecilia albert, john j. hudak, charles (bud) hammons, david j. carney.
This report documents an investigation into issues related to aligning acquisition strategies with business and mission goals.
Socio-Adaptive Systems Challenge Problems Workshop Report
June 1, 2013 • special report, by mark h. klein, timothy morrow, scott hissam.
This report presents a summary of the findings of the Socio-Adaptive Systems Challenge Problem Workshop, held in Pittsburgh, PA, on April 12-13, 2012.
Strengths in Security Solutions
May 31, 2013 • white paper, by carol woody, allen d. householder, robert c. seacord, arjuna shunn (microsoft).
In this white paper, the authors map eight CERT tools, services, and processes to Microsoft's Simplified Security Development Lifecycle.
Integrating Software Assurance Knowledge into Conventional Curricula
May 23, 2013 • white paper.
In this paper, the authors discuss the results of comparing the Common Body of Knowledge for Secure Software Assurance with traditional computing disciplines.
Maturity of Practice
In this paper, Julia Allen identifies indicators that organizations are addressing security as a governance and management concern, at the enterprise level.
Integrating Security and IT
May 21, 2013 • white paper.
In this paper, Julia Allen describes the key relationship between IT processes and security controls.
Individual Certification of Security Proficiency for Software Professionals: Where Are We? Where Are We Going?
In this paper, Dan Shoemaker describes existing professional certifications in information assurance and emerging certifications for secure software assurance.
How Much Security Is Enough?
In this paper, Julia Allen provides guidelines for answering this question, including means for determining adequate security based on risk.
Models for Assessing the Cost and Value of Software Assurance
By john bailey, dan shoemaker (university of detroit mercy), antonio drommi, jeff ingalsbe (university of detroit mercy), nancy r. mead.
In this paper, the authors present IT valuation models that represent the most commonly accepted approaches to the valuation of IT and IT processes.
Adapting Penetration Testing for Software Development Purposes
By ken van wyk (no affiliation).
In this paper, Ken van Wyk provides background information on penetration testing processes and practices.
Requirements Engineering Annotated Bibliography
In this paper, Nancy Mead provides a bibliography of sources related to requirements engineering.
Defining the Discipline of Secure Software Assurance: Initial Findings from the National Software Assurance Repository
By nancy r. mead, jeff ingalsbe (university of detroit mercy), dan shoemaker (university of detroit mercy), rita barrios.
In this paper, the authors characterize the current state of secure software assurance work and suggest future directions.
Making the Business Case for Software Assurance
In this paper, Nancy Mead provides an overview of the Business Case content area.
Spotlight On: Insider Theft of Intellectual Property Inside the United States Involving Foreign Governments or Organizations (2013)
May 20, 2013 • technical note, by andrew p. moore, randall f. trzeciak, derrick spooner, dawn cappelli, matthew l. collins.
In this report, the authors provide a snapshot of individuals involved in insider threat cases and recommends how to mitigate the risk of similar incidents.
The Software Assurance Competency Model: A Roadmap to Enhance Individual Professional Capability
May 16, 2013 • white paper, by nancy r. mead, dan shoemaker (university of detroit mercy).
In this paper, the authors describe a software assurance competency model that can be used by professionals to improve their software assurance skills.
Building a Body of Knowledge for ICT Supply Chain Risk Management
In this paper, the authors propose a set of Supply Chain Risk Management (SCRM) activities and practices for Information and Communication Technologies (ICT).
Modeling Tools References
May 15, 2013 • white paper, by samuel t. redwine.
In this paper, Samuel Redwine provides references related to modeling tools.
Software Assurance Education Overview
In this paper, Nancy Mead discusses the growing demand for skilled professionals who can build security and correct functionality into software.
Governance and Management References
May 14, 2013 • white paper.
In this paper, Julia Allen provides references related to governance and management.
Getting Secure Software Assurance Knowledge into Conventional Practice
By linda laird, nancy r. mead, dan shoemaker (university of detroit mercy).
In this paper, the authors describe three educational initiatives in support of software assurance education.
General Modeling Concepts
In this paper, Samuel Redwine introduces several concepts related to the Introduction to Modeling Tools for Software Security article and modeling in general.
A Systemic Approach for Assessing Software Supply-Chain Risk
By robert j. ellison, carol woody, christopher j. alberts, rita c. creel, audrey j. dorofee.
In this paper, the authors highlight the approach being implemented by SEI researchers for assessing and managing software supply-chain risks and provides a summary of the status of this work.
Framing Security as a Governance and Management Concern: Risks and Opportunities
In this paper, Julia Allen describes six "assets" or requirements of being in business that can be compromised by insufficient security investment.
Assembly, Integration, and Evolution Overview
By howard f. lipson.
In this paper, Howard Lipson describes the objective of the Assembly, Integration & Evolution content area.
A Common Sense Way to Make the Business Case for Software Assurance
By dan shoemaker (university of detroit mercy), jeff ingalsbe (university of detroit mercy), antonio drommi, nancy r. mead, john bailey.
In this article, the authors demonstrate how a true cost/benefit for secure software can be derived.
Deployment and Operations References
In this paper, Julia Allen provides a list of references related to deployment and operations.
Deploying and Operating Secure Systems
In this paper, Julia Allen provides a brief overview of deployment and operations security issues and advice for using related practices.
Two Nationally Sponsored Initiatives for Disseminating Assurance Knowledge
In this paper, the authors describe two efforts that support national cybersecurity education goals.
By Dan Shoemaker (University of Detroit Mercy), Nancy R. Mead, Carol Woody
In this paper, the authors highlight efforts underway to address our society's growing dependence on software and the need for effective software assurance.
Assurance Cases Overview
In this paper, Howard Lipson introduces the concepts and benefits of developing and maintaining assurance cases for security.
It’s a Nice Idea but How Do We Get Anyone to Practice It? A Staged Model for Increasing Organizational Capability in Software Assurance
May 13, 2013 • white paper.
In this paper, Dan Shoemaker presents a standard approach to increasing the security capability of a typical IT function.
Software Security Engineering: A Guide for Project Managers (white paper)
By sean barnum, gary mcgraw, julia h. allen, nancy r. mead, robert j. ellison.
In this guide, the authors discuss our reliance on software and systems that use the internet or internet-exposed private networks.
Requirements Elicitation Introduction
In this paper, Nancy Mead discusses elicitation methods and the kind of tradeoff analysis that can be done to select a suitable one.
Requirements Prioritization Introduction
In this paper, Nancy Mead discusses using a systematic prioritization approach to prioritize security requirements.
Optimizing Investments in Security Countermeasures: A Practical Tool for Fixed Budgets
By jonathan caulkins, eric hough, hassan osman, nancy r. mead.
In this paper, the authors introduce a novel method of optimizing using integer programming (IP).
Security Is Not Just a Technical Issue
In this paper, Julia Allen defines the scope of governance concern as they apply to security.
PSP-VDC: An Adaptation of the PSP that Incorporates Verified Design by Contract
May 7, 2013 • technical report, by silvana moreno (universidad de la república), álvaro tasistro (universidad ort uruguay), diego vallespir (universidad de la república), bill nichols.
This paper describes a proposal for integrating Verified Design by Contract into PSP in order to reduce the amount of defects present at the Unit Testing phase, while preserving or …
How You Can Help Your Utility Clients with a Critical Aspect of Smart Grid Transformation They Might be Overlooking
May 1, 2013 • white paper, by the sgmm communications team.
This paper discusses how you can use the Smart Grid Maturity Model (SGMM) to benefit your utility clients.
Five Smart Grid Questions Every Utility Executive Should Ask
This paper recommends the Smart Grid Maturity Model (SGMM), a tool utilities can use to plan and measure smart grid progress.
Application Virtualization as a Strategy for Cyber Foraging in Resource-Constrained Environments
May 1, 2013 • technical note, by dominik messinger, grace lewis.
This technical note explores application virtualization as a more lightweight alternative to VM synthesis for cloudlet provisioning.
The Perils of Treating Software as a Specialty Engineering Discipline
April 30, 2013 • white paper, by keith korzec, tom merendino.
This paper reviews the perils of insufficiently engaging key software domain experts during program development.
Four Pillars for Improving the Quality of Safety-Critical Software-Reliant Systems
April 29, 2013 • white paper, by lutz wrage, charles weinstock, john b. goodenough, arie gurfinkel, peter h. feiler.
This white paper presents an improvement strategy comprising four pillars of an integrate-then-build practice that lead to improved quality through early defect discovery and incremental end-to-end validation and verification.
MERIT Interactive Insider Threat Training Simulator
April 16, 2013 • white paper.
In this paper, the authors describe how state-of-the-art multi-media technologies were used to develop the MERIT InterActive training simulator.
Software Assurance Competency Model
March 11, 2013 • technical note, by thomas b. hilburn (embry-riddle aeronautical university), andrew j. kornecki (embry-riddle aeronautical university), mark a. ardis (stevens institute of technology), glenn johnson ((isc)2), nancy r. mead.
In this report, the authors describe a model that helps create a foundation for assessing and advancing the capability of software assurance professionals.
Detecting and Preventing Data Exfiltration Through Encrypted Web Sessions via Traffic Inspection
March 1, 2013 • technical note, by todd lewellen, daniel l. costa, george silowash, joshua w. burns.
In this report, the authors present methods for detecting and preventing data exfiltration using a Linux-based proxy server in a Microsoft Windows environment.
Justification of a Pattern for Detecting Intellectual Property Theft by Departing Insiders
By dave mundie, david zubrow, andrew p. moore, david mcintire.
In this report, the authors justify applying the pattern “Increased Review for Intellectual Property (IP) Theft by Departing Insiders.”
Quantifying Uncertainty in Expert Judgment: Initial Results
March 1, 2013 • technical report, by robert w. stoddard, dennis goldenson.
The work described in this report, part of a larger SEI research effort on Quantifying Uncertainty in Early Lifecycle Cost Estimation (QUELCE), aims to develop and validate methods for calibrating …
History of CERT-RMM
February 15, 2013 • white paper.
This paper explains the history of how the CERT-RMM came to be.
The MAL: A Malware Analysis Lexicon
February 1, 2013 • technical note, by david mcintire, dave mundie.
In this report, the authors present results of the Malware Analysis Lexicon (MAL) initiative, which developed the first common vocabulary for malware analysis.
Tunisia Case Study
January 24, 2013 • white paper.
This case study describes the experiences of the Tunisia CSIRT in getting its organization up and running.
Columbia CSIRT Case Study
This case study describes the experiences of the Columbia CSIRT in getting its organization up and running.
Insider Threat Control: Using Universal Serial Bus (USB) Device Auditing to Detect Possible Data Exfiltration by Malicious Insiders
January 1, 2013 • technical note, by george silowash, todd lewellen.
In this report, the authors present methods for auditing USB device use in a Microsoft Windows environment.
Cyber Intelligence Tradecraft Project: Summary of Key Findings
January 1, 2013 • white paper, by kate ambrose, troy townsend, andrew o. mellinger, jay mcallister, melissa ludwick.
This study, known as the Cyber Intelligence Tradecraft Project (CITP), seeks to advance the capabilities of organizations performing cyber intelligence by elaborating on best practices and prototyping solutions to shared …
Insider Threat Control: Understanding Data Loss Prevention (DLP) and Detection by Correlating Events from Multiple Sources
By christopher king, george silowash.
In this report, the authors present methods for controlling removable media devices in a MS Windows environment.
SEI Product Line Bibliography
December 31, 2012 • white paper.
This bibliography lists SEI and non-SEI resources that have informed the SEI Product Lines efforts. Examples cover diverse domains and show the kind of improvements you can achieve using a …
A Framework for Software Product Line Practice, Version 5.0
By sholom g. cohen, linda m. northrop, reed little, john mcgregor, paul c. clements, felix bachmann, john k. bergey, gary chastek, patrick donohoe, liam o'brien, lawrence g. jones, robert w. krut, jr..
This document describes the activities and practices in which an organization must be competent before it can benefit from fielding a product line of software systems.
Chronological Examination of Insider Threat Sabotage: Preliminary Observations
December 1, 2012 • white paper, by carly l. huth, david mcintire, william r. claycomb, lori flynn, todd lewellen.
In this paper, the authors examine 15 cases of insider threat sabotage of IT systems to identify points in the attack time-line.
The Business Case for Systems Engineering Study: Assessing Project Performance from Sparse Data
December 1, 2012 • special report, by joseph p. elm.
This report describes the data collection and analysis process used to support the assessment of project performance for the systems engineering (SE) effectiveness study.
Analyzing Cases of Resilience Success and Failure - A Research Study
December 1, 2012 • technical note, by andrew p. moore, randall f. trzeciak, robert w. stoddard, julia h. allen, nader mehravari, pamela d. curtis, kevin g. partridge.
In this report, the authors describe research aimed at helping organizations to know the business value of implementing resilience processes and practices.
Common Sense Guide to Mitigating Insider Threats, Fourth Edition
December 1, 2012 • technical report, by dawn cappelli, timothy j. shimeall, lori flynn, george silowash, andrew p. moore, randall f. trzeciak.
In this report, the authors define insider threats and outline current insider threat patterns and trends.
Arabic Language Translation of CMMI for Services V1.3
November 1, 2012 • white paper, by the cmmi product team.
Arabic translation of CMMI-SVC V1.3
TSP Symposium 2012 Proceedings
November 1, 2012 • special report, by shigeru kusakabe (kyushu university), yoichi omori (kyushu university), keijiro araki (kyushu university), fernanda grazioli (universidad de la república), silvana moreno (universidad de la república), álvaro tasistro (universidad ort uruguay), diego vallespir (universidad de la república), joão pascoal faria (university of porto), mushtaq raza (university of porto), pedro c. henriques (strongstep – innovation in software quality), césar duarte (strongstep – innovation in software quality), elias fallon (cadence design systems, inc.), lee gazlay (cadence design systems, inc.), bill nichols.
The 2012 TSP Symposium was organized by the Software Engineering Institute (SEI) and took place September 18-20 in St. Petersburg, FL. The goal of the TSP Symposium is to bring …
DoD Information Assurance and Agile: Challenges and Recommendations Gathered Through Interviews with Agile Program Managers and DoD Accreditation Reviewers
November 1, 2012 • technical note, by stephany bellomo, carol woody.
This paper discusses the natural tension between rapid fielding and response to change (characterized as agility) and DoD information assurance policy. Data for the paper was gathered through interviews with …
Reliability Improvement and Validation Framework
By peter h. feiler, arie gurfinkel, charles weinstock, john b. goodenough, lutz wrage.
This report discusses the reliability validation and improvement framework developed by the SEI. The purpose of this framework is to provide a foundation for addressing the challenges of qualifying increasingly …
The Business Case for Systems Engineering Study: Results of the Systems Engineering Effectiveness Survey
By joseph p. elm, dennis goldenson.
This report summarizes the results of a survey that had the goal of quantifying the connection between the application of systems engineering (SE) best practices to projects and programs and …
Maturity Models 101: A Primer for Applying Maturity Models to Smart Grid Security, Resilience, and Interoperability
By richard a. caralli, austin montgomery, mark knight (cgi group).
In this paper, the authors explain the history and evolution of and applications for maturity models.
Technical Debt: From Metaphor to Theory and Practice
By robert nord, ipek ozkaya, philippe kruchten.
This article discusses the technical debt metaphor and considers it beyond a "rhetorical concept." The article explores the role of decision making about developmental activities and future changes and the …
Architecture-Driven Semantic Analysis of Embedded Systems (Dagstuhl Seminar 12272)
October 10, 2012 • special report, by peter h. feiler, jerome hugues.
This report documents the program and outcomes of presentations and working groups from Dagstuhl Seminar 12272, "Architecture-Driven Semantic Analysis of Embedded Systems."
Spotlight On: Insider Threat from Trusted Business Partners Version 2: Updated and Revised
October 1, 2012 • white paper, by andrew p. moore, randall f. trzeciak, derrick spooner, todd lewellen, robert weiland (carnegie mellon university), dawn cappelli.
In this article, the authors focus on cases in which the malicious insider was employed by a trusted business partner of the victim organization.
The Role of Standards in Cloud-Computing Interoperability
October 1, 2012 • technical note, by grace lewis.
This report explores the role of standards in cloud-computing interoperability. It covers cloud-computing basics and standard-related efforts, discusses several use cases, and provides recommendations for cloud-computing adoption.
Cloud Computing at the Tactical Edge
By grace lewis, edwin j. morris, soumya simanta, mahadev satyanarayanan (carnegie mellon university), kiryong ha (carnegie mellon school of computer science).
This technical note presents a strategy to overcome the challenges of obtaining sufficient computation power to run applications needed for warfighting and disaster relief missions. It discusses the use of …
Well There’s Your Problem: Isolating the Crash-Inducing Bits in a Fuzzed File
In this 2012 report, Allen Householder describes an algorithm for reverting bits from a fuzzed file to those found in the original seed file to recreate the crash.
Resource Allocation in Dynamic Environments
October 1, 2012 • technical report, by jeffrey hansen, gabriel moreno, daniel plakosh, joe seibel, scott hissam, b. craig meyers, lutz wrage.
When warfighting missions are conducted in a dynamic environment, the allocation of resources needed for mission operation can change from moment to moment. This report addresses two challenges of resource …
Building an Incident Management Body of Knowledge
September 7, 2012 • white paper, by dave mundie, robin ruefle.
In this paper, the authors describe the components of the CERT Incident Management Body of Knowledge (CIMBOK) and how they were constructed.
SEPG Europe 2012 Conference Proceedings
September 1, 2012 • special report, by jose maria garcia (software quality assurance), ana m. moreno (universidad politecnica de madrid), radouane oudrhiri (systonomy), fabrizio pellizzetti (systonomy), alejandro ruiz-robles (university of piura), maria-isabel sanchez-segura (carlos iii university of madrid), prasad m. shrasti (tata consultancy services), aman kumar singhal (infosys), javier garcia-guzman (carlos iii university of madrid), javier garzas (kybele research and kybele consulting), amit arun javadekar (infosys), patrick kirwan, joaquin lasheras (centic), fuensanta medina-dominguez (carlos iii university of madrid), erich meier (method park), arturo mora-soto (carlos iii university of madrid).
This report compiles seven papers based on presentations given at SEPG Europe 2012.
Competency Lifecycle Roadmap: Toward Performance Readiness
September 1, 2012 • technical note, by robin ruefle, christopher j. alberts, sandra behrens.
In this report, the authors describe the Competency Lifecycle Roadmap (CLR), a preliminary roadmap for understanding and building workforce readiness.
Communication Among Incident Responders – A Study
By brett tjaden, robert floodeen.
In this report, the authors describe three factors for helping or hindering the cooperation of incident responders.
Toward a Theory of Assurance Case Confidence
September 1, 2012 • technical report, by ari z. klein, charles weinstock, john b. goodenough.
In this report, the authors present a framework for thinking about confidence in assurance case arguments.
Insider Fraud in Financial Services
August 3, 2012 • white paper.
In this brochure, the authors present the findings of a study that analyzed computer criminal activity in the financial services sector.
Probability-Based Parameter Selection for Black-Box Fuzz Testing
August 1, 2012 • technical note, by allen d. householder, jonathan foote.
In this report, the authors describe an algorithm for automating the selection of seed files and other parameters used in black-box fuzz testing.
Results of SEI Line-Funded Exploratory New Starts Projects
August 1, 2012 • technical report, by bill nichols, robert nord, cory cohen, soumya simanta, rick kazman, nanette brown, william casey, david french, edwin j. morris, arie gurfinkel, sagar chaki, dionisio de niz, ipek ozkaya, brad myers, gene cahill, ofer strichman, raghvinder sangwan, len bass, peppo valetto.
This report describes the line-funded exploratory new starts (LENS) projects that were undertaken during fiscal year 2011. For each project, the report presents a brief description and a recounting of …
Network Profiling Using Flow
By sid faber, austin whisnant.
In this report, the authors provide a step-by-step guide for profiling and discovering public-facing assets on a network using netflow data.
Insider Threats to Cloud Computing: Directions for New Research Challenges
July 16, 2012 • white paper, by william r. claycomb, alex nicoll.
In this paper, the authors explain how cloud computing related insider threats are a serious concern, but that this threat has not been thoroughly explored.
Insider Threat Study: Illicit Cyber Activity Involving Fraud in the U.S. Financial Services Sector
July 1, 2012 • special report, by david mcintire, adam cummings, andrew p. moore, randall f. trzeciak, todd lewellen.
In this report, the authors describe insights and risk indicators of malicious insider activity in the banking and finance sector.
Supporting the Use of CERT Secure Coding Standards in DoD Acquisitions
July 1, 2012 • technical note, by john k. bergey, philip miller, robert c. seacord, timothy morrow.
In this report, the authors provide guidance for helping DoD acquisition programs address software security in acquisitions.
The Evolution of a Science Project: A Preliminary System Dynamics Model of a Recurring Software-Reliant Acquisition Behavior
July 1, 2012 • technical report, by william e. novak, andrew p. moore, christopher j. alberts.
This report uses a preliminary system dynamics model to analyze a specific adverse acquisition dynamic concerning the poorly controlled evolution of small prototype efforts into full-scale systems.
Introduction to System Strategies
June 27, 2012 • white paper.
In this paper, the authors discuss the effects of the changing operational environment on the development of secure systems.
Introduction to Modeling Tools for Software Security
June 24, 2012 • white paper.
In this paper, Samuel Redwine introduces security concepts and tools useful for modeling security properties.
Security-Specific Bibliography
June 22, 2012 • white paper.
In this paper, the authors provide a bibliography of sources related to security.
A Virtual Upgrade Validation Method for Software-Reliant Systems
June 1, 2012 • technical report, by dionisio de niz, peter h. feiler, david p. gluch, lutz wrage.
This report presents the Virtual Upgrade Validation (VUV) method, an approach that uses architecture-centric, model-based analysis to identify system-level problems early in the upgrade process to complement established test qualification …
Report from the First CERT-RMM Users Group Workshop Series
April 1, 2012 • technical note, by lisa r. young, julia h. allen.
In this report, the authors describe the first CERT RMM Users Group (RUG) Workshop Series and the experiences of participating members and CERT staff.
Source Code Analysis Laboratory (SCALe)
By david svoboda, robert w. stoddard, robert c. seacord, will dormann, james mccurley, philip miller, jefferson welch.
In this report, the authors describe the CERT Program's Source Code Analysis Laboratory (SCALe), a conformance test against secure coding standards.
Insider Threat Security Reference Architecture
April 1, 2012 • technical report, by joji montelibano, andrew p. moore.
In this report, the authors describe the Insider Threat Security Reference Architecture (ITSRA), an enterprise-wide solution to the insider threat.
A Pattern for Increased Monitoring for Intellectual Property Theft by Departing Insiders
By andrew p. moore, dave mundie, michael hanley.
In this report, the authors present techniques for helping organizations plan, prepare, and implement means to mitigate insider theft of intellectual property.
The Impact of Passive DNS Collection on End-User Privacy
March 22, 2012 • white paper, by jonathan spring, carly l. huth.
In this paper, the authors discuss whether pDNS allows reconstruction of an end user's DNS behavior and if DNS behavior is personally identifiable information.
Approaches for Edge-Enabled Tactical Systems
March 19, 2012 • white paper.
This booklet contains brief articles about using mobile devices in the areas of edge-enabled systems and cloud computing and a report on cloud offload in hostile environments.
Digital Investigation Workforce Development
March 1, 2012 • white paper.
In this paper, the authors describe an approach for deriving measures of software security from well-established and commonly used standard practices.
What’s New in V2 of the Architecture Analysis & Design Language Standard?
March 1, 2012 • special report, by peter h. feiler, joe seibel, lutz wrage.
This report provides an overview of changes and improvements to the Architecture Analysis & Design Language (AADL) standard for describing both the software architecture and the execution platform architectures of …
Principles of Trust for Embedded Systems
March 1, 2012 • technical note, by david fisher.
In this report, David Fisher provides substance and explicit meaning to the terms trust and trustworthy as they relate to automated systems.
Deriving Software Security Measures from Information Security Standards of Practice
February 16, 2012 • white paper, by robert w. stoddard, julia h. allen, christopher j. alberts.
In this paper, the authors describe an approach for deriving measures of software security from common standard practices for information security.
Risk-Based Measurement and Analysis: Application to Software Security
February 1, 2012 • technical note, by christopher j. alberts, julia h. allen, robert w. stoddard.
In this report, the authors present the concepts of a risk-based approach to software security measurement and analysis and describe the IMAF and MRD.
Mission Risk Diagnostic (MRD) Method Description
By christopher j. alberts, audrey j. dorofee.
In this report, the authors describe the Mission Risk Diagnostic (MRD) method, which is used to assess risk in systems across the lifecycle and supply chain.
Proceedings of the Smart Grid Maturity Model Leadership Workshop
January 31, 2012 • special report.
In January 2012, leaders in the electric power industry collaborated with the SEI to build the future of the Smart Grid Maturity Model at the SGMM Leadership Workshop.
Modifying Lanchester's Equations for Modeling and Evaluating Malicious Domain Name Take-Down
January 6, 2012 • white paper.
In this paper, Jonathan Spring models internet competition on large, decentralized networks using a modification of Lanchester's equations for combat.
January 2, 2012 • White Paper
In this paper, the authors demonstrate that there are name servers that exhibit IP address flux, a behavior that falls outside the prescribed parameters.
Discerning the Intent of Maturity Models from Characterizations of Security Posture
January 1, 2012 • white paper.
In this paper, Rich Caralli discusses how using maturity models and characterizing security posture are activities with different intents, outcomes, and uses.
Communication Among Incident Responders - A Study
By robert floodeen, brett tjaden.
In this paper, the authors describe preliminary results of a study of how effective nine autonomous incident response organizations are.
Best Practices for Artifact Versioning in Service-Oriented Systems
January 1, 2012 • technical note, by william anderson, marc novakouski, grace lewis, jeff davenport.
This report describes some of the challenges of software versioning in an SOA environment and provides guidance on how to meet these challenges by following industry guidelines and recommended practices.
Interoperability in the e-Government Context
By marc novakouski, grace lewis.
This report describes a proposed model through which to understand interoperability in the e-government context.
Spotlight On: Malicious Insiders and Organized Crime Activity
By christopher king.
In this report, Christopher King provides a snapshot of who malicious insiders are, what and how they strike, and why.
A Closer Look at 804: A Summary of Considerations for DoD Program Managers
December 1, 2011 • special report, by stephany bellomo.
The information in this report is intended to help program managers reason about actions they may need to take to adapt and comply with the Section 804 NDAA for 2010 …
Standards-Based Automated Remediation: A Remediation Manager Reference Implementation, 2011 Update
By sagar chaki, mary popeck, rita c. creel, benjamin mccormick, jeff davenport, mike kinney (national security agency).
In this report, the authors describe work to develop standards for automated remediation of vulnerabilities and compliance issues on DoD networked systems.
Using Defined Processes as a Context for Resilience Measures
December 1, 2011 • technical note, by pamela d. curtis, linda parker gates, julia h. allen.
In this report, the authors describe how implementation-level processes can provide context for identifying and defining measures of operational resilience.
Quantifying Uncertainty in Early Lifecycle Cost Estimation (QUELCE)
December 1, 2011 • technical report, by debra anderson, james mccurley, robert w. stoddard, dennis goldenson, david zubrow, robert ferguson.
The method of quantifying uncertainty described in this report synthesizes scenario building, Bayesian Belief Network (BBN) modeling and Monte Carlo simulation into an estimation method that quantifies uncertainties, allows subjective …
An Investigation of Techniques for Detecting Data Anomalies in Earned Value Management Data
By mark kasunic, david zubrow, dennis goldenson, james mccurley.
This research demonstrated the effectiveness of various statistical techniques for discovering quantitative data anomalies.
German language translation of CMMI for Development, V1.3
November 1, 2011 • white paper.
This PDF contains a German language translation of CMMI for Development, V1.3.
Japanese Language Translation of CMMI for Development, V1.3
CERT® Resilience Management Model (CERT®-RMM) V1.1: NIST Special Publication Crosswalk Version 1
November 1, 2011 • technical note, by lisa r. young, kevin g. partridge.
In this report, the authors map CERT-RMM process areas to selected NIST special publications in the 800 series.
Agile Methods: Selected DoD Management and Acquisition Concerns
October 1, 2011 • technical note, by mary ann lapham, suzanne miller, nanette brown, alfred schenker, bart hackemack, linda levine, lorraine adams, charles (bud) hammons.
This technical note addresses some of the key issues that either must be understood to ease the adoption of Agile or are seen as potential barriers to adoption of Agile …
An Acquisition Perspective on Product Evaluation
By harry l. levinson, richard librizzi, grady campbell.
This technical note focuses on software acquisition and development practices related to the evaluation of products before, during, and after implementation.
CERT® Resilience Management Model (RMM) v1.1: Code of Practice Crosswalk Commercial Version 1.1
By kevin g. partridge, lisa r. young.
In this report, the authors explain how CERT-RMM process areas, industry standards, and codes of practice are used by organizations in an operational setting.
Insider Threat Control: Using Centralized Logging to Detect Data Exfiltration Near Insider Termination
By joji montelibano, michael hanley.
In this report, the authors present an insider threat pattern on how organizations can combat insider theft of intellectual property.
CERT® Resilience Management Model Capability Appraisal Method (CAM) Version 1.1
October 1, 2011 • technical report, by resilient enterprise management team.
In this report, the authors demonstrate that the SCAMPI method can be adapted and applied to CERT-RMM V1.1 as the reference model for a process appraisal.
Smart Grid Maturity Model: Matrix, Version 1.2
September 1, 2011 • white paper.
This document shows a matrix related to Smart Grid Maturity Model levels.
Proceedings of the Fourth International Workshop on a Research Agenda for Maintenance and Evolution of Service-Oriented Systems (MESOA 2010)
September 1, 2011 • special report, by dennis b. smith, kostas kontogiannis, grace lewis.
This report summarizes the proceedings from the 2010 MESOA workshop and includes the accepted papers that were the basis for the presentations given during the workshop.
Software Assurance Curriculum Project Volume IV: Community College Education
September 1, 2011 • technical report, by nancy r. mead, mark a. ardis (stevens institute of technology), elizabeth k. hawthorne (union county college).
In this report, the authors focus on community college courses for software assurance.
Understanding and Leveraging a Supplier’s CMMI Efforts: A Guidebook for Acquirers (Revised for V1.3)
By john scibilia, lawrence t. osiecki, mike phillips.
This guidebook helps acquisition organizations formulate questions for their suppliers related to CMMI. It also helps organizations interpret responses to identify and evaluate risks for a given supplier.
Smart Grid Maturity Model, Version 1.2: Model Definition
By the sgmm team.
The Smart Grid Maturity Model (SGMM) is business tool that provides a framework for electric power utilities to help modernize their operations and practices for delivering electricity.
Keeping Your Family Safe in a Highly Connected World
August 10, 2011 • white paper, by jonathan frederick, marie baker.
In this paper, the authors describe the risks of being victims of theft, including becoming involved unknowingly in illegal activities over a networked device.
Which CMMI Model Is for You?
August 1, 2011 • white paper, by mike phillips, sandra shrum.
A short white paper that provides guidance on selecting the best CMMI model for process improvement.
Architecting Service-Oriented Systems
August 1, 2011 • technical note, by philip bianco, grace lewis, paulo merson, soumya simanta.
This report presents guidelines for architecting service-oriented systems and the effect of architectural principles on system quality attributes.
Standards-Based Automated Remediation: A Remediation Manager Reference Implementation
July 1, 2011 • special report, by sagar chaki, mary popeck, rita c. creel, jeff davenport, mike kinney (national security agency), benjamin mccormick.
In this report, the authors describe work to develop standards for vulnerability and compliance remediation on DoD networked systems.
A Decision Framework for Selecting Licensing Rights for Noncommercial Computer Software in the DoD Environment
July 1, 2011 • technical report.
This report describes standard noncommercial software licensing alternatives as defined by U.S. Government and DoD regulations. It suggests an approach for identifying agency needs for license rights and the license …
Measures for Managing Operational Resilience
By pamela d. curtis, julia h. allen.
In this report, the Resilient Enterprise Management (REM) team suggests a set of top ten strategic measures for managing operational resilience.
An Online Learning Approach to Information Systems Security Education
June 13, 2011 • white paper, by robert c. seacord, norman bier (carnegie mellon university), marsha lovett (carnegie mellon university).
In this paper, the authors describe the development of a secure coding module that shows how to capture content, ensure learning, and scale to meet demand.
Monitoring Cloud Computing by Layer, Part 2
June 1, 2011 • white paper.
In this paper, Jonathan Spring presents a set of recommended restrictions and audits to facilitate cloud security.
A Preliminary Model of Insider Theft of Intellectual Property
June 1, 2011 • technical note, by dawn cappelli, thomas c. caron (john heinz iii college, school of information systems management, carnegie mellon university), eric d. shaw, andrew p. moore, randall f. trzeciak, derrick spooner.
In this report, the authors describe general observations about and a preliminary system dynamics model of insider crime based on our empirical data.
Software Assurance for System of Systems
May 1, 2011 • white paper, by john b. goodenough, linda m. northrop.
In this paper, the authors discuss confidence in system and SoS behavior and how theories can be used to make the assurance process more effective.
Architecture Evaluation without an Architecture: Experience with the Smart Grid
April 30, 2011 • white paper, by rick kazman, gabriel moreno, james ivers, len bass.
This paper describes an analysis of some of the challenges facing one portion of the Electrical Smart Grid in the United States - residential Demand Response (DR) systems.
Correlating Domain Registrations and DNS First Activity in General and for Malware
April 11, 2011 • white paper, by ed stoner, jonathan spring, leigh b. metcalf.
In this paper, the authors describe a pattern in the amount of time it takes for that domain to be actively resolved on the Internet.
Architectures for the Cloud: Best Practices for Navy Adoption of Cloud Computing
April 5, 2011 • white paper.
The goal of SEI research is to create best practices for architecture and design of systems that take advantage of the cloud, leading to greater system quality from both a …
Monitoring Cloud Computing by Layer, Part 1
April 1, 2011 • white paper, principles of survivability and information assurance.
In this paper, the authors describe a Security Information and Event Management signature for detecting possible malicious insider activity.
Employing SOA to Achieve Information Dominance
SEI research will enable the Navy to to develop service-oriented systems that address information dominance priority requirements.
Managing Technical Debt in Software-Reliant Systems
By nanette brown.
This whitepaper argues that there is an opportunity to study and improve the “technical debt” metaphor concept and offers software engineers a foundation for managing such trade-offs based on models …
Appraisal Requirements for CMMI Version 1.3 (ARC, V1.3)
April 1, 2011 • technical report, by scampi upgrade team.
The Appraisal Requirements for CMMI, Version 1.3 (ARC, V1.3), defines the requirements for appraisal methods intended for use with Capability Maturity Model Integration (CMMI) and with the People CMM.
Best Practices for National Cyber Security: Building a National Computer Security Incident Management Capability, Version 2.0
By samuel a. merrell, bradford j. willke, john haller, matthew j. butkovic.
In this 2011 report, an update to its 2010 counterpart, the authors provide insight that interested organizations and governments can use to develop a national incident management capability.
Trusted Computing in Embedded Systems Workshop
March 1, 2011 • special report, by archie d. andrews, jonathan m. mccune.
In this report, the authors describe the November 2010 Trusted Computing in Embedded Systems Workshop held at Carnegie Mellon University.
Issues and Opportunities for Improving the Quality and Use of Data in the Department of Defense
By erin harper, mark kasunic, david zubrow.
This report contains the recommendations of an SEI-lead, joint-sponsored workshop by the OSD (AT&L) and DDR&, around the topics of data quality, data analysis, and data use.
IEEE Computer Society/Software Engineering Institute Software Process Achievement (SPA) Award 2009
March 1, 2011 • technical report, by satyendra kumar, ramakrishnan m..
This report describes the work of the 2009 recipient of the IEEE Computer Society Software Process Achievement Award, jointly established by the SEI and IEEE to recognize outstanding achievements in …
CMMI for Acquisition (CMMI-ACQ) Primer, Version 1.3
By mike phillips.
Acquisition practices for the project level that help you get started with CMMI for Acquisition practices without using the whole model.
Software Assurance Curriculum Project Volume III: Master of Software Assurance Course Syllabi
By julia h. allen, nancy r. mead, richard c. linger (oak ridge national laboratory), andrew j. kornecki (embry-riddle aeronautical university), thomas b. hilburn (embry-riddle aeronautical university), mark a. ardis (stevens institute of technology).
In this report, the authors provide sample syllabi for the nine core courses in the Master of Software Assurance Reference Curriculum.
Delivering Software-Reliant Products Faster: Take Action to Help Your Organization Gain Speed Without Sacrificing Quality
February 14, 2011 • white paper.
Learn how to deliver software-reliant products faster and explore ways to use software architecture more effectively.
Delivering Software-Reliant Products Faster: Help Your Organization Gain Speed Without Sacrificing Quality
Learn how to look into the initial steps suggested for delivering software-reliant products faster.
A Framework for Evaluating Common Operating Environments: Piloting, Lessons Learned, and Opportunities
February 1, 2011 • special report, by steve rosemergy, cecilia albert.
This report explores the interdependencies among common language, business goals, and soft-ware architecture as the basis for a common framework for conducting evaluations of software technical solutions.
Integrating the Master of Software Assurance Reference Curriculum into the Model Curriculum and Guidelines for Graduate Degree Programs in Information Systems
February 1, 2011 • technical note, by dan shoemaker (university of detroit mercy), jeff ingalsbe (university of detroit mercy), nancy r. mead.
In this report, the authors examine how the Master of Software Assurance Reference Curriculum can be used for a Master of Science in Information Systems.
An Analysis of Technical Observations in Insider Theft of Intellectual Property Cases
By michael hanley, joji montelibano, tyler dean, will schroeder, matt houy, randall f. trzeciak.
In this report, the authors provide an overview of techniques used by malicious insiders to steal intellectual property.
Results of SEI Independent Research and Development Projects (FY 2010)
February 1, 2011 • technical report, by gabriel moreno, jeffrey hansen, john j. hudak, daniel plakosh, joe seibel, charles weinstock, cory cohen, william anderson, soumya simanta, peter h. feiler, robert nord, dionisio de niz, ipek ozkaya, edwin j. morris, nanette brown, jörgen hansson (university of skovde), lutz wrage, david p. gluch, richard c. linger (oak ridge national laboratory), howard f. lipson, david fisher, onur mutlu, christopher craig, tim daly, andres diaz-pace, ragunathan rajkumar, karthik lakshmanan, mark pleszkoch, archie d. andrews.
This report describes results of independent research and development (IRAD) projects undertaken in fiscal year 2010.
Network Monitoring for Web-Based Threats
By matthew heckathorn.
In this report, Matthew Heckathorn models the approach an attacker would take and provides detection or prevention methods to counter that approach.
Function Extraction (FX) Research for Computation of Software Behavior: 2010 Development and Application of Semantic Reduction Theorems for Behavior Analysis
By tim daly, mark pleszkoch, richard c. linger (oak ridge national laboratory).
In this report, the authors present research to compute the behavior of software with mathematical precision and how this research has been implemented.
FloCon 2011 Proceedings
January 10, 2011 • white paper.
These papers were presented at FloCon 2011, where participants discussed dark space, web servers, spam, and the susceptibility of DNS servers to cache poisoning.
Deriving Candidate Technical Controls and Indicators of Insider Attack from Socio-Technical Models and Data
January 1, 2011 • technical note, by michael hanley.
In this 2011 report, Michael Hanley demonstrates how a method for modeling insider crimes can create candidate technical controls and indicators.
Trust and Trusted Computing Platforms
By archie d. andrews, jonathan m. mccune, david fisher.
This technical note examines the Trusted Platform Module, which arose from work related to the Independent Research and Development project "Trusted Computing in Extreme Adversarial Environments: Using Trusted Hardware as …
Enabling Agility Through Architecture
December 16, 2010 • white paper, by nanette brown, ipek ozkaya, robert nord.
Enabling Agility Through Architecture: A Crosstalk article by Nanette Brown, Rod Nord, and Ipek Ozkaya.
Software Supply Chain Risk Management: From Products to Systems of Systems
December 1, 2010 • technical note, by christopher j. alberts, carol woody, rita c. creel, robert j. ellison, audrey j. dorofee.
In this report, the authors consider current practices in software supply chain analysis and suggest some foundational practices.
A Taxonomy of Operational Cyber Security Risks
By james j. cebula, lisa r. young.
In this report, the authors present a taxonomy of operational cyber security risks and its harmonization with other risk and security activities.
Source Code Analysis Laboratory (SCALe) for Energy Delivery Systems
December 1, 2010 • technical report, by philip miller, jefferson welch, james mccurley, david svoboda, robert w. stoddard, robert c. seacord, will dormann.
In this report, the authors describe the Source Code Analysis Laboratory (SCALe), which tests software for conformance to CERT secure coding standards.
Adaptive Flow Control for Enabling Quality of Service in Tactical Ad Hoc Wireless Networks
By edwin j. morris, soumya simanta, scott hissam, jeffrey hansen, daniel plakosh, b. craig meyers, lutz wrage.
The network infrastructure for users such as emergency responders or warfighters is wireless, ad hoc, mobile, and lacking in sufficient bandwidth. This report documents the results from 18 experiments to …
Combining Architecture-Centric Engineering with the Team Software Process
By robert nord, felix bachmann, jim mchale.
ACE methods and the TSP provides an iterative approach for delivering high quality systems on time and within budget. The combined approach helps organizations that must set an architecture/developer team …
Beyond Technology Readiness Levels for Software: U.S. Army Workshop Report
By suzanne miller, cecilia albert, stephen blanchette, jr..
This report synthesizes presentations, discussions, and outcomes from the "Beyond Technology Readiness Levels for Software" workshop from August 2010.
The CERT Approach to Cybersecurity Workforce Development
By christopher may, josh hammerstein.
This report describes a model commonly used for developing and maintaining a competent cybersecurity workforce, explains some operational limitations associated with that model, and presents a new approach to cybersecurity …
Guide for SCAMPI Appraisals: Accelerated Improvement Method (AIM)
December 1, 2010 • special report.
This document provides guidance to lead appraisers and appraisal teams unfamiliar with TSP+ when conducting Standard CMMI Appraisal Method for Process Improvement (SCAMPI) appraisals within organizations that use the TSP+ …
Implementation Guidance for the Accelerated Improvement Method (AIM)
This 2010 report describes the (AIM which helps an organization to implement high-performance, high-quality CMMI practices much more quickly than industry norms.
Executive Overview: Best Practices for Adoption of Cloud Computing
November 24, 2010 • white paper.
This paper describes the SEI approach to cloud computing research for the DoD.
Executive Overview: Employing SOA to Achieve Information Dominance
The current ability to implement systems in the DoD based on SOA technologies falls short of the DoD's goals. To close the gaps in these areas, research is needed in …
French language translation of CMMI for Development, V1.3
November 1, 2010 • white paper.
This is The French language translation of CMMI for Development, V1.3.
Dutch language translation of CMMI for Development V1.3
This document is the Dutch language translation of CMMI-DEV V1.3.
Spanish Language Translation of CMMI for Development, v1.3
Spanish language translation of CMMI for Development, v1.3
Traditional Chinese Language Translation of CMMI for Development V1.3
CMMI-DEV V1.3 Traditional Chinese Translation
A Workshop on Analysis and Evaluation of Enterprise Architectures
November 1, 2010 • technical note, by john klein, michael j. gagliardi.
This report summarizes a workshop on the analysis and evaluation of enterprise architectures that was held at the SEI in April of 2010.
Performance Analysis of WS-Security Mechanisms in SOAP-Based Web Services
November 1, 2010 • technical report, by gunnar peterson, marc novakouski, soumya simanta, edwin j. morris, grace lewis.
This paper presents the results of a series of experiments targeted at analyzing the performance impact of adding WS-Security, a common security standard used in IdM frameworks, to SOAP-based web …
CMMI for Acquisition, Version 1.3
The CMMI-ACQ model provides guidance for applying CMMI best practices in an acquiring organization. Best practices in the model focus on activities for initiating and managing the acquisition of products …
CMMI for Development, Version 1.3
This 2010 report details CMMI for Development (CMMI-DEV) V.1.3, which provides a comprehensive integrated set of guidelines for developing products and services.
CMMI for Services, Version 1.3
This 2010 report details CMMI for Services (CMMI-SVC) V.1.3, which provides a comprehensive integrated set of guidelines for providing superior services.
Strategic Planning with Critical Success Factors and Future Scenarios: An Integrated Strategic Planning Framework
By linda parker gates.
This report explores the value of enhancing typical strategic planning techniques with the CSF method and scenario planning.
Designing for Incentives: Better Information Sharing for Better Software Engineering
October 31, 2010 • white paper.
This paper outlines a research agenda in bridging to the economic theory of mechanism design, which seeks to align incentives in multi-agent systems with private information and conflicting goals.
Cloud Computing Basics Explained
September 30, 2010 • white paper.
This paper seeks to help organizations understand cloud computing essentials, including drivers for and barriers to adoption, in support of making decisions about adopting the approach.
Primer on SOA Terms
September 1, 2010 • white paper.
This white paper presents basic terminology related to Service- Oriented Architecture (SOA). The goal of the paper is to establish a baseline of terms for service-oriented systems.
T-Check in System-of-Systems Technologies: Cloud Computing
September 1, 2010 • technical note, by grace lewis, harrison d. strowd.
The purpose of this report is to examine a set of claims about cloud computing adoption.
Emerging Technologies for Software-Reliant Systems of Systems
The purpose of this report is to present an informal survey of technologies that are, or are likely to become, important for software-reliant systems of systems in response to current …
Integrated Measurement and Analysis Framework for Software Security
By christopher j. alberts, robert w. stoddard, julia h. allen.
In this report, the authors address how to measure software security in complex environments using the Integrated Measurement and Analysis Framework (IMAF).
Security Requirements Reusability and the SQUARE Methodology
In this report, the authors discuss how security requirements engineering can incorporate reusable requirements.
Measuring Operational Resilience Using the CERT® Resilience Management Model
By noopur davis, julia h. allen.
In this 2010 report, the authors begin a dialogue and establish a foundation for measuring and analyzing operational resilience.
Program Executive Officer Aviation, Major Milestone Reviews: Lessons Learned Report
September 1, 2010 • technical report, by kate ambrose, scott reed.
This report documents ideas and recommendations for improving the overall acquisition process and presents the actions taken by project managers in several programs to develop, staff, and obtain approval for …
Smart Grid Maturity Model, Version 1.1: Model Definition
Success in acquisition: using archetypes to beat the odds, by william e. novak, linda levine.
This report describes key elements in systems thinking, provides an introduction to general systems archetypes, and applies these concepts to the software acquisition domain.
Building Assured Systems Framework
By julia h. allen, nancy r. mead.
This report presents the Building Assured Systems Framework (BASF) that addresses the customer and researcher challenges of selecting security methods and research approaches for building assured systems.
Using TSP Data to Evaluate Your Project Performance
By bill nichols, james mccurley, shigeru sasao.
A set of measures was determined that allow analyses This report discusses the application of a set of measures to a data set of 41 TSP projects from an organization …
Suggestions for Documenting SOA-Based Systems
This report provides suggestions for documenting service-oriented architecture-based systems based on the Views & Beyond (V&B) software documentation approach.
Exploring Acquisition Strategies for Adopting a Software Product Line
August 25, 2010 • white paper, by john k. bergey, lawrence g. jones.
Some basics of software product line practice, the challenges that make product line acquisition unique, and three basic acquisition strategies are all part of this white paper.
YAF: Yet Another Flowmeter
August 23, 2010 • white paper, by chris inacio, brian trammell.
In this paper, the authors describe issues encountered in designing and implementing YAF.
A Continuous Time List Capture Model for Internet Threats
August 4, 2010 • white paper, by rhiannon weaver.
In this paper, Rhiannon Weaver describes a population study of malware files under the CTLC framework and presents a simulation study as well as future work.
Software Assurance Curriculum Project Volume I: Master of Software Assurance Reference Curriculum
August 1, 2010 • technical report, by james mcdonald (monmouth university), richard c. linger (oak ridge national laboratory), thomas b. hilburn (embry-riddle aeronautical university), andrew j. kornecki (embry-riddle aeronautical university), mark a. ardis (stevens institute of technology), julia h. allen, nancy r. mead.
In this report, the authors present a master of software assurance curriculum that educational institutions can use to create a degree program or track.
Risk Management Framework
By audrey j. dorofee, christopher j. alberts.
In this report, the authors specify (1) a framework that documents best practice for risk management and (2) an approach for evaluating a program's risk management practice in relation to …
Software Assurance Curriculum Project Volume II: Undergraduate Course Outlines
By thomas b. hilburn (embry-riddle aeronautical university), richard c. linger (oak ridge national laboratory), nancy r. mead.
In this report, the authors describe seven courses for an undergraduate curriculum specialization for software assurance.
A Framework for Modeling the Software Assurance Ecosystem: Insights from the Software Assurance Landscape Project
By christopher j. alberts, carol woody, lisa brownsword, andrew p. moore.
In this report, the authors describe the SEI Assurance Modeling Framework, piloting to prove its value, and insights gained from that piloting.
COVERT: A Framework for Finding Buffer Overflows in C Programs via Software Verification
By arie gurfinkel, sagar chaki.
In this report, the authors present COVERT, an automated framework for finding buffer overflows in C programs using software verification tools and techniques.
Measurement and Analysis Infrastructure Diagnostic, Version 1.0: Method Definition Document
By mark kasunic.
This 2010 report is a guidebook for conducting a Measurement and Analysis Infrastructure Diagnostic (MAID) evaluation.
Security Requirements Engineering
July 14, 2010 • white paper.
In this paper, Nancy Mead how a systematic approach to security requirements engineering helps to avoid problems.
Adapting the SQUARE Process for Privacy Requirements Engineering
July 1, 2010 • technical note, by nancy r. mead, ashwini bijwe (carnegie mellon university).
In this 2010 report, the authors explore how the SQUARE process can be adapted for privacy requirements engineering in software development.
Team Software Process (TSP) Body of Knowledge (BOK)
July 1, 2010 • technical report, by timothy a. chick, bill nichols, watts s. humphrey, marsha pomeroy-huff.
The TSP BOK helps practitioners and employers assess and improve their skills, and shows academic institutions how to incorporate TSP into their engineering courses.
Programmatic and Constructive Interdependence: Emerging Insights and Predictive Indicators of Development Resource Demand
By mark kasunic, william anderson, david zubrow, paul l. hardin, iii, mary m. brown, robert m. flowe, james mccurley.
This 2010 report describes a series of ongoing research efforts that investigate the role of interdependence in the acquisition of major defense acquisition programs.
Rayon: A Unified Framework for Data Visualization
June 24, 2010 • white paper, by phil groce.
In this paper, Phil Groce describes the Rayon visualization toolkit, developed to augment network analytic information and improve analytic operations.
Finding Malicious Activity in Bulk DNS Data
By ed stoner.
In this paper, Ed Stoner describes techniques for detecting certain types of malicious traffic.
Best Practices for National Cyber Security: Building a National Computer Security Incident Management Capability
June 1, 2010 • special report, by john haller, matthew j. butkovic, samuel a. merrell, bradford j. willke.
In this report, the authors provide insight that interested organizations and governments can use to develop a national incident management capability.
Team Software Process (TSP) Coach Mentoring Program Guidebook, Version 1.1
By jefferson welch, alan willett, marsha pomeroy-huff, robert cannon, timothy a. chick, bill nichols, jim mchale.
This guidebook is designed to explain the steps for becoming an SEI-Certified Team Software Process (TSP) Coach or SEI-Certified TSP Mentor Coach, with emphasis on guiding individuals through the mentoring …
Survivability Analysis Framework
June 1, 2010 • technical note.
In this report, the authors describe the Survivability Analysis Framework, which is used to evaluate critical operational capabilities.
Software Product Lines: Report of the 2010 U.S. Army Software Product Line Workshop
June 1, 2010 • technical report, by linda m. northrop, sholom g. cohen, john k. bergey, gary chastek, patrick donohoe, lawrence g. jones.
This report synthesizes presentations and discussions from a 2010 workshop to discuss product line practices and operational accomplishments.
Performance Effects of Measurement and Analysis: Perspectives from CMMI High Maturity Organizations and Appraisers
By dennis goldenson, james mccurley.
This report describes results from two recent surveys conducted by the Software Engineering Institute (SEI) to collect information about the measurement and analysis activities of software systems development organizations.
Resource Allocation in Distributed Mixed-Criticality Cyber-Physical Systems
May 31, 2010 • white paper, by karthik lakshmanan.
This paper explains a formal overload-resilience metric called ductility.
The Illusion of Certainty - Paper
May 25, 2010 • white paper, by grady campbell.
In this 2010 paper, Grady Campbell - delivered at the 7th Acquisition Research Symposium - argues that a new approach to acquisition is needed that recognizes that hiding uncertainty is …
Edge Enabled Systems
May 19, 2010 • white paper, by zacharie hall (aberdeen proving ground), joseph giampapa, rick kazman, kurt c. wallnau, daniel plakosh.
This paper describes the characteristics of edge systems and the edge organizations in which these systems operate, and make initial recommendations about how such systems and organizations can be created …
Managing Variation in Services in a Software Product Line Context
May 1, 2010 • technical note, by sholom g. cohen, robert w. krut, jr..
This report highlights the mutual benefits of combining systematic reuse approaches from product line development with flexible approaches for implementing business processes in a service oriented architecture.
Evaluating and Mitigating Software Supply Chain Security Risks
By carol woody, robert j. ellison, john b. goodenough, charles weinstock.
In this 2010 report, the authors identify software supply chain security risks and specify evidence to gather to determine if these risks have been mitigated.
Relating Business Goals to Architecturally Significant Requirements for Software Systems
By paul c. clements, len bass.
The purpose of this report is to facilitate better elicitation of high-pedigree quality attribute requirements. Toward this end, we want to be able to elicit business goals reliably and understand …
Case Study: Model-Based Analysis of the Mission Data System Reference Architecture
May 1, 2010 • technical report, by peter h. feiler, kurt woodham (l-3 communications-titan group), david p. gluch.
This report describes how AADL support an instantiation of a reference architecture, address architectural themes, and provide a foundation for the analysis of performance elements and system assurance concerns.
Identifying Anomalous Port-Specific Network Behavior
In this report, Rhiannon Weaver describes a method for identifying network behavior that may be a sign of coming internet-wide attacks.
CERT Resilience Management Model, Version 1.0
By david w. white, julia h. allen, richard a. caralli, lisa r. young, pamela d. curtis.
In this report, the authors present CERT-RMM, an approach to managing operational resilience in complex, risk-evolving environments.
Java Concurrency Guidelines
By fred long, dhruv mohindra, david svoboda, robert c. seacord.
In this report, the authors describe the CERT Oracle Secure Coding Standard for Java, which provides guidelines for secure coding in Java.
Specifications for Managed Strings, Second Edition
By robert c. seacord, david svoboda, fred long, raunak rungta, hal burch.
In this report, the authors describe a managed string library for the C programming language.
Considerations for Using Agile in DoD Acquisition
April 1, 2010 • technical note, by mary ann lapham, alfred schenker, daniel burton, charles (bud) hammons, ray c. williams.
This 2010 report explores the questions: Can Agile be used in the DoD environment? If so, how?
As-If Infinitely Ranged Integer Model, Second Edition
By timothy wilson, thomas plum (plum hall, inc.), roger dannenberg (school of computer science, carnegie mellon university), alex volkovitsky, robert c. seacord, will dormann, david keaton, david svoboda.
In this report, the authors present the as-if infinitely ranged (AIR) integer model, a mechanism for eliminating integral exceptional conditions.
Data Rights for Proprietary Software Used in DoD Programs
By julie b. cohen, bonnie troup (the aerospace corporation), henry ouyang (the aerospace corporation).
This report examines how data rights issues were addressed in the TSAT program. It also reviews concerns posed by the use of commercial software in the TSAT program's Space Segment, …
Characterizing Technical Software Performance Within System of Systems Acquisitions: A Step-Wise Methodology
April 1, 2010 • technical report, by bryce l. meyer, james wessel.
This report focuses on both qualitative and quantitative ways of determining the current state of SWP (software performance) in terms of both test coverage and confidence for SOA-based SoS environments.
Measuring Software Security
March 1, 2010 • white paper.
This paper, extracted from the 2009 CERT Research Report, describes planned research tasks in the field of software security.
Cyber Assurance
By robert j. ellison, carol woody, christopher j. alberts.
This paper, extracted from the 2009 CERT Research Report, describes planned research tasks in the field of cyber assurance.
Evaluating Software's Impact on System and System and System of Systems Reliability
In this paper, the authors discuss how system engineers are uncertain about how to determine the impact of software on overall system.
A Research Agenda for Service-Oriented Architecture (SOA): Maintenance and Evolution of Service-Oriented Systems
March 1, 2010 • technical note.
This 2010 report describes the agenda of an SEI-led group that was formed to explore the business, engineering, and operations aspects of service-oriented architecture.
Extending Team Software Process (TSP) to Systems Engineering: A NAVAIR Experience Report
March 1, 2010 • technical report, by timothy a. chick, anita carleton, jeff schwalb, delwyn kellogg, james w. over.
This 2010 report communicates status, progress, lessons learned, and results on a joint collaboration between the SEI and NAVAIR.
Testing in Service-Oriented Environments
By david j. carney, sriram balasubramaniam, john morley, patrick r. place, soumya simanta, william anderson, edwin j. morris.
This report makes 65 recommendations for improving testing in service-oriented environments. It covers testing functionality and testing for interoperability, security, performance, and reliability qualities.
Reports from the Field on System of Systems Interoperability Challenges and Promising Approaches
By carol sledge.
In this report, Carol Sledge identifies challenges and successful approaches to achieving system of systems (SoS) interoperability.
Adapting the SQUARE Method for Security Requirements Engineering to Acquisition
February 22, 2010 • white paper.
In this paper, Nancy Mead adapts the SQUARE process for security requirements engineering to different acquisition situations.
0-knowledge fuzzing
February 9, 2010 • white paper, by vincenzo iozzo (zynamics).
In this paper, Vincenzo Iozzo describes how to effectively fuzz with no knowledge of the user-input and the binary.

MITRE, CWE, and CERT Secure Coding Standards
February 8, 2010 • white paper, by robert c. seacord, robert a. martin.
In this paper, the authors summarize the Common Weakness Enumeration (CWE) and CERT Secure Coding Standards and the relationship between the two.
A Probabilistic Population Study of the Conficker-C Botnet
February 1, 2010 • white paper.
In this paper, Rhiannon Weaver estimates the number of active machines per hour infected with the Conficker-C worm using a probability model.
Instrumented Fuzz Testing Using AIR Integers (Whitepaper)
By will dormann, robert c. seacord, david keaton, roger dannenberg (school of computer science, carnegie mellon university), thomas plum (plum hall, inc.), timothy wilson.
In this paper, the authors present the as-if infinitely ranged (AIR) integer model, which provides a mechanism for eliminating integral exceptional conditions.
Spotlight On: Insider Threat from Trusted Business Partners
By randall f. trzeciak, andrew p. moore, derrick spooner, dawn cappelli, robert weiland (carnegie mellon university).
In this report, the authors focus on cases in which the insider was employed by a trusted business partner of the victim organization.
Profiling Systems Using the Defining Characteristics of Systems of Systems (SoS)
February 1, 2010 • technical note, by donald firesmith.
This technical note identifies and describes the characteristics that have been used in various definitions of the term system of systems.
Proceedings of the 3rd International Workshop on a Research Agenda for Maintenance and Evolution of Service-Oriented Systems (MESOA 2009)
February 1, 2010 • special report.
This report contains selected papers from the 3rd International Workshop on a Research Agenda for Maintenance and Evolution of Service-Oriented Systems (MESOA 2009).
Acquisition Archetype: Shooting the Messenger
January 20, 2010 • white paper.
When problems are detected in programs, everyone needs to listen and work together towards a solution. Shooting the messenger only delays the process, and hurts program morale.
Industry Standard Notation for Architecture-Centric Model-Based Engineering
In this paper, Peter Feiler describes the AADL, an industry standard for modeling and analyzing the architecture of software-reliant systems.
Approaches to Process Performance Modeling: A Summary from the SEI Series of Workshops on CMMI High Maturity Measurement and Analysis
January 1, 2010 • technical report.
This report summarizes the results from the second and third high maturity measurement and analysis workshops.
Evaluating the Software Design of a Complex System of Systems
By steven crosson (u.s. army), barry boehm (university of california, los angeles), stephen blanchette, jr..
The report examines the application of the life-cycle architecture milestone to the software and computing elements of the former Future Combat Systems program.
Secure Coding Governance and Guidance
December 4, 2009 • white paper.
In this paper, the authors propose the use of secure coding standards in the development of software for surface combatants and submarines.
Secure Coding Plan
This plan is a government-provided customizable document that is part of the acquisition's government reference library.
Generalized Criteria and Evaluation Method for Center of Excellence: A Preliminary Report
December 1, 2009 • technical note, by william craig (amrdec sed), clay kaylor (amrdec sed), john porter (amrdec sed), scott reed, matt fisher, suzanne miller.
Criteria and standards to certify an organization as a COE are presented in this Carnegie Mellon Software Engineering Institute preliminary report.
A Structured Approach for Reviewing Architecture Documentation
By rich hilliard, david emery, robert nord, paul c. clements.
This technical note proposes a structured approach for reviewing architecture documentation that is centered on the documentation's stakeholders and engages them in a guided manner so as to ensure that …
Measurement and Analysis Infrastructure Diagnostic (MAID) Evaluation Criteria, Version 1.0
December 1, 2009 • technical report, by software engineering measurement and analysis (sema) group.
This 2009 report presents the criteria used during a MAID evaluation that serve as a checklist to rate the quality of an organization's measurement and analysis practices and the quality …
Results of SEI Independent Research and Development Projects (FY 2009)
By jörgen hansson (university of skovde), len bass, lutz wrage, cal waits, matthew geiger, karthik lakshmanan, ragunathan rajkumar, peter h. feiler, kurt c. wallnau, dionisio de niz, paul c. clements, mark h. klein, james ivers, daniel plakosh, kristopher rush, jeffrey hansen, gabriel moreno, scott hissam.
In this report, the authors describe the SEI independent research and development (IRAD) projects conducted during fiscal year 2009.
An Everyday Example of Architecture Documentation: Subway Maps
November 30, 2009 • white paper, by paul c. clements.
This white paper explores the idea that subway maps provide a good, common example of architecture documentation and that they might be instructive about good software architecture documentation.
System of Systems Software Assurance
November 2, 2009 • white paper, by john b. goodenough.
This white paper describes SEI investigation into ways to provide justified confidence that a system of systems will behave as needed in its actual and evolving usage environments.
Proceedings of the Workshop on Software Engineering Foundations for End-User Programming (SEEUP 2009)
November 1, 2009 • special report, by brad myers, len bass, dennis b. smith, grace lewis.
This report presents the papers that were given at SEEUP 2009, held at the 31st ICSE in Vancouver, British Columbia on May 23, 2009.
The Watts New Collection: Columns by the SEI’s Watts Humphrey
By watts s. humphrey.
news@sei columns written by the SEI's Watts Humphrey between June 1998 and August 2008
Evaluating Artifact Quality from an Appraisal Perspective
November 1, 2009 • technical note, by emanuel r. baker, matt fisher, charlene gross.
This report explores the lack of agreement among SCAMPI Lead Appraisers about what “artifact quality” means in the SCAMPI process context.
Evaluating Process Quality from an Appraisal Perspective
By matt fisher, emanuel r. baker.
This report explores the lack of agreement among SCAMPI Lead Appraisers about what “process quality” means in the SCAMPI process context.
A Method for Assessing Technical Progress and Quality Throughout the System Life Cycle
By robert ferguson, rita c. creel, summer c. fowler.
This 2009 paper provides a framework for evaluating a system from several perspectives for a comprehensive picture of progress and quality.
Integrating CMMI and TSP/PSP: Using TSP Data to Create Process Performance Models
By shurei tamura.
This report describes the fundamental concepts of process performance models (PPMs) and describes how they can be created using data generated by projects following the TSP.
System Architecture Virtual Integration: An Industrial Case Study
November 1, 2009 • technical report, by lutz wrage, jörgen hansson (university of skovde), peter h. feiler, dionisio de niz.
This report introduces key concepts of the SAVI paradigm and discusses the series of development scenarios used in a POC demonstration to illustrate the feasibility of improving the quality of …
The Software Quality Profile
October 29, 2009 • white paper.
The software community has been slow to use data to measure software quality. This paper discusses the reasons for this problem and describes a way to use process measurements to …
Acquisition Archetypes: Happy Path Testing
October 15, 2009 • white paper, by linda levine, william e. novak.
When time and budget are tight, it's tempting to follow the "happy path" in testing. But be careful: it may be a path that brings your program great unhappiness.
Acquisition Archetypes: Brooks' Law
This April 2009 whitepaper focuses on the problems of underspending, which can result in funds being shifted from one acquisition program to another.
The Economics of CMMI
This paper provides practical guidance for CMMI adopters in the effective use of CMMI, based upon established NDIA principles.
Insights on Program Success
October 1, 2009 • special report, by systems and software consortium, inc., the software engineering institute.
This 2009 report examines the reasons why some programs fail and studies the factors that lead to program success.
A Bibliography of the Personal Software Process (PSP) and the Team Software Process (TSP)
By marlene macdonald, rachel callison.
This 2009 special report provides a bibliography of books, articles, and other literature concerning the PSP and TSP methodologies.
Towards an Assurance Case Practice for Medical Devices
October 1, 2009 • technical note, by charles weinstock, john b. goodenough.
In this report, the authors explore how to enable manufacturers and federal regulators gain confidence in software-dominated medical devices.
Data Model as an Architectural View
By paulo merson.
This 2009 report describes the data model as an architectural style in an effort to help architects apply this style to create data model architectural views.
Secure Design Patterns
October 1, 2009 • technical report, by chad dougherty, david svoboda, robert c. seacord, kirk sayre, kazuya togashi (jpcert/cc).
In this report, the authors describe a set of general solutions to software security problems that can be applied in many different situations.
CMMI and Medical Device Engineering
September 29, 2009 • white paper, by david w. walker.
This paper summarizes the comparison performed between the CMMI and the regulations and standards that drive software intensive medical device product development.
Lessons Learned from a Large, Multi-Segment, Software-Intensive System
September 1, 2009 • technical note, by mary ann lapham, john t. foreman.
This 2009 report contains a series of observations and their associated lessons learned from a large, multi-segment, software-intensive system.
Effectiveness of the Vulnerability Response Decision Assistance (VRDA) Framework
August 1, 2009 • white paper, by fumihiko kousaka (jpcert/cc), shawn mccaffrey (carnegie mellon university), masanori yamaguchi (iij technology inc.), robert weiland (carnegie mellon university), joseph b. kadane, kazuya togashi (jpcert/cc), christopher king, art manion.
In this paper, the authors describe the Vulnerability Response Decision Assistance (VRDA) framework, a decision support and expert system.
The Personal Software Process (PSP) Body of Knowledge, Version 2.0
August 1, 2009 • special report, by robert cannon, marsha pomeroy-huff, julia l. mullaney, timothy a. chick, bill nichols.
The Personal Software Process (PSP) body of knowledge (BOK) provides guidance to software professionals who are interested in using proven-effective, disciplined methods to improve their personal software development process.
Formulation of a Production Strategy for a Software Product Line
August 1, 2009 • technical note, by john mcgregor, gary chastek, patrick donohoe.
This 2009 report describes a technique for formulating the production strategy of a production system.
Realizing and Refining Architectural Tactics: Availability
August 1, 2009 • technical report, by james scott, rick kazman.
Tactics are fundamental elements of software architecture that an architect employs to meet a system's quality requirements. This report describes an updated set of tactics that enable the architect to …
Team Software Process (TSP) Coach Mentoring Program Guidebook
German language translation of cmmi for development, v1.2, july 31, 2009 • white paper.
The German language translation of CMMI for Development, V1.2.
Insider Theft of Intellectual Property for Business Advantage: A Preliminary Model
July 20, 2009 • white paper, by randall f. trzeciak, andrew p. moore, dawn cappelli, thomas c. caron (john heinz iii college, school of information systems management, carnegie mellon university), eric d. shaw.
In this paper, the authors describe general observations about a preliminary system dynamics model of insider crime based on our empirical data.
Why Don't They Practice What We Preach?
July 17, 2009 • white paper.
One of the most intractable problems in software is getting engineers to consistently use effective methods. The Software Engineering Institute has worked on this problem for a number of years …
Resiliency Management Model: Communications
July 1, 2009 • white paper.
In this paper, the authors describe the purpose of Communications: to develop, deploy, and manage communications to support resiliency activities and processes.
Privacy Risk Assessment Case Studies in Support of SQUARE
July 1, 2009 • special report, by nancy r. mead, varokas panusuwan, prashanth batlagundu.
In this report, the authors describe enhancements to the SQUARE method for addressing privacy requirements.
A Proactive Means for Incorporating a Software Architecture Evaluation in a DoD System Acquisition
July 1, 2009 • technical note, by john k. bergey.
This technical note provides guidance on how to contractually incorporate architecture evaluations in an acquisition.
Building Process Improvement Business Cases Using Bayesian Belief Networks and Monte Carlo Simulation
By ben linders.
This report describes a collaboration between the SEI and Ericsson Research and Development to build a business case using high maturity measurement approaches that require limited measurement effort.
As-if Infinitely Ranged Integer Model
By thomas plum (plum hall, inc.), alex volkovitsky, timothy wilson, robert c. seacord, david svoboda, david keaton.
In this report, the authors present the as-if infinitely ranged (AIR) integer model, which eliminates integer overflow and integer truncation in C and C++ code.
People Capability Maturity Model (P-CMM), Version 2.0, Second Edition
July 1, 2009 • technical report, by bill curtis (cast research labs), william e. hefley, sarah miller.
This report documents an update to the People CMM, Version 2, which updates informative material within the People CMM and its subpractices and provides new information learned from the continuing …
Revealing Cost Drivers for Systems Integration and Interoperability Through Q Methodology
June 10, 2009 • white paper, by william anderson, maureen brown (university of north carolina).
The findings suggest that Q Methodology may prove helpful in isolating many of the non-technical latent cost factors associated with system integration and interoperability.
Spanish language translation of CMMI for Development, V1.2
June 5, 2009 • white paper.
The Spanish language translation of CMMI for Development, V1.2 was performed by Cátedra de Mejora de Procesos de Software en el Espacio, Iberoamericano de la Universidad Politécnica de Madrid and …
Spotlight On: Insider Theft of Intellectual Property Inside the United States Involving Foreign Governments or Organizations (2009)
June 1, 2009 • white paper, by dawn cappelli, derrick spooner, randall f. trzeciak, andrew p. moore.
In this report, the authors focus on employees, contractors, and business partners who stole intellectual property to benefit a foreign entity.
Computational Evaluation of Software Security Attributes
By richard c. linger (oak ridge national laboratory), gwendolyn h. walton, thomas a. longstaff.
This paper provides an introduction to the CSA approach, provides behavioral requirements for security attributes, and discusses possible application of the CSA approach.
Measurement for Improvement: Successful Measurement Practices Used in Army Software Acquisition
June 1, 2009 • technical note, by james wessel, robert ferguson.
This report summarizes the findings of a study conducted for the Army to find and describe software measurement practices that are being used successfully.
A Scenario-Based Technique for Developing SOA Technical Governance
By grace lewis, edwin j. morris, soumya simanta, dennis b. smith, sriram balasubramaniam.
Organizations can make the available SOA governance frameworks more effective in their organizations using the scenario-based tailoring technique introduced in this technical note.
Incremental Development in Large-Scale Systems: Finding the Programmatic IEDs
By charles (bud) hammons.
This paper explores how continued use of the acquisition roadmaps opens up the potential for running into program pitfalls (programmatic IEDs) that aren‰t acknowledged on the map at hand.
Integrating Quality-attribute Reasoning Frameworks in the ArchE Design Assistant
May 5, 2009 • white paper, by felix bachmann, philip bianco, len bass, hyunwoo kim, andres diaz-pace.
Bachmann et al present their work on a design assistant called ArchE that provides third-party researchers with an infrastructure to integrate their own quality-attribute models.
Incorporating Software Requirements into the System RFP: Survey of RFP Language for Software by Topic, v. 2.0
May 1, 2009 • special report.
The 2009 report defines and communicates software engineering and management events necessary to support the successful acquisition of software-intensive systems.
Evaluating Hazard Mitigations with Dependability Cases
April 21, 2009 • white paper, by matthew r. barry (software intensive systems, inc.), john b. goodenough.
In this 2009 paper, the authors present an example to show the value a dependability case adds to a traditional hazard analysis.
Risk Detection and Mitigation Metrics and Design Check Lists for Real Time and Embedded Systems
April 19, 2009 • white paper, by doug locke, lui r. sha.
A whitepaper by Lui Sha of the University of Illinois and C. Douglass Locke of LC System Services Inc. The paper discusses risk detection and mitigation metrics and design check …
Assurance Cases for Design Analysis of Complex System of Systems Software
April 1, 2009 • white paper, by stephen blanchette, jr..
This paper discusses the application of assurance cases as a means of building confidence that the software design of a complex system of systems will actually meet the operational objectives …
Acquisition Archetypes: Longer Begets Bigger
Planning for a long development period doesn't always solve acquisition scheduling problems. Sometimes it makes them worse.
Acquisition Archetypes: Robbing Peter to Pay Paul
This April 2009 whitepaper is one in a short series of acquisition failures. This paper focuses on the problems of underspending, which can result in funds being shifted from one …
April 1, 2009 • Special Report
By antonio drommi, john harrison, jeff ingalsbe (university of detroit mercy), art conklin, james rainey, dan shoemaker (university of detroit mercy), nancy r. mead, julia h. allen.
In this report, the authors provide advice for those making a business case for building software assurance into software products during software development.
Impact of Army Architecture Evaluations
By stephen blanchette, jr., john k. bergey, robert nord, mark h. klein.
This 2009 report describes the results of a study of the impact that the ATAM evaluations and QAWs had on Army programs.
A Workshop on Architecture Competence
April 1, 2009 • technical note, by jeannine siviy, len bass, rick kazman, paul c. clements, mark h. klein, john klein.
This report summarizes a June 2008 architecture competence workshop where practitioners discussed key issues in assessing architecture competence in organizations.
A Framework for Categorizing Key Drivers of Risk
April 1, 2009 • technical report.
This 2009 report features a systemic approach for managing risk that takes into account the complex nature of distributed environments.
Software Product Lines: Report of the 2009 U.S. Army Software Product Line Workshop
By sholom g. cohen, lawrence g. jones, john k. bergey, matt fisher, patrick donohoe.
This report is a synthesis of the presentations and discussions that took place during the 2009 U.S. Army Software Product Line Workshop.
Acquisition Archetypes: Everything for Everybody
March 1, 2009 • white paper.
When projects attempt to please too many customers, complexity mounts, schedules slip, costs expand, and no one is happy.
Spotlight On: Malicious Insiders with Ties to the Internet Underground Community
By michael hanley, dawn cappelli, andrew p. moore, randall f. trzeciak.
In this report, the authors focus on insider threat cases in which the insider had relationships with the internet underground community.
An Initial Comparative Analysis of the CMMI Version 1.2 Development Constellation and the ISO 9000 Family
March 1, 2009 • special report, by david kitson, robert vickroy, john walz, dave wynn.
A preliminary, high-level comparison of the CMMI Development constellation and the ISO 9001:2000 family of process improvement standards.
U.S. Army Workshop on Exploring Enterprise, System of Systems, System, and Software Architectures
March 1, 2009 • technical report, by stephen blanchette, jr., john k. bergey, john klein, michael j. gagliardi, william wood, robert wojcik, paul c. clements.
This report confirms that various architectural genres enjoy more commonalities than differences. Each one has its own important knowledge base, and openness among the various architectural tasks within an organization …
Deploying TSP on a National Scale: An Experience Report from Pilot Projects in Mexico
By rafael salazar, bill nichols.
This report communicates status, progress, lessons learned, and next steps for the Mexican TSP Initiative.
CMMI for Services V1.2 (Traditional Chinese)
February 1, 2009 • white paper.
The Traditional Chinese translation of CMMI for Services V.1.2.
Multi-View Decision Making (MVDM) Workshop
February 1, 2009 • special report, by christopher j. alberts, carol woody, james smith.
In this report, the authors describe the value of multi-view decision making, a set of practices that reflect the realities of complex development efforts.
Overview of the Lambda-* Performance Reasoning Frameworks
February 1, 2009 • technical report, by jeffrey hansen, gabriel moreno.
This report provides an overview of the Lambda-* performance reasoning frameworks, their current capabilities, and ongoing research.
Use and Organizational Effects of Measurement and Analysis in High Maturity Organizations: Results from the 2008 SEI State of Measurement and Analysis Practice Surveys
By dennis goldenson, robert w. stoddard, james mccurley.
This report contains results from a survey of high maturity organizations conducted by the Software Engineering Institute (SEI) in 2008. The questions center on the use of process performance modeling …
CMMI for Services, Version 1.2
A model of best practices to improve the processes of service providers.
The Arcade Game Maker Pedagogical Product Line
January 5, 2009 • white paper.
The Arcade Game Maker product line is an example product line created to support learning about and experimenting with software product lines in the classroom.
Common Sense Guide to Prevention and Detection of Insider Threats 3rd Edition – Version 3.1
January 1, 2009 • white paper, by andrew p. moore, randall f. trzeciak, timothy j. shimeall, dawn cappelli.
In this paper, the authors present findings from examining insider crimes in a new way and add new practices that were not present in the second edition.
Developing An Acquisition Strategy
An acquisition strategy is of great importance to those organizations that primarily acquire rather than develop.
High-Fidelity E-Learning: The SEI's Virtual Training Environment (VTE)
January 1, 2009 • technical report, by david w. white, julia h. allen, jim wrubel.
In this 2008 report, the authors compare various approaches and tools used to capture and analyze evidence from computer memory.
Statistical-Based WCET Estimation and Validation
December 31, 2008 • white paper, by gabriel moreno, jeffrey hansen, scott hissam.
This paper presents a measurement-based approach that produces both a WCET (Worst Case Execution Time) estimate and a prediction of the probability that a future execution time will exceed a …
Spotlight On: Programming Techniques Used as an Insider Attack Tool
December 1, 2008 • white paper, by andrew p. moore, randall f. trzeciak, dawn cappelli, thomas c. caron (john heinz iii college, school of information systems management, carnegie mellon university).
In this report, the authors focus on persons who use programming techniques to commit malicious acts against their organizations.
A Survey of Systems Engineering Effectiveness - Initial Results
December 1, 2008 • special report, by the ndia se effectiveness committee, khaled el emam, nichole donitelli, angelica neisa, joseph p. elm, dennis goldenson.
This survey quantifies the relationship between the application of Systems Engineering (SE) best practices to projects and programs, and the performance of those projects and programs.
Results of SEI Independent Research and Development Projects (FY 2008)
December 1, 2008 • technical report, by lui r. sha, lutz wrage, jörgen hansson (university of skovde), sherman eagles, paul jones, insup lee, ragunathan rajkumar, robert w. stoddard, robert nord, kurt c. wallnau, peter h. feiler, dionisio de niz, rick kazman, ipek ozkaya, gabriel moreno, john b. goodenough, charles weinstock, daniel plakosh, mark h. klein.
This report describes the independent research and development (IRAD) projects that were conducted during fiscal year 2008 (October 2007 through September 2008).
CMMI or Agile: Why Not Embrace Both!
November 1, 2008 • technical note, by hillel glazer - entinex inc., jeff dalton (broadsword solutions corporation), david anderson (david j. anderson & associates inc.), michael d. konrad, sandra shrum.
This report describes how CMMI and Agile methods can be used together successfully.
CMMI Roadmaps
By ben linders, jan j. cannegieter, andre heijstek, rini van solingen.
The report guides organizations that are starting a CMMI for development implementation and deciding to use the continuous representation. The report offers guidance for how to decide what process areas …
CMMI High Maturity Measurement and Analysis Workshop Report: March 2008
By robert w. stoddard, david zubrow, dennis goldenson, erin harper.
This report outlines a 2008 workshop, in which leaders discussed high maturity practices and how to sustain momentum for improvement.
Can You Trust Your Data? Establishing the Need for a Measurement and Analysis Infrastructure Diagnostic
By david zubrow, mark kasunic, james mccurley.
This report describes common errors in measurement and analysis and the need for a criterion-based assessment method that will allow organizations to evaluate key characteristics of their measurement programs.
Software Engineering Bibliography
September 29, 2008 • white paper.
In this paper, the authors provide a bibliography of sources related to software engineering.
Application Firewalls and Proxies - Introduction and Concept of Operations
September 27, 2008 • white paper, by howard f. lipson, ken van wyk (no affiliation).
In this paper, the authors describe one of the many potential topic areas involving the integration of business applications into a supporting IT security infrastructure.
Existence Plots: A Low-Resolution Time Series for Port Behavior Analysis
September 15, 2008 • white paper, by jeff janies.
In this paper, Jeff Janies introduces the existence plot as a visualization and discuss its use in gaining insight into a host's behavior.
Acquisition Archetypes: Underbidding the Contract
September 1, 2008 • white paper.
From the Acquisition Support Program, one in a series of short papers on acquisition patterns of failure.
Acquisition Archetypes: Staff Burnout and Turnover
Applying more pressure on staff can temporarily increase productivity, but burnout soon sets in.
T-Check in Technologies for Interoperability: Business Process Management in a Web Services Context
September 1, 2008 • technical note, by lutz wrage, fabian hueppi, grace lewis.
This technical note presents an investigation of the Business Process Execution Language, a popular BPM technology used to describe, analyze, execute, and monitor business processes.
Service Level Agreements in Service-Oriented Architecture Environments
By philip bianco, paulo merson, grace lewis.
This 2008 report surveys the state of practice in service level agreement specification and offers guidelines on how to assure that services are provided with high availability, security, performance, and …
Requirements and Their Impact Downstream: Improving Causal Analysis Processes Through Measurement and Analysis of Textual Information
September 1, 2008 • technical report, by dennis goldenson, lawrence t. osiecki, ira monarch.
Requirements documents, test procedures, and problem and change reports from a U. S. Army Software Engineering Center (SEC) were analyzed to identify, clarify, and begin categorizing recurring patterns of issues …
Computer Forensics: Results of Live Response Inquiry vs. Memory Image Analysis
August 1, 2008 • technical note, by joseph a. akinyele, richard nolan, cal waits, larry rogers.
The authors compare various approaches and tools used to capture and analyze evidence from computer memory.
Introducing Function Extraction into Software Testing (July 2008)
July 14, 2008 • white paper, by richard c. linger (oak ridge national laboratory), alan r. hevner (university of south florida), mark pleszkoch.
This paper describes the emerging technology of function extraction (FX).
Preview of the Mission Assurance Analysis Protocol (MAAP): Assessing Risk and Opportunity in Complex Environments
July 1, 2008 • technical note, by lisa marino, audrey j. dorofee, christopher j. alberts.
In this 2008 document, the authors preview a core set of activities and outputs that define a MAAP assessment.
A Data Specification for Software Project Performance Measures: Results of a Collaboration on Performance Measurement
July 1, 2008 • technical report.
This 2008 document contains defined software project performance measures and influence factors that can be used by software development projects so that valid comparisons can be made between completed projects.
Results of SEI Independent Research and Development Projects (FY 2007)
By stefan schuster, marin litoiu (ibm canada ltd.), lui r. sha, len bass, jörgen hansson (university of skovde), dennis b. smith, kostas kontogiannis, john j. hudak, mark h. klein, peter h. feiler, kurt c. wallnau, dionisio de niz, donald firesmith, grace lewis.
This report describes the independent research and development (IRAD) projects that were conducted during fiscal year 2007 (October 2006 through September 2007).
Proceedings of the International Workshop on the Foundations of Service-Oriented Architecture (FSOA 2007)
June 1, 2008 • special report, by dennis b. smith, grace lewis.
This report presents the results of the Foundations of Software-Oriented Architecture (FSOA) workshop held at the Third International Conference on Interoperability for Enterprise Software and Applications (I-ESA 2007).
SQUARE-Lite: Case Study on VADSoft Project
By nancy r. mead, ashwin gayash, venkatesh viswanathan, deepa padmanabhan.
In this 2008 report, the authors describe SQUARE and SQUARE-Lite, and using SQUARE-Lite to develop security requirements for a financial application.
SoS Navigator 2.0: A Context-Based Approach to System-of-Systems Challenges
June 1, 2008 • technical note, by william anderson, suzanne miller, lisa brownsword, john morley, philip j. boxer, dennis b. smith, david j. carney, patrick kirwan.
This report introduces the fundamental concepts, processes, and techniques of the SoS Navigator approach. It also presents case studies that show the use of SoS Navigator in healthcare, military, and …
SMART: Analyzing the Reuse Potential of Legacy Components in a Service-Oriented Architecture Environment
By dennis b. smith, grace lewis, edwin j. morris, soumya simanta.
Is legacy system migration feasible for your organization as a means of SOA adoption? The Service Migration and Reuse Technique (SMART) assists an organization in determining what to migrate, the …
Evaluation of CERT Secure Coding Rules through Integration with Source Code Analysis Tools
June 1, 2008 • technical report, by chad dougherty, robert c. seacord, david svoboda, david keaton, chris taschner, stephen dewhurst, yurie ito, dan saks, kazuya togashi (jpcert/cc).
In this report, the authors describe a study to evaluate CERT Secure Coding Standards and source code analysis tools in commercial software projects.
Strategic Technology Selection and Classification in Multimodel Environments
May 8, 2008 • white paper, by john morley, lisa marino, patrick kirwan, jeannine siviy.
This white paper is the second in a five-part series dedicated to examining problems organizations encounter when operating in multimodel environments and the current process improvement approaches such organizations need …
Leadership and Management in Software Architecture
May 1, 2008 • white paper, by brian berenbach, len bass.
The workshop on Leadership and Management in Software Architecture that took place at ICSE 2008 was focused on understanding these non-technical duties and the type of support an architect should …
Management and Education of the Risk of Insider Threat (MERIT): System Dynamics Modeling of Computer System
By andrew p. moore, timothy j. shimeall, dawn cappelli, bradford j. willke, akash g. desai (information networking institute, carnegie mellon university), elise a. weaver (worcester polytechnic institute).
In this paper, the authors describe the MERIT insider threat model and simulation results.
Implementation Challenges in a Multimodel Environment
By john morley, jeannine siviy, patrick kirwan, lisa marino.
This white paper is the fifth in a five-part series dedicated to examining problems organizations encounter when operating in multimodel environments.
Using Model-Based Engineering and Architectural Models to Build Secure Systems
By peter h. feiler, john morley, jörgen hansson (university of skovde).
In this paper, the authors present analytical techniques to model and validate security protocols for enforcing confidentiality and integrity.
Building Secure Systems Using Model-Based Engineering and Architectural Models
By jörgen hansson (university of skovde), john morley, peter h. feiler.
A system designer faces several challenges when specifying security for distributed computing environments or migrating systems to a new execution platform.
Proceedings of the First Workshop on Service-Oriented Architectures and Product Lines
May 1, 2008 • special report.
This 2008 report includes an overview of the First Workshop on Service-Oriented Architectures and Product Lines, four invited presentations, details of the workshops outcomes, and the workshop position papers.
Incorporating Security Quality Requirements Engineering (SQUARE) into Standard Life-Cycle Models
May 1, 2008 • technical note, by nancy r. mead, anusha raveendran, venkatesh viswanathan, deepa padmanabhan.
In this 2008 report, the authors describe how SQUARE can be incorporated into standard lifecycle models for security-critical projects.
Survivability Assurance for System of Systems
May 1, 2008 • technical report, by carol woody, robert j. ellison, charles weinstock, john b. goodenough.
In this report, the authors describe the Survivability Analysis Framework, a structured view of people, process, and technology.
The "Big Picture" of Insider IT Sabotage Across U.S. Critical Infrastructures
By randall f. trzeciak, andrew p. moore, dawn cappelli.
In this report, the authors describe seven observations about insider IT sabotage based on their empirical data and study findings.
CMMI for Acquisition (CMMI-ACQ) Primer, Version 1.2
By karen richter.
This primer can be used by projects that acquire products or services in government and non-government organizations to improve acquisition processes.
The State of Information Security Law A Focus on the Key Legal Trends
March 30, 2008 • white paper, by tom smedinghoff (wildman harrold).
This paper will examine new developments as they relate to three trends that are posing significant new challenges for most businesses..
The Value of Harmonizing Multiple Improvement Technologies: A Process Improvement Professional's View
March 1, 2008 • white paper, by jeannine siviy, patrick kirwan, lisa marino, john morley.
This white paper is the first in a five-part series dedicated to examining problems organizations encounter when operating in multimodel environments and the current process improvement approaches such organizations need …
Process Architecture in a Multimodel Environment
By lisa marino, patrick kirwan, jeannine siviy, john morley.
This white paper is the fourth in a five-part series that examines problems organizations encounter when operating in multimodel environments.
Improvement Technology Classification and Composition in Multimodel Environments
This paper is the third in a five-part series dedicated to examining problems organizations encounter when operating in multimodel environments and the current process improvement approaches such organizations need to …
Acquisition Archetypes: Feeding the Sacred Cow
Some programs take on a life of their own—privileged, and woven into an organization's existence. But when "sacred cow" projects begin to go wrong, that privilege and protection makes fixing …
Acquisition Archetypes: PMO versus Contractor Hostility
Everyone intends the best in project-driven marriages of PMOs and contractors, but good intentions can't overcome the hostility generated by loss of trust and squabbles in poorly developed relationships.
Acquisition Archetypes: Firefighting
All hands on deck helps put out the immediate blazes threatening projects, but falling into a routine of constant firefighting is not the way to guide a project across the …
Maximizing your Process Improvement ROI through Harmonization
By john morley, patrick kirwan, jeannine siviy, lisa marino.
This white paper is an executive overview of the business value in harmonizing process improvement efforts when multiple improvement technologies, models and standards are in use.
Lessons Learned Applying the Mission Diagnostic
March 1, 2008 • technical note, by christopher j. alberts, lisa marino, audrey j. dorofee.
This technical note describes the adaptation of the Mission Diagnostic (MD) necessary for a customer and the lessons we learned from its use.
Mission Diagnostic Protocol, Version 1.0: A Risk-Based Approach for Assessing the Potential for Success
March 1, 2008 • technical report.
This 2008 document describes the core set of activities and outputs that defines mission diagnostic protocol (MDP).
Models for Evaluating and Improving Architecture Competence
By len bass, mark h. klein, rick kazman, paul c. clements.
This report outlines the concepts of software architecture competence and describes four models for explaining, measuring, and improving the architecture competence of an individual or a software-producing organization.
Incident Management Mission Diagnostic Method, Version 1.0
By mark zajicek, robin ruefle, audrey j. dorofee, georgia killcrece.
This report is superseded by the Mission Risk Diagnostic for Incident Management Capabilities, CMU/SEI-2014-TN-004.
ASSIP Study of Real-Time Safety-Critical Embedded Software-Intensive System Engineering Practices
February 1, 2008 • special report, by peter h. feiler, dionisio de niz.
This report presents findings of a study of RTSCE software-intensive systems issues and develop recommendations for effectively dealing with those issues.
On the Anonymization and Deanonymization of NetFlow Traffic
January 8, 2008 • white paper, by michalis foukarakis (institute of computer science), demetres antoniades (institute of computer science), evangelos p. markatos (institute of computer science).
In this paper, the authors describe anontool, which allows per-field anonymization up to the NetFlow layer and offers a wide range of primitives to choose from.
Assessing Disclosure Risk in Anonymized Datasets
January 7, 2008 • white paper, by alexi kounine (epfl), michele bezzi (atl).
In this paper, the authors propose a framework for estimating disclosure risk using conditional entropy between the original and the anonymized datasets.
Vulnerability Detection in ActiveX Controls through Automated Fuzz Testing
January 1, 2008 • white paper, by will dormann, daniel plakosh.
In this 2008 paper, the authors explore results of a test of a large number of Active X controls, which provides insight into the current state of ActiveX security.
Insider Threat Study: Illicit Cyber Activity in the Information Technology and Telecommunications Sector Executive Summary
In this paper, the authors present the findings of research examining reported insider incidents in information technology and telecommunications sectors.
Insider Threat Study: Illicit Cyber Activity in the Government Sector Executive Summary
In this paper, the authors present the findings of a research effort to examine reported insider incidents within the government sector.
Insider Threat Study: Illicit Cyber Activity in the Information Technology and Telecommunications Sector
By eileen kowalski (united states secret service), dawn cappelli, andrew p. moore.
In this paper, the authors present the findings of research examining reported insider incidents in the information technology and telecommunications sectors.
Insider Threat Study: Illicit Cyber Activity in the Government Sector
By andrew p. moore, dawn cappelli, bradford j. willke, eileen kowalski (united states secret service).
In this paper, the authors present the findings of a research effort to examine reported insider incidents in the government sector.
T-Check in Technologies for Interoperability: Web Services and Security—Single Sign-On
January 1, 2008 • technical note, by grace lewis, soumya simanta, lutz wrage, saul jaspan.
This technical note presents the results of applying the T-Check approach in an initial investigation of two Web services standards, WS-Security and SAML, to create an SSO solution that works …
Moving Up the CMMI Capability and Maturity Levels Using Simulation
January 1, 2008 • technical report, by david m. raffo (portland state university), wayne wakeland (portland state university).
This report shows examples of how PSIM has been implemented within industry and government organizations to improve process consistency and results.
Using the Vickrey-Clarke-Groves Auction Mechanism for Enhanced Bandwidth Allocation in Tactical Data Networks
By daniel plakosh, mark h. klein, kurt c. wallnau.
This report describes an investigation of the potential for using computational mechanisms to improve the quality of a combat group's common operating picture, in a setting where network bandwidth is …
Handling Interdependent Values in an Auction Mechanism for Bandwidth Allocation in Tactical Data Networks
December 31, 2007 • white paper, by kurt c. wallnau, gabriel moreno, daniel plakosh, mark h. klein.
This paper introduces a mechanism that achieves efficient bandwidth allocation and provides incentive compatibility by conditioning payments on the realized value for data shared between agents.
The State of Information Security Law: A Focus on the Key Legal Trends
December 18, 2007 • white paper.
This paper provides information about the expanding duty to provide security and the emergency of a legal obligation for compliance.
Diagrams and Languages for Model-Based Software Engineering of Embedded Systems: UML and AADL
December 1, 2007 • white paper, by dionisio de niz.
The tools compared in this discussion, the Unified Modeling Language (UML) and the Architecture Analysis and Design Language (AADL), facilitate the modeling of software architecture and provide elements to understand …
Basic Principles and Concepts for Achieving Quality Parent
December 1, 2007 • technical note.
This report extends the quality concepts first articulated in "A Software Quality Framework (SQF)" developed in the early 1980s for the DoD by Baker and colleagues.
Flow Latency Analysis with the Architecture Analysis and Design Language (AADL)
By jörgen hansson (university of skovde), peter h. feiler.
This 2007 report describes the ability of AADL to determine a lower bound for the worst-case end-to-end latency in a system.
Software-Intensive Systems Producibility: A Vision and Roadmap (v 0.1)
This 2007 document is a draft in progress of a technology vision and roadmap to improve the ability of the DoD and industry to deliver needed SiS capability in a …
Programmatic Interoperability
By b. craig meyers, james smith.
This report introduces the concept of programmatic interoperability, which is the application of principles of interoperability to the acquisition management of systems. The report also discusses the orchestration of decisions …
Common Misconceptions About Service-Oriented Architecture
November 1, 2007 • white paper, by grace lewis, edwin j. morris, soumya simanta, dennis b. smith, lutz wrage.
This 2007 article from Crosstalk magazine suggests ways to more effectively address critical SOA issues that potential users, developers, and acquisition officers may have.
Traditional Chinese language translation of CMMI for Acquisition, V1.2
The Traditional Chinese language translation of CMMI for Acquisition (CMMI-ACQ), V1.2.
Classifying Architectural Elements as a Foundation for Mechanism Matching
By rick kazman, paul c. clements, len bass.
This paper presents a set of well-known but informally described software architectural elements used in system composition and taxonomizes them under a basic set of characteristic features.
A-Specification for the CMMI Product Suite, Version 1.7
The A-Specification for the CMMI Product Suite (A-SPEC) defines the scope and requirements the CMMI Product Suite must meet to be considered acceptable.
A Survey of Systems Engineering Effectiveness: Initial Results
November 1, 2007 • special report, by khaled el emam, nichole donitelli, angelica neisa, the ndia se effectiveness committee, dennis goldenson, joseph p. elm.
This survey quantifies the relationship between the application of systems engineering best practices to projects and the performance of those projects.
CMMI for Acquisition, Version 1.2
November 1, 2007 • technical report.
The CMMI-ACQ model provides guidance for the application of CMMI best practices by the acquirer.
Fishing for Phishes: Applying Capture-Recapture Methods to Estimate Phishing Populations
October 4, 2007 • white paper, by rhiannon weaver, m. p. collins (redjack).
In this paper, the authors describe addressing phishing problems by estimating population in terms of netblocks and by clustering phishing attempts into scams.
Acquisition Archetypes: The Bow Wave Effect
October 1, 2007 • white paper, cots and reusable software management planning: a template for life-cycle management, october 1, 2007 • technical report, by dennis b. smith, mary c. ward, edwin j. morris, william anderson.
This 2007 report presents a COTS and Reusable Software Management Plan that can serve as a guide for how to manage multiple COTS and other reusable software components in complex …
SCAMPI Lead Appraiser Body of Knowledge (SLA BOK)
By judah mogilensky, steve masters, sandra behrens, charlie ryan.
The SLA BOK identifies the competencies needed to carry out the method requirements and guidelines detailed in the MDD (Method Definition Document).
Hit-List Worm Detection and Bot Identification in Large Networks Using Protocol Graphs
September 5, 2007 • white paper, by m. p. collins (redjack), michael k. reiter.
In this paper, the authors present a novel method for detecting hit-list worms using protocol graphs.
Four Pillars of Service-Oriented Architecture
September 1, 2007 • white paper, by grace lewis, dennis b. smith.
This 2007 SEI whitepaper by Grace Lewis and Dennis B. Smith outlines four pillars to Service-Oriented Architecture (SOA) success.
Using ArchE in the Classroom: One Experience
September 1, 2007 • technical note, by len bass, mark h. klein, john mcgregor, philip bianco, felix bachmann.
The ArchE (Architecture Expert) tool serves as a software architecture design assistant. This report describes the use of a pre-alpha release of ArchE in a graduate-level software architecture class at …
Using Aspect-Oriented Programming to Enforce Architecture
This report illustrates how to use AOP (aspect-oriented programming) to ensure conformance to architectural design, proper use of design patterns and programming best practices, conformance to coding policies and naming …
Process Improvement Should Link to Security: SEPG 2007 Security Track Recap
In this document, Carol Woody summarizes the content shared at the 2007 SEPG conference and steps underway toward ties between security and process improvement.
Ranged Integers for the C Programming Language
By robert c. seacord, jeff gennari, fred long, shaun hedrick, justin pincar.
In this 2007 report, the authors describe an extension to the C programming language to introduce the notion of ranged integers.
Certified Binaries for Software Components
September 1, 2007 • technical report, by sagar chaki, kurt c. wallnau, james ivers, peter lee, noam zeilberger.
In this report, the authors present an approach to certify binary code against expressive policies to achieve the benefits of PCC and CMC.
Modifiability Tactics
By len bass, robert nord, felix bachmann.
This report describes how architectural tactics are based on the parameters of quality attribute models.
Evaluating a Service-Oriented Architecture
By philip bianco, paulo merson, rick kotermanski.
This report contains technical information about SOA design considerations and tradeoffs that can help the architecture evaluator to identify and mitigate risks in a timely and effective manner.
Business Rules for CMMI Focus Topics
August 22, 2007 • white paper.
This paper provides guidelines for organizations seeking to publish material related to any CMMI focus topics.
Governing for Enterprise Security (GES) Implementation Guide
August 1, 2007 • technical note, by julia h. allen, jody r. westby.
In this 2007 report, the authors provide prescriptive guidance for creating and sustaining an enterprise security governance program.
How To Compare the Security Quality Requirements Engineering (SQUARE) Method with Other Methods
In this 2007 report, Nancy Mead describes SQUARE, and outlines other methods used for identifying security requirements.
System Strategies References
July 17, 2007 • white paper.
In this paper, the authors provide references related to system strategies.
Governing for Enterprise Security Implementation Guide: Sample Artifact Roles and Responsibilities for an Enterprise Security Program
July 11, 2007 • White Paper
The use of malware analysis in support of law enforcement, by ross kinder.
In this paper, Ross Kinder discusses how malware analysis supports the efforts of those pursuing adversaries employing malicious code in their tradecraft.
Introduction to the Architecture of the CMMI Framework
July 1, 2007 • technical note, by the cmmi architecture team.
This 2007 document is an introduction to the CMMI Framework architecture, which guides how CMMI products are developed and integrated.
Dependability Modeling with the Architecture Analysis & Design Language (AADL)
By ana rugina, peter h. feiler.
This 2007 report explains the capabilities of the Error Model Annex and provides guidance on the use of the AADL and the error model in modeling dependability aspects of embedded …
Modeling of System Families
This report discusses how AADL can be used to model system families and configurations of system and component variants.
Results of SEI Independent Research and Development Projects (FY 2006)
July 1, 2007 • technical report, by christopher j. alberts, carol sledge, aaron greenhouse, thomas a. longstaff, james ivers, sagar chaki, mike phillips, lisa brownsword, suzanne miller, kurt c. wallnau, peter h. feiler, william anderson, pratyusa k. manadhata, j. wing, matt bass, peter lee, noam zeilberger, gwendolyn h. walton, philip j. boxer, james smith, len bass, eileen c. forrester, jörgen hansson (university of skovde), richard c. linger (oak ridge national laboratory), david fisher, b. craig meyers, james d. herbsleb.
This report describes the IRAD projects that were conducted during fiscal year 2006 (October 2005 through September 2006).
Developing AADL Models for Control Systems: A Practitioner's Guide
By peter h. feiler, john j. hudak.
This 2007 document helps practitioners use AADL and describes an approach for and the mechanics of constructing an architectural model that can be analyzed based on the AADL.
Progress Toward an Organic Software Architecture Capability in the U.S. Army
June 1, 2007 • technical report, by stephen blanchette, jr., john k. bergey.
This 2007 report describes the Software Architecture Initiative of the Army Strategic Software Improvement Program.
Case Study: Accelerating Process Improvement by Integrating the TSP and CMMI
By daniel s. wall, marsha pomeroy-huff, jim mchale.
This report describes how two NAVAIR organizations integrated the use of the TSP methodology and the CMM framework to progress from maturity level 1 to maturity level 4 in 30 …
SAAM: A Method for Analyzing the Properties of Software Architectures
May 1, 2007 • white paper, by len bass, mike webb (texas instruments), gregory abowd, rick kazman.
This paper describes three perspectives by which we can understand the description of a software architecture and proposes a five-step method for analyzing software architectures called SAAM (Software Architecture Analysis …
Quality-Attribute-Based Economic Valuation of Architectural Patterns
May 1, 2007 • technical report, by ipek ozkaya, rick kazman, mark h. klein.
This report shows how an analysis of the options embodied within architectural patterns allows a software and system architect or manager to make reasoned choices about the future value of …
Introducing the CERT® Resiliency Engineering Framework: Improving the Security and Sustainability Processes
By lisa r. young, james f. stevens, richard a. caralli, david w. white, william r. wilson, charles m. wallen.
In this 2007 report, the authors explore the transformation of security and business continuity into processes to support and sustain operational resiliency.
Introducing OCTAVE Allegro: Improving the Information Security Risk Assessment Process
By william r. wilson, james f. stevens, richard a. caralli, lisa r. young.
In this 2007 report, the authors highlight the design considerations and requirements for OCTAVE Allegro based on field experience.
Function Extraction: Automated Behavior Computation for Aerospace Software Verification and Certification
April 29, 2007 • white paper, by tim daly, richard c. linger (oak ridge national laboratory), stacy j. prowell.
This paper describes verification and certification challenges for avionics software.
Copper Manual, Tutorial, and Specification Grammar
April 1, 2007 • white paper, by sagar chaki.
Copper is a software model checker for concurrent message-passing C programs.
T-Check for Technologies for Interoperability: Open Grid Services Architecture (OGSA)—Part 1 Parent SEI Program
April 1, 2007 • technical note, by soumya simanta, grace lewis, lutz wrage.
This report investigates Open Grid Services Architecture (OGSA), one of the many technologies for accomplishing interoperability, using the T-Check technique.
Governing for Enterprise Security (GES) Implementation Guide Article 3: Enterprise Security Governance Activities
March 5, 2007 • White Paper
Governing for Enterprise Security (GES) Implementation Guide Article 2: Defining an Effective Enterprise Security Program (ESP)
March 1, 2007 • White Paper
Global information grid survivability: four studies, march 1, 2007 • special report, by richard c. ciampa, dawn day, jennifer r. franks, christopher t. tsuboi.
Four studies from 2006 that explore an issue relevant to the survivability of networks which are systems of systems.
Modeling and Analysis of Information Technology Change and Access Controls in the Business Context
March 1, 2007 • technical note, by andrew p. moore, rohit s. antao.
In this report, the authors describe progress in developing a system dynamics model of typical use of change and access controls to support IT operations.
Management and Education of the Risk of Insider Threat (MERIT): Mitigating the Risk of Sabotage to Employers Information, Systems, or Networks
By akash g. desai (information networking institute, carnegie mellon university), elise a. weaver (worcester polytechnic institute), bradford j. willke, dawn cappelli, andrew p. moore, timothy j. shimeall.
In this 2006 report, the authors describe MERIT insider threat model and simulation results.
+SAFE, V1.2: A Safety Extension to CMMI-DEV, V1.2
By defence materiel organisation, australian department of defence.
This technical report describes how to use +SAFE to appraise an organization's capability in developing, sustaining, maintaining, and managing safety-critical products.
Executive Overview of SEI MOSAIC: Managing for Success Using a Risk-Based Approach
This 2007 report provides an overview of the concepts and foundations of MOSAIC, a suite of advanced, risk-based analysis methods for assessing complex, distributed programs, processes, and information-technology systems.
Understanding and Leveraging a Supplier's CMMI Efforts: A Guidebook for Acquirers
March 1, 2007 • technical report, by the cmmi guidebook for acquirers team.
This guidebook is designed to help acquisition organizations benefit from their suppliers' use of CMMI for Development, a collection of best practices that addresses product development and maintenance activities throughout …
Governing for Enterprise Security (GES) Implementation Guide Article 1: Characteristics of Effective Security Governance1
February 5, 2007 • White Paper
A practical example of applying attribute-driven design (add), version 2.0, february 1, 2007 • technical report, by william wood.
This 2007 report describes an example application of the ADD method, an approach to defining a software architecture in which the design process is based on the quality attribute requirements …
Defining Computer Security Incident Response Teams
January 24, 2007 • white paper.
In this paper, Robin Ruefle describes the purpose and goals of a computer security incident response team (CSIRT).
Penetration Testing Tools
January 18, 2007 • white paper, cert® resiliency engineering framework, january 1, 2007 • white paper.
In this paper, the authors answer commonly asked questions about the CERT Resiliency Engineering Framework project.
Instructional Case of Insider Threat in the SDLC: The Case of InsureACure, Inc.
In this paper, the authors provide an instructional case of insider threat in the systems development lifecycle.
A Proposed Taxonomy for Software Development Risks for High-Performance Computing (HPC) Scientific/Engineering Applications
January 1, 2007 • technical note, by jeffrey carver, dale b. henderson, richard kendall, david fisher, douglass post (dod high performance computing modernization program).
In this report, the authors classify the sources of software development risk for scientific/engineering applications.
Case Study of the NENE Code Project
By douglass post (dod high performance computing modernization program), richard kendall, andrew mark (dod high performance computing modernization program).
This report outlines the case studies of high-performance code development projects. This is the fifth case study in this series.
Conditions for Achieving Network-Centric Operations in Systems of Systems
By david fisher, b. craig meyers, patrick r. place.
This 2007 report lists conditions that must prevail to achieve effective acquisition, development, and use of systems of systems.
Interpreting Capability Maturity Model Integration (CMMI) for Business Development Organizations in the Government and Industrial Business Sectors
By donald r. beynon.
This 2007 interpretation of CMMI best practices is for business development activities applicable to contractors doing business within the government (Department of Defense) and industrial business sectors.
The State of Software Measurement Practice: Results of 2006 Survey
December 1, 2006 • technical report.
This paper reports the results of a February 2006 study to gauge the state of the practice in software measurement.
Technology Foundations for Computational Evaluation of Software Security Attributes
In this 2006 report, the authors describe foundations for computational security attributes technology.
Comparing Insider IT Sabotage and Espionage: A Model-Based Analysis
By dawn cappelli, eric d. shaw, stephen r. band (counterintelligence field activity - behavioral science directorate), lynn f. fischer, andrew p. moore, randall f. trzeciak.
In this report, the authors examine the psychological, technical, organizational, and contextual factors that contribute to espionage and insider sabotage.
Action List for Developing a Computer Security Incident Response Team (CSIRT)
November 2, 2006 • white paper.
In this paper, the authors summarize actions to take and topics to address when planning and implementing a Computer Security Incident Response Team (CSIRT).
Army ASSIP System-of-Systems Test Metrics Task
November 1, 2006 • special report.
This report contains presents the results of an effort to improve the acquisition of software-intensive systems by focusing on acquisition programs, people, and production/sustainment and by institutionalizing continuous improvement.
Schedule Considerations for Interoperable Acquisition
November 1, 2006 • technical note, by carol sledge, b. craig meyers.
This 2006 report examines the issue of schedule considerations for interoperable acquisition.
Attribute-Driven Design (ADD), Version 2.0
November 1, 2006 • technical report, by william wood, robert wojcik, paul c. clements, paulo merson, felix bachmann, robert nord, len bass.
This report revises the steps of the Attribute-Driven Design (ADD) method and offers practical guidelines for carrying out each step.
A Traffic Analysis of a Small Private Network Compromised by an Online Gaming Host (White Paper)
October 10, 2006 • white paper, by ron mcleod (corporate development telecom applications research alliance).
In this paper, Ron McLeod describes a network traffic capture and analysis used to investigate network performance issues of a small private network.
System Requirements for Flow Processing
By raj srinivasan (bivio networks).
In this paper, Raj Srinivasan proposes an architecture that meets security requirements and is flexible enough to support future application needs.
Scalable Flow Analysis (White Paper)
By abhishek kumar (university of maryland), sapan bhatia (princeton).
In this paper, the authors present a new approach for summarization and analysis of flow records.
RAVE: The Retrospective Analysis and Visualization Engine
By john prevost, phil groce.
In this paper, the authors present RAVE as an analysis service provider.
The Effect of Packet Sampling on Anomaly Detection
By daniela brauckhoff (swiss federal institute of technology (eth)), bernhard tellenbach (swiss federal institute of technology (eth)), martin may (swiss federal institute of technology (eth)), anukool lakhina (boston university), arno wagner (communication systems laboratory swiss federal institute of technology zurich (eth zurich)).
In this paper, the authors empirically evaluate the impact of sampling on anomaly detection.
Attribution and Aggregation of Network Flows for Security Analysis (White Paper)
By vincent berk (dartmouth college), annarita giani (uc berkeley), iangregoriode souza (dartmouth college), george cybenko (dartmouth college).
In this paper, the authors describe a network flow analyzer capable of attribution and aggregation of different flows to identify suspicious behaviors.
IPFIX/PSAMP: What Future Standards Can Offer to Network Security (White Paper)
By thomas hirsch (fraunhofer fokus), tanja zseby (fraunhofer fokus), mark lutz (fraunhofer fokus), elisa boschi (hitachi).
In this paper, the authors show how IPFIX and PSAMP can be used to support network security.
Identifying Anomalous Network Traffic Through the Use of Client Port Distribution
By josh goldfarb (us-cert).
In this paper, Josh Goldfarb introduces an approach to IP flow analysis that examines server ports and client ports that exchange flows with them.
Anomaly Detection Through Blind Flow Analysis Inside a Local Network (White Paper)
October 2, 2006 • white paper, by ron mcleod (corporate development telecom applications research alliance), vagishwari nagaonkar (wipro technologies).
In this paper, the authors describe how hosts may be clustered into user workstations, servers, printers, and hosts compromised by worms.
An Examination of a Structural Modeling Risk Probe Technique
October 1, 2006 • special report, by william anderson, lisa brownsword, philip j. boxer.
This report examines a structural dynamic analysis modeling technique called Projective ANalysis (PAN) that was used on an interoperability technical probe of a NATO modernization program.
System-of-Systems Governance: New Patterns of Thought
October 1, 2006 • technical note, by dennis b. smith, patrick r. place, edwin j. morris.
This 2006 technical note examines the ways in which six key characteristics of good IT governance are affected by the autonomy of individual systems in a system of systems.
Topics in Interoperability: Structural Programmatics in a System of Systems
By james smith.
This technical note presents a case study on how choices of structural programmatics (e.g., hierarchical or peer-to-peer organization, centralized or decentralized execution) affect programmatic interoperability in complex systems of systems.
Next-Generation Software Engineering: Function Extraction for Computation of Software Behavior
September 9, 2006 • white paper, by gwendolyn h. walton, alan r. hevner (university of south florida), richard c. linger (oak ridge national laboratory).
This white paper discusses function extraction FX technology.
Finding Peer-To-Peer File-Sharing Using Coarse Network Behaviors?
September 4, 2006 • white paper, by michael collins, michael k. reiter.
In this paper, the authors propose a set of tests for identifying masqueraded peer-to-peer file-sharing based on traffic summaries (flows).
Quantitative Methods for Software Selection and Evaluation
September 1, 2006 • technical note, by michael s. bandor.
This 2006 report describes methods for selecting candidate commercial off-the-shelf packages for further evaluation, possible methods for evaluation, and other factors besides requirements to be considered.
Evolutionary Systems Design: Recognizing Changes in Security and Survivability Risks
In this 2006 report, Howard Lipson uses an example to illustrate the critical importance of evolutionary design changes in secure and survivable systems.
Assume-Guarantee Reasoning for Deadlock
By nishant sinha, sagar chaki.
This report shows how L^F can be used for compositional regular failure language containment and deadlock detection, using non-circular and circular assume-guarantee rules.
Certifying the Absence of Buffer Overflows
By sagar chaki, scott hissam.
In this report, the authors present a technique for certifying the safety of buffer manipulations in C programs.
Interoperable Acquisition for Systems of Systems: The Challenges
By james smith, mike phillips.
This 2006 report explores how systems-of-systems realities necessitate changes in the processes used to acquire, develop, field, and sustain operational capability.
Risk Themes Discovered Through Architecture Evaluations
September 1, 2006 • technical report, by len bass, robert nord, david zubrow, william wood.
This 2006 report analyzes the output of 18 evaluations conducted using the Architecture Tradeoff Analysis (ATAM). The goal of the analysis was to find patterns in the risk themes identified …
French language translation of CMMI for Development, V1.2
August 1, 2006 • white paper.
The French language translation of CMMI for Development (CMMI-DEV), V1.2.
Traditional Chinese language translation of CMMI for Development, V1.2
The Traditional Chinese language translation of CMMI for Development (CMMI-DEV), V1.2.
Security in the Software Lifecycle
Security in the Software Lifecycle: Making Software Development Processes--and Software Produced by Them--More Secure (Draft).
Portuguese language translation of CMMI for Development, V1.2
This is the Portuguese language translation of CMMI for Development, V1.2.
Workshop on Model-Driven Architecture and Program Generation
August 1, 2006 • technical note, by grace lewis, kurt c. wallnau, b. craig meyers.
This report summarizes the results of a June 2006 workshop, held to explore business and technical aspects of program generation in the context of the Object Management Group's model-driven architecture …
Risk Management Considerations for Interoperable Acquisition
By b. craig meyers.
In this report, Craig Meyers addresses interoperable risk management, the interoperability of organizations that engage in risk management.
Techniques for Developing an Acquisition Strategy by Profiling Software Risks
August 1, 2006 • technical report, by mary c. ward, joseph p. elm, susan kushner.
This report introduces a taxonomy of strategy drivers and strategy elements and provides a method for performing a comparative analysis of the strategy drivers and the resulting strategic choices for …
Performance Results of CMMI-Based Process Improvement
By keith kost, diane gibson, dennis goldenson.
This technical report summarizes much of the publicly available empirical evidence about the performance results that can occur as a consequence of CMMI-based process improvement.
CMMI for Development, Version 1.2
This report is an upgrade of CMMI-SE/SW/IPPD/SS, Version 1.1 and represents the model portion of the CMMI Product Suite.
Proceedings of the Second Software Architecture Technology User Network (SATURN) Workshop
By robert nord.
This report describes the second SATURN workshop format, discussion, and results, as well as plans for future SATURN workshops.
Appraisal Requirements for CMMI, Version 1.2 (ARC, V1.2)
The report defines the Appraisal Requirements for CMMI (ARC) V1.2 requirements that are considered to be essential to appraisal methods intended for use with Capability Maturity Model Integration (CMMI) models.
A Comparison of Requirements Specification Methods from a Software Architecture Perspective
By paulo merson, paul c. clements, ipek ozkaya, len bass, raghvinder sangwan, john k. bergey.
In this report, five methods for the elicitation and expression of requirements are evaluated with respect to their ability to capture architecturally significant requirements.
Systems of Systems: Scaling Up the Development Process
This report reviews the fundamental process and project-management problems of large-scale SoS-like programs and outlines steps to address these problems.
A Model for Opportunistic Network Exploits: The Case of P2P Worms
July 13, 2006 • white paper, by michael collins, carrie gates.
In this paper, the authors present VisFlowConnect-IP, a network flow visualization tool that detects and investigates anomalous network traffic.
Adapting CMMI for Acquisition Organizations: A Preliminary Report
June 1, 2006 • special report, by gowri s. ramani (hewlett packard), kathryn m. dodson (eds), hubert f. hofmann (general motors), deborah k. yedlin (general motors).
This 2006 document presents the initial draft CMMI-ACQ, which adapts CMMI for acquisition organizations.
Information Assurance: Building Educational Capacity
This 2006 report describes SEI and CERT Program efforts to increase the capacity of institutions of higher education to offer IA and IS courses.
Model Problems in Technologies for Interoperability: Web Services
June 1, 2006 • technical note, by grace lewis, lutz wrage.
This 2006 report presents the results of applying the model problem approach in an initial investigation of the potential of Web services to enable interoperability.
Specifying Initial Design Review (IDR) and Final Design Review (FDR) Criteria
By mary ann lapham.
This 2006 report presents definitions of IDR and FDR, their context in the acquisition life cycle, a comparison of engineering emphasis during IDR and FDR, IDR and FDR pre- and …
Joint Capabilities and System-of-Systems Solutions: A Case for Crossing Solution Domains
By william anderson, robert m. flowe, mary m. brown.
This 2006 report presents a case for the investigation and adaptation of structural and dynamic modeling techniques to the engineering of systems of systems.
Security Quality Requirements Engineering (SQUARE): Case Study Phase III
May 1, 2006 • special report, by lydia chung, frank hung, eric hough, don ojoko-adams, nancy r. mead.
In this report, the authors present their results of using SQUARE when working with three clients over the course of a semester.
Sustaining Software-Intensive Systems
May 1, 2006 • technical note, by carol woody, mary ann lapham.
This 2006 report discusses questions about sustaining new and legacy systems; the report presents definitions, related issues, future considerations, and recommendations for sustaining software-intensive systems.
Applying OCTAVE: Practitioners Report
By lisa r. young, johnathan coleman (no affiliation), michael fancher (no affiliation), carol myers (no affiliation), carol woody.
In this report, the authors describe how OCTAVE has been used and tailored to fit a wide range of organizational risk assessment needs.
PROxy Based Estimation (PROBE) for Structured Query Language (SQL)
By rob schoedel.
This 2006 report outlines a method for applying the PROxy Based Estimation (PROBE) technique to Structured Query Language (SQL).
Specifications for Managed Strings
May 1, 2006 • technical report, by fred long, hal burch, robert c. seacord.
This report has been superseded by Specifications for Managed Strings, Second Edition (CMU/SEI-2010-TR-018).
Autonomic Computing
April 1, 2006 • technical note, by william wood, mark h. klein, william o'brien, hausi a. muller (university of victoria).
This report examines selected aspects of autonomic computing and explores some of the strengths and weaknesses of that technology.
Sustaining Operational Resiliency: A Process Improvement Approach to Security Management
By richard a. caralli.
In this 2006 report, Richard Caralli describes the fundamental elements and benefits of a process approach to security and operational resiliency.
Common Elements of Risk
This technical note begins to define a foundation for effective risk management by identifying the basic elements of risk and exploring how these elements can affect the potential for mission …
Model Problems in Technologies for Interoperability: OWL Web Ontology Language for Services (OWL-S)
By chris metcalf c., grace lewis.
This 2006 report presents the results of applying the model problem approach to examine the feasibility of using OWL-S to allow applications to automatically discover, compose, and invoke services in …
System-of-Systems Navigator: An Approach for Managing System-of-Systems Interoperability
By edwin j. morris, lisa brownsword, james smith, david fisher, patrick kirwan.
This technical note introduces the System-of-Systems Navigator (SoS Navigator), the collection and codification of essential practices for building large-scale systems of systems.
Detecting Scans at the ISP Level
April 1, 2006 • technical report, by marc i. kellner, joseph b. kadane, josh mcnutt, carrie gates.
In this 2006 report, the authors present an approach to detecting scans against, or passing through, very large networks.
R2PL 2005 Proceedings of the First International Workshop on Reengineering Towards Product Lines
March 1, 2006 • special report, by barbara graaf, rafael capilla.
This 2006 report contains the proceedings from the First International Workshop on Reengineering Towards Product Lines (R2PL) 2005, which was held in November 2005.
On System Scalability
March 1, 2006 • technical note, by john b. goodenough, charles weinstock.
This 2006 report presents an analysis of what is meant by scalability and a description of factors to be considered when assessing the potential for system scalability.
Toward Measures for Software Architectures
By robert ferguson, gary chastek.
In this 2006 report, the authors describe the results of a preliminary investigation into measures for software architecture.
Requirements Management in a System-of-Systems Context: A Workshop
By peter capell, patrick r. place, b. craig meyers, james smith.
This 2006 report summarizes the results of a workshop focused on requirements management in a system of systems.
Product Line Acquisition in a DoD Organizational Guidance for Decision Makers
By john k. bergey, sholom g. cohen.
This 2006 report chronicles the decisions a program manager might face in considering the adoption of a product line approach.
An Emergent Perspective on Interoperation in Systems of Systems
March 1, 2006 • technical report.
This 2006 report facilitates discussion and reasoning about interoperation within systems of systems by showing some of the interdependencies among systems, emergence, and interoperation.
The Influence of System Properties on Software Assurance and Project Management
February 6, 2006 • white paper.
In this paper, Robert Ellison discusses characteristics of software and how they influence how software assurance should be managed.
The Architecture Analysis & Design Language (AADL): An Introduction
February 1, 2006 • technical note, by john j. hudak, peter h. feiler, david p. gluch.
This 2006 report provides an introduction to the AADL, a modeling language that supports early and repeated analyses of a system's architecture with respect to performance-critical properties.
Acquiring Evolving Technologies: Web Services Standards
By liam o'brien, harry l. levinson.
This technical note discusses some of the challenges of using Web services standards and presents the results generated by an assessment tool used to track the appropriateness of using this …
SAT-Based Software Certification
This 2006 report presents a technique that uses proofs to certify software.
2006 Tech Tip: UNIX Configuration Guidelines
January 1, 2006 • white paper.
This tech tip contains information about UNIX configuration guidelines.
Proceedings of the First International Research Workshop for Process Improvement in Small Settings, 2005
January 1, 2006 • special report, by keith kost, caroline graettinger, suzanne miller.
This 2006 report includes papers from the Proceedings of the First International Research Workshop for Process Improvement in Small Settings workshop, and presents conclusions and next steps for process improvement …
Incident Management
December 1, 2005 • white paper, by georgia killcrece.
In this paper, the author describes incident management capability and what it implies for controlling security events and incidents.
Botnets as a Vehicle for Online Crime
By aaron hackworth, nicholas ianelli.
In this paper, the authors describe the capabilities present in bot malware and the motivations for operating botnets.
Precise Buffer Overflow Detection via Model Checking
In this paper, the authors present an automated overflow detection technique based on model checking and iterative refinement.
December 1, 2005 • Special Report
By jim mchale, daniel s. wall, marsha pomeroy-huff.
This report describes how two NAVAIR organizations integrated the use of the Team Software Process methodology and the CMM framework to progress from Maturity Level 1 to Maturity Level 4 …
Relationships Between CMMI and Six Sigma
December 1, 2005 • technical note, by mary lynn penn, jeannine siviy, erin harper.
This 2005 report focuses on the joint use of two popular improvement initiatives: Capability Maturity Model Integration (CMMI) and Six Sigma.
Secure Software Development Life Cycle Processes: A Technology Scouting Report
The purpose of this 2005 technical note is to present overview information about existing processes, standards, life cycle models, frameworks, and methodologies that support or could support secure software development.
The CERT Function Extraction Experiment: Quantifying FX Impact on Software Comprehension and Verification
By richard c. linger (oak ridge national laboratory), rosann w. collins, gwendolyn h. walton, alan r. hevner (university of south florida).
In this report, the authors describe an experiment comparing traditional methods of comprehension with automated behavior computation using an FX prototype.
Verification of Evolving Software via Component Substitutability Analysis
December 1, 2005 • technical report, by sagar chaki, edmund clarke, natasha sharygina, nishant sinha.
This 2005 report describes the application of the SEI Architecture Tradeoff Analysis Method (ATAM) to the U.S. Army's Warfighter Information Network-Tactical (WIN-T) system.
Results of SEI Independent Research and Development Projects and Report on Emerging Technologies and Technology Trends (FY2005)
By stacy j. prowell, richard c. linger (oak ridge national laboratory), lutz wrage, jörgen hansson (university of skovde), natasha sharygina, rosann w. collins, angel jordan, gwendolyn h. walton, mark pleszkoch, alan r. hevner (university of south florida), sagar chaki, rick kazman, kurt c. wallnau, peter h. feiler, john j. hudak, john b. goodenough, charles weinstock, aaron greenhouse.
This report describes the IR&D projects that were conducted during fiscal year 2005 (October 2004 through September 2005). In addition, this report provides information on what the SEI has learned …
Categorizing Business Goals for Software Architectures
By rick kazman, len bass.
This report provides a categorization of possible business goals for software-intensive systems, so that individuals have some guidance in the elicitation, expression, and documentation of business goals.
Survivability and Information Assurance Curriculum Lab Overview
November 28, 2005 • white paper.
The overview provides information about the hardware and the software required for the lab in general and for each specific course. Other topics include configuration management, user identity and privileges, …
Survivability and Information Assurance Curriculum Overview
The Survivability and Information Assurance (SIA) Curriculum is designed to teach experienced system administrators about security and ways to integrate security into their routine tasks.
Foundations of the Survivability and Information Assurance Curriculum
This document highlights the foundations of the SIA Curriculum.
Safety-Critical Systems and the TSP
November 1, 2005 • technical note.
This 2005 report provides a brief overview of recent work in software safety, discusses the problems and implications of using the TSP for developing safety-critical systems, and presents some conclusions.
Topics in Interoperability: Infrastructure Replacement in a System of Systems
By james smith, david j. carney, patrick r. place.
This technical note examines the Common Operations System (COS), a large aggregation of independently developed systems, and the risks posed to it by an infrastructure upgrade.
Topics in Interoperability: Concepts of Ownership and Their Significance in Systems of Systems
By david j. carney, william anderson, patrick r. place.
This technical note is a brief examination of the concept of ownership and the ways in which it might apply to systems of systems.
Security Quality Requirements Engineering Technical Report
November 1, 2005 • technical report, by eric hough, ted stehney ii, nancy r. mead.
In this 2005 report, the authors present the SQUARE Methodology for eliciting and prioritizing security requirements in software development projects.
Software Product Lines: Experience from the Eighth DoD Software Product Line Workshop
By patrick donohoe, john k. bergey, lawrence g. jones, sholom g. cohen.
This 2005 report summarizes the discussions from a 2005 PLP workshop in which participants shared DoD product line practices, experiences, and issues and discussed ways in which specific product line …
Software Vulnerabilities in Java
October 1, 2005 • technical note, by fred long.
In this report, Fred Long briefly describes potential software vulnerabilities in Java version 5.
U.S. Army Acquisition: The Program Office Perspective
October 1, 2005 • special report.
This report documents the results of the interviews conducted during BFI engagements. These results are of interest to Program Executive Office staffs, Program Management Office staffs, and Department of Army …
VisFlowConnet-IP: An Animated Link Analysis Tool for Visualizing Netflows
September 20, 2005 • white paper, by xiaoxin yin (national center for supercomputing applications (ncsa) at university of illinois at urbana-champaign), adam slagell (national center for supercomputing applications (ncsa) at university of illinois at urbana-champaign), william yurcik (national center for supercomputing applications (ncsa) at university of illinois at urbana-champaign).
In this paper, the authors present VisFlowConnect-IP, a network flow visualization tool that allows operators to detect and investigate network traffic.
VisFlowConnect-IP: An Animated Link Analysis Tool For Visualizing Netflows (White Paper)
Identifying p2p heavy-hitters from network-flow data, by arno wagner (communication systems laboratory swiss federal institute of technology zurich (eth zurich)), thomas dubendorfer (communication systems laboratory swiss federal institute of technology zurich (eth zurich)), lukas hammerle (communication systems laboratory swiss federal institute of technology zurich (eth zurich)), bernhard plattner (communication systems laboratory swiss federal institute of technology zurich (eth zurich)).
In this September 2005 paper, the authors present measurements done on a medium-sized internet backbone and discuss accuracy issues.
Flow-Data Compressibility Changes During Internet Worm Outbreaks
By arno wagner (communication systems laboratory swiss federal institute of technology zurich (eth zurich)).
In this paper, Arno Wagner presents measurements and analysis done on a Swiss internet backbone during the Blaster and Witty internet worm outbreak.
A Proposed Translation Data Model for Flow Format Interoperability
By brian trammell.
In this paper, Brian Trammell presents a proposed solution to the problem of mutual unintelligibility of raw flow and intermediate analysis data.
R: A Proposed Analysis and Visualization Environment for Network Security Data (White Paper)
By josh mcnutt.
In this paper, Josh McNutt discusses the R statistical language as an analysis and visualization interface to SiLK flow analysis tools.
Correlations Between Quiescent Ports in Network Flows (White Paper)
By josh mcnutt, markus deshon.
In this paper, the authors introduce a method for detecting the onset of anomalous port-specific activity by recognizing deviation from correlated activity.
CANINE: A NetFlows Converter/Anonymizer Tool for Format Interoperability and Secure Sharing (White Paper)
By katherine luo (national center for supercomputing applications (ncsa) university of illinois at urbana-champaign), adam slagell (national center for supercomputing applications (ncsa) at university of illinois at urbana-champaign), william yurcik (national center for supercomputing applications (ncsa) at university of illinois at urbana-champaign), yifan li (national center for supercomputing applications (ncsa) university of illinois at urbana-champaign).
In this paper, the authors introduce a tool to address two problems with using Net-Flow logs for security analysis.
Detecting Distributed Attacks using Network-Wide Flow Traffic
By anukool lakhina (boston university), mark crovella (boston university), chrisophe diot (intel).
In this paper, the authors present their methods for detecting distributed attacks in backbone networks using sampled flow traffic data.
IP Flow Information Export (IPFIX): Applicability and Future Suggestions for Network Security
By elisa boschi (hitachi), tanja zseby (fraunhofer fokus), mark lutz (fraunhofer fokus), thomas hirsch (fraunhofer fokus).
In this paper, the authors present the IPFIX protocol and discuss its applicability with a special focus on network security.
NVisionIP: An Animated State Analysis Tool for Visualizing NetFlows (White Paper)
In this paper, the authors describe NVisionIP, a NetFlow visualization tool.
Using the OPEN Process Framework to Produce a Situation-Specific Requirements Engineering Method
September 1, 2005 • white paper, by donald firesmith, b. henderson-sellers, d. zowghi.
The OPEN Process Framework (or OPF) is an appropriate focused requirements engineering method (REM) that facilitates the search for a mechanism that will support the flexible creation of a number …
Covert Channel Detection Using Process Query Systems (White Paper)
By vincent berk (dartmouth college).
In this FloCon 2005 presentation, the author uses traffic analysis to investigate a stealthy form of data exfiltration.
Building Information Assurance Educational Capacity: Pilot Efforts to Date
September 1, 2005 • special report.
In this report, Carol Sledge describes work to increase the capacity of educational institutions to offer and expand IA and IS topics and courses.
Quality Attributes and Service-Oriented Architectures
September 1, 2005 • technical note, by len bass, liam o'brien, paulo merson.
This report examines the relationship between service-oriented architectures (SOAs) and quality attributes.
Using the SEI Architecture Tradeoff Analysis Method to Evaluate WIN-T: A Case Study
By paul c. clements, john k. bergey, dave mason.
This report describes the application of the SEI ATAM (Architecture Tradeoff Analysis Method) to the U.S. Army's Warfighter Information Network-Tactical (WIN-T) system.
SMART: The Service-Oriented Migration and Reuse Technique
By grace lewis, edwin j. morris, liam o'brien, lutz wrage, dennis b. smith.
This document has been superseded by CMU/SEI-2008-TN-008, SMART: Analyzing the Reuse Potential of Legacy Components in a Service-Oriented Architecture Environment.
Elements of a Usability Reasoning Framework
By len bass, jinhee lee.
This note describes an ARL implementation of two usability scenarios: displaying progress feedback and allowing cancel.
Mission Assurance Analysis Protocol (MAAP): Assessing Risk in Complex Environments
In this 2005 report, the authors present concepts and theories underlying the Mission Assurance Analysis Protocol.
Integrated Diagnostics: Operational Missions, Diagnostic Types, Characteristics, and Capability Gaps
By theodore f. marz.
This 2005 report attempts to fill in these gaps in knowledge and experience by presenting an overview of the operational diagnostic life cycle of a system.
A Taxonomy of Operational Risks
By rita c. creel, ray c. williams, brian p. gallagher, susan kushner, pamela j. case.
This report presents a taxonomy-based method for identifying and classifying risks to operational aspects of an enterprise.
Proceedings of the First Software Architecture Technology User Network (SATURN) Workshop
By james e. tomayko, len bass, linda m. northrop, paul c. clements, robert nord.
This report describes the format, discussion, and results of the first SATURN workshop, and outlines the plans for future SATURN workshops.
Lessons Learned Model Checking an Industrial Communications Library
By james ivers.
This 2005 report describes the application of a reasoning framework to the design of an industrial communications library and the problems that were found.
Experience Using the Web-Based Tool Wiki for Architecture Documentation
By paulo merson, felix bachmann.
This 2005 report discusses the benefits and challenges of using a wiki-based collaborative environment to create software architecture documentation.
Exploring Programmatic Interoperability: Army Future Force Workshop
This report documents the proceedings of the Future Force Workshop held at the SEI in 2004.
SAT-Based Predicate Abstraction of Programs
September 1, 2005 • technical report, by natasha sharygina, edmund clarke, daniel kroening, karen yorav (ibm).
This note presents technical details of a SAT-based predicate abstraction technique used in ComFoRT (component formal reasoning technology).
Variability in Software Product Lines
By paul c. clements, felix bachmann.
This 2005 report describes the concepts needed when creating core assets with included variability. These concepts provide guidelines to core asset creators on how to model the variability explicitly, so …
QuARS: A Tool for Analyzing Requirement
By giuseppe lami.
This 2005 report describes a disciplined method and a related automated tool that can be used for the analysis of natural language requirements documents.
Preparing for Automated Derivation of Products in a Software Product Line
By john mcgregor.
This 2005 report provides an end-to-end view of the activities that are needed to support the automatic derivation of products within a software product line.
The U.S. Army's Common Avionics Architecture System (CAAS) Product Line: A Case Study
By paul c. clements, john k. bergey.
This report offers a case study of organizations that have adopted a software product line approach for developing a family of software-intensive systems.
Limits to Effectiveness in Computer Security Incident Response Teams
August 22, 2005 • white paper, by johannes wiik (agder university college norway), jose j. gonzalez (agder university college norway).
In this paper, the authors present an attempt to gain a better understanding of how a CSIRT can handle a growing work load with limited resources.
Information Technology: Programming Languages, Their Environments and System Software Interfaces: Specification for Managed Strings
August 19, 2005 • white paper, by robert c. seacord, fred long.
In this paper, the authors present a standard specification for managed strings.
Simulating Insider Cyber-Threat Risks: A Model-Based Case and a Case-Based Model
August 11, 2005 • white paper, by elise a. weaver (worcester polytechnic institute), howard f. lipson, eliot rich (university at albany state university of new york), jose m. sarriegui (university of navarra spain), agata sawicka (agder university college norway), thomas r. stewart (university at albany state university of new york), jose m. torres (university of navarra spain), johannes wiik (agder university college norway), ignacio j. martinez-moyano (university at albany state university of new york), paul conrad, david f. andersen (university at albany state university of new york), dawn cappelli, andrew p. moore, dave mundie, timothy j. shimeall, robert j. ellison, jose j. gonzalez (agder university college norway).
In this paper, the authors identify actions that may inadvertently lead to increased vulnerability to threats from employees, contractors, and clients.
Obtaining the Benefits of Predictable Assembly from Certifiable Components (PACC)
August 1, 2005 • white paper, by kurt c. wallnau.
PACC combines the complementary features of software architecture technology and software component technology to improve both engineering productivity and product quality in the design and implementation of quality-critical software systems.
The Personal Software Process (PSP) Body of Knowledge, Version 1.0
August 1, 2005 • special report, by watts s. humphrey, marsha pomeroy-huff, julia l. mullaney, robert cannon, mark sebern.
The body of knowledge contained in this report is designed to complement the IEEE Computer Society's Software Engineering Body of Knowledge (SWEBOK) by delineating the key skills and concepts that …
Self-Assessment and the CMMI-AM—A Guide for Government Program Managers
August 1, 2005 • technical note, by stephen blanchette, jr., kristi keeler.
This 2005 report provides program managers with general information about the CMMI-AM, details about the self-assessment technique, and the questions used in a self-assessment.
Some Current Approaches to Interoperability
By david j. carney, david fisher, patrick r. place, edwin j. morris.
This 2005 report examines some of the complexities of interoperability and some recent research approaches to achieving it.
Using Containers to Enforce Smart Constraints for Performance in Industrial Systems
By gabriel moreno, scott hissam, kurt c. wallnau.
This technical note shows how smart constraints can be embedded in software infrastructure, so that systems conforming to those constraints are predictable by construction.
The ComFoRT Reasoning Framework
July 1, 2005 • white paper, by kurt c. wallnau, sagar chaki, james ivers, natasha sharygina.
Model checking is a promising technology for verifying critical behavior of software. However, software model checking is hamstrung by scalability issues and is difficult for software engineers to use directly. …
Comparing the SEI's Views and Beyond Approach for Documenting Software Architectures with ANSI-IEEE 1471-2000
July 1, 2005 • technical note.
This report summarizes the V&B and 1471 approaches to architecture description, and shows how a software architecture document prepared using V&B can be made compliant with 1471.
Product Line Adoption in a CMMI Environment
By lawrence g. jones, linda m. northrop.
This 2005 technical note addresses product line adoption in the context of an organization that is using the CMMI models to guide its process improvement effort.
Reasoning Frameworks
July 1, 2005 • technical report, by len bass, paulo merson, james ivers, mark h. klein.
This report describes a vehicle for encapsulating the quality attribute knowledge needed to understand a system's quality behavior as a reasoning framework that can be used by nonexperts.
The Impact of Function Extraction Technology on Next-Generation Software Engineering
By alan r. hevner (university of south florida), mark pleszkoch, gwendolyn h. walton, rosann w. collins, stacy j. prowell, richard c. linger (oak ridge national laboratory).
In this 2005 report, the authors summarize FX research and development and investigates the impact of FX on software engineering.
Designing for Reuse of Configurable Logic
This 2005 report provides an overview of a generic FPGA firmware design process and identifies the resulting work products that may be suitable for reuse in future development efforts.
Word Level Predicate Abstraction and Refinement for Verifying RTL Verilog
June 1, 2005 • white paper, by natasha sharygina, edmund clarke, daniel kroening.
This paper proposes to use predicate abstraction for verifying RTL Verilog, a technique successfully used for software verification.
Advanced Security Reporting Systems for Large Network Situational Awareness
By greg virgin (redjack), michael collins.
In this paper, the authors describe the technologies that support an asset inventory system and enable a flexible, ad-hoc intrusion detection capability.
The CENTAUR System: Helping to Protect the NIPRNet
By jeffrey jaime (applied technology unit, joint task force - global network operations, united states strategic command), marc i. kellner.
In this paper, the authors describe the CENTAUR system, which was developed to help DoD security analysts better understand and defend the NIPRNet.
By Aaron Hackworth
In this 2005 paper, the authors give an overview of spyware, provide examples of common threats, and describe how to defend against spyware.
Report on Annual Regional Information Assurance Symposia
June 1, 2005 • special report.
In this report, Carol Sledge explains why the annual Regional Information Assurance Symposia is a key transition component of Regional Collaborative Clusters.
Using Earned Value Management (EVM) in Spiral Development
June 1, 2005 • technical note, by james smith, lisa brownsword.
This report explores the fundamental challenges in using Earned Value Management (EVM) with spiral development processes and proposes adaptations to some EVM principles to render it more suitable for today's …
Information Asset Profiling
By bradford j. willke, james f. stevens, richard a. caralli.
In this 2005 report, the authors describe IAP, a documented and repeatable process for developing consistent asset profiles.
Governing for Enterprise Security
In this 2005 report, Julia Allen examines governance thinking, principles, and approaches and applies them to the subject of enterprise security.
A Process for Context-Based Technology Evaluation
By lutz wrage, grace lewis.
This report describes a process called context-based evaluation that determines the fitness of a technology within a specific context.
Insider Threat Study: Illicit Cyber Activity in the Banking and Finance Sector
June 1, 2005 • technical report, by andrew p. moore, dawn cappelli, marissa r. randazzo (united states secret service), michelle keeney (united states secret service), eileen kowalski (united states secret service).
In this 2005 report, the authors outline the ITS, a study of insider incidents identified by public reporting or in fraud cases from the Secret Service.
Secret Service and CERT Release Report Analyzing Acts of Insider Sabotage via Computer Systems in Critical Infrastructure Sectors
May 16, 2005 • white paper.
This press release is the second in a series of reports focusing on insider threats to information systems and data in critical infrastructure sectors.
2005 E-Crime Watch Survey Findings
May 3, 2005 • white paper.
In this 2005 report, the authors summarize the results of the 2005 E-Crime Watch Survey, conducted to unearth electronic crime fighting trends and techniques.
A Taxonomy of Security-Related Requirements
May 1, 2005 • white paper.
This paper addresses the problems associated with a lack of a clear security taxonomy by identifying four different types of security-related requirements, providing them with clear definitions, and placing them …
Reflections on Software Agility and Agile Methods: Challenges, Dilemmas, and the Way Ahead
By linda levine.
This 2005 whitepaper argues for that the shift toward agile models and methods signals a larger transformation in the workplace toward the organization of the 21st century. The transition is …
Method Engineering and COTS Evaluation
By b. henderson-sellers, c. gonzalez-perez, m. k. serour, donald firesmith.
This position paper argues that a successful COTS evaluation process should be based on the principles of method engineering (ME).
2005 E-Crime Watch Survey Results
This paper summarizes the results of a survey conducted to gauge the current state of cybercrime.
Technical Trends in Phishing Attacks
By jason milletary.
In this paper, Jason Milletary identifies technical capabilities used to conduct phishing scams, reviews trends, and discusses countermeasures.
System Quality Requirements Engineering (SQUARE): Case Study on Asset Management System, Phase II
May 1, 2005 • special report, by dan gordon, neha wattas, eugene yu, ted stehney ii, nancy r. mead.
In this report, the authors describe the second phase of an application of the SQUARE Methodology on an asset management system.
Model Problems in Technologies for Interoperability: Model-Driven Architecture
May 1, 2005 • technical note.
This 2005 report looks at Model-Driven Architecture (MDA) as one of many technologies for accomplishing interoperability.
CMMI Acquisition Module (CMMI-AM), Version 1.1
May 1, 2005 • technical report, by hal wilson, roger bate, thomas bernard, brian p. gallagher.
This report documents acquisition practices that should be performed by government acquisition projects acquiring systems or services.
Industry Best Practices in Achieving Service Oriented Architecture
April 22, 2005 • white paper.
This document represents the first iteration of a conversation and is neither a complete nor exhaustive coverage of the evolving subject of SOA.
Pin Component Technology (V1.0) and Its C Interface
April 1, 2005 • technical note, by kurt c. wallnau, daniel plakosh, james ivers, scott hissam.
This 2005 report describes the main concepts of Pin and documents the C-language interface to Pin V1.0.
Robustness Testing of Software-Intensive Systems: Explanation and Guide
By julie b. cohen, daniel plakosh, kristi keeler.
This 2005 technical note provides guidance and procedures for performing robustness testing as part of DoD or federal acquisition programs that have a software component.
Mapping TSP to CMMI
April 1, 2005 • technical report, by daniel s. wall, watts s. humphrey, jim mchale, michael d. konrad.
This 2005 report provides an essential element to facilitate the adoption of the TSP in organizations using CMMI, namely, a mapping of ideal TSP practices into the specific and generic …
U.S. Army Acquisition: The Program Executive Officer Perspective
March 1, 2005 • special report.
The U.S. Army Strategic Software Improvement Program (ASSIP) is a multi-year effort to improve the way the Army acquires software-intensive systems. As part of the ASSIP, the Carnegie Mellon Software …
Topics in Interoperability: System-of-Systems Evolution
March 1, 2005 • technical note, by patrick r. place, david fisher, david j. carney.
This report - the first in a series of reports on interoperability - examines how interoperable systems of systems evolve.
Eliciting and Analyzing Quality Requirements: Management Influences on Software Quality Requirements
In this 2005 report, Carol Woody documents how environments for system development can support or reject improved quality requirements elicitation mechanisms.
Software Product Lines: Experiences from the Seventh DoD Software Product Line Workshop
March 1, 2005 • technical report, by lawrence g. jones, patrick donohoe, john k. bergey, sholom g. cohen.
This 2005 report summarizes discussions and presentations from the Seventh Department of Defense (DoD) Product Line Practice Workshop.
Software Process Improvement Journey: IBM Australia Application Management Services
By robyn nichols, colin connaughton.
This report describes the work of the 2004 recipient of the IEEE Computer Society Software Process Achievement Award, jointly established by the SEI and IEEE to recognize outstanding achievements in …
Including Interoperability in the Acquisition Process
By ira monarch, james smith, b. craig meyers, linda levine.
This 2005 report explores achieving interoperability in the acquisition process.
Interpreting SCAMPI for a People CMM Appraisal at Tata Consultancy Services
February 1, 2005 • special report, by sarah miller, will hayes, ron radice, gian wemyss, jack r. ferguson, william e. hefley, bill curtis (cast research labs).
This 2005 report includes the draft interpretation guide used for four mini-appraisal pilots and the final enterprise-wide Class A appraisal at Tata Consultancy Services (TCS).
Software Architecture in DoD Acquisition: An Approach and Language for a Software Development Plan
February 1, 2005 • technical note.
This report discusses the Software Development Plan (SDP), providing an example approach and corresponding SDP language that enable software architecture to play a central role in the technical and organizational …
Software Architecture in DoD Acquisition: A Reference Standard for a Software Architecture Document
By john k. bergey, paul c. clements.
This report provides a reference standard for a Software Architecture Document (SAD). Acquisition organizations can use this to acquire documentation needed for communicating the architecture design and conducting software architecture …
The Structured Intuitive Model for Product Line Economics (SIMPLE)
February 1, 2005 • technical report, by sholom g. cohen, john mcgregor, paul c. clements.
This 2005 report presents SIMPLE, a general-purpose business model that supports the estimation of the costs and benefits in a product line development organization.
Preliminary System Dynamics Maps of the Insider Cyber-Threat Problem
January 1, 2005 • white paper, by andrew p. moore, timothy j. shimeall, dawn cappelli, david f. andersen (university at albany state university of new york), jose j. gonzalez (agder university college norway), eliot rich (university at albany state university of new york), jose m. sarriegui (university of navarra spain), elise a. weaver (worcester polytechnic institute), aldo zagonel (university at albany, rockefeller college of public affairs and policy), mohammad mojtahedzadeh (attune group, inc.), jeffrey m. stanton (syracuse university, school of information studies).
This paper discusses the preliminary system dynamic maps of the insider cyber-threat and describes the main ideas behind the research proposal.
MAAP Information Sheet
Information sheet on MAAP, a technique for assuring completion of defined missions by identifying and analyzing operational risks affecting mission-critical processes.
A Structured Approach to Classifying Security Vulnerabilities
January 1, 2005 • technical note, by robert c. seacord, allen d. householder.
In this 2005 report, the authors propose a classification scheme that uses attribute-value pairs to provide a multidimensional view of vulnerabilities.
2004 CERT Incident Notes
December 31, 2004 • white paper.
This document contains the CERT incident notes from 2004.
2004 CERT Advisories
This document contains the CERT advisories from 2004.
CMMI-Based Professional Certifications: The Competency Lifecycle Framework
December 1, 2004 • special report, by sandra behrens, steve masters, judah mogilensky.
This report describes how a competency life-cycle framework can be used as the basis for the CMMI-based professional certifications.
Systems Quality Requirements Engineering (SQUARE) Methodology: Case Study on Asset Management System
By marjon dean, don ojoko-adams, peter chen, hassan osman, lilian lopez, nick xie, nancy r. mead.
In this 2004 report, the authors describe the first case study that applied the SQUARE methodology to an organization.
Promising Technologies for Future Systems
December 1, 2004 • technical note, by lutz wrage, grace lewis, edwin j. morris.
This 2004 report presents of a few of the many programs, technologies, and research efforts that are addressing the challenges faced by future systems.
Managing for Enterprise Security
By william r. wilson, julia h. allen, richard a. caralli, james f. stevens, bradford j. willke.
In this 2004 report, the authors itemize characteristics of common approaches to security that limit effectiveness and success.
Discovering Architectures from Running Systems: Lessons Learned
December 1, 2004 • technical report, by jonathan aldrich, bradley schmerl, david garlan, hong yan, rick kazman.
This report describes a technique that uses automatically generated runtime observations of an executing system to construct an architectural view of the system.
Approaches to Constructive Interoperability
This report outlines several approaches to constructing systems of systems that have interoperability requirements, with respect to syntactic and semantic interoperability.
Rapid Integration Tools for Rapid Application Development A Case Study on Legacy Integration
By patrick r. place, amit midha, ravindra singh, lakshimi p. hari.
This 2004 report investigates the rapid integration tools available in the current market. The report presents a generic evaluation framework for identifying and evaluating rapid integration tools and an evaluation …
The Incident Object Description Exchange Format (IODEF) Implementation Guide
November 9, 2004 • white paper, by roman danyliw.
This document provides implementation guidelines for CSIRTs adopting the IODEF.
SQUARE Project: Cost/Benefit Analysis Framework for Information Security Improvement Projects in Small Companies
November 1, 2004 • technical note, by lilian lopez, nick xie, peter chen, marjon dean, don ojoko-adams, hassan osman, nancy r. mead.
In this 2004 report, the authors describe a cost/benefit analysis for estimations in small companies' information security improvement projects.
Predicate Abstraction with Minimum Predicates
October 1, 2004 • white paper, by sagar chaki, edmund clarke.
Predicate abstraction is a popular abstraction technique employed in formal software verification. Experiments show that predicate minimization can result in a significant reduction of both verification time and memory usage …
Results of SEI Independent Research and Development Projects and Report on Emerging Technologies and Technology Trends (FY 2004)
October 1, 2004 • technical report, by william o'brien, angel jordan, dennis b. smith, eileen c. forrester, sven dietrich, jeannine siviy, john k. bergey, howard f. lipson, charles weinstock, nancy r. mead, carol woody, edwin j. morris, rick kazman, donald firesmith, grace lewis.
This report describes the IR&D projects that were conducted during fiscal year 2004 (October 2003 through September 2004).
CMMI Interpretive Guidance Project: What We Learned
October 1, 2004 • special report, by mary beth chrissis, sandra shrum, michael d. konrad, gian wemyss, kenneth smith.
This report summarizes the results of the Capability Maturity Model Integration (CMMI) Interpretive Guidance Project, and summarizes and analyzes 7500 comments received regarding CMMI adoption that were reported by CMMI …
Illuminating Patterns of Perception: An Overview of Q Methodology
October 1, 2004 • technical note, by mary m. brown.
This 2004 technical note describes ways for applying Q methodology, a research method with a proven history for illuminating agreement and differences among individual and group perceptions, to assist software …
Defining Incident Management Processes for CSIRTs: A Work in Progress
By christopher j. alberts, robin ruefle, mark zajicek, audrey j. dorofee, georgia killcrece.
In this report, the authors present a prototype best practice model for performing incident management processes and functions.
Measurement and Analysis: What Can and Does Go Wrong?
September 1, 2004 • white paper, by dennis goldenson, maureen brown (university of north carolina).
Analyses of more than 1350 findings drawn from 663 Software CMM appraisals suggest several areas where both managers and engineers would benefit from better guidance about the proper use of …
A Taxonomy of Safety-Related Requirements
This paper describes a taxonomy of different kinds of safety-related requirements, and clearly and briefly defines and describes each of them.
A Roadmap of Risk Diagnostic Methods: Developing an Integrated View of Risk Identification and Analysis Techniques
September 1, 2004 • technical note, by kate ambrose, laura bentrem, ray c. williams.
This technical note describes the characteristics that determine whether a risk diagnostic method qualifies for the roadmap. It also describes the characteristics of diagnostic methods that do not qualify for …
Code of Professional Conduct for SEI Services, Version 1.0
September 1, 2004 • special report, by richard cox.
This report provides a set of expectations and practices for those operating under license or other applicable agreement with Carnegie Mellon University, acting through its Software Engineering Institute.
Benefits of Improvement Efforts
By peter capell.
This special report surveys the process improvement efforts undertaken by programs and projects that incorporate software-intensive systems.
Risk Based Diagnostics
By ray c. williams, laura bentrem, tom merendino, kate ambrose.
The SEI has constructed a tentative "roadmap" for personnel involved in the systems and software acquisition community. This report describes the characteristics that determine whether a risk diagnostic method qualifies …
Security and Survivability Reasoning Frameworks and Architectural Design Tactics
By andrew p. moore, felix bachmann, robert j. ellison, mark h. klein, len bass.
In this report, the authors describe an approach to disciplined software architecture design for the related quality attributes of security and survivability.
Applications of the Indicator Template for Measurement and Analysis
By wolfhart b. goethert, jeannine siviy.
This report presents guidance for adapting and completing an indicator template--an SEI-developed tool to describe an indicator's construction, interpretation, and how it can be best utilized.
Software Component Certification: 10 Useful Distinctions
This 2004 report discusses 10 useful distinctions that can help in understanding different aspects of certification in the context of software components.
Integrating Software-Architecture-Centric Methods into Extreme Programming (XP)
By robert nord, james e. tomayko, robert wojcik.
The report presents a summary of XP (Extreme Programming) and examines the potential uses of the SEI's architecture-centric methods.
Creating and Using Software Architecture Documentation Using Web-Based Tool Support
By judith a. stafford.
This report describes a design prototype that demonstrates a web-based approach to creating, communicating, and using software architecture throughout the life of the system.
Software Process Improvement and Product Line Practice: Building on Your Process Improvement Infrastructure
By lawrence g. jones.
This 2004 report describes how a process improvement infrastructure can provide a foundation for product line adoption.
Performance Property Theories for Predictable Assembly from Certifiable Components (PACC)
September 1, 2004 • technical report, by paulo merson, kurt c. wallnau, scott hissam, gabriel moreno, mark h. klein, john lehoczky (carnegie mellon university).
This report develops a queueing-theoretic solution to predict, for a real-time system, the average-case latency of aperiodic tasks managed by a sporadic server.
Software Product Line Adoption Roadmap
By linda m. northrop.
This 2004 report introduces a variant of the Factory Pattern called the Adoption Factory pattern that provides a generic roadmap to guide a manageable, phased product line adoption strategy.
Steps for Creating National CSIRTs
August 2, 2004 • white paper.
In this paper, Georgia Killcrece provides a high-level description of a National Computer Security Incident Response Team (NatCSIRT), its problems, and challenges.
Assumptions Management in Software Development
August 1, 2004 • technical note, by teeraphong mahatham, lutz wrage, grace lewis.
This technical note explores assumptions management as a method for improving software quality.
Statistical Methods for Flow Data
July 22, 2004 • white paper, by joseph b. kadane.
In this presentation, Joseph B. Kadane discusses how Bayesian methods help make the logistic regression approach to scan data stable and operationally feasible.
Integrating the Quality Attribute Workshop (QAW) and the Attribute-Driven Design (ADD) Method
July 1, 2004 • technical note, by william wood, robert nord, paul c. clements.
This technical note reports on a proposal to integrate the SEI Quality Attribute Workshop (QAW) and the SEI Attribute-Driven Design (ADD) method.
A Model Problem for an Open Robotics Controller
By scott hissam, mark h. klein.
This report describes the model problem created to support the continued enhancement and development of the PECT reasoning frameworks for an industrial trial in the domain of industrial robotics.
A Process for COTS Software Product Evaluation
July 1, 2004 • technical report, by santiago comella-dorda, john dean, tricia oberndorf, erin harper, grace lewis, edwin j. morris.
This 2004 report focuses on COTS product evaluations conducted for the purpose of selecting products to meet a known need in a system.
The Critical Success Factor Method: Establishing a Foundation for Enterprise Security Management
By william r. wilson, bradford j. willke, richard a. caralli, james f. stevens.
In this report, the authors describe the critical success factor method and present theories and experience in applying it to enterprise security management.
Integrating Software-Architecture-Centric Methods into the Rational Unified Process
By james e. tomayko, philippe kruchten, robert nord, rick kazman.
This report presents a summary of the RUP (Rational Unified Process) and examines the potential uses of the SEI's architecture-centric methods.
Acquisition Overview: The Challenges
June 1, 2004 • white paper.
In this paper, the authors raise issues involving how systems are integrated to provide required capabilities.
Embedded Systems Architecture Analysis Using SAE AADL
June 1, 2004 • technical note, by john j. hudak, peter h. feiler, david p. gluch, bruce lewis (u.s. army amcom).
This 2004 report discusses the role and benefits of using the AADL in the process of analyzing an existing avionics system.
2004 E-Crime Watch Survey Findings
May 25, 2004 • white paper.
In this report, the authors summarize the results of the 2004 E-Crime Watch Survey, conducted to unearth e-crime fighting trends and techniques.
An Empirical Analysis of Target-Resident DoS Filters
May 9, 2004 • white paper, by michael k. reiter, michael collins.
In this paper, the authors provide an empirical analysis of proposed techniques for filtering network traffic.
Software Patents: Innovation or Litigation?
May 1, 2004 • white paper, by linda levine, kurt m. saunders.
This paper summarizes the scope of patent protection in the European Union, the United States, and Japan. In doing so, it examines the patentability of computer software as inventions allowed …
Networked Technologies: The Role of Networks in the Diffusion and Adoption of Software Process Improvement (SPI) Approaches
By karlheinz kautz, jorn johansen, peter a. nielsen, linda levine, william e. hefley.
Social networks play a key role in the adoption and diffusion of software process improvement as a networked technology. This panel addressed actual examples of SPI networks and identified key …
Selecting Advanced Software Technology in Two Small Manufacturing Enterprises
May 1, 2004 • technical note, by william anderson, charles buhman, len estrin.
This 2004 report documents two small manufacturing enterprises' (SMEs') efforts to select advanced software technologies for their business operations.
Survivable Functional Units: Balancing an Enterprise's Mission and Technology
By larry rogers.
In this 2004 report, Larry Rogers describes enterprise networks in a way that helps system administrators see how technology supports the enterprise's mission.
Dependability Cases
By john j. hudak, john b. goodenough, charles weinstock.
In this 2004 report, the authors explain how to create a dependability case for a system that helps identify and keep track of details of large systems.
Case Study: A Measurement Program for Product Lines
By ed dunn (naval undersea warfare center), sholom g. cohen, david zubrow.
This report documents NUWC's approach for measurement by describing the Goal-Driven Software Measurement approach and providing early results of the measurement program.
Advanced Engineering Environments for Small Manufacturing Enterprises: Volume II
May 1, 2004 • technical report, by steven j. fenves (national institute of standards and technology), ram d. sriram (national institute of standards and technology), young choi (chung-ang university), joseph p. elm, john e. robert.
This report documents the Self-Assessment Tool for Engineering Environments (SAT-EE) and the Self-Assessment Tool for Engineering Tool Capabilities (SAT-ETC).
Standard Systems Group (SSG) Technology Adoption Planning Workshop
April 1, 2004 • special report, by lorraine nemeth-adams, jan vargas, suzanne miller.
This 2004 report presents the results of the SSG Technology Adoption Planning Workshop, which was held in October 2003 in Alabama.
Measuring Systems Interoperability: Challenges and Opportunities
April 1, 2004 • technical note, by william anderson, mark kasunic.
This 2004 report presents best practices for measuring systems interoperability and assisting military planners in the acquisition, development, and implementation of interoperable C4I systems.
Overview of ComFoRT: A Model Checking Reasoning Framework
By james ivers, natasha sharygina.
This 2004 report describes ComFoRT, a reasoning framework that packages the effectiveness of state-of-the-art model checking in a form that enables users to apply the analysis technique without being experts …
Systems of Systems Interoperability
April 1, 2004 • technical report, by edwin j. morris, patrick r. place, daniel plakosh, linda levine, b. craig meyers.
This technical report documents the findings of an internal research and development effort on system of systems interoperability (SOSI).
Documenting Component and Connector Views with UML 2.0
By james ivers, robert nord, paul c. clements, oviedo silva (carnegie mellon school of computer science), bradley schmerl, david garlan.
This 2004 report explores how changes in UML 2.0 affect UML's suitability for documenting component and connector views.
An Alternative to Technology Readiness Levels for Non-Developmental Item (NDI) Software
This report explores the difficulties in using TRLs as they apply to NDI software technology and products, and explores an alternative set of readiness criteria.
COTS Usage Risk Evaluation Participant’s Overview
March 29, 2004 • white paper.
This document provides an overview of the three steps of the COTS Usage Risk Evaluation (CURE) that involve participation by the program's team members. For each step, both the activity …
Sets, Bags, and Rock and Roll? Analyzing Large Data Sets of Network Data
March 24, 2004 • white paper, by john mchugh.
In this paper, John McHugh describes problems with monitoring and analyzing traffic on high-speed networks.
Conflict Patterns: Toward Identifying Suitable Middleware
March 1, 2004 • white paper.
This whitepaper describes patterns of interoperability conflicts along with their typical resolution in an effort to present reusable solutions for the design of integration architectures.
Software Product Lines: Experiences from the Sixth DoD Software Product Line Workshop
March 1, 2004 • technical note, by john k. bergey, dennis b. smith, lawrence g. jones, sholom g. cohen.
This 2004 report summarizes the presentations and discussions from the Sixth Department of Defense (DoD) Product Line Practice Workshop in September 2003.
A Study of Product Production in Software Product Lines
By john mcgregor, patrick donohoe, gary chastek.
This 2004 report presents the results of a study that focused on how product line organizations create products.
Case Study: IRS Business System Modernization Process Improvement
March 1, 2004 • technical report, by lloyd anderson, jon gross, matt fisher.
This report provides an overview of applying the SA-CMM to the IRS modernization effort to establish and implement more effective acquisition management processes and practices.
Army Strategic Software Improvement Program (ASSIP) Survey of Army Acquisition Managers
This report analyzes a survey that covered four areas of the acquisition system: the acquirer's environment, the developer's environment, communication between the acquirer and developer, and external factors that could …
An Integrated Approach to Software Process Improvement at Wipro Technologies: veloci-Q
By deb sambuddha (wipro technologies), priya krishnaswamy (wipro technologies), rituparna ghosh (wipro technologies).
This report describes the work of the 2002 recipient of the IEEE Computer Society Software Process Achievement Award, jointly established by the SEI and IEEE to recognize outstanding achievements in …
Current Perspectives on Interoperability
By b. craig meyers, david j. carney, lutz wrage, david fisher, james smith, grace lewis, edwin j. morris, lisa brownsword, patrick r. place.
This 2004 report describes current research within the software engineering community on the topic of interoperability between software systems.
A-Specification for the CMMI Product Suite, Version 1.6
February 6, 2004 • white paper.
The A-Specification for the CMMI Product Suite defines the scope, lists applicable documents, and defines the requirements the CMMI Product Suite must meet to be considered acceptable.
Upgrading from SW-CMM to CMMI
February 1, 2004 • white paper.
This whitepaper shows how organizations can promptly move from a maturity level of the SW-CMM to the corresponding maturity level of CMMI.
CMMI Acquisition Module (CMMI-AM) Version 1.0
February 1, 2004 • technical report, by thomas bernard, roger bate, brian p. gallagher, hal wilson.
This report contains the acquisition practices that should be performed by government acquisition organizations acquiring systems and/or services.
Working with Small Manufacturing Enterprises: An Analysis of TIDE
By john t. foreman, len estrin, john e. robert, alfred schenker, william anderson, suzanne miller, joseph p. elm.
This 2004 paper documents some of the challenges and risks facing programs or organizations trying to help small manufacturing enterprises (SMEs).
Financial Institution CSIRT Case Study
January 22, 2004 • white paper.
This case study describes the experiences of a financial institution CSIRT in getting its organization up and running.
Eight Architecture Lessons from History
January 1, 2004 • white paper.
This 2004 whitepaper offers eight lessons from history for the software architecture field, drawn from peer fields i.e. Military, Civil, Finance, Mathematics, Astronomy, Social and Medical.
COTS Acquisition Evaluation Process: Preacher's Practice
January 1, 2004 • technical note, by vijay sai.
This paper outlines a successful effort to apply COTS-based engineering principles to a software acquisition by various groups at the SEI.
2003 CERT Incident Notes
December 31, 2003 • white paper.
This document contains the CERT incident notes from 2003.
CERT Research 2003 Annual Report
This report provides brief abstracts for major research projects, followed by more detailed descriptions of these projects, for all CERT research conducted in the year 2003.
2003 CERT Advisories
This document contains the CERT advisories from 2003.
Common Concepts Underlying Safety, Security, and Survivability Engineering
December 1, 2003 • technical note.
In this report, Donald Firesmith presents information models that identify and define concepts underlying safety, security, and survivability engineering.
Integrating the Architecture Tradeoff Analysis Method (ATAM) with the Cost Benefit Analysis Method (CBAM)
By rick kazman, paul c. clements, robert nord, mark h. klein, james e. tomayko, liam o'brien, mario r. barbacci.
This technical note reports on a proposal to integrate the SEI ATAM (Architecture Tradeoff Analysis Method) and the CBAM (Cost Benefit Analysis Method).
SACAM: The Software Architecture Comparison Analysis Method
December 1, 2003 • technical report, by felix bachmann, christoph stoermer, chris verhoef.
The report describes SACAM, a method that provides rationale for an architecture selection process by comparing the fitness of architecture candidates for required systems.
Advanced Engineering Environments for Small Manufacturing Enterprises: Volume I
By joseph p. elm, john e. robert, steven j. fenves (national institute of standards and technology), ram d. sriram (national institute of standards and technology), young choi (chung-ang university).
This report provides an overview of AEE technologies, their benefits for subject matter experts, and the technical considerations for AEE adoption.
Real-Time Application Development with OSEK: A Review of the OSEK Standards
November 1, 2003 • technical note.
This 2003 report examines the OSEK OS, OSEK COM, and OSEK OIL specifications from the perspective of a real-time application developer.
Interpreting Capability Maturity Model Integration (CMMI) for Service Organizations' Systems Engineering and Integration Services Example
By mike phillips, julie a. walker, mary anne herndon (saic), robert moore (saic), laura west (saic).
This 2003 technical note presents one organization's interpretation of CMMI best practices for organizations that primarily provide services.
Architecture Reconstruction of J2EE Applications: Generating Views from the Module Viewtype
By liam o'brien, vorachat tamarree.
This report outlines the application of architecture reconstruction techniques to the Sun Microsystems' Duke's Bank system- Java2 Platform, Enterprise Edition/Enterprise JavaBeans (J2EE/EJB) application implemented mainly in Java.
Architecture Reconstruction Guidelines, Third Edition
November 1, 2003 • technical report, by liam o'brien, chris verhoef, rick kazman.
This report describes the process of architecture reconstruction using the Dali architecture reconstruction workbench.
Developing a Communication Strategy for a Research Institute
October 1, 2003 • white paper, by bill pollak, mike petock, anne humphreys.
This 2004 white paper presents a communication strategy that defines products and internal processes for optimizing communication with the Software Engineering Institute's (SEI) most important stakeholders.
CMMI Interpretive Guidance Project: Preliminary Report
October 1, 2003 • special report, by gian wemyss, kenneth smith, agapi svolou, michael d. konrad, mary beth chrissis, dennis goldenson.
The SEI collected data to learn more about how CMMI is being accepted by various organizations. This report describes those activities and includes summaries of the data collected.
Demonstrating the Impact and Benefits of CMMI: An Update and Preliminary Results
By dennis goldenson, diane gibson.
This 2003 report demonstrates credible quantitative evidence that CMMI-based process improvement can result in better project performance and higher quality products.
Deriving Enterprise-Based Measures Using the Balanced Scorecard and Goal-Driven Measurement Techniques
October 1, 2003 • technical note, by matt fisher, wolfhart b. goethert.
This 2003 report describes the application of the balanced scorecard and goal-driven measurement methodologies to ways to measure an organization's health and performance.
A Template for Documenting Prediction-Enabled Component Technologies
This report proposes a template for documenting a PECT, and provides guidelines and a few examples to help PECT developers consolidate the broad range of information produced into the PECT …
Measures for Software Product Lines
By david zubrow, gary chastek.
This 2003 report characterizes the status of measurement associated with the operation of a software product line, suggests a small set of measures to support its management, and provides guidance …
State of the Practice of Computer Security Incident Response Teams (CSIRTs)
October 1, 2003 • technical report, by klaus-peter kossakowski, georgia killcrece, mark zajicek, robin ruefle.
In this 2003 report, the authors provide a study of the state of the practice of incident response, based on how CSIRTs around the world are operating.
Quality Attribute Workshops (QAWs), Third Edition
By robert j. ellison, charles weinstock, william wood, anthony j. lattanze, judith a. stafford, mario r. barbacci.
This report describes the newly revised QAW (Quality Attribute Workshop) and describes potential uses of the refined scenarios generated during it.
Analyzing and Specifying Reusable Security Requirements
September 1, 2003 • white paper.
A system cannot have high assurance if it has poor security, and thus, requirements for high assurance systems will logically include security requirement as well as availability, reliability, and robustness …
Requirements Engineering for Survivable Systems
September 1, 2003 • technical note.
In this 2003 report, Nancy Mead describes the state of requirements engineering for survivable systems.
A Life-Cycle View of Architecture Analysis and Design Methods
By robert nord, rick kazman, mark h. klein.
This report examines the architecture-centric analysis and design methods that were created at the SEI between 1993 and 2003.
DoD Experience with the C4ISR Architecture Framework
By sholom g. cohen, william wood.
This report discusses the context for using the C4ISRAF, the observations made during the interviews about its use, and the strengths and challenges of using it.
Predictable Assembly of Substation Automation Systems: An Experiment Report, Second Edition
September 1, 2003 • technical report, by judith a. stafford, magnus larsson, william wood, scott hissam, mark h. klein, james ivers, john j. hudak, linda m. northrop, gabriel moreno, daniel plakosh, kurt c. wallnau.
This 2003 report describes the results of an exploratory PECT prototype for substation automation, an application area in the domain of power generation, transmission, and management.
Product Line Analysis for Practitioners
By gary chastek, patrick donohoe.
This 2003 technical report describes the addition of development requirements to product line analysis.
The Team Software Process (TSP) in Practice: A Summary of Recent Results
By julia l. mullaney, noopur davis.
This 2003 report provides results and implementation data from projects and individuals that have adopted the TSP.
SEI Independent Research and Development Projects (FY 2003)
By edwin j. morris, suzanne miller, robert c. seacord, peter h. feiler, felix bachmann, mark h. klein, daniel plakosh, patrick r. place, anthony j. lattanze, david j. carney, sven dietrich, b. craig meyers, len bass, john mchugh.
This report describes the IR&D projects that were conducted during fiscal year 2003 (October 2002 through September 2003).
A Model Problem Approach to Measurement-to-Track Association
By b. craig meyers, grace lewis.
This report illustrates the use of model problems in the design of a system.
Preliminary Design of ArchE: A Software Architecture Design Assistant
By felix bachmann, mark h. klein, len bass.
This 2003 report presents a procedure for moving from a set of quality attribute scenarios to an architecture design that satisfies those scenarios.
Interpreting Capability Maturity Model Integration (CMMI) for COTS-Based Systems
By barbara tyson, cecilia albert, lisa brownsword.
This 2003 report shows that developing and maintaining COTS-based systems is more than selecting products and managing vendor relationships.
Identifying Commercial Off-the-Shelf (COTS) Product Risks: The COTS Usage Risk Evaluation
By edwin j. morris, patrick r. place, david j. carney.
This 2003 report describes the development of an approach to reduce the number of program failures attributable to COTS software: the COTS Usage Risk Evaluation (CURE).
Locality: A New Paradigm for Thinking About Normal Behavior and Outsider Threat
August 18, 2003 • white paper, by carrie gates, john mchugh.
In this paper, the authors describe how locality appears in many dimensions and applies to diverse mechanisms.
Building Relationships between Small Manufacturing Enterprises and Vendors: Findings from the TIDE Program
August 1, 2003 • technical note, by len estrin, john t. foreman.
This report presents findings to help vendors, VARs, and SMEs develop mutually beneficial and successful relationships.
Preserving Real Concurrency
July 1, 2003 • white paper, by kurt c. wallnau, james ivers.
In this 2003 whitepaper, the authors make use of information provided by components and extracted from static assembly topologies to faithfully model real concurrency. The result is more effective analysis.
Measurement and Analysis in Capability Maturity Model Integration Models and Software Process Improvement
By dennis goldenson, joe jarzombek (osd-nii), terry rout (griffith university).
This article reviews the content and rationale behind the new process area and describes how the ideas introduced there are further elaborated and evolved throughout capability maturity model integration models.
Organizational Interoperability Maturity Model for C2
A model of organizational interoperability is proposed in this paper, which extends the LISI model into the more abstract layers of C2 Support, that is, the C2 Frameworks, C2 Processes, …
Gobus Toolkit 3 Core - A Grid Service Container Framework
By derek gabbard.
The core infrastructure of Globus Toolkit 3 (GT3 Core) is based on the OGSI primitives and protocols. The main design goal has been to make the OGSI technology easy to …
International Liability Issues for Software Quality
July 1, 2003 • special report.
In this 2003 report, Nancy Mead focuses on international liability as it relates to information security for critical infrastructure applications.
Using the Architecture Tradeoff Analysis Method (ATAM) to Evaluate the Software Architecture for a Product Line of Avionics Systems: A Case Study
July 1, 2003 • technical note, by anthony j. lattanze, mario r. barbacci, paul c. clements, linda m. northrop, william wood.
This 2003 technical note describes an ATAM evaluation of the software architecture for an avionics system developed for the Technology Applications Program Office (TAPO) of the U.S. Army Special Operations …
CMM-Based Process Improvement and Schedule Deviation in Software Maintenance
By dennis goldenson, ho-won jung.
This study evaluates the predictive validity of the Capability Maturity Model (CMM) for Software (SW-CMM) as applied to software maintenance.
Predicting When Product Line Investment Pays
By sholom g. cohen.
This 2003 report defines key factors to consider in taking an incremental approach to fielding a product line.
What About Ada? The State of the Technology in 2003
This 2003 report documents a recent investigation which characterized the technical and programmatic risks in reusing significant quantities of legacy Ada code in a new system.
Documenting Software Architectures in an Agile World
By judith a. stafford, robert nord, paul c. clements, james ivers, reed little.
This report compares the Software Engineering Institute's Views and Beyond approach for documenting software architectures with the documentation philosophy embodied in agile software-development methods.
Third International Workshop on Adoption-Centric Software Engineering
June 1, 2003 • special report, by jens-holger jahnke (university of victoria), marin litoiu (ibm canada ltd.), hausi a. muller (university of victoria), margaret-anne storey (university of victoria), scott r. tilley (florida institute of technology), kenny wong (university of alberta), anke weber (university of victoria), robert balzer (teknowledge corporation), dennis b. smith.
This report contains a set of papers that focus on overcoming barriers to adopting research tools. The papers were presented at the Third International Workshop on Adoption-centric Software Engineering (ACSE).
Proceedings of the System of Systems Interoperability Workshop (February 2003)
June 1, 2003 • technical note, by linda levine, b. craig meyers, edwin j. morris, patrick r. place, daniel plakosh.
This report documents the model of interoperability presented and the findings from the System of Systems Interoperability Workshop, held in February 2003.
Snapshot of CCL: A Language for Predictable Assembly
By james ivers, kurt c. wallnau.
This 2003 report presents a snapshot of the construction and composition language (CCL) by examining a small example CCL specification.
The Software Engineering Institute's Second Workshop on Predictable Assembly: Landscape of Compositional Predictability
By judith a. stafford, scott hissam.
To further its work in predictable assembly focusing on compositional reasoning techniques, the Software Engineering Institute (SEI) held its second Predictable Assembly from Certifiable Components (PACC) Workshop on January 10-11, …
Interactions Among Techniques Addressing Quality Attributes
June 1, 2003 • technical report, by mario r. barbacci, hernan r. eguiluz.
This report provides software architects a chart for determining the relationships among techniques that promote different architectural qualities.
The Evolution of Product Line Assets
The focus of this 2003 technical report is how evolutionary changes affect the various types of assets in a software product line.
Fifth DoD Product Line Practice Workshop Report
By lawrence g. jones, william o'brien, matt fisher, john k. bergey, sholom g. cohen, linda m. northrop.
This 2003 document summarizes the presentations and discussions from the Fifth Department of Defense (DoD) Product Line Practice Workshop, held in August 2002.
Overcoming Barriers to Technology Adoption in Small Manufacturing Enterprises (SMEs)
By len estrin, john t. foreman, suzanne miller.
This 2003 report summarizes technology demonstrations, workforce development activities, and technology development efforts of the SEI's TIDE Program.
Integration of Computer-Aided Design and Finite Element Analysis Tools in a Small Manufacturing Enterprise
By john e. robert, joseph p. elm.
This 2003 report summarizes two case studies of tool integration activities at one small manufacturer.
Architecture, Design, Implementation
May 1, 2003 • white paper, by rick kazman.
Architecture, design, and implementation are used informally in partitioning software specifications into three coarse strata of abstraction. These strata are not well-defined in either research or practice, causing miscommunication and …
The SAE Avionics Architecture Description Language (AADL) Standard: A Basis for Model-Based Architecture-Driven Embedded Systems Engineering
By peter h. feiler, steve vestal (honeywell technology center).
The AADL standard will include a UML profile useful for avionics, space, automotive, robotics and other real-time concurrent processing domains including safety critical applications.
A Basis for an Assembly Process for COTS-Based Systems (APCS)
May 1, 2003 • technical report, by patrick r. place, david j. carney, tricia oberndorf.
This paper describes a generic process framework for developing software systems based on commercial off-the-shelf (COTS) products.
Case Study: Computer Supplier Evaluation Practices of the Parenteral Drug Association
By tricia oberndorf, david j. carney, harvey greenawalt, grigonis grigonis.
This case study describes the development of a method for evaluating computer and software suppliers for the pharmaceutical industry.
Architecture Reconstruction Case Study
April 1, 2003 • technical note.
This report outlines an architecture reconstruction carried out at the SEI on a software system called VANISH, which was developed for prototyping visualizations.
Volume III: A Technology for Predictable Assembly from Certifiable Components
April 1, 2003 • technical report.
This 2003 report, the final in a three-volume series on CBSE, identifies the key technical concepts of PACC, with an emphasis on the theory of prediction-enabled component technology (PECT).
DoD Architecture Framework and Software Architecture Workshop Report
March 1, 2003 • technical note, by lyn uzzle, john weiler, art krummenoehl, huei-wan ang, loring bernhardt, fatma dandashi, david emery, mario r. barbacci, steve palmquist, paul c. clements, william wood, sarah sheard.
This report summarizes the activities of the Workshop on the Department of the 2003 Defense Architecture Framework and Software Architecture workshop.
A Federation Object Model (FOM) Flexible Federate Framework
By reed little, regis dumond.
This 2003 report describes an approach to designing a domain framework that encapsulates expertise in developing an HLA federate by hiding RTI internal operations from the developer.
Application of Options Analysis for Reengineering in a Lead System Integrator Environment
This note describes the use of OAR to guide decision making on mining assets within an LSI (lead system integrator) context.
Relating the Team Software Process (TSP) to the Capability Maturity Model for Software (SW-CMM)
March 1, 2003 • technical report, by noopur davis, watts s. humphrey, jim mchale.
This 2003 report helps process professionals, process managers, project leaders, and organizational managers establish process improvement strategies and plans.
Deriving Architectural Tactics: A Step Toward Methodical Architectural Design
By len bass, felix bachmann, mark h. klein.
This 2003 technical report provides the status on the work being done by the SEI to understand the relationship between quality requirements and architectural design.
On the Suitability of Tcl/Tk for SYS
February 1, 2003 • technical note, by fred hansen.
This 2003 report reviews various websites and considers other factors that should influence the choice of Tcl/Tk as a tool for further development of SYS.
Rendering Tcl/Tk Windows as HTML
Tcl is a programming language having a Toolkit library that provides a standard set of GUI widgets. Since these are aimed at direct presentation via a window manager, Tcl/Tk applications …
Applying FSQ Engineering Foundations to Automated Calculation of Program Behavior
By richard c. linger (oak ridge national laboratory).
In this report, Richard Linger describes the application of function-theoretic mathematical foundations to the problem of program behavior calculation.
Quantifying the Value of Architecture Design Decisions: Lessons from the Field
January 1, 2003 • white paper, by rick kazman, mark h. klein, mike moore (nasa goddard space flight center), jai asundi.
This paper outlines experiences with using economic criteria to make architecture design decisions.
Simple Network Management Protocol (SNMP) Vulnerabilities Frequently Asked Questions (FAQ)
This tech tip provides advice about the Simple Network Management Protocol (SNMP).
2003 Tech Tip: W32/Blaster Recovery Tips
This tech tip contains information about recovery from W32/Blaster.
2002 CERT Incident Notes
December 31, 2002 • white paper.
This document contains the CERT incident notes from 2002.
2002 CERT Advisories
This document contains the CERT advisories from 2002.
Supporting the CANCEL Command Through Software Architecture
December 1, 2002 • technical note, by bonnie e. john, len bass.
This report, published in 2002, details the responsibilities that a system must implement to support command cancellation.
PECT Infrastructure: A Rough Sketch
By james ivers, scott hissam.
This 2002 paper investigates the nature of PECT infrastructures, summarizes the activities that a PECT infrastructure should support, and proposes a design for the tools that make up a PECT …
Rules of Thumb for the Use of COTS Products
December 1, 2002 • technical report, by michele motsko, ellen-jane pairo, james smith, tricia oberndorf.
This 2002 report provides information to help guide decisions about when COTS products are an appropriate solution,and when they are not.
The Internal Consistency of Key Process Areas in the Capability Maturity Model (CMM) for Software (SW-CMM)
This report examines the dimensions underlying the maturity construct in the Capability Maturity Model (CMM) for Software (SW-CMM) and then estimates the internal consistency (reliability) of each dimension.
Network Survivability Analysis Using Easel
By alan m. christie.
In this 2002 report, Alan Christie describes the results of exploring the use of simulation in examining internet survivability.
CSIRT Services
November 25, 2002 • white paper.
In this paper, the authors define computer security incident response team (CSIRT) services.
Tracking and Tracing Cyber-Attacks: Technical Challenges and Global Policy Issues
November 1, 2002 • special report.
In this report, Howard Lipson describes the technical challenges and global policy issues related to cyber attacks.
Evolutionary Process for Integrating COTS-Based Systems (EPIC) Building, Fielding, and Supporting Commercial-off-the-Shelf (COTS) Based Solutions
November 1, 2002 • technical report, by david bentley (u.s. air force), thomas bono (mitre), deborah pruitt (mitre), edwin j. morris, lisa brownsword, cecilia albert.
This 2002 document is the first release of a full description of the EPIC framework along with its activities and artifacts.
Salion, Inc.: A Software Product Line Case Study
By paul c. clements, linda m. northrop.
This 2002 case study outlines the efforts of Salion, Inc., an enterprise software company providing Revenue Acquisition Management solutions tailored to the unique needs of automotive suppliers.
2002 Tech Tip: Problems With The FTP PORT Command or Why You Don't Want Just Any Port in a Storm
October 16, 2002 • white paper.
This tech tip contains discussion about problems with the FTP PORT command.
SEI Architecture Analysis Techniques and When to Use Them
October 1, 2002 • technical note, by mario r. barbacci.
When analyzing system and software architectures, the Quality Attribute Workshop (QAW) and the Architecture Tradeoff Analysis Method (ATAM) can be used in combination to obtain early and continuous benefits.
Model-Based Verification: Abstraction Guidelines
By santiago comella-dorda, david p. gluch, charles weinstock, john j. hudak, grace lewis.
This 2002 report presents abstraction techniques that can be used to build essential models of system behavior in the context of MBV and details a methodology for creating state machine …
Using CMMI to Improve Earned Value Management
By paul solomon.
For organizations using Earned Value Management (EVM) or that plan to implement EVM during Capability Maturity Model Integration (CMMI) implementation, this technical note provides guidance for cost-effective process improvement and …
SEI Independent Research and Development Projects
October 1, 2002 • technical report, by linda levine, dennis b. smith, richard c. linger (oak ridge national laboratory), eileen c. forrester, steve cross, ira monarch, thomas a. longstaff, scott hissam, kurt c. wallnau, rick kazman.
This report describes the IR&D projects that were conducted during fiscal year 2002 (October 2001 through September 2002).
Life-Cycle Models for Survivable Systems
By carol sledge, nancy r. mead, richard c. linger (oak ridge national laboratory), howard f. lipson, john mchugh.
In this 2002 report, the authors describe a software development life-cycle model for survivability and illustrate techniques to support survivability goals.
Trustworthy Refinement Through Intrusion-Aware Design
By robert j. ellison, andrew p. moore.
This document has been superseded by CMU/SEI-2003-TR-002.
Trustworthy Refinement Through Intrusion-Aware Design (TRIAD)
In this report, the authors demonstrate the application of TRIAD to refining a survivability strategy for a business that sells products on the internet.
Using the Technology Readiness Levels Scale to Support Technology Management in the DoD's ATD/STO Environments (A Findings and Recommendations Report Conducted for Army CECOM)
September 1, 2002 • special report, by caroline graettinger, jeannine siviy, peter j. van syckle, robert j. schenk, suzanne miller.
This report describes the results of the SEI study of the feasibility of (a) using TRLs in STO technology screening, (b) developing or acquiring a TRL tool, and (c) implementing …
Product Line State of the Practice Report
September 1, 2002 • technical note.
This 2002 report outlines the state of software product line practice in industry. The report blends a case study with the results of a product line questionnaire that was sent …
Successful Product Line Development and Sustainment: A DoD Case Study
By sholom g. cohen, ed dunn (naval undersea warfare center), albert soule.
This case study describes the Naval Undersea Warfare Center's (NWUC) efforts to sustain and support the evolution of RangeWare, a software product line asset base used to test range operations.
A Basis for Composition Language CL
By nishant sinha, james ivers, kurt c. wallnau.
This report describes the composition language CL and its rudimentary graphical syntax, and defines and illustrates the compositional semantics for CL using Hoare's CSP.
An Application of an Iterative Approach to DoD Software Migration Planning
By liam o'brien, dennis b. smith, john k. bergey.
This 2002 report outlines the early results of an approach to support software migration planning that focused on deriving actionable plans for focus areas that were identified in an initial …
Product Line Production Planning for the Home Integration System Example
By gary chastek, patrick donohoe, john mcgregor.
This 2002 technical note examines the significant characteristics of the production plans of three hypothetical organizations that create product lines of home integration systems.
Discovery Colloquium: Quality Software Development @ Internet Speed
September 1, 2002 • technical report, by richard baskerville, jan pries-heje, balasubramaniam ramesh, sandra slaughter, linda levine.
This report presents the data collected during a 2001 colloquium to explore issues associated with developing quality software at Internet speed.
Making Architecture Design Decisions: An Economic Approach
By rick kazman, mark h. klein, jai asundi.
This report describes the improvements to the CBAM (Cost Benefit Analysis Method) and provides a pilot case study conducted with NASA.
2002 Tech Tip: Securing an Internet Name Server
August 1, 2002 • white paper, by brian king, allen d. householder.
This document discusses name server security and focuses on BIND, which is the most commonly used software for DNS servers.
A Report on the May 2002 CMMI Workshop
August 1, 2002 • special report, by mark c. paulk, bill curtis (cast research labs), michael d. konrad, mary beth chrissis.
This report summarizes the results of the CMMI Workshop held on May 7-8, 2002.
PAMD: Developing a Plug-In Architecture for Palm OS-Powered Devices Using Software Engineering
August 1, 2002 • technical note, by hernan r. eguiluz, venkat govi, you jung kim, adrian sia.
This 2002 technical note describes a plug-in architecture for Palm Operating System devices developed by the authors, a team of graduate students from the CMU Master of Software Engineering program.
Plug-In Architecture for Mobile Devices
By madhu keshavamurthy, jung soo kim, mona li, vichaya sagetong.
This 2002 report describes plug-in architecture for mobile devices (PAMD), an architectural specification that extends the function of applications in mobile devices.
Model-Based Verification: An Engineering Practice
August 1, 2002 • technical report, by julie a. walker, david p. gluch, santiago comella-dorda, charles weinstock, john j. hudak, grace lewis, david zubrow.
This 2002 report summarizes MBV and outlines the responsibilities of engineers engaged in Model-Based Verification.
Software Architecture Reconstruction: Practice Needs and Current Approaches
By christoph stoermer, chris verhoef, liam o'brien.
This report presents the concept of practice scenarios for architecture reconstruction.
Illuminating the Fundamental Contributors to Software Architecture Quality
This 2002 report presents the basic concepts of analysis models for two quality attributes-modifiability and performance, identifies a collection of tactics that can be used to control responses within those …
CMMI for Software Engineering, Version 1.1, Continuous Representation (CMMI-SW, V1.1, Continuous)
This CMMI model is designed to help organizations improve their product and service development, acquisition, and maintenance processes.
CMMI for Software Engineering, Version 1.1, Staged Representation (CMMI-SW, V1.1, Staged)
Home computer security, july 8, 2002 • white paper.
This 2002 document provides tips for securing your home computer.
Reeducation to Expand the Software Engineering Workforce: Successful Industry/University Collaborations
July 1, 2002 • special report, by nancy r. mead, heidi j. ellis, stephen b. seidman, ana m. moreno (universidad politecnica de madrid).
In this 2002 report, the authors describe a study of reeducating non-software professionals and practitioners to become software engineers.
Replaceable Components and the Service Provider Interface
July 1, 2002 • technical note, by lutz wrage, robert c. seacord.
This 2002 report considers the motivation for using replaceable components and defines the requirements of replaceable component models.
Software Process Improvement and Product Line Practice: CMMI and the Framework for Software Product Line Practice
By lawrence g. jones, albert soule.
This 2002 report explores the relationship between software product line practice, as defined by the Framework for Software Product Line Practice, and software engineering process discipline, as defined by the …
Evolutionary Process for Integrating COTS-Based Systems (EPIC): An Overview
July 1, 2002 • technical report, by lisa brownsword, edwin j. morris, cecilia albert, deborah pruitt (mitre), david bentley (u.s. air force), thomas bono (mitre).
This document is the first release of an overview of the EPIC framework along with its activities and artifacts.
Distributed Software: From Component Model to Software Architecture
June 1, 2002 • white paper.
This 2002 whitepaper presents a component model for redeveloping software.
A Software Product Line Vision for Defense Acquisition
June 1, 2002 • technical note.
This report presents a vision for software product lines as an acquisition focus and suggests extensions to current Department of Defense policy and practices to increase the awareness of and …
Use of the Architecture Tradeoff Analysis Method (ATAM) in Source Selection of Software-Intensive Systems
By matt fisher, john k. bergey, lawrence g. jones.
This report explains the role of software architecture evaluation in a source selection and describes the contractual elements that are needed to support its use.
Use of Quality Attribute Workshops (QAWs) in Source Selection for a DoD System Acquisition: A Case Study
By john k. bergey, william wood.
This case study outlines how a DoD organization used architecture analysis and evaluation in a major system acquisition to reduce program risk.
Documenting Software Architecture: Documenting Interfaces
By reed little, james ivers, paul c. clements, felix bachmann, robert nord, judith a. stafford, david garlan, len bass.
This report provides guidance for documenting the interfaces to software elements.
Flow-Service-Quality (FSQ) Engineering: Foundations for Network System Analysis and Development
By mark pleszkoch, gwendolyn h. walton, alan r. hevner (university of south florida), richard c. linger (oak ridge national laboratory).
In this 2002 report, the authors describe Flow-Service-Quality engineering, an emerging technology for management, acquisition, and more.
Guidelines for Developing a Product Line Production Plan
June 1, 2002 • technical report, by john mcgregor, gary chastek.
This 2002 technical report provides guidance for creating, using, and evaluating a production plan, which is a description of how core assets are to be used to develop a product …
Quality Attribute Workshops, 2nd Edition
By judith a. stafford, anthony j. lattanze, mario r. barbacci, william wood, robert j. ellison, charles weinstock.
This report clarifies the context in which a QAW (Quality Attribute Workshop) is applicable, provides a rationale for developing the process and describes it in detail, and concludes with a …
Using EVMS with COTS-Based Systems
By carol sledge, mary jo staley, tricia oberndorf.
This 2002 report focuses is on the use of Earned Value in the context of a COTS-Based System (CBS).
Packaging and Deploying Predictable Assembly
May 31, 2002 • white paper, by scott hissam, gabriel moreno, kurt c. wallnau, judith a. stafford.
This paper describes prediction-enabled component technology (PECT), which integrates component technology with analysis models.
Foundations for Survivable Systems Engineering
May 20, 2002 • white paper, by andrew p. moore, nancy r. mead, robert j. ellison, richard c. linger (oak ridge national laboratory).
In this paper, the authors describe their efforts to perform risk assessment and analyze and design robust survivable systems.
Issues in Predicting the Reliability of Components
May 1, 2002 • white paper, by john mcgregor, judith a. stafford.
This whitepaper presents the design of an experiment that forms the basis of a reliability prediction-enabled component technology (PECT). It also discusses aspects of models that need to be adapted …
Statistical Models for Empirical Component Properties and Assembly-Level Property Predictions: Toward Standard Labeling
April 30, 2002 • white paper, by kurt c. wallnau, gabriel moreno, scott hissam.
This paper identifies statistical models that could form a basis for standard industry labels for component properties and prediction theories.
Is Third Party Certification Necessary?
April 1, 2002 • white paper, by kurt c. wallnau, judith a. stafford.
This paper describes a model for the component marketplace, along with two possible forms that the model may take in order to establish trust among participants in component-based design.
The Potential for Synergy Between Certification and Insurance
By mary shaw, p. luo li, kevin stolarick, kurt c. wallnau.
Because of their affordability and availability, reusable software components have long been a tantalizing IT investment, but they are not without their risks. Certification and insurance are potential approaches to …
Interpreting Capability Maturity Model Integration (CMMI) for Operational Organizations
April 1, 2002 • technical note, by brian p. gallagher.
This 2002 report details how operational organizations that perform a variety of missions can benefit from the concepts in CMMI to improve the processes and effectiveness of mission operations.
MAP and OAR Methods: Techniques for Developing Core Assets for Software Product Lines from Existing Assets
By dennis b. smith, liam o'brien.
This 2002 report describes the MAP and OAR methods, the activities that each involves, and examples of applying them.
SCAMPI V1.1 Use in Supplier Selection and Contract Process Monitoring
By rick barbour, thomas bernard.
A newer document covers this topic in more detail. If you want to see the newer document, see Standard CMMI Appraisal Method for Process Improvement (SCAMPI) A, Version 1.3: Method …
Experiences in Architecture Reconstruction at Nokia
March 1, 2002 • technical note, by liam o'brien.
This 2002 report outlines details of past and current architecture reconstruction work on several systems at Nokia.
Software Acquisition Capability Maturity Model (SA-CMM) Version 1.03
March 1, 2002 • technical report, by jack cooper, matt fisher.
This 2002 version of the SA-CMM incorporates change requests that have been received, as well as the results of lessons learned from conducting appraisals and from the use of Version …
CMMI for Systems Engineering/Software Engineering/Integrated Product and Process Development/Supplier Sourcing, Version 1.1, Continuous Representation (CMMI-SE/SW/IPPD/SS, V1.1, Continuous)
Cmmi for systems engineering/software engineering/integrated product and process development/supplier sourcing, version 1.1, staged representation (cmmi-se/sw/ippd/ss, v1.1, staged), the road to cmmi: results of the first technology transition workshop, february 1, 2002 • technical report, by caroline graettinger, lynn carter, shelly zasadni, gian wemyss, mac patrick.
This 2002 paper reports the findings of the First Technology Transition Workshop, held in November 2001.
2002 Tech Tip: A Brief Tour of the Simple Network Management Protocol
January 1, 2002 • white paper.
In this 2002 tech tip, the authors provide a brief overview of the Simple Network Management Protocol (SNMP).
2002 Tech Tip: Email Bombing and Spamming
This CERT Division tech tip describes email bombing and spamming.
2002 Tech Tip: Spoofed/Forged Email
This tech tip contains information about spoofed and forged email.
2002 Tech Tip: Securing Your Web Browser
Writing a Technical Paper By Bronwyn Brench, N.C.E.
Introduction Whether experienced at writing papers or just beginning, it is always useful to have your memory refreshed on what constitutes a successful technical paper. Clearly, a successful paper is one that is accepted into a technical publication and then is read and referenced by others. To achieve this end, it must first be determined that a particular body of work is unique and valuable to others. Second, the paper must be well written and follow the style guide of the chosen publication. This article covers the basics of paper acceptance, and reviews many of the writing pitfalls made by both veteran and beginner authors alike.
I. Paper Acceptance It is vital to know the criteria for the type of publication, and to understand the audience for which the paper is intended. Two typical venues for technical papers in the EMC field are the IEEE EMC Transactions and the IEEE EMC Symposium. A third option is the Practical Papers section in the IEEE EMC Society Newsletter. Here, papers are generally shorter and cover topics of wider interest to readers. The focus of this article is on papers submitted to the IEEE Transactions on EMC and the IEEE International Symposium on EMC Proceedings publications.
IEEE EMC Transactions The IEEE Transactions on EMC has very clear instructions, located on the inside back cover of the journal, on the requirements for a paper submitted for publication. Basically, work of archival (long lasting) value is sought, including advances in the state of the art, both theoretical and experimental. There are two paper length options; a full length, eight page Paper, and a Short Paper. Full length papers are peer reviewed in detail and edited, and multiple review periods are possible. Short Papers are generally four pages in length and typically narrower in scope. These are either accepted as submitted without any substantial changes, or rejected.
IEEE EMC Symposium Paper submittals to the annual IEEE International Symposium on EMC may be directed toward the Regular or Special Sessions, and all papers have the same requirements: they must be significant to EMC, have technical depth, be readable in clear English, and contain new, unpublished work. These papers are peer reviewed, although not as heavily as for the IEEE Transactions on EMC papers. Manuscripts will be either: accepted, accepted with required changes (requiring a second peer review), accepted with suggested changes, or rejected. If the paper is directed toward one of the Special Sessions at the Symposium, do not make the mistake of thinking it will be automatically accepted because it was “invited”. These sessions are typically organized by an individual or EMC Society Technical Committee (TC) on a topic that is of particular interest. Therefore, think of it as an invitation to submit a paper on a special topic; a topic that will not necessarily be repeated the following year. All Special Sessions papers are peer reviewed, and are held to the same required high standards as Regular Session papers. Regular Session papers may be presented orally or in a Poster Session (Open Forum). Both types receive equal peer reviews; it is merely the presentation that differs. One common misconception is that papers in the Poster Session are of lesser value or have more relaxed standards. This is far from the truth as it is always a goal of the Symposium review committee to ensure that a good variety of topics are presented in the Poster Sessions. The major benefit of a Poster Session to the author is the ability to directly interact with interested attendees, which can be a great source of information to those doing similar work.
II. Key Parts of a Technical Paper
The Writing Overview Once the requirements for the paper have been reviewed and the work has been completed and researched for technical value, the writing may begin. Writing a technical paper, especially for an international audience, can be a daunting task. Not only can the English language be a problem, but many scientists and engineers never learned how to write a formal technical paper. There are a few good instruction guides on line, [1] and [2], if a tutorial is needed; however, the highlights of technical paper writing and a few notes on many of the common errors are given in this article. A technical paper is not an English paper. It is also not a science lab report. The layout of a formal technical paper typically consists of the following key elements: Abstract, Introduction, Work Done, Results & Discussion, Conclusion, and References. The Abstract and Introduction are standard with their titles and content. The meat of the paper is contained in the middle sections, Work Done, Results, and Discussion, and the labeling or titles for these sections vary depending on the topic. The final two sections, Conclusion and References, are also relatively standard with their titling and content. Sometimes an Acknowledgements section is inserted between the Conclusions and References. Working drafts often begin with the Work Done, Results, and Discussion sections. The Introduction and Conclusion sections can be started a bit later, to aid in binding the flow of the paper together. Make certain that any goals and objectives stated in the Introduction are addressed in the Conclusions. Oddly enough, the Abstract should be written last. It is only after the introduction and conclusions have been written that there will be clarity in how to phrase this special, brief summary of the paper.
Abstract The Abstract is the most important part of a technical paper, and perhaps one of the most misunderstood parts. Everyone reads them, and they are essentially the “selling point” for the paper. Even experienced authors lose sight of the purpose of an abstract and how it should be written. The key thing to remember about an abstract is that it should be a stand-alone mini-summary of the paper. Abstracts are typically extracted from each paper and published separately in an abstract listing, for readers to browse when deciding which papers they want to read in full or attend for the actual presentation of the paper. For this reason, it is especially important to spend detailed writing time on the abstract to get it precise. The Abstract should be clear and concise, a single paragraph, typically 200 words maximum. It should include the purpose, a brief description of the work, and the pertinent results or conclusions. The English should be impeccable, especially if an international audience is expected. A special effort had to be made at the 2007 IEEE International Symposium on EMC, for example, where the EMC Society celebrated its 50 year anniversary, to grammatically edit a large majority of the extracted abstracts so that they could be clearly understood by the wide set of international attendees. The most common mistake made is to treat the abstract as a brief introduction to the paper. The author mistakenly believes that this is where the reader’s attention must be caught with eye grabbing phrases, and then leaves them with a cliff hanger to hope they will read on. The reality is that the abstract loses its conciseness and the crucial results/conclusions synopsis is left out. Other points to note include:
- Using too many words can cause readers to skim and possibly miss important points.
- Leaving out the summary results or conclusions can cause readers to lose interest.
- Using acronyms should only be done if used again within the abstract.
- Making a reference with a footnote is never allowed.
- Making a reference with a citation at the end of the paper is never allowed.
- Make certain the English is perfect.
- Avoid background information; that is for the Introduction.
If these guidelines are followed, then your abstract will become a perfect selling point for your paper.
Introduction The Introduction is the true start of the paper. Do not make the mistake of thinking that the Abstract is a sort of first paragraph; it is totally separate. The Introduction does just that – it introduces the reader to the work. A typical Introduction includes four paragraphs. The first paragraph is the place for those wordy, eye catching phrases giving the reasons for and importance of the work, and why someone would want to read the paper. The second and third paragraphs contain a brief description of the background to the problem and the connection of the present work to the background. The final paragraph includes a clear statement of the purpose or goal of the work; it is an expansion from the Abstract. This will lead the readers smoothly into the start of the actual work of paper. One error that is frequently found in paper submittals is that little, if any, research was done by the authors to determine that the work is indeed new and original. No matter how well written the paper is, it will be rejected if it is not original. Researching the subject matter is a good fundamental engineering practice. Why would you want to spend time doing the work and writing it up if the answer is already known? This vital step can save a great deal of wasted effort.
The Main Body This is the main part, or “meat” of the paper, and includes the work done, results, analysis, and discussion sections. The exact layout and section titles will vary depending on the topic. A description of the work and methods used, i.e. how the work was performed, should be given in the first section. A mistake sometimes made is to list the equipment used, as if it were a lab report. If a description of any of the equipment used is necessary in understanding the work, then it is acceptable to describe that key equipment. Next, the results should be given and analyzed. The results section is sometimes separated from the discussion section, but usually they are combined. Tables, graphs, and diagrams should be used to help visualize and explain the results and analysis. Each table and figure needs a written explanation; do not assume the reader can understand it on their own. What may be obvious to the authors may not always be obvious to others. Frequent problems are found with tables and figures when they are shrunk down to fit in a two column format. Please, use the sizes and formatting as defined in [3] or [4]. Using anything different makes the paper harder to read and follow, and causes it to look unprofessional. If the details of the figure cannot be seen when shrunk down, then consider breaking it into multiple figures. Pay attention to any labels or wording in figures that get reduced; these must be 8 to 12 point type after reduction. Also, it is important to make sure the curves in multiple curve plots are distinguishable. Even though the use of color is now acceptable, solid fill colors are preferred as they contrast well both on screen and on a black-and-white hardcopy. Discussing the results is also important, but leave the conclusions for the Conclusion section. The objective here is to provide an interpretation of your results and a description of any significant findings. This will logically lead readers into the Conclusion section.
This is a place many authors get stuck. They have written up their work and described, analyzed, and discussed their results. What more can be said without repeating everything in the summing up? This is the time for the author to sit back and think about how their work relates to the big picture. The author should review their original stated purpose, the results, and discussions. Perhaps there is more that can be done to further the work. With these thoughts fresh on the mind, the conclusion can then be written such that it is not simply a “we did this, this, and that”, but rather a concise summing up, or review, followed by a brief discussion on how your findings relate to the big picture. A discussion of any recommendations for further work is also a fine addition, if relevant.
Acknowledgements & References Sometimes an Acknowledgement section is inserted just before the Reference section. This is especially important if funding has been received from a special source for the work and research that was performed. Co-workers who assisted in the work but were not involved in the final writing may also be listed here. There are many categories of references or works cited, so use the style guide in [3] or [4] for details on how to list each type. It is essential to supply a comprehensive and relevant set of references. This is necessary because it gives credit to those who have done similar work and it indicates to the reviewers that you have done your homework. Papers that only reference the author’s previous work or a few recent papers attract the reviewer’s attention as being incomplete. A word about authors and co-authors: the IEEE has a policy [5] concerning who should be included as co-authors on a paper; an extraction of this policy is quoted below: “The IEEE affirms that authorship credit must be reserved for individuals who have met each of the following conditions:
- Made a significant intellectual contribution to the theoretical development, system or experimental design, prototype development, and/or the analysis and interpretation of data associated with the work contained in the manuscript,
- Contributed to drafting the article or reviewing and/or revising it for intellectual content, and
- Approved the final version of the manuscript, including references.”
Anyone not meeting each of the three conditions should therefore be included in the Acknowledgement section.
III. And Finally … Proofread! Once the final draft of the paper is finished, do not forget to leave time for the review, both technical and grammatical. Incomplete sentences, redundant phrases, misspellings, and grammatical errors are unprofessional. Waiting a day or two before reviewing helps to provide a fresh approach, and more mistakes can be found. Another good way to catch errors is to give the paper to somebody else to read. The more people who review it, the more comments will be received, creating opportunities to improve the paper. If English is not your native language, it would help if one of the reviewers is a native English speaker, or have a trained technical editor proofread your paper. It may be that your heavily accented English is passable to a native English speaker, but can other non-native English speakers also understand? I heard a story about how one native English speaker had to act as an interpreter between two others speaking their own accented versions of the English language! It will increase your chances for success if the grammar is correct. Writing an effective paper is time consuming, but is worth the effort when it is finally published and others can read and reference your work in their own research. Know and follow the criteria for the particular publication to which you are submitting, and make sure that all the components of a good technical paper are included in the next one you write.
IV. Acknowledgement I would like to thank Colin Brench, who has reviewed technical papers for many years for the IEEE International Symposium on EMC, for his input on what reviewers look for in Symposium and Transactions papers.
References [1] D. R. Caprette (updated Aug. 2010) Rice University class notes on Writing Research Papers. Available: https://www.ruf.rice.edu/~bioslabs/tools/report/reportform.html [2] H. Schulzrinne (updated Oct. 2009) Columbia University class notes on Writing Technical Articles. Available: https://www1.cs.columbia.edu/~hgs/etc/writing-style.html [3] IEEE sample paper template for IEEE Transactions, Preparation of Papers for IEEE TRANSACTIONS and JOURNALS (May 2007). Available: https://www.ieee.org/publications_standards/publications/authors/authors_journals.html#sect2 Click on: Updated-Template and Instructions on How to Create Your Paper (DOC, 92KB) [4] IEEE sample paper templates for IEEE conference proceedings, Sample IEEE Paper for US Letter Page Size , Version 3, original version of this template was provided by courtesy of Causal Productions ( www.causalproductions.com ). Available: https://www.emcs.org/technical-committees.html [5] IEEE Publication Services and Products Board Operations Manual, Piscataway, NJ: IEEE Publications, amended Feb. 2010, Section 8.2.1.A. Available: https://www.ieee.org/portal/cms_docs_iportals/iportals/publications/PSPB/opsmanual.pdf

Libraries | Research Guides
Technical reports, technical reports: a definition, search engines & databases, multi-disciplinary technical report repositories, topical technical report repositories.
"A technical report is a document that describes the process, progress, or results of technical or scientific research or the state of a technical or scientific research problem. It might also include recommendations and conclusions of the research." https://en.wikipedia.org/wiki/Technical_report
Technical reports are produced by corporations, academic institutions, and government agencies at all levels of government, e.g. state, federal, and international. Technical reports are not included in formal publication and distribution channels and therefore fall into the category of grey literature .
- Science.gov Searches over 60 databases and over 2,200 scientific websites hosted by U.S. federal government agencies. Not limited to tech reports.
- WorldWideScience.org A global science gateway comprised of national and international scientific databases and portals, providing real-time searching and translation of globally-dispersed multilingual scientific literature.
- Open Grey System for Information on Grey Literature in Europe, is your open access to 700.000 bibliographical references. more... less... OpenGrey covers Science, Technology, Biomedical Science, Economics, Social Science and Humanities.
- National Technical Reports Library (NTRL) This link opens in a new window The National Technical Reports Library provides indexing and access to a collection of more than two million historical and current government technical reports of U.S. government-sponsored research. Full-text available for 700,000 of the 2.2 million items described. Dates covered include 1900-present.
- Argonne National Lab: Scientific Publications While sponsored by the US Dept of Energy, research at Argonne National Laboratory is wide ranging (see Research Index )
- Defense Technical Information Center (DTIC) The Defense Technical Information Center (DTIC®) has served the information needs of the Defense community for more than 65 years. It provides technical research, development, testing & evaluation information; including but not limited to: journal articles, conference proceedings, test results, theses and dissertations, studies & analyses, and technical reports & memos.
- HathiTrust This repository of books digitized by member libraries includes a large number of technical reports. Search by keywords, specific report title, or identifiers.
- Lawrence Berkeley National Lab (LBNL) LBNL a multiprogram science lab in the national laboratory system supported by the U.S. Department of Energy through its Office of Science. It is managed by the University of California and is charged with conducting unclassified research across a wide range of scientific disciplines.
- National Institute of Standards and Technology (NIST) NIST is one of the nation's oldest physical science laboratories.
- RAND Corporation RAND's research and analysis address issues that impact people around the world including security, health, education, sustainability, growth, and development. Much of this research is carried out on behalf of public and private grantors and clients.
- TRAIL Technical Report Archive & Image Library Identifies, acquires, catalogs, digitizes and provides unrestricted access to U.S. government agency technical reports. TRAIL is a membership organization . more... less... Majority of content is pre-1976, but some reports after that date are included.
Aerospace / Aviation
- Contrails 20th century aerospace research, hosted at the Illinois Institute of Technology
- Jet Propulsion Laboratory Technical Reports Server repository for digital copies of technical publications authored by JPL employees. It includes preprints, meeting papers, conference presentations, some articles, and other publications cleared for external distribution from 1992 to the present.
- NTRS - NASA Technical Reports Server The NASA STI Repository (also known as the NASA Technical Reports Server (NTRS)) provides access to NASA metadata records, full-text online documents, images, and videos. The types of information included are conference papers, journal articles, meeting papers, patents, research reports, images, movies, and technical videos – scientific and technical information (STI) created or funded by NASA. Includes NTIS reports.
Computing Research
- Computing Research Repository
- IBM Technical Paper Archive
- Microsoft Research
- INIS International Nuclear Information System One of the world's largest collections of published information on the peaceful uses of nuclear science and technology.
- Oak Ridge National Laboratory Research Library Primary subject areas covered include chemistry, physics, materials science, biological and environmental sciences, computer science, mathematics, engineering, nuclear technology, and homeland security.
- OSTI.gov The primary search tool for DOE science, technology, and engineering research and development results more... less... over 70 years of research results from DOE and its predecessor agencies. Research results include journal articles/accepted manuscripts and related metadata; technical reports; scientific research datasets and collections; scientific software; patents; conference and workshop papers; books and theses; and multimedia
- OSTI Open Net Provides access to over 495,000 bibliographic references and 147,000 recently declassified documents, including information declassified in response to Freedom of Information Act requests. In addition to these documents, OpenNet references older document collections from several DOE sources.
Environment
- National Service Center for Environmental Publications From the Environmental Protection Agency
- US Army Corp of Engineers (USACE) Digital Library See in particular the option to search technical reports by the Waterways Experiment Station, Engineering Research and Development Center, and districts .
- National Clearinghouse for Science, Technology and the Law (NCSTL) Forensic research at the intersection of science, technology and law.
Transportation
- ROSA-P National Transportation Library Full-text digital publications, datasets, and other resources. Legacy print materials that have been digitized are collected if they have historic, technical, or national significance.
- Last Updated: Jul 13, 2022 11:46 AM
- URL: https://libguides.northwestern.edu/techreports
Purdue Online Writing Lab Purdue OWL® College of Liberal Arts
Reports, Proposals, and Technical Papers

Welcome to the Purdue OWL
This page is brought to you by the OWL at Purdue University. When printing this page, you must include the entire legal notice.
Copyright ©1995-2018 by The Writing Lab & The OWL at Purdue and Purdue University. All rights reserved. This material may not be published, reproduced, broadcast, rewritten, or redistributed without permission. Use of this site constitutes acceptance of our terms and conditions of fair use.
Technology Research Paper

This sample technology research paper features: 8300 words (approx. 27 pages), an outline, and a bibliography with 48 sources. Browse other research paper examples for more inspiration. If you need a thorough research paper written according to all the academic standards, you can always turn to our experienced writers for help. This is how your paper can get an A! Feel free to contact our writing service for professional assistance. We offer high-quality assignments for reasonable rates.
Introduction
Man’s relation to technology: a brief history, technology and biological anthropology, the sts approach, classical philosophical anthropology, philosophy of technology, the continental approach to the philosophy of technology, the analytic approach to the philosophy of technology, recent developments: bridging the gap, conclusion and future directions.
- Bibliography
More Technology Research Papers:
- History of Technology Research Paper
- Internet Research Paper
- Nanotechnology Research Paper
- Compstat Research Paper
- Computer Forensics Research Paper
- Healthcare Technology Assessment Research Paper
- Ethics of Information Technology Research Paper
- Neurotechnology Research Paper
The term technology is derived from the Greek word techné. The Greek word refers to all forms of skillful, rule-based mastery in any field of human praxis, originally encompassing both arts (like painting, sculpture, writing, and the like) and craftsmanship (like carpentry, shipbuilding, architecture, and the like). The Roman culture uses the Latin word arts for these domains. Accordingly the medieval terminology distinguishes between the seven free arts (grammar, rhetoric, logic, geometry, arithmetic, music, astronomy) and the mechanical arts (e.g., agriculture, architecture, tailoring), thus prefiguring the later distinction between arts (as linked to the study of humans and the humanities) and technology (as linked to engineering and the study and science of nature).
Academic Writing, Editing, Proofreading, And Problem Solving Services
Get 10% off with 24start discount code.
The modern word technology finally refers either to procedures and skillful application of sciences for the production of industrial or manual products or to the products of these processes themselves. In this sense, technology nowadays encompasses only a part of the original Greek definition. The place of technology as being on the one hand a product of humans (being thus rooted in human anthropology and human tool usage), and being on the other hand based on a solid scientific understanding of the laws of nature (modern technology), can be seen as the two key features of contemporary and recent approaches to analyze and understand technology. Technology is then in one respect as old as humankind: Many approaches in anthropology thus refer to the general structure of technology in all of human history and relate it to the biological condition of humans. But recent anthropological thinking also reflects on the specific details of modern technology. It has often been argued that there is a structural difference between modern, science-based technology and older forms of craftsmanship of ancient or medieval types of technology. Therefore, a central question for modern anthropology is to analyze the consequences modern technology has for our picture of humankind: how to define man in the age of technology.
Reflection about the anthropological function of technology is probably as old as human self-reflection itself, since the ability to use tools and create cultural products has always been seen as a unique human feature, distinguishing humankind from most other animals (see also the next section on biological anthropology). But an analysis of technology was not at the center of political, social, anthropological, or philosophical thoughts before the development of the modern natural sciences and their counterpart, modern technology. Following Carl Mitcham (1994) one can roughly distinguish three approaches to technology before the 20th century, encompassing many topics that later became essential parts of contemporary discussions about technology (p. 275). The three approaches are as follows:
- In the ancient world, technology is looked at with certain skepticism. The use of tools is seen as necessary for survival, but also regarded as dangerous, since it might lead to human hubris and might raise the envy and anger of the gods. In this sense, mythological thinking envisions technology as, for example, stolen from the gods (the myth of Prometheus), and thus not properly belonging to humans. The extensive use of technology is often seen as leading to megalomaniac fantasies or unjustified overstepping of religious and ethical boundaries (e.g., myth of the Tower of Babel, myth of Icarus). Philosophical reflection, however, acknowledges the value of technology for an otherwise defenseless human being. Already Plato anticipates a central thought of modern anthropology: Human beings are poorly equipped for survival in nature. They need to compensate for this lack by developing skills of rational thinking and the usage of tools (this idea later becomes a central thesis of the famous anthropology of Arnold Gehlen [1988]). But the emphasis in ancient philosophical anthropology lies not so much on man’s capacities to invent technology, but on man’s moral character (exemplified by ancient wisdom or medieval religiosity). The usage of technical knowledge should thus be kept within strict ethical boundaries.
- In the hierarchy of knowledge, ethical wisdom is regarded in principle as higher than and superior to technological skills. Socrates points to the question that we should not only seek knowledge about how to do certain things (technical knowledge), but rather about whether we should perform certain actions (ethical knowledge); this idea can also be found in the medieval distinction between the (superior form of a) life in contemplation ( vita contemplativa ) and the (lower) life in active involvement ( vita activa ). Ancient and medieval technology is thus embedded in an anthropological vision, in which human virtues play an important role. Different forms of virtues are combined in the original crafts, as opposed to the later, modern differentiation of these virtues: In craftmanship one can find a union of economical virtues (e.g., efficient usage of limited resources), technical virtues (creating new entities that did not exist before), and often also aesthetic virtues (a sense of beauty that adds an aesthetic component to these newly created entities going beyond the modern idea that “form follows function”). In the Greek world, these three skills are combined in the realm of poiesis, while in modernity they are separated in the three domains of economy, technology, and art—each relatively independent of the others (Hösle, 2004, p. 366).
- A profound change in the evaluation of technology emerges with modernity, a position that Mitcham (1994) summarizes as Enlightenment optimism. Already in the writings of Francis Bacon (1620), the new science of nature and its application to experimental and technological research is highly welcomed. Progress in technology is seen as very beneficial to humankind, as it may lead to the cure of diseases, mastery over nature, and a constant progress toward a more human society. Many utopian writings mark the beginning of early modern thoughts in which technology is seen as essential in leading to a brighter future for humankind (e.g., Thomas More’s Utopia [1516], J. V. Andreae’s Christianopolis [1619], F. Bacon’s New Atlantis [1627]). In a similar line of thought, Enlightenment thinkers defend science and modern technology against attacks from religious conservatism, pointing at the beneficial consequences of technological and scientific progress.
- A countermovement to the Enlightenment is Romanticism, which accordingly has a different view on technology, referred to by Mitcham (1994) as Romantic uneasiness. Again, the central thought is an anthropological perspective in which man is seen as being good by nature, while it is civilization that poses the danger of alienating man from nature and from his fellow man, focusing only on his rational capacities and suppressing his emotional and social skills. Already Vico (1709) opposed Cartesian rationalism and feared that the new interest in science would lead to a neglect of traditional humanistic education. Rousseau’s critique of modern societies then became influential, seeing an advancement of knowledge and science, but a decay of virtues and immediacy ( Discourse on the Arts and Sciences; Rousseau, 1750). With the age of industrialism, the negative social consequences of modern labor work become the scope of interest of social theorists, leading up to Marx’s famous analysis of modern societies (see subsequent section on cultural and sociological anthropology). In opposition to the positive utopias centered on technology in early modernity, the 20th century then sees the literary success of pessimistic dystopias, in which often technological means of suppression or control play an important role (e.g., already in M. W. Schelley’s Frankenstein or the Modern Prometheus [1818] and later in H. G. Wells’s The Island of Doctor Moreau [1896], A. Huxley’s Brave New World [1932], George Orwell’s 1984 [1948], and Ray Bradbury’s Fahrenheit 451 [1953]).
The tension between approaches praising the benefits of technology (in the spirit of the Enlightenment) and approaches focusing on negative consequences (in the spirit of Romanticism) still forms the background of most of the contemporary philosophical and anthropological debate; this debate circles around an understanding of modern technology, often rooted in the different “cultures” of the humanities and the sciences. It can be regarded as being a particularly vivid opposition at the beginning of the 20th century, that only later gave room for more detailed and balanced accounts of technology (some classics of the debate being Snow, 1959; McDermott, 1969).
Recent contributions toward a deeper understanding of the usage and development of technology stem from such different disciplines as biology, sociology, philosophical anthropology, metaphysics, ethics, theory of science, and religious worldviews. This research paper aims at a brief overview of important topics in the debate over technology during the 20th century to the present time. Three anthropological perspectives will be distinguished, depending on the main focus of anthropological interest. This will start with a brief summary of the biological anthropological perspective on technology, move on to those theories which focus more on social or cultural aspects, and conclude with more general philosophical anthropologies. This research paper is thus not chronologically organized, but tries to identify common themes of the debate, even though sometimes the topics might overlap (e.g., the case of Gehlen, a philosophical anthropologist who starts from a biological perspective and then moves on toward a more social view on technology).
In contemporary anthropology, technology becomes a central issue for at least two different reasons:
- From a biological perspective the usage of tools is regarded (next to the development of language and a cognitive rational apparatus) as one of the key features of humanization. Biological anthropology thus initially focuses on the differences and similarities of tool usage in humans and animals, trying to understand the role technology plays in general for an understanding of humans’ biological and social nature. With the focus on human evolution, attention is often drawn to the question of which role technology played at the beginning of humankind.
- While in this way always being a part of human culture, technology becomes arguably one of the single most influential key features of society only in modernity. According to Max Weber, science, technology, and economy form the “superstructure” of modernity, while they all share a common “rationality” (mainly of means-ends reasoning in economy and technology). The experience of the powers and dangers of modern technology (as in industrialized labor work, medical progress, nuclear energy and weapon technology, environmental problems due to pollution, and extensive usage of resources, etc.) has triggered many social, political, and philosophical reflections that—in opposition to biological anthropology—aim primarily at understanding the specifics of modern
Let us look at these two tendencies in turn, starting with the biological perspective, before moving to the social or cultural anthropology of technology.
Biological anthropologists are interested in the role technology played during humanization, and they attempt to give evolutionary accounts of the development of tool usage and technology and compare tool usage in man with tool usage in other animals. The development of technology has often been regarded as an evolutionarily necessary form of adaption or compensation. Since most of man’s organs are less developed than those of other species, he needed to compensate for this disadvantage in the evolutionary struggle for life (see Gehlen, 1980). Initially the usage of tools was considered a unique human feature, distinguishing the genus Homo from other animals (Oakley, 1957), but research on tool usage in different animals, especially chimpanzees, led to a more or less complete revision of this thesis (Schaik, Deaner, & Merrill, 1999).
Nowadays, many examples of tool usage in the animal kingdom are known (Beck, 1980). For example, chimpanzees use sticks to fish for termites, and elephants have been described as having a remarkable capacity for tool usage. Even though tool usage must thus be regarded as more common among animals, attention still needs to be drawn to the specifics of man’s tool usage, which arguably in scope and quality goes beyond what is known from the animal kingdom. It has been pointed out that our biological anatomy offers us several advantages for an extended usage of tools: walking erectly frees the two hands, which can then be used for other purposes. Furthermore, the position of the human thumb and short straight finger are of great benefit, especially in making and using stone tools (Ambrose, 2001). Still debated, however, is whether social and technological developments go hand in hand or whether one of the two factors is prior.
Even though many anthropologists tended to see social behaviors and cultural revolutions mostly as a consequence of a change in tool usage or a development of new technologies, it has also occasionally been argued that the development of social skills precedes the development of technical skills (e.g., in joint group hunting). It has additionally been acknowledged that chimpanzees also pass over some of their technical knowledge through the mechanism of learning and establishing cultural “traditions” that resemble, to some extent, human traditions (Wrangham, 1994; Laland, 2009). But there seems to be a specific difference in human and primate learning, namely in the fact that human children learn tool usage mainly via imitation and by simply copying a shown behavior, even if it is not the most efficient solution to a given problem. Opposed to this, chimpanzees seem to learn through a process called emulation, which implies that they diverge from the paradigmatic solution that has been “taught” to them. It has been argued that learning through imitation has been selected in humans, even though it is a less flexible strategy, because it is a more social strategy of learning (Tomasello, 1999, p. 28). In this way, biological anthropology mirrors a debate in social anthropology about the role of technology; this can be seen either as a driving force born out of necessity that calls for social changes (technical determinism), or as highly mediated or even constructed by culture (social constructivism).
Technology and Social/Cultural Anthropology
As already mentioned, technology was identified early on as a key feature of modern society (Misa, Brey, & Feenberg, 2004). Many studies have been written about the impact of modern technology on society, focusing mainly on the industrial revolution (e.g., Haferkamp, 1992; Pressnell, 1960; Smelser, 1969) or on the more recent revolution of the information society (e.g., Castells, 1999; Nora, 1980), as well as on the impact of technological change on traditional societies.
The analyses of Karl Marx and the Frankfurt School are influential, not only in trying to grasp the role of modern technology in society, but also in hinting on potential anthropological roots of technology and their essential interrelation with social aspects of the human condition. Marx insisted that the study of technology holds the highest relevance for human sciences, since it reveals the way humans deal with nature and sustain life (Marx, 1938). An essential feature of man’s nature is that he has to work in order to sustain his life, that he is the “toolmaking animal” or—as he has later been called—the Homo faber. Marx analyzes the role of technology in Chapter 13 of his first volume of Das Kapital. He argues that the division of labor becomes fostered through machines, which at the same time replace more and more traditional manpower and can furthermore be operated by less skilled employees, thus leading to very bad labor conditions for the working class. Technology in general is, however, still greeted as an option to make humans’ lives easier; it is mainly the social distribution of the possession of the means of production that Marx regards as problematic. (Also later thinkers, inspired by Marxian thought, tend to see technology as an important means toward establishing a better future.) On the other hand, at the same time, technology is seen as rooted in man’s will to dominate nature.
Following this later insight in particular, Theodor Adorno argues that Western civilization has developed powerful tools to ensure its self-preservation against nature. Technical rationality is regarded as the exercise of strategic power to dominate (external) nature, but it is at the same time also leading to a suppression of the inner nature of man (Adorno, 1979). The main strategy of this rationality is quantification, which lies at the heart of the mathematical-scientific interpretation of nature and the development of modern technology. At the same time it brings forth a type of rationality, which leads to a selfmutilation. The will to exercise power becomes the main feature of modern rationality, thus leading to a dialectic that turns the noble aims of the Age of Enlightenment into a morality of humankind that is its very opposite: A new barbaric system of oppression and dictatorship arises, using technology for totalitarian purposes.
While Adorno seeks redemption mainly in the arts (Adorno, 1999), seeming to promise the possibility of a completely different kind of subjectivity, Jürgen Habermas (1971) tries to propose an antidote; this does not lie outside of modern-Enlightenment rationality, but rather returns to its original intention. Habermas argues with Marx and Adorno, asserting that technological knowledge has its anthropological roots in the will to dominate nature and therefore serves a strategic interest of man. With this, man is not only Homo faber but also a social animal. Besides the strategic means-end rationality he also possesses a communicative rationality, aimed at defining common moral values and engaging in discourse over ethically acceptable principles of actions. In thus distinguishing two types of rationality, Habermas tries to incorporate much of the German tradition of cognitivistic ethics into his approach. It is important for Habermas that technology be brought under the control of democratic decision-making processes; his discourse ethics has thus helped to inspire ideas of participatory technology assessment.
Outside the Frankfurt School, technology has not been at the center of social and cultural anthropology, as has been often complained (Pfaffenberger, 1988, 1992). Langdon Winner (1986) coined the term technological somnambulism to refer to those theories that neglect the social dimension of technology. According to this dominant tradition, the human-technology relation is “too obvious” to merit serious reflection. Technology is seen as an independent factor of the material and social world, one that forms a relatively autonomous realm of ethically neutral tools to acquire human ends. But already Winner argues that technology is essentially social and is shaped by cultural conditions and underlying value decisions. He claims in a famous article (Winner, 1980) that Long Island’s low bridges were intentionally built in a way that would keep buses away, making it more difficult for the poor, and mainly the black population, to reach the island. Even though this particular claim has been challenged, Winner seems to be correct in pointing out that value decisions play a role in creating technology, and that the social value system leaves its trace in technological artifacts.
In line with this renewed interest in social issues, a new field of studies related to technology emerged in the 1980s, focusing explicitly on this neglected relation between society and technology: the so-called STS approach. Having been labeled the “turn to technology” (Woolgar, 1991), science and technology studies (STS) analyzes society’s impact on science and technology, and science and technology’s impact on society. Several writers draw attention to the social shaping of technology. An influential author is Bruno Latour, who contributed to both the initial appeal to social constructivism (that he later gave up) and the development of the actor-network theory; both are at the center of the debate about the theoretical underpinnings of STS.
Social Constructivism
Woolgar and Latour employ a social-constructivist perspective in their early case study on the production of scientific results, in which they analyze scientists’ attempt to establish and accumulate recognition and credibility of their research through the “cycle of credibility” (Latour, 1979). The main idea of social constructivism is the attempt to interpret alleged objective “facts” in the social world as being socially constructed, so that knowledge of the world and its interpretation depends on social mechanisms and cannot be traced back to objective facts (Berger & Luckmann, 1966). In this sense technology is also not an objective, independent given, but shaped by social ideas and societal interpretations.
Actor-Network Theory
In the 1980s and 1990s, Latour became one of the main proponents of the actor-network theory (Latour, 2005); this is also attractive to scholars who reject social constructivism, since it can be combined with the idea that not all of technology is socially constructed. The social-constructive interpretation of this theory aims to develop a framework in which society and nature, or society and technology, are not separated. The idea of technology as a sociotechnical system implies that agent and tool form a unity, which cannot be explained completely by referring to one of the two elements in isolation. According to this idea, technological artifacts dispose over some form of agency and can be—to some extent—regarded as actants. This ascription of intentionality and agency to technical systems is, however, highly debated. The debate between realism and social constructivism has thus not been settled.
Philosophical Anthropology and the Philosophy of Technology
Research in philosophical anthropology peaked in early 20th-century Germany, discussed in the next section. But outside of anthropological discussions, the topic of technology became an important issue for philosophy, so in this brief overview, important contributions and themes of the continental and analytic tradition will be discussed next. Finally, more recent developments and topics in the philosophy of technology will be sketched that do not try to revitalize a philosophical anthropology, but that nevertheless do touch in one way or another on anthropological perspectives on technology.
Classical philosophical anthropology was mainly interested in understanding the essence of human nature and often draws specific attention to the role of technology. Important contributions came from Gehlen, Plessner, and Scheler during the first half of the 20th century. The attempt to link technology to a biological interpretation of man in Gehlen’s early works especially deserves attention. Given his biological constitution, man must be seen as deficient by nature ( Mängelwesen ), since he is not endowed with instinctive routines and is not adapted well to a specific natural environment, but rather is open to the world ( weltoffen ). He compensates for this deficiency with the help of his mental capacities and tool usage. Gehlen interprets human language and human institutions as relief mechanisms ( Entlastungen ) that help him to interpret and organize the plentitude of impressions (the sensory overload, Reizüberflutung ) that he is exposed to. Most technologies can thus be regarded to be either organ-amplification ( Organverstärkung ) or organ-replacement ( Organersatz ) (Gehlen, 1988). In Man in the Age of Technology (1980), Gehlen focuses more on sociological perspectives of technology. He identifies two essential cultural breaks marking principle changes in humans’ world interpretation and social organization, both of which are linked to technological developments: (1) the neolithic revolution of sedentism, marking the passage from a hunter’s culture to a society of agriculture and cattle breeding, and (2) the industrial revolution in modernity (Gehlen, 1980).
Scheler also analyzes man’s rational capacities from a biological perspective, but he concludes that a purely naturalistic approach does not render justice to our selfunderstanding. The human ways of sustaining life are from an often inefficient biological perspective. Therefore, it must be pointed out that the main function of human knowledge is not only to strategically ensure humans’ own survival, but also to be directed toward the discovery of moral values and toward the process of self-education ( Bildung ). Humans not only live in an environment, but also reflect on their place in the world—a capacity that marks a fundamental difference between humans and animals (Scheler, 1961).
This type of philosophical anthropology came to a certain end when the main interest of philosophers shifted from understanding “man” to understanding “society” during the 1960s. With the recent developments of sociobiology, philosophers have taken a renewed interest in the linkage between biological and cultural interpretations of man. Let us look at some tendencies of later research in the philosophy of technology.
If we look at a philosophical interpretation of technology, we find the first origins of a discipline of the philosophy of technology by the end of the 19th and the beginning of the 20th century (see Kapp, 1877, and Dessauer, 1933). During the first half of the 20th century, the philosophical analysis of technology can, roughly speaking, be divided into two main schools of thought: the continental, often skeptical approach, and the analytical, often optimistic approach . As with all such very generic typologies, this distinction likewise does not claim to be more than an approximation, while the general tendency of recent research seems precisely to be to overcome this gap and to aim for a convergence or crossfertilization of these two approaches. Therefore, what follows is an ideal-type distinction that tries to make some of the basic ideas of these two approaches more visible and aims at understanding their more general features.
The continental approach originally focused on a humanities-centered perspective on technology, its (mainly negative) consequences for society, and its rootedness in a problematic feature of human anthropology (the will to power), and finally tried to understand technology as such (its “essence”). The analytic approach, on the other hand, originally focused on a more science-based understanding of technology, its (mostly beneficial) potential for the progress of societies, and its rootedness in a rational (scientific) way to approach nature, and it finally tried to look not at technology as such but at specific problems or specific types of technologies.
In the continental philosophy of technology, technology is often interpreted as closely linked to a certain form of consciousness, a form of approaching nature (and also human interaction) from a perspective that is rooted in a scientific understanding of the world, which itself is rooted in the will to dominate nature. This approach is seen to replace or at least to endanger a value-based approach to reality. In this sense, Edmund Husserl’s phenomenology regards science and technology as a mere abstraction from the fullfledged real experience of the world we live in. In this way, the sphere of technical knowledge is limited and needs to be guided by value decisions, which do not have their basis in scientific or technical knowledge, but stem from our ethical knowledge of our life-world.
While technology is not at the center of Husserl’s interest, José Ortega y Gasset (1914/1961) was one of the first philosophers who aimed at a deeper understanding of the relation between human nature and technology. Rejecting Husserl’s later emphasis on the transcendental subject, he insists that human nature can only be understood by the formula “I am I plus my circumstances.” Philosophy can thus neither start from the isolated subject (as in idealism), nor can it interpret everything from the perspective of the material conditions (as in materialism). Rather, it must find a middle ground. The essence of humans is for Ortega not determined by nature; this distinguishes humans from plants or animals or from physical objects—all having a defined, specific given nature. Man must determine his own nature by himself by way of the creative imagination. Technology is interpreted as the material realization of this self-image; it is a projection of an inner invention into nature. According to Ortega, technology evolved in three phases: It started as a collection of accidental findings of means toward ends by pure chance. In a later state, these findings became traditions and skills that were passed on to the next generation. Modern technology marks a radical difference, since it is based on a systematic scientific approach, which forms the third phase. This approach, however, tends to become the dominant mode of thinking, so that man’s creative capacity for imagination (which is at the heart of man’s very essence) is in danger of being replaced or losing its importance (Ortega y Gasset, 1914/1961).
Martin Heidegger’s (1977) analysis of technology in his essay “The Question Concerning Technology” is also very influential. His philosophy aims at understanding the notion of being, which—so claims Heidegger—has been misinterpreted or neglected by traditional European philosophy. Since man is the only known being that can ask for the meaning of being, Heidegger’s analysis in Sein und Zeit starts from an interpretation of the existence of such a being ( Da-sein ). Even though his book is meant to be an exercise in philosophical (fundamental) ontology, it offers many anthropological insights about the specific human form of existence, in which the knowledge and the denial of one’s own mortality form essential human features.
In his later work, Heidegger (1977) understands technology as a specific form of disclosing reality. Asked for the essence of technology, people usually refer to it as a means to achieve an end (instrumental definition), or they define technology as an essential human activity (anthropological definition). Even though Heidegger admits that these definitions are “correct,” they do not disclose the essential truth about technology for two reasons. Essentially, (1) technology is not a tool for achieving an end, but rather the perspective under which everything that exists is seen only as a potential resource to achieve an (external) end. Furthermore, (2) this disclosure of reality is not a human-directed practice: Humans are driven objects rather than being themselves the active subjects. According to these conclusions, the instrumental and the anthropological definitions of technology do not capture the whole truth of technology. Let us look at these two points in turn, as follows:
- The essence of technology lies, according to Heidegger, in its capacity to disclose reality ( entbergen ) under a very specific, limited perspective. This perspective reduces everything to a potential object for manipulation, a resource ( Bestand ) for further activity. Technology is thus a way to disclose something hidden. Following his analysis of the Greek word for truth ( aletheia ) as referring to something undisclosed, he sees thus a “truth” at work, under which reality presents itself as a mere collection of resources for external purposes, rid of all inner logic and teleology that was so prominent in traditional understandings of nature. Heidegger points at the different ways in which a river is seen by a poet in an artwork ( Kunst werk), on the one hand, and, on the other hand, in which the same river is seen by an engineer as a potential resource for energy generation in a power plant ( Kraft werk).
- Heidegger then goes on to claim that opposed to the image of man being in control of technology and using it for his purposes, he should rather be seen as being provoked ( herausgefordert ) by this coming to pass. Heidegger clearly wants to reject the optimistic idea of “man being in control” through the help of modern technology and, rather, revert it to its opposite: man being driven by a force greater than himself. He calls this driving force the essence of technology, the en-framing ( Ge-stell ) that prompts humans to look at nature under the idea of its usability. In doing so, man is in highest danger, but not because of potential hazards or specific negative consequence of modern technology. The danger is, rather, that he loses sight of understanding nature in a different way and that he might finally end up understanding also himself and other humans only as potential “resources” or potential material for manipulation and instrumentalization. Heidegger suspects that art might be a potential antidote to this development: In Greek, techne originally encompassed also the production of beautiful objects in art. Thus, a deeper understanding of technology might reveal its relation to art and might point to the fact that art offers a potential answer to the challenge that modern technology poses to human self-understanding.
Certainly, Heidegger’s contribution to the modern philosophy of technology lies more in highlighting this essential dimension of technology as a threat, rather than in elaborating strategies to counter these inherent dangers. Heidegger’s article is arguably the single most influential essay written in the philosophy of technology, although his mannered, often dark language allows for different interpretations and often lacks the clarity of philosophical contributions from the analytical school. But the idea that “technology” and technological rationality is a limited form of looking at reality—one that is in strong need of a countervision, and that might further lead to a deformation of intersubjective human relations and that finally affects human self-understanding—has ever since been a prominent topic in different thinkers from Adorno and Marcuse to Jürgen Habermas, as illustrated earlier. This idea has often been linked with an ethical concern: Modern technology calls for new ethical guidelines, and despite some beneficial consequence, poses a potential threat to human existence. Much of this ethical debate about modern technology was triggered by its potential to radically destroy human life, be it through nuclear, biological, or chemical weapons or by consequences of environmental pollution and climate change.
Heidegger’s pupil Hans Jonas (1984) was one of the first philosophers to emphasize the need for a specific “ethics for the age of technology,” feeling that modern technology urges us to radically reconsider our ethical intuitions in order to meet the new challenges. Nevertheless, based on humans’ anthropological need to seek protection against nature, classical technology never fully reached this aim. Nature remained always more powerful than men, and the consequences of human actions were mostly not far-reaching. Traditional ethics could therefore focus on the “near and dear.” Modern technology, however, radically changes the picture: Its scope is unknown in premodern times; its consequences and potential dangers could be fatal, far-reaching, and irreversible. Focusing on the environmental problems of modern societies with, as the darkest perspective, the possible extinction of humankind, Jonas suggests broadening the scope of our ethical obligations: If our actions are more far-reaching than ever before in the history of humankind, we need to acquire a new ethical countervision. Jonas finds this remedy in the anthropological feature of our feelings of responsibility. Responsibility often expresses an asymmetrical relation, as in parents who feel responsible to care for their children. The old ethical intuition to derive obligations from the rights of free and conscious individuals, able to participate in argumentation and democratic decisions, seems to be too narrow to account for most environmental problems: Future generations are not yet born, animals and nature cannot in the same sense be regarded as having rights, as has been established in previous ethical approaches to the idea of universal human rights. But obligations may also stem from the idea of responsibility, from the idea that something has been given into our care.
Analytic philosophy is rooted in the quest for clear conceptualization, sound argumentation, and scientific precision. For early analytical philosophy in the Vienna Circle, the mathematical nature of scientific knowledge could serve as a role model for knowledge as such: hence, the need for and the extended usage of logical formalization within analytic philosophy. Skeptical of the quest to address the essence of things like “the technology” in general, analytic philosophers very often focus on concrete problems linked to very specific technologies. Even though many thinkers in the line of logical positivism thus greeted scientific knowledge as the highest form of knowledge, this did not always lead to an unbalanced embrace of technology. In Bertrand Russell (1951), we find a skeptical attitude toward the social benefits of technology, especially if it is linked with totalitarian ideology. Thus, he stresses the importance of democratic education; if placed in a democratic context and applied in well-defined careful steps, technology is, however, beneficial for progress in a way in which Karl Popper (1957) typically advertises as piecemeal social engineering. Important early contributions to an analytic philosophy of technology stem further from Mario Bunge (1979), whose ideas closely link to the program of logical empiricism and oppose the “romantic wailings about the alleged evils of technology” (p. 68).
Even though this distinction between humanities’ philosophy of technology and engineering’s philosophy of technology (Mitcham, 1994) marks the background of the philosophical discussion on technology in the early 20th century, the debate soon moved beyond this opposition. Three tendencies seem to be of importance.
First, continental philosophy was moving away from the attempt to come up with metaphysical, religious, or anthropological answers to the big questions. With the emergence of postmodernism, the alleged end of the “big stories” was proclaimed, thus making a metaphysical approach less fashionable. Appealing to ontology (as in Heidegger), to metaphysics, or to religious ideals (as in Jonas) seemed less promising. Even though early continental philosophy was very critical with regard to strategic rationality and technology, it has been criticized by postmodernism as not moving radically beyond the central modernistic Western ideal of a rational philosophical synthesis or universal world interpretation.
Second, the focus within the philosophy of technology moved toward a renewed interest in looking at concrete technologies and the challenges they pose for analytical and ethical reflection, a movement that has been called the empirical turn in the philosophy of technology (Kroes, 2001).
Third, different attempts were soon made to bridge the gap between the two camps. In post-world-war Germany, the Society of German Engineers (VDI) established a dialogue about the responsibilities of scientists and engineers, addressing topics and worries of the humanities. The experience of the massive and systematic use of technology for organized mass murder during the holocaust and the development of technology for modern warfare, including the development of the nuclear bomb, raised issues about the responsibilities of engineers. The debate of the VDI meetings resulted in a series of important publications on the philosophy of technology (Rapp, 1981); these must be recognized as an important attempt to synthesize different strands of philosophical thinking, even though it can be asked how far the VDI school was really successful in transcending its engineering-philosophical origins (Mitcham, 1994, p. 71).
Along a similar line, authors have tried to combine the phenomenological approach with American pragmatism, thus bridging insights of a more continental and a more analytical tradition. Common to phenomenology and pragmatism is the idea of the priority of praxis over theory and thus the tendency not to see technology as applied science but, rather, science as a purified or abstract form of (technological) praxis. Following the works of John Dewey, thinkers like Paul T. Durbin (1992), Larry Hickman (1990), and Don Ihde (1979) have tried to establish a pragmatist phenomenological approach to technology. The insights of Don Ihde that each technology either extends human bodily experience (e.g., the microscope) or calls for human interpretations (e.g., the thermometer) are of particular anthropological interest. If technology amplifies our experience, then it always does so at the cost of a reduction: In highlighting or amplifying certain aspects of reality, it makes invisible other aspects of this very same reality (as in an ultrasonic picture) (Ihde, 1979). The way technology thus “mediates” our interpretation of the world, and our actions within it, has been a further object of extended research (e.g., Verbeek, 2005).
A further attempt to bridge humanist and engineering tradition has been made by Carl Mitcham (1994), who nevertheless tries to defend the priority of the humanist perspective, but at the same time develops an analytic framework that should serve for further investigation within the philosophy of technology. He distinguishes among technology as object (tools), as type of knowledge, as activity, and as volition (expression of man’s intention or will). The 1980s and 1990s saw an increased interest, especially in the analyses of the first three aspects of this distinction.
With regard to the fourth aspect, ethical issues have been a central topic for many philosophers of technology, ranging from debates about the responsibility of scientists and engineers, medical and bioethics, business ethics, technology assessment, risk assessment and decision under uncertainty, to environmental ethics. Two of these fields are of particular interest from an anthropological perspective: In environmental ethics, those theories might shed light on anthropological questions seeking to interpret the environmental crisis as essentially rooted in human nature. It has been argued that it is a human tendency to value short-term (individual) interests more highly than long-term (collective) interests, thus putting a pessimistic neo-Hobbesian anthropology in the middle of the debate. According to Garrett Hardin (1968), it is this very human tendency (together with a mismatch in the growth of the human population that exceeds the growth of the supply of the food or other resources) that leads to the “tragedy of the commons.” Research in game theory and environmental sociobiology indicates the possibility of holding a more optimistic view of the development of cooperative strategies in humans (Axelrod, 1984), though the issue is still debated and there is room for a more pessimistic perspective, as has been defended early on by some sociobiologists (Dawkins, 1978) or recently by some philosophers (Gardiner, 2001).
In the ethical debate on transhumanism, finally, many links can be found to classical anthropological questions about the essence of man (e.g., Baillie, 2005; Fukuyama, 2004). The central debated question is whether it is morally allowed, forbidden, or even demanded from us to enhance our human capacities through new technologies, ranging from short-term nonevasive ways (like taking performanceenhancing drugs) to fundamental irreversible changes (like genetic engineering). While bioconservativists argue against an extended usage of enhancement technologies, transhumanists point to the potential benefits of these new options. It is reasonable to assume that these issues will be with us as technology advances and opens new possibilities to alter the human condition. This opens a radical new challenge to anthropology, which until recently dedicated itself to understanding the given human nature, while it now has to face the normative question of which we should choose as our future nature, once technology offers radical new options of changing human nature (e.g., as by slowing down or even stopping the process of aging). It seems that the anthropology of the future must take into consideration, more and more, normative claims and it must reach out to incorporate ethics to prepare itself for the challenges modern technology poses.
Looking at recent tendencies in research, it can be argued that the initial focus on linking technology with a universal, philosophical anthropological vision, also rooted in biological knowledge, was one of the key achievements of early philosophical anthropology in the works of Gehlen and others. What made these anthropologies remarkable was their attempt to bring together the different traditions of anthropological thought, ranging from philosophy to sociology and biology. A turn toward a more social perspective was established first by Gehlen himself, the Frankfurt school, and later STS studies, sometimes leading away from or even lacking both an underlying philosophical vision and an interest in our biological nature. Very recently, however, sociologists and philosophers have shown an increased interest in biology (as is visible in the ever-growing numbers of publications in sociobiology and the philosophy of biology). This increased attention has not yet led to a revival of an interest in the links between anthropology and technology. But in order to understand man—both in his evolutionary origins and (maybe even more) in his current historical situation—it seems to demand attention to man’s amazing capacity to develop technology.
It can reasonably be argued that what is thus needed is a new vision of how to synthesize the different fields of biological, social, and cultural anthropology. It seems that after the empirical turn to gather extended details over the biological and social aspects of technology, there is now a call for a new philosophical turn, seeking a new discourse synthesis. Many classical questions of anthropology will tend to remain unanswered, if academic research remains focused only on disciplinary perspectives, which always look at only a part of the whole picture. It is certainly true that man is a social animal, that he has biological roots and that he can ask ethical and philosophical questions about the good and about his place in this universe. The disciplinary separations in biology, sociology, and philosophy (to name just a few) tend, however, to distract from the fact that man in reality is a unity, meaning that a true answer to the most fundamental question of anthropology (What is man?) calls for a plausible combination of these approaches. To synthesize the different aspects of our knowledge about our own human nature is certainly far from being an easy task, but it seems more needed than ever.
But if this is not yet a big enough challenge, there is even a second aspect that makes the quest for a synthesis even more challenging. It seems that a new anthropological vision of humankind must answer a question that classical anthropology has not been dealing with: If technology soon allows us to alter our very nature, then we must know not only what the human condition is, but also what the human condition should be.
Ethics might again enter anthropological reflection, as has been hinted at already by early thinkers such as Scheler and Jonas. Recent attempts to place man in the middle of both a normative vision of ideals, on the one side, and against a profound overview of our descriptive knowledge about our essence, on the other side (as in the voluminous attempt at a synthesis in Hösle, 2004), deserve attention, as they might be the first steps toward a renewed synthetic anthropology that tries to bridge the gaps among the different disciplines. A deepened understanding of technology must be a central part of these efforts, since the way we use tools and produce artifacts is one of the remarkable features of humankind—a feature in much need of guidance by descriptive knowledge and ethical wisdom, especially in our age in which technology (of which humans have been the subject) is about to discover the condition humana as its potential object in a way more radical than ever before.
Bibliography:
- Adorno, T. (1979). Dialectic of enlightenment. London: Verso.
- Adorno, T. (1999). Aesthetic theory. London: Athlone.
- Ambrose, S. H. (2001). Paleolithic technology and human evolution. Science, 291 (5509), 1748–1753.
- Axelrod, R. (1984). The evolution of cooperation. New York: Basic Books.
- Baillie, H. (2005). Is human nature obsolete? Genetics, bioengineering, and the future of the human condition. Cambridge: MIT Press.
- Beck, B. (1980). Animal tool behaviour. New York: Garland.
- Berger, P. L., & Luckmann, T. (1966). The social construction of reality: A treatise in the sociology of knowledge. Garden City, NY: Anchor Books.
- Bunge, M. (1979). The five buds of technophilosophy. Technology in Society, 1 (1), 67–74.
- Castells, M. (1999). The information age: Economy, society and culture. Malden, MA: Blackwell.
- Dawkins, R. (1978). The selfish gene. Oxford, UK: Oxford University Press.
- Durbin, P. (1992). Social responsibility in science, technology, and medicine. Bethlehem, PA: Lehigh University Press.
- Fukuyama, F. (2004). Transhumanism. Foreign Policy, 144, 42–43.
- Gardiner, S. M. (2001). The real tragedy of the commons. Philosophy and Public Affairs, 30 (4), 387–416.
- Gehlen, A. (1980). Man in the age of technology. New York: Columbia University Press.
- Gehlen, A. (1988). Man, his nature and place in the world. New York: Columbia University Press.
- Habermas, J. (1971). Knowledge and human interests. Boston: Beacon Press.
- Haferkamp, H. (1992). Social change and modernity. Berkeley: University of California Press.
- Heidegger, M. (1977). The question concerning technology, and other essays. New York: Harper & Row.
- Hickman, L. (1990). John Dewey’s pragmatic technology. Bloomington: Indiana University Press.
- Hösle, V. (2004). Morals and politics (S. Randall, Trans.). Notre Dame, IN: University of Notre Dame Press.
- Ihde, D. (1979). Technics and praxis. Boston: D. Reidel.
- Jonas, H. (1984). The imperative of responsibility: In search of an ethics for the technological age. Chicago: University of Chicago Press.
- Kroes, P. (2001). The empirical turn in the philosophy of technology. New York: JAI.
- Laland, K. (2009). The question of animal culture. Cambridge, MA: Harvard University Press.
- Latour, B. (1979). The social construction of scientific facts. Beverly Hills, CA: Sage.
- Latour, B. (2005). Reassembling the social: An introduction to actor-network-theory. New York: Oxford University Press.
- Marx, K. (1938). London: Allen & Unwin.
- McDermott, J. (1969). Technology: The opiate of the intellectuals. The New York Review of Books, 13 (2), 25–35.
- Misa, T. J., Brey, P., & Feenberg, A. (2004). Modernity and technology. Cambridge: MIT Press.
- Mitcham, C. (1994). Thinking through technology: The path between engineering and philosophy. Chicago: University of Chicago Press.
- Nora, S. (1980). The computerization of society: A report to the president of France. Cambridge: MIT Press.
- Oakley, K. (1957). Man the tool-maker. Chicago: University of Chicago Press.
- Ortega y Gasset, J. (1961). Meditations on Quixote. New York: Norton. (Original work published 1914)
- Pfaffenberger, B. (1988). Fetishised objects and humanized nature: Towards an anthropology of technology. Man, 23 (2), 236–252.
- Pfaffenberger, B. (1992). Social anthropology of technology. Annual Revue of Anthropology, 21, 491–516.
- Pressnell, L. (1960). Studies in the industrial revolution, presented to T. S. Ashton. London: University of LondonAthlone Press.
- Rapp, F. (1981). Analytical philosophy of technology. Boston: D. Reidel.
- Russell, B. (1951). The impact of science on society. New York: Columbia University Press.
- Schaik, C. P., Deaner, R. O., & Merrill, M.Y. (1999).The conditions for tool use in primates: Implications for the evolution of material culture. Journal of Human Evolution, 36 (6), 719–741.
- Scheler, M. (1961). Man’s place in nature. New York: Farrar, Strauss & Giroux.
- Smelser, N. (1969). Social change in the industrial revolution: An application of theory to the British cotton industry. Chicago: University of Chicago Press.
- Snow, C. (1959). The two cultures and the scientific revolution (The Rede lecture, 1959). Cambridge, UK: Cambridge University Press.
- Tomasello, M. (1999). The cultural origins of human cognition. Cambridge, MA: Harvard University Press.
- Verbeek, P. P. (2005). What things do: Philosophical reflections on technology, agency, and design. University Park: Pennsylvania State University Press.
- Winner, L. (1980). Do artifacts have politics? Daedalus, 109, 121–123.
- Winner, L. (1986). Technology as forms of life. In The whale and the reactor: A search for limits in an age of high technology. Chicago: University of Chicago Press.
- Woolgar, S. (1991). The turn to technology. Science, Technology and Human Values, 16 (1), 20–50.
- Wrangham, R. (1994). Chimpanzee cultures. Cambridge, MA: Harvard University Press.
ORDER HIGH QUALITY CUSTOM PAPER

- Trending Now
- Foundational Courses
- Data Science
- Practice Problem
- Machine Learning
- System Design
- DevOps Tutorial
Difference between Research Papers and Technical Articles for Journal Publication
- Difference between Paper and Article for Scientific Writings
- Difference between Vertical search and Horizontal search
- Difference between Software Inspection and Technical Review
- Difference between Research Paper and Review Paper
- Difference between Data Science and Operations Research
- Difference between <article> tag and <section> tag
- Difference between Qualitative research and Quantitative research
- Difference between Fundamental and Technical Analysis
- Difference between Information System and Information Technology
- Difference Between Article and Essay
- Difference between Project Report and Research Report
- Difference between Functional Testing and Implementational Testing Approach
- Difference between Project Engineer and Mechanical Engineer
- Difference between Elasticsearch and Solr
- Difference between semantic and non-semantic elements
- Differences between Interface and Integration Testing
- Technical Product Manager vs Product Manager | Difference Between
- Difference Between Journal and Ledger
- What Is The Difference Between NATA And JEE Paper 2?
Research Papers: Research Papers are write-ups which record the result/report examinations tired specific zone. For the most part, they take an up to this point obscure issue in a given field, propose an arrangement for it and assess the status of the arrangement in comparison with other modern solutions. In this way, in a sense, they move the wilderness of information within the field. Based on the nature and reason of the movement carried out, and the way the write-up is composed. Technical Articles: A technical article is an editorial for a magazine or an internet benefit that’s about a specialized point, and regularly the article drills down into a few low-level of detail. May be computers, maybe material science or chemistry or any other science. It can be around math. It can be approximately pharmaceutical or wellbeing or diet. It can be around the material science of cooking. There are truly thousands of potential points of specialized articles. Below is a table of differences between Research Papers and Technical Articles:
.Difference-table { border-collapse: collapse; width: 100%; } .Difference-table td { text-color: black !important; border: 1px solid #5fb962; text-align: left !important; padding: 8px; } .Difference-table th { border: 1px solid #5fb962; padding: 8px; } .Difference-table tr>th{ background-color: #c6ebd9; vertical-align: middle; } .Difference-table tr:nth-child(odd) { background-color: #ffffff; }
Please Login to comment...
Similar reads.
- Difference Between
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
NTRS - NASA Technical Reports Server
Available downloads, related records.
MIT Technology Review
- Newsletters
Super-efficient solar cells: 10 Breakthrough Technologies 2024
Solar cells that combine traditional silicon with cutting-edge perovskites could push the efficiency of solar panels to new heights.
- Emma Foehringer Merchant archive page

Beyond Silicon, Caelux, First Solar, Hanwha Q Cells, Oxford PV, Swift Solar, Tandem PV
3 to 5 years
In November 2023, a buzzy solar technology broke yet another world record for efficiency. The previous record had existed for only about five months—and it likely won’t be long before it too is obsolete. This astonishing acceleration in efficiency gains comes from a special breed of next-generation solar technology: perovskite tandem solar cells. These cells layer the traditional silicon with materials that share a unique crystal structure.
In the decade that scientists have been toying with perovskite solar technology , it has continued to best its own efficiency records, which measure how much of the sunlight that hits the cell is converted into electricity. Perovskites absorb different wavelengths of light from those absorbed by silicon cells, which account for 95% of the solar market today. When silicon and perovskites work together in tandem solar cells, they can utilize more of the solar spectrum, producing more electricity per cell.
Technical efficiency levels for silicon-based cells top out below 30%, while perovskite-only cells have reached experimental efficiencies of around 26%. But perovskite tandem cells have already exceeded 33% efficiency in the lab. That is the technology’s tantalizing promise: if deployed on a significant scale, perovskite tandem cells could produce more electricity than the legacy solar cells at a lower cost.
But perovskites have stumbled when it comes to actual deployment. Silicon solar cells can last for decades. Few perovskite tandem panels have even been tested outside.
The electrochemical makeup of perovskites means they’re sensitive to sucking up water and degrading in heat, though researchers have been working to create better barriers around panels and shifting to more stable perovskite compounds.
In May, UK-based Oxford PV said it had reached an efficiency of 28.6% for a commercial-size perovskite tandem cell, which is significantly larger than those used to test the materials in the lab, and it plans to deliver its first panels and ramp up manufacturing in 2024. Other companies could unveil products later this decade.
Climate change and energy
The problem with plug-in hybrids their drivers..
Plug-in hybrids are often sold as a transition to EVs, but new data from Europe shows we’re still underestimating the emissions they produce.
- Casey Crownhart archive page
These artificial snowdrifts protect seal pups from climate change
The human-built habitats shield the pups from predators and the freezing cold, but they’re threatened by global temperature rise.
- Matthew Ponsford archive page
How thermal batteries are heating up energy storage
The systems, which can store clean energy as heat, were chosen by readers as the 11th Breakthrough Technology of 2024.
The hard lessons of Harvard’s failed geoengineering experiment
Some observers argue the end of SCoPEx should mark the end of such proposals. Others say any future experiments should proceed in markedly different ways.
- James Temple archive page
Stay connected
Get the latest updates from mit technology review.
Discover special offers, top stories, upcoming events, and more.
Thank you for submitting your email!
It looks like something went wrong.
We’re having trouble saving your preferences. Try refreshing this page and updating them one more time. If you continue to get this message, reach out to us at [email protected] with a list of newsletters you’d like to receive.
Main Navigation
- Code of Conduct
- Create Profile
- Reset / Forgot Password
- Privacy Policy
- Contact CVPR
CVPR Technical Program Features Presentations on the Latest AI and Computer Vision Research for Healthcare, Robotics, Virtual Reality, Autonomous Vehicles, and Beyond
From pathology to human avatars, oral papers—top 3% of all papers—reveal advanced research results.
LOS ALAMITOS, Calif. , 1 6 May 2024 – Co-sponsored by the IEEE Computer Society (CS) and the Computer Vision Foundation (CVF), the 2024 Computer Vision and Pattern Recognition (CVPR) Conference is the preeminent event for research and development (R&D) in the hot topic areas of computer vision, artificial intelligence (AI), machine learning (ML), augmented, virtual and mixed reality (AR/VR/MR), deep learning, and related fields. Over the past decade, these areas have seen significant growth, and the emphasis on this sector by the science and engineering community has fueled an increasingly competitive technical program.
This year, the CVPR Program Committee received 11,532 paper submissions—a 26% increase over 2023—but only 2,719 were accepted, resulting in an acceptance rate of just 23.6%. Of those accepted papers, only 3.3% were slotted for oral presentations based on nominations from the area chairs and senior area chairs overseeing the program.
“CVPR is not only the premiere conference in computer vision, but it’s also among the highest-impact publication venues in all of science ,” said David Crandall , Professor of Computer Science at Indiana University, Bloomington, Ind., U.S.A., and CVPR 2024 Program Co-Chair. “Having one’s paper accepted to CVPR is already a major achievement, and then having it selected as an oral presentation is a very rare honor that reflects its high quality and potential impact.”
Taking place 17-21 June at the Seattle Convention Center in Seattle, Wash., U.S.A., CVPR offers oral presentations that speak to both fundamental and applied research in areas as diverse as healthcare applications, robotics, consumer electronics, autonomous vehicles, and more. Examples include:
- Pathology: Transcriptomics-guided Slide Representation Learning in Computational Pathology *– Training computer systems for pathology requires a multi-modal approach for efficiency and accuracy. New work from a multi-disciplinary team at Harvard University (Cambridge, Mass., U.S.A.), the Massachusetts Institute of Technology (MIT; Cambridge, Mass., U.S.A.), Emory University (Atlanta, Ga., U.S.A.) and others employs modality-specific encoders, and when applied on liver, breast, and lung samples from two different species, they demonstrated significantly better performance when compared to current baselines.
- Robotics: SceneFun3D: Fine-Grained Functionality and Affordance Understanding in 3D Scenes – Creating realistic interactions in 3D scenes has been troublesome from a technology perspective because it has been difficult to manipulate objects in the scene context. Research from ETH Zürich (Zürich, Switzerland), Google (Mountainview, Calif., U.S.A.), Technical University of Munich (TUM; Munich, Germany), and Microsoft (Redmond, Wash., U.S.A.) has begun bridging that divide by creating a large-scale dataset with more than 14.8k highly accurate interaction annotations for 710 high-resolution real-world 3D indoor scenes. This work, as the paper concludes, has the potential to “stimulate advancements in embodied AI, robotics, and realistic human-scene interaction modeling .”
- Virtual Reality: URHand: Universal Relightable Hands – Teams from Codec Avatars Lab at Meta (Menlo Park, Calif., U.S.A.) and Nanyang Technological University (Singapore) unveil a hand model that generalizes to novel viewpoints, poses, identities, and illuminations, which enables quick personalization from a phone scan. The resulting images make for a more realistic experience of reaching, grabbing, and interacting in a virtual environment.
- Human Avatars: Semantic Human Mesh Reconstruction with Textures – Working to create realistic human models, teams at Nanjing University (Nanjing, China) and Texas A&M University (College Station, Texas, U.S.A.) designed a method of 3-D human mesh reconstruction that is capable of producing high-fidelity and robust semantic renderings that outperform state-of-the-art methods. The paper concludes, “This approach bridges existing monocular reconstruction work and downstream industrial applications, and we believe it can promote the development of human avatars.”
- Text-to-Image Systems: Ranni: Taming Text-to-Image Diffusion for Accurate Instruction – Existing text-to-image models can misinterpret more difficult prompts, but now, new research from Alibaba Group (Hangzhou, Zhejiang, China) and Ant Group (Hangzhou, Zhejiang, China) has made strides in addressing that issue via a middleware layer. This approach, which they have dubbed Ranni, supports the text-to-image generator in better following instructions. As the paper sums up, “Ranni shows potential as a flexible chat-based image creation system, where any existing diffusion model can be incorporated as the generator for interactive generation.”
- Autonomous Driving: Producing and Leveraging Online Map Uncertainty in Trajectory Prediction – To enable autonomous driving, vehicles must be pre-trained on the geographic region and potential pitfalls. High-definition (HD) maps have become a standard part of a vehicle’s technology stack, but current approaches to those maps are siloed in their programming. Now, work from a research team from the University of Toronto (Toronto, Ontario, Canada), Vector Institute (Toronto, Ontario, Canada), NVIDIA Research (Santa Clara, Calif., U.S.A.), and Stanford University (Palo Alto, Calif., U.S.A.) enhances current methodologies by incorporating uncertainty, resulting in up to 50% faster training convergence and up to 15% better prediction performance.
“As the field’s leading event, CVPR introduces the latest research in all areas of computer vision,” said Crandall. “ In addition to the oral paper presentations, there will be thousands of posters, dozens of workshops and tutorials, several keynotes and panels, and countless opportunities for learning and networking. You really have to attend the conference to get the full scope of what’s next for computer vision and AI technology.”
Digital copies of all final technical papers* will be available on the conference website by the week of 10 June to allow attendees to prepare their schedules. To register for CVPR 2024 as a member of the press and/or request more on a specific paper, visit https://cvpr.thecvf.com/Conferences/2024/MediaPass or email [email protected] . For more information on the conference, visit https://cvpr.thecvf.com/ .
*Papers linked in this press release refer to pre-print publications. Final, citable papers will be available just prior to the conference.
About CVPR 2024
The Computer Vision and Pattern Recognition Conference (CVPR) is the preeminent computer vision event for new research in support of artificial intelligence (AI), machine learning (ML), augmented, virtual and mixed reality (AR/VR/MR), deep learning, and much more. Sponsored by the IEEE Computer Society (CS) and the Computer Vision Foundation (CVF), CVPR delivers the important advances in all areas of computer vision and pattern recognition and the various fields and industries they impact. With a first-in-class technical program, including tutorials and workshops, a leading-edge expo, and robust networking opportunities, CVPR, which is annually attended by more than 10,000 scientists and engineers, creates a one-of-a-kind opportunity for networking, recruiting, inspiration, and motivation.
CVPR 2024 takes place 17-21 June at the Seattle Convention Center in Seattle, Wash., U.S.A., and participants may also access sessions virtually. For more information about CVPR 2024, visit cvpr.thecvf.com .
About the Computer Vision Foundation
The Computer Vision Foundation (CVF) is a non-profit organization whose purpose is to foster and support research on all aspects of computer vision. Together with the IEEE Computer Society, it co-sponsors the two largest computer vision conferences, CVPR and the International Conference on Computer Vision (ICCV). Visit thecvf.com for more information.
About the IEEE Computer Society
Engaging computer engineers, scientists, academia, and industry professionals from all areas and levels of computing, the IEEE Computer Society (CS) serves as the world’s largest and most established professional organization of its type. IEEE CS sets the standard for the education and engagement that fuels continued global technological advancement. Through conferences, publications, and programs that inspire dialogue, debate, and collaboration, IEEE CS empowers, shapes, and guides the future of not only its 375,000+ community members, but the greater industry, enabling new opportunities to better serve our world. Visit computer.org for more information.
NVIDIA Presents New Robotics Research on Geometric Fabrics, Surgical Robots, and More at ICRA

During the IEEE International Conference on Robotics and Automation (ICRA) May 13-17 in Yokohama, Japan, many people will be discussing geometric fabrics. That topic is the subject of one of seven papers submitted by members of the NVIDIA Robotics Research Lab , along with collaborators, and featured at ICRA this week.
What are geometric fabrics?
In robotics, trained policies are approximate by nature. They usually do the right thing, but sometimes, they move the robot too fast, collide with things, or jerk the robot around. There is no guarantee of what may occur.
So, any time that someone deploys trained policies and especially reinforcement learning-trained policies on a physical robot, they use a layer of low-level controllers to intercept the commands from the policy. Then, they translate those commands so that they satisfy the limitations of the hardware.
When you’re training RL policies, run those controllers with the policy during training. The researchers determined that a unique value that could be supplied with their GPU-accelerated RL training tools was to vectorize those controllers so they’re available both during training and deployment. That’s what this research does.
For example, companies working on humanoid robots may show demos with low-level controllers that balance the robot but also keep the robot from running its arms into its own body.
The controllers the researchers chose to vectorize are from a past line of work on geometric fabrics. The paper, Geometric Fabrics: Generalizing Classical Mechanics to Capture the Physics of Behavior , won a best paper award at last year’s ICRA.
DeXtreme policies
The in-hand manipulation tasks that the researchers address in this year’s paper also come from a well-known line of research on DeXtreme .
In this new work, the researchers merge those two lines of research to train DeXtreme policies over the top of vectorized geometric fabric controllers. This keeps the robot safer, guides policy learning through the nominal fabric behavior, and systematizes sim2real training and deployment to get one step closer to using RL tooling in production settings.
This creates a foundational infrastructure enabling the researchers to quickly iterate to get the domain randomization right during training for successful sim2real deployment. For instance, by iterating quickly between training and deployment, they could adjust the fabric structure and add substantial random perturbation forces during training to achieve a level of robustness far superior to previous work.
In the prior DeXtreme work, the real-world experiments proved extremely hard on the physical robot, wearing down the motors and sensors and changing the behavior of underlying control through the course of experimentation. At one point, the robot broke down and started smoking!
But with geometric fabric controllers underlying the policy and protecting the robot, the researchers found that they could be much more liberal in deploying and testing policies without worrying about the robot destroying itself.
For more information, see Geometric Fabrics: A Safe Guiding Medium for Policy Learning or watch the DeXtreme example videos .
More robotics research at ICRA
Other noteworthy papers submitted this year include the following:
Out of Sight, Still in Mind
- Point Cloud World Model
The SynH2R authors propose a framework to generate realistic human grasping motions suitable for training a robot. For more information, see SynH2R: Synthesizing Hand-Object Motions for Learning Human-to-Robot Handovers .
The RDMemory authors test a robotic arm’s reaction to things previously seen but then occluded from view to ensure that it responds reliably in various environments. This work was done in both simulation and in real-world experiments.
For more information, see Out of Sight, Still in Mind: Reasoning and Planning About Unobserved Objects With Video Tracking Enabled Memory Models or watch the RDMemory example videos .
Point Cloud World Models
The Point Cloud World Models researchers set up a novel Point Cloud World Model (PCWM) and point cloud-based control policies that were shown to improve performance, reduce learning time, and increase robustness for robotic learners.
For more information, see Point Cloud Models Improve Visual Robustness in Robotic Learners .
The SKT-Hang authors look at the problem of how to use a robot to hang up a wide variety of objects on different supporting structures (Figure 1). While this might seem like an easy problem to solve, the variations in both the shapes of the objects as well as the supporting structures pose multiple challenges for the robot to overcome.

For more information, see SKT-Hang: Hanging Everyday Objects via Object-Agnostic Semantic Keypoint Trajectory Generation and the /HCIS-Lab/SKT-Hang GitHub repo.
Robots with surgical precision
Several new research papers have applications for use in hospital surgical environments.
ORBIT-Surgical
ORBIT-Surgical is a physics-based surgical robot simulation framework with photorealistic rendering powered by NVIDIA Isaac Sim on the NVIDIA Omniverse platform.
It uses GPU parallelization to train reinforcement learning and imitation learning algorithms that facilitate the study of robot learning to augment human surgical skills. It also enables realistic synthetic data generation for active perception tasks. The researchers demonstrate using ORBIT-Surgical sim-to-real transfer of learned policies onto a physical dVRK robot.
The underlying robotics simulation application for ORBIT-Surgical will be released as a free, open-source package upon publication.
For more information, see ORBIT-Surgical: An Open-Simulation Framework for Learning Surgical Augmented Dexterity .
The DefGoalNet paper focuses on shape servoing , which is a robotic task dedicated to controlling objects to create a specific goal shape. For more information, see DefGoalNet: Contextual Goal Learning From Demonstrations for Deformable Object Manipulation .
Meet NVIDIA Robotics partners at ICRA
NVIDIA robotics partners are showing off their latest developments at ICRA.
Zürich-based ANYbotics presents its ANYmal Research, which provides a complete software package that grants users access to low-level controls down to the ROS system. ANYmal Research is a community of hundreds of researchers working in top robotics research centers, including the AI Institute, ETH Zürich, and the University of Oxford. (Booth IC010)
Munich-based Franka Robotics highlights its work with NVIDIA Isaac Manipulator , an NVIDIA Jetson -based AI companion to power robot control and the Franka toolbox for Matlab. (Booth IC050)
Enchanted Tools shows off its Jetson-powered Mirokaï robots. (Booth IC053)
The NVIDIA Robotics Research Lab is a Seattle-based center of excellence focused on robot manipulation, perception, and physics-based simulation. It’s part of NVIDIA Research , which has more than 300 leading researchers around the globe, focused on topics spanning AI, computer graphics, computer vision, and self-driving cars.
Related resources
- GTC session: AI Robotics: Driving Innovation for the Future of Automation
- GTC session: Immersive Digital Assistants for Hybrid Teams: Weaving Generative AI into Collaborative XR for Manufacturing Planning
- GTC session: Next Phase of Industrial Robot Skills with AI
- SDK: Isaac Sim
- SDK: Isaac ROS
- Webinar: Enhancing Robotic Perception: Synthetic Data Generation using Omniverse Replicator
About the Authors

Related posts

NVIDIA Researchers Introduce Robot that Automatically Adapts to Different Terrains

UC Berkeley’s BADGR Robot Learns to Navigate on Its Own

Virtual Character Animation System Uses AI to Generate More Human-Like Movements

NVIDIA Unveils New Reinforcement Learning Research at ICRA 2019

Google's Tossingbot Can Toss Over 500 Objects Per Hour Into Target Locations
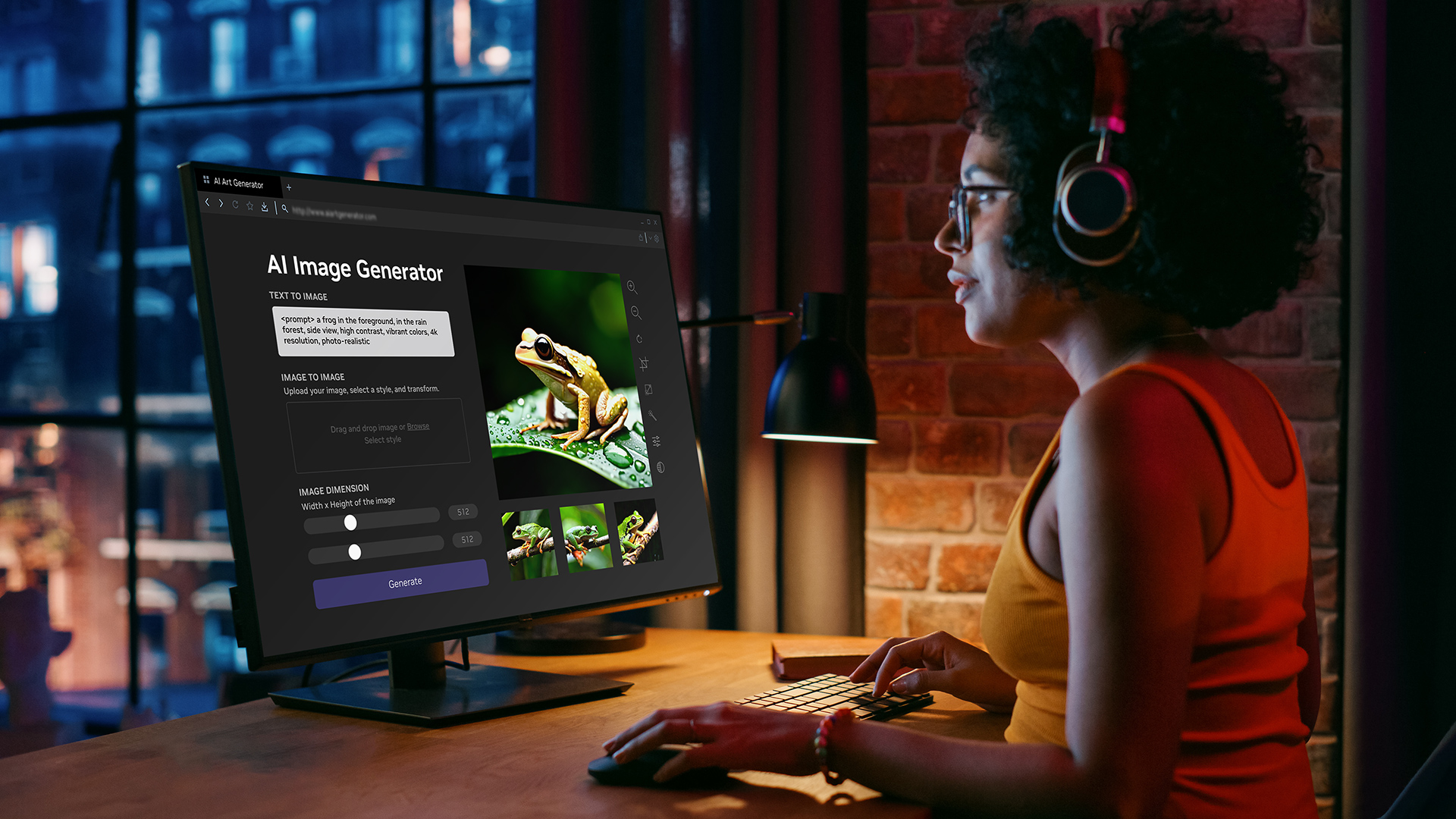
Rethinking How to Train Diffusion Models
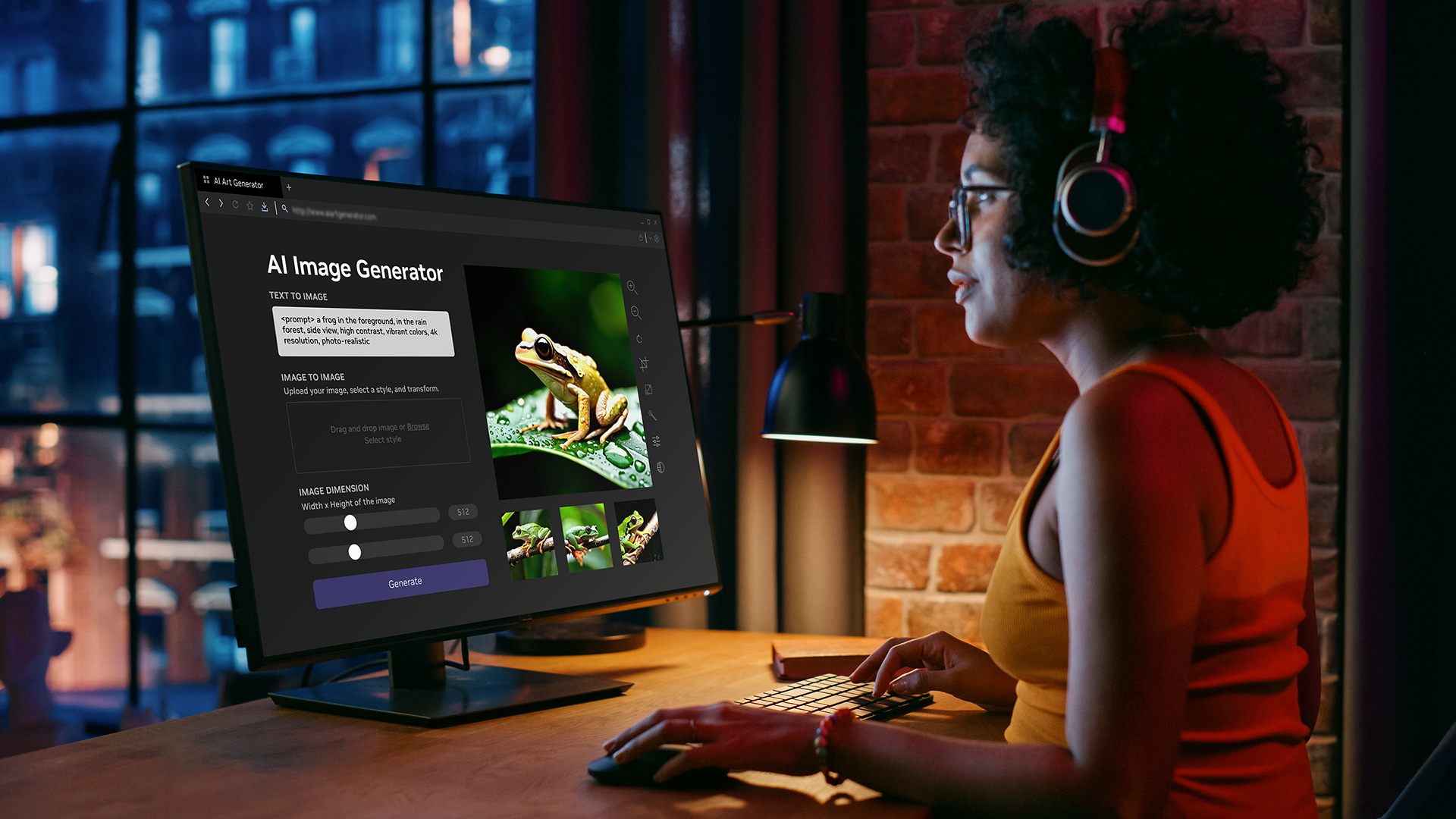
Generative AI Research Spotlight: Personalizing Text-to-Image Models

Most Popular NVIDIA Technical Blog Posts of 2023: Generative AI, LLMs, Robotics, and Virtual Worlds Breakthroughs
Teaching avs the language of human driving behavior with trajeglish.

Generative AI Research Spotlight: Demystifying Diffusion-Based Models
Help | Advanced Search
Computer Science > Machine Learning
Title: rlhf workflow: from reward modeling to online rlhf.
Abstract: We present the workflow of Online Iterative Reinforcement Learning from Human Feedback (RLHF) in this technical report, which is widely reported to outperform its offline counterpart by a large margin in the recent large language model (LLM) literature. However, existing open-source RLHF projects are still largely confined to the offline learning setting. In this technical report, we aim to fill in this gap and provide a detailed recipe that is easy to reproduce for online iterative RLHF. In particular, since online human feedback is usually infeasible for open-source communities with limited resources, we start by constructing preference models using a diverse set of open-source datasets and use the constructed proxy preference model to approximate human feedback. Then, we discuss the theoretical insights and algorithmic principles behind online iterative RLHF, followed by a detailed practical implementation. Our trained LLM, SFR-Iterative-DPO-LLaMA-3-8B-R, achieves impressive performance on LLM chatbot benchmarks, including AlpacaEval-2, Arena-Hard, and MT-Bench, as well as other academic benchmarks such as HumanEval and TruthfulQA. We have shown that supervised fine-tuning (SFT) and iterative RLHF can obtain state-of-the-art performance with fully open-source datasets. Further, we have made our models, curated datasets, and comprehensive step-by-step code guidebooks publicly available. Please refer to this https URL and this https URL for more detailed information.
Submission history
Access paper:.
- HTML (experimental)
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
- IEEE CS Standards
- Career Center
- Subscribe to Newsletter
- IEEE Standards
- For Industry Professionals
- For Students
- Launch a New Career
- Membership FAQ
- Membership FAQs
- Membership Grades
- Special Circumstances
- Discounts & Payments
- Distinguished Contributor Recognition
- Grant Programs
- Find a Local Chapter
- Find a Distinguished Visitor
- Find a Speaker on Early Career Topics
- Technical Communities
- Collabratec (Discussion Forum)
- Start a Chapter
- My Subscriptions
- My Referrals
- Computer Magazine
- ComputingEdge Magazine
- Let us help make your event a success. EXPLORE PLANNING SERVICES
- Events Calendar
- Calls for Papers
- Conference Proceedings
- Conference Highlights
- Top 2024 Conferences
- Conference Sponsorship Options
- Conference Planning Services
- Conference Organizer Resources
- Virtual Conference Guide
- Get a Quote
- CPS Dashboard
- CPS Author FAQ
- CPS Organizer FAQ
- Find the latest in advanced computing research. VISIT THE DIGITAL LIBRARY
- Open Access
- Tech News Blog
- Author Guidelines
- Reviewer Information
- Guest Editor Information
- Editor Information
- Editor-in-Chief Information
- Volunteer Opportunities
- Video Library
- Member Benefits
- Institutional Library Subscriptions
- Advertising and Sponsorship
- Code of Ethics
- Educational Webinars
- Online Education
- Certifications
- Industry Webinars & Whitepapers
- Research Reports
- Bodies of Knowledge
- CS for Industry Professionals
- Resource Library
- Newsletters
- Women in Computing
- Digital Library Access
- Organize a Conference
- Run a Publication
- Become a Distinguished Speaker
- Participate in Standards Activities
- Peer Review Content
- Author Resources
- Publish Open Access
- Society Leadership
- Boards & Committees
- Local Chapters
- Governance Resources
- Conference Publishing Services
- Chapter Resources
- About the Board of Governors
- Board of Governors Members
- Diversity & Inclusion
- Open Volunteer Opportunities
- Award Recipients
- Student Scholarships & Awards
- Nominate an Election Candidate
- Nominate a Colleague
- Corporate Partnerships
- Conference Sponsorships & Exhibits
- Advertising
- Recruitment
- Publications
- Education & Career
CVPR Technical Program Features Presentations on the Latest AI and Computer Vision Research

LOS ALAMITOS, Calif., 16 May 2024 – Co-sponsored by the IEEE Computer Society (CS) and the Computer Vision Foundation (CVF), the 2024 Computer Vision and Pattern Recognition (CVPR) Conference is the preeminent event for research and development (R&D) in the hot topic areas of computer vision, artificial intelligence (AI), machine learning (ML), augmented, virtual and mixed reality (AR/VR/MR), deep learning, and related fields. Over the past decade, these areas have seen significant growth, and the emphasis on this sector by the science and engineering community has fueled an increasingly competitive technical program.
This year, the CVPR Program Committee received 11,532 paper submissions—a 26% increase over 2023—but only 2,719 were accepted, resulting in an acceptance rate of just 23.6%. Of those accepted papers, only 3.3% were slotted for oral presentations based on nominations from the area chairs and senior area chairs overseeing the program.
“CVPR is not only the premiere conference in computer vision, but it’s also among the highest-impact publication venues in all of science,” said David Crandall, Professor of Computer Science at Indiana University, Bloomington, Ind., U.S.A., and CVPR 2024 Program Co-Chair. “Having one’s paper accepted to CVPR is already a major achievement, and then having it selected as an oral presentation is a very rare honor that reflects its high quality and potential impact.”
Taking place 17-21 June at the Seattle Convention Center in Seattle, Wash., U.S.A., CVPR offers oral presentations that speak to both fundamental and applied research in areas as diverse as healthcare applications, robotics, consumer electronics, autonomous vehicles, and more. Examples include:
- Pathology: Transcriptomics-guided Slide Representation Learning in Computational Pathology *– Training computer systems for pathology requires a multi-modal approach for efficiency and accuracy. New work from a multi-disciplinary team at Harvard University (Cambridge, Mass., U.S.A.), the Massachusetts Institute of Technology (MIT; Cambridge, Mass., U.S.A.), Emory University (Atlanta, Ga., U.S.A.) and others employs modality-specific encoders, and when applied on liver, breast, and lung samples from two different species, they demonstrated significantly better performance when compared to current baselines.
- Robotics: SceneFun3D: Fine-Grained Functionality and Affordance Understanding in 3D Scenes – Creating realistic interactions in 3D scenes has been troublesome from a technology perspective because it has been difficult to manipulate objects in the scene context. Research from ETH Zürich (Zürich, Switzerland), Google (Mountainview, Calif., U.S.A.), Technical University of Munich (TUM; Munich, Germany), and Microsoft (Redmond, Wash., U.S.A.) has begun bridging that divide by creating a large-scale dataset with more than 14.8k highly accurate interaction annotations for 710 high-resolution real-world 3D indoor scenes. This work, as the paper concludes, has the potential to “stimulate advancements in embodied AI, robotics, and realistic human-scene interaction modeling.”
- Virtual Reality: URHand: Universal Relightable Hands – Teams from Codec Avatars Lab at Meta (Menlo Park, Calif., U.S.A.) and Nanyang Technological University (Singapore) unveil a hand model that generalizes to novel viewpoints, poses, identities, and illuminations, which enables quick personalization from a phone scan. The resulting images make for a more realistic experience of reaching, grabbing, and interacting in a virtual environment.
- Human Avatars: Semantic Human Mesh Reconstruction with Textures – Working to create realistic human models, teams at Nanjing University (Nanjing, China) and Texas A&M University (College Station, Texas, U.S.A.) designed a method of 3-D human mesh reconstruction that is capable of producing high-fidelity and robust semantic renderings that outperform state-of-the-art methods. The paper concludes, “This approach bridges existing monocular reconstruction work and downstream industrial applications, and we believe it can promote the development of human avatars.”
- Text-to-Image Systems: Ranni: Taming Text-to-Image Diffusion for Accurate Instruction – Existing text-to-image models can misinterpret more difficult prompts, but now, new research from Alibaba Group (Hangzhou, Zhejiang, China) and Ant Group (Hangzhou, Zhejiang, China) has made strides in addressing that issue via a middleware layer. This approach, which they have dubbed Ranni, supports the text-to-image generator in better following instructions. As the paper sums up, “Ranni shows potential as a flexible chat-based image creation system, where any existing diffusion model can be incorporated as the generator for interactive generation.”
- Autonomous Driving: Producing and Leveraging Online Map Uncertainty in Trajectory Prediction – To enable autonomous driving, vehicles must be pre-trained on the geographic region and potential pitfalls. High-definition (HD) maps have become a standard part of a vehicle’s technology stack, but current approaches to those maps are siloed in their programming. Now, work from a research team from the University of Toronto (Toronto, Ontario, Canada), Vector Institute (Toronto, Ontario, Canada), NVIDIA Research (Santa Clara, Calif., U.S.A.), and Stanford University (Palo Alto, Calif., U.S.A.) enhances current methodologies by incorporating uncertainty, resulting in up to 50% faster training convergence and up to 15% better prediction performance.
“As the field’s leading event, CVPR introduces the latest research in all areas of computer vision,” said Crandall. “In addition to the oral paper presentations, there will be thousands of posters, dozens of workshops and tutorials, several keynotes and panels, and countless opportunities for learning and networking. You really have to attend the conference to get the full scope of what’s next for computer vision and AI technology.”
Digital copies of all final technical papers* will be available on the conference website by the week of 10 June to allow attendees to prepare their schedules. To register for CVPR 2024 as a member of the press and/or request more on a specific paper, visit https://cvpr.thecvf.com/Conferences/2024/MediaPass or email [email protected]. For more information on the conference, visit https://cvpr.thecvf.com/ .
*Papers linked in this press release refer to pre-print publications. Final, citable papers will be available just prior to the conference.
About the CVPR 2024 The Computer Vision and Pattern Recognition Conference (CVPR) is the preeminent computer vision event for new research in support of artificial intelligence (AI), machine learning (ML), augmented, virtual and mixed reality (AR/VR/MR), deep learning, and much more. Sponsored by the IEEE Computer Society (CS) and the Computer Vision Foundation (CVF), CVPR delivers the important advances in all areas of computer vision and pattern recognition and the various fields and industries they impact. With a first-in-class technical program, including tutorials and workshops, a leading-edge expo, and robust networking opportunities, CVPR, which is annually attended by more than 10,000 scientists and engineers, creates a one-of-a-kind opportunity for networking, recruiting, inspiration, and motivation.
CVPR 2024 takes place 17-21 June at the Seattle Convention Center in Seattle, Wash., U.S.A., and participants may also access sessions virtually. For more information about CVPR 2024, visit cvpr.thecvf.com .
About the Computer Vision Foundation The Computer Vision Foundation (CVF) is a non-profit organization whose purpose is to foster and support research on all aspects of computer vision. Together with the IEEE Computer Society, it co-sponsors the two largest computer vision conferences, CVPR and the International Conference on Computer Vision (ICCV). Visit thecvf.com for more information.
About the IEEE Computer Society Engaging computer engineers, scientists, academia, and industry professionals from all areas and levels of computing, the IEEE Computer Society (CS) serves as the world’s largest and most established professional organization of its type. IEEE CS sets the standard for the education and engagement that fuels continued global technological advancement. Through conferences, publications, and programs that inspire dialogue, debate, and collaboration, IEEE CS empowers, shapes, and guides the future of not only its 375,000+ community members, but the greater industry, enabling new opportunities to better serve our world. Visit computer.org for more information.
Recommended by IEEE Computer Society

The IEEE International Roadmap for Devices and Systems (IRDS) Emerges as a Global Leader for Chips Acts Visions and Programs

IEEE Computer Society Announces 2024 Class of Fellow

IEEE CS Releases 20 in their 20s List, Identifying Emerging Leaders in Computer Science and Engineering

IEEE CS Authors, Speakers, and Leaders Named to Inaugural TIME100 Most Influential People in Artificial Intelligence List

IEEE SustainTech Leadership Forum 2024: Unlocking the Future of Sustainable Technology for Buildings and Factories in the Built Environment

J. Gregory Pauloski and Rohan Basu Roy Named Recipients of 2023 ACM/IEEE CS George Michael Memorial HPC Fellowships

Keshav Pingali Selected to Receive ACM-IEEE CS Ken Kennedy Award

Hironori Washizaki Elected IEEE Computer Society 2025 President

IMAGES
VIDEO
COMMENTS
Supporting the automotive, aerospace, and commercial vehicle sectors, SAE Technical Papers provide professionals and students with the latest advances in mobility research. SAE Technical Papers help guide engineers through their project challenges and establish leadership in a competitive landscape.
Guideline #1: A clear new important technical contribution should have been articulated by the time the reader finishes page 3 (i.e., a quarter of the way through the paper). Guideline #2: Every section of the paper should tell a story.
IEEE Spectrum is an award-winning technology magazine and the flagship publication of IEEE, covering major trends and developments in technology, engineering, and science. The Institute, dedicated to IEEE members, features stories about IEEE activities, member profiles, conference information, important member dates and deadlines, IEEE election ...
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. ... CALL FOR PAPERS. ABOUT. 20-24 OCT 2024 | Kobe, Japan . SEE ALL UPCOMING. IEEE Personal Account. Change username/password; Purchase Details. Payment Options;
Naming. Give each concept in your paper a descriptive name to make it more memorable to readers. Never use terms like "approach 1", "approach 2", or "our approach", and avoid acronyms when possible. If you can't think of a good name, then quite likely you don't really understand the concept.
Scientific/technical writing is an essential part of research. The outcome of a research activity should be shared with others in the form of scientific paper publications; some ideas require a patent to reserve the implementation rights; and almost any research activity requires a funding source, for which a grant proposal is necessary.
Getting Started. Start collecting data a year or two ahead of time. Technical papers are generally focused on data, data interpretation, validation, and application. Otherwise, it is not a technical paper. For any paper, plan on a few weeks to write a 5,000 (CCP Technical Paper word count is 2,500) word paper.
Elsevier journals offer the latest peer-reviewed research papers on climate change, biodiversity, renewable energy and other topics addressing our planet's climate emergency. ... Explore scientific, technical, and medical research on ScienceDirect. Physical Sciences and Engineering Life Sciences Health Sciences Social Sciences and Humanities.
Technical papers are short - usually around six to eight pages long - however the actual text can be as little as two or three pages. This is because the Title, Synopsis and Introduction sections can take up the first page, and the Conclusions, Acknowledgements, References, and Bio's of authors can take up the last page.
NATO is boosting AI and climate research as scientific diplomacy remains on ice. As the military alliance created to counter the Soviet Union expands, it is prioritizing studies on how climate ...
In this paper we discuss the different principles of. writing a good technical paper. In section 2, we dis-. cus Quality Content, section 3 Good Grammar and Proper. Punctuation, Section 4 Writing ...
Section 1: Choosing Your Topic. The first step in technical paper writing is to choose a topic that is interesting as well as relevant to your field of study. Consider the current trends and advancements in your field, and identify a topic that you are passionate about and have a good understanding of. It's important to choose a topic that is ...
Technical Papers. The SEI Digital Library houses thousands of technical papers and other documents, ranging from SEI Technical Reports on groundbreaking research to conference proceedings, survey results, and source code. ... This paper describes the future research discussed at the 2022 Zero Trust Industry Day event.
IEEE provides guidelines for formatting your paper. These guidelines must be followed when you're submitting a manuscript for publication in an IEEE journal. Some of the key guidelines are: Formatting the text as two columns, in Times New Roman, 10 pt. Including a byline, an abstract, and a set of keywords at the start of the research paper.
I would like to thank Colin Brench, who has reviewed technical papers for many years for the IEEE International Symposium on EMC, for his input on what reviewers look for in Symposium and Transactions papers. References [1] D. R. Caprette (updated Aug. 2010) Rice University class notes on Writing Research Papers.
The NASA STI Repository (also known as the NASA Technical Reports Server (NTRS)) provides access to NASA metadata records, full-text online documents, images, and videos. The types of information included are conference papers, journal articles, meeting papers, patents, research reports, images, movies, and technical videos - scientific and ...
The Journal of Technical Writing and Communication (JTWC) is one of several prestigious international scholarly journals in the field of technical and professional communications. Published quarterly, JTWC strives to meet the diverse … | View full journal description. This journal is a member of the Committee on Publication Ethics (COPE).
in a technical paper. Based on the content of the abstract, the reader will decide whether the pa-per is worthy enough to merit further study. The abstract should classify your research and contri-bution in the research areas. It should contain the following four parts: a brief introduction de-scribing the discipline that the paper belongs to;
Reports, Proposals, and Technical Papers. Media File: Reports, Proposals, and Technical Papers. This resource is enhanced by a PowerPoint file. If you have a Microsoft Account, you can view this file with PowerPoint Online.
This sample technology research paper features: 8300 words (approx. 27 pages), an outline, and a bibliography with 48 sources. Browse other research paper examp ... Technical rationality is regarded as the exercise of strategic power to dominate (external) nature, but it is at the same time also leading to a suppression of the inner nature of ...
Research Papers. Technical Articles. Research paper carries more weight on the basic issues. Technical article puts more accentuation on the technique angle, not necessary announcing on the discoveries. A research paper won't warrant as broad of a reference list. A technical article, a peruser can anticipate to discover an broad book index.
The Research Aircraft for eVTOL Enabling TechNologies (RAVEN) Subscale Wind-Tunnel and Flight Test (SWFT) model is a subscale aircraft built for flight dynamics and controls research demonstrated in wind-tunnel and flight-test experiments. The intent of this paper is to provide a summary of past, current, and future efforts being pursued by the RAVEN-SWFT project.
In May, UK-based Oxford PV said it had reached an efficiency of 28.6% for a commercial-size perovskite tandem cell, which is significantly larger than those used to test the materials in the lab ...
From pathology to human avatars, oral papers—top 3% of all papers—reveal advanced research results ... With a first-in-class technical program, including tutorials and workshops, a leading-edge expo, and robust networking opportunities, CVPR, which is annually attended by more than 10,000 scientists and engineers, creates a one-of-a-kind ...
During the IEEE International Conference on Robotics and Automation (ICRA) May 13-17 in Yokohama, Japan, many people will be discussing geometric fabrics. That topic is the subject of one of seven papers submitted by members of the NVIDIA Robotics Research Lab, along with collaborators, and featured at ICRA this week.. What are geometric fabrics? In robotics, trained policies are approximate ...
We present the workflow of Online Iterative Reinforcement Learning from Human Feedback (RLHF) in this technical report, which is widely reported to outperform its offline counterpart by a large margin in the recent large language model (LLM) literature. However, existing open-source RLHF projects are still largely confined to the offline learning setting. In this technical report, we aim to ...
We explore large-scale training of generative models on video data. Specifically, we train text-conditional diffusion models jointly on videos and images of variable durations, resolutions and aspect ratios. We leverage a transformer architecture that operates on spacetime patches of video and image latent codes. Our largest model, Sora, is capable of generating a minute of high fidelity video.
LOS ALAMITOS, Calif., 16 May 2024 - Co-sponsored by the IEEE Computer Society (CS) and the Computer Vision Foundation (CVF), the 2024 Computer Vision and Pattern Recognition (CVPR) Conference is the preeminent event for research and development (R&D) in the hot topic areas of computer vision, artificial intelligence (AI), machine learning (ML ...