- Help & FAQ

The 10 research topics in the Internet of Things
- School of Computing
- Faculty of Science and Engineering
Research output : Chapter in Book/Report/Conference proceeding › Conference proceeding contribution › peer-review
Since the term first coined in 1999 by Kevin Ashton, the Internet of Things (IoT) has gained significant momentum as a technology to connect physical objects to the Internet and to facilitate machine-to-human and machine-to-machine communications. Over the past two decades, IoT has been an active area of research and development endeavors by many technical and commercial communities. Yet, IoT technology is still not mature and many issues need to be addressed. In this paper, we identify 10 key research topics and discuss the research problems and opportunities within these topics.
| Original language | English |
|---|---|
| Title of host publication | Proceedings - 2020 IEEE 6th International Conference on Collaboration and Internet Computing, CIC 2020 |
| Place of Publication | Piscataway, NJ |
| Publisher | |
| Pages | 34-43 |
| Number of pages | 10 |
| ISBN (Electronic) | 9781728141466 |
| DOIs | |
| Publication status | Published - 2020 |
| Event | - Virtual, Atlanta, United States Duration: 1 Dec 2020 → 3 Dec 2020 |
Publication series
| Name | Proceedings - 2020 IEEE 6th International Conference on Collaboration and Internet Computing, CIC 2020 |
|---|
| Conference | 6th IEEE International Conference on Collaboration and Internet Computing, CIC 2020 |
|---|---|
| Country/Territory | United States |
| City | Virtual, Atlanta |
| Period | 1/12/20 → 3/12/20 |
- Internet of Things
- Energy Harvesting
- Recommendation
- Summarization
- Conversational IoT
- IoT Service Discovery
Access to Document
- 10.1109/CIC50333.2020.00015
Other files and links
- Link to publication in Scopus
- ARC grant information
Fingerprint
- Internet of things Engineering & Materials Science 100%
- Machine-to-machine communication Engineering & Materials Science 54%
- Momentum Engineering & Materials Science 36%
- Internet Engineering & Materials Science 27%
Projects per year
Efficient Management of Things for the Future World Wide Web
Sheng, M. & Mans, B.
1/01/17 → …
Project : Research
What Can You Trust in the Large and Noisy Web?
Sheng, M. , Yang, J. , Zhang, W. & Dustdar, S.
1/05/20 → 30/04/23
A Large-Scale Distributed Experimental Facility for the Internet of Things
Sheng, M. , Bouguettaya, A., Loke, S., Li, X., Liang, W., Benattalah, B., Ali Babar, M., Yang, J. , Zomaya, A. Y., Wang, Y. , Zhou, W., Yao, L., Taylor, K. & Bergmann, N.
1/01/18 → 31/12/20
T1 - The 10 research topics in the Internet of Things
AU - Zhang, Wei Emma
AU - Sheng, Quan Z.
AU - Mahmood, Adnan
AU - Tran, Dai Hoang
AU - Zaib, Munazza
AU - Hamad, Salma Abdalla
AU - Aljubairy, Abdulwahab
AU - Alhazmi, Ahoud Abdulrahmn F.
AU - Sagar, Subhash
AU - Ma, Congbo
N2 - Since the term first coined in 1999 by Kevin Ashton, the Internet of Things (IoT) has gained significant momentum as a technology to connect physical objects to the Internet and to facilitate machine-to-human and machine-to-machine communications. Over the past two decades, IoT has been an active area of research and development endeavors by many technical and commercial communities. Yet, IoT technology is still not mature and many issues need to be addressed. In this paper, we identify 10 key research topics and discuss the research problems and opportunities within these topics.
AB - Since the term first coined in 1999 by Kevin Ashton, the Internet of Things (IoT) has gained significant momentum as a technology to connect physical objects to the Internet and to facilitate machine-to-human and machine-to-machine communications. Over the past two decades, IoT has been an active area of research and development endeavors by many technical and commercial communities. Yet, IoT technology is still not mature and many issues need to be addressed. In this paper, we identify 10 key research topics and discuss the research problems and opportunities within these topics.
KW - Internet of Things
KW - Energy Harvesting
KW - Recommendation
KW - Search
KW - Summarization
KW - Conversational IoT
KW - IoT Service Discovery
UR - http://www.scopus.com/inward/record.url?scp=85100752198&partnerID=8YFLogxK
UR - http://purl.org/au-research/grants/arc/DP200102298
UR - http://purl.org/au-research/grants/arc/LE180100158
UR - http://purl.org/au-research/grants/arc/FT140101247
U2 - 10.1109/CIC50333.2020.00015
DO - 10.1109/CIC50333.2020.00015
M3 - Conference proceeding contribution
AN - SCOPUS:85100752198
T3 - Proceedings - 2020 IEEE 6th International Conference on Collaboration and Internet Computing, CIC 2020
BT - Proceedings - 2020 IEEE 6th International Conference on Collaboration and Internet Computing, CIC 2020
PB - Institute of Electrical and Electronics Engineers (IEEE)
CY - Piscataway, NJ
T2 - 6th IEEE International Conference on Collaboration and Internet Computing, CIC 2020
Y2 - 1 December 2020 through 3 December 2020
Help | Advanced Search
Computer Science > Distributed, Parallel, and Cluster Computing
Title: the 10 research topics in the internet of things.
Abstract: Since the term first coined in 1999 by Kevin Ashton, the Internet of Things (IoT) has gained significant momentum as a technology to connect physical objects to the Internet and to facilitate machine-to-human and machine-to-machine communications. Over the past two decades, IoT has been an active area of research and development endeavours by many technical and commercial communities. Yet, IoT technology is still not mature and many issues need to be addressed. In this paper, we identify 10 key research topics and discuss the research problems and opportunities within these topics.
| Comments: | 10 pages. IEEE CIC 2020 vision paper |
| Subjects: | Distributed, Parallel, and Cluster Computing (cs.DC) |
| Cite as: | [cs.DC] |
| (or [cs.DC] for this version) | |
| Focus to learn more arXiv-issued DOI via DataCite |
Submission history
Access paper:.
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
DBLP - CS Bibliography
Bibtex formatted citation.
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
The 10 Research Topics in the Internet of Things
Since the term first coined in 1999 by Kevin Ashton, the Internet of Things (IoT) has gained significant momentum as a technology to connect physical objects to the Internet and to facilitate machine-to-human and machine-to-machine communications. Over the past two decades, IoT has been an active area of research and development endeavours by many technical and commercial communities. Yet, IoT technology is still not mature and many issues need to be addressed. In this paper, we identify 10 key research topics and discuss the research problems and opportunities within these topics.
Please sign up or login with your details
Generation Overview
AI Generator calls
AI Video Generator calls
AI Chat messages
Genius Mode messages
Genius Mode images
AD-free experience
Private images
- Includes 500 AI Image generations, 1750 AI Chat Messages, 30 AI Video generations, 60 Genius Mode Messages and 60 Genius Mode Images per month. If you go over any of these limits, you will be charged an extra $5 for that group.
- For example: if you go over 500 AI images, but stay within the limits for AI Chat and Genius Mode, you'll be charged $5 per additional 500 AI Image generations.
- Includes 100 AI Image generations and 300 AI Chat Messages. If you go over any of these limits, you will have to pay as you go.
- For example: if you go over 100 AI images, but stay within the limits for AI Chat, you'll have to reload on credits to generate more images. Choose from $5 - $1000. You'll only pay for what you use.
Out of credits
Refill your membership to continue using DeepAI
Share your generations with friends

Top 40 IoT Research Topics for 2024 [With Source Code]
Home Blog others Top 40 IoT Research Topics for 2024 [With Source Code]
With new applications being created every day, the Internet of Things (IoT) is one of the technologies that is expanding the fastest in the world right now. The Internet of Things (IoT) is a network of physical objects like cars, appliances, and other household things that are equipped with connectivity, software, and sensors to collect and share data. IoT is revolutionizing the way we live and work, creating new opportunities for businesses, governments, and individuals alike.
In this blog, we will discuss the top 40 Internet of Things research topics and ideas for 2024. We will also provide a comprehensive guide on how to choose the best IoT research topic and discuss some of the challenges and ethical considerations in IoT research papers.
To get started, then Web Development Certificate online is one of the best certifications course you can consider.
What is IoT?
IoT has numerous applications in various sectors such as healthcare, agriculture, transportation, manufacturing, and smart cities. The data collected from IoT devices can be used to improve decision-making, optimize processes, and enhance customer experiences. If you want to know more about IoT, check out online IoT training .
List of IoT Research Topics in 2024
Here's a updated list of internet of things research topic ideas of 2024:
1. Smart Homes
2. wearable devices, 3. smart agriculture, 4. smart cities, 5. industrial iot, 6. smart health, 7. smart retail, 8. energy iot, 9. transportation iot.
- Hospitality IoT
- Aerospace IoT
Top IoT Research Projects
Come let’s discuss the top 10 IoT-based research topics and ideas in detail for 2024.
The idea of a smart home is gaining popularity, and with IoT technology, it has become possible to control and automate various devices in a house. Some of the popular smart home projects include smart lighting, smart security, smart thermostat, and smart appliances.
- Smart Lighting: Smart lighting refers to the use of IoT technology to control the lighting of a house. This can be done by using sensors that detect the presence of people in a room and adjust the lighting accordingly. For example, when someone enters a room, the lights automatically turn on, and when the person leaves, the lights turn off. This can aid in energy conservation and lower electricity costs.
- Smart Security: Smart security refers to the use of IoT technology to enhance the security of a house. This can be done by using sensors and cameras that detect any suspicious activity and alert the homeowners. Smart security can also include features such as remote access control, automatic locking, and real-time monitoring.
- Smart Thermostat: Smart thermostat refers to the use of IoT technology to control the temperature of a house. This can be done by using sensors that detect the temperature of each room and adjust the thermostat accordingly. The ability to remotely operate a smart thermostat can aid in energy conservation and lower electricity costs.
Wearable devices such as smartwatches, fitness trackers, and medical devices are becoming increasingly popular. IoT technology can be used to develop wearable devices that can collect and analyze data, monitor health parameters, and provide real-time feedback to the user.
- Smartwatches: Smartwatches refer to the use of IoT technology to develop watches that can perform various functions such as making phone calls, sending messages, and tracking fitness. Smartwatches can also be integrated with other devices such as smartphones and laptops.
- Fitness Trackers: Fitness trackers refer to the use of IoT technology to develop devices that can track physical activity, monitor heart rate, and measure calories burned. Fitness trackers can be used to improve health and fitness and can also be integrated with other devices such as smartphones and laptops.
- Medical Devices: Medical devices refer to the use of IoT technology to develop devices that can monitor and track various health parameters such as blood pressure, glucose levels, and oxygen saturation. Medical devices can be used to improve patient care and can also be integrated with other devices such as smartphones and laptops.
IoT technology can be used to develop smart agriculture solutions that can improve crop yields, reduce water consumption, and increase efficiency. Some of the popular smart agriculture projects include precision farming, soil monitoring, and crop monitoring.
- Precision Farming: Precision farming refers to the use of IoT technology to develop farming techniques that can help farmers optimize their crop yields. This can be done by using sensors that detect soil moisture, temperature, and nutrient levels, and adjusting the amount of water and fertilizer used accordingly.
- Soil Monitoring: Soil monitoring refers to the use of IoT technology to develop devices that can monitor soil conditions such as pH levels, temperature, and moisture content. Soil monitoring can help farmers make informed decisions about crop management and reduce the amount of water and fertilizer used.
- Crop Monitoring: Crop monitoring refers to the use of IoT technology to develop devices that can monitor crop growth and health. This can be done by using sensors that detect the amount of sunlight, temperature, and humidity, and provide real-time feedback to farmers. Crop monitoring can help farmers identify and address any issues that may affect crop growth and yield.
Smart cities refer to the use of IoT technology to develop cities that are more efficient, sustainable, and livable. Some of the popular smart city projects include smart transportation, smart energy, and smart waste management.
- Smart Transportation: Smart transportation refers to the use of IoT technology to develop transportation solutions that are more efficient and sustainable. This can include features such as real-time traffic monitoring, intelligent traffic routing, and smart parking.
- Smart Energy: Smart energy refers to the use of IoT technology to develop energy solutions that are more efficient and sustainable. This can include features such as smart grids, renewable energy sources, and energy-efficient buildings.
- Smart Waste Management: Smart waste management refers to the use of IoT technology to develop waste management solutions that are more efficient and sustainable. This can include features such as smart bins that detect when they are full and automatically alert waste collection services.
Industrial IoT refers to the use of IoT technology to develop solutions that can improve efficiency and productivity in industries such as manufacturing, transportation, and logistics. Some of the popular industrial IoT projects include predictive maintenance, asset tracking, and supply chain optimization.
- Predictive Maintenance: Predictive maintenance refers to the use of IoT technology to develop maintenance solutions that can detect and address issues before they become major problems. This can include features such as real-time monitoring of machinery and equipment, and predictive analytics that can identify potential issues.
- Asset Tracking: Asset tracking refers to the use of IoT technology to develop solutions that can track the location and status of assets such as machinery and vehicles. This can include features such as real-time tracking, geofencing, and alert notifications.
- Supply Chain Optimization: Supply chain optimization refers to the use of IoT technology to develop solutions that can optimize supply chain operations such as inventory management, logistics, and shipping. This can include features such as real-time tracking of shipments, predictive analytics, and automated inventory management.
Smart health refers to the use of IoT technology to develop solutions that can improve patient care, reduce costs, and enhance overall health outcomes. Some of the popular smart health projects include remote patient monitoring, medication management, and personalized health tracking.
- Remote Patient Monitoring: Remote patient monitoring refers to the use of IoT technology to monitor patients remotely and provide real-time feedback to healthcare providers. This can include features such as wearable devices that monitor vital signs and alert healthcare providers if any issues arise.
- Medication Management: Medication management refers to the use of IoT technology to develop solutions that can help patients manage their medications more effectively. This can include features such as smart pillboxes that remind patients to take their medications and alert healthcare providers if medications are missed.
- Personalized Health Tracking: Personalized health tracking refers to the use of IoT technology to develop solutions that can track and analyze individual health data such as activity levels, sleep patterns, and dietary habits. This can help individuals make informed decisions about their health and well-being.
Smart retail is an emerging application of IoT technology that is changing the way we shop. The goal of smart retail is to provide customers with a more personalized and efficient shopping experience while also improving the efficiency and profitability of retailers. Here are some more details on some popular smart retail applications:
- Smart Shelves: Smart shelves are shelves equipped with IoT sensors that detect when products are running low or out of stock. This data is sent to the retailer's inventory management system, which can then automatically order more inventory. Smart shelves can also be used to display product information, promotions, and customer recommendations.
- Smart Inventory Management: Smart inventory management refers to the use of IoT technology to track inventory levels in real time. This can help retailers to optimise their inventory levels, reduce waste, and avoid stockouts. Smart inventory management can also help retailers to automate their ordering and fulfilment processes.
- Personalized Shopping Experiences: Personalized shopping experiences refer to the use of IoT technology to provide customers with tailored product recommendations and promotions. This can be done by analyzing customer data, such as purchase history and browsing behavior, and using machine learning algorithms to generate personalized recommendations.
The energy industry is also poised for transformation through the use of IoT technology. Energy IoT solutions can help companies optimize energy usage, reduce waste, and improve sustainability. Some project ideas for energy IoT include:
- Smart Grids: A system that uses sensors and data analytics to optimize the distribution of energy, reducing waste and improving efficiency.
- Energy Management: A system that uses sensors to monitor energy usage in buildings, identifying areas where energy usage can be reduced and optimizing the energy usage of appliances and lighting.
- Renewable Energy Monitoring: A system that uses sensors to monitor the performance of renewable energy systems, optimizing energy production and reducing downtime.
IoT technology is also transforming the way we move people and goods. Transportation IoT solutions can help optimize transportation networks, reduce traffic congestion, and improve safety. Some project ideas for transportation IoT include:
- Connected Vehicles: Vehicles that are equipped with sensors and connectivity, allowing them to communicate with each other and with infrastructure to optimize traffic flow and improve safety.
- Intelligent Transportation Systems: A system that uses sensors and data analytics to optimize traffic flow, reducing congestion and improving safety.
- Smart Parking: A system that uses sensors and data analytics to optimize parking availability, reducing search times and improving the parking experience for drivers.
10. Hospitality IoT
IoT technology can help hotels and other hospitality businesses improve the guest experience, increase efficiency, and reduce costs. Some project ideas for hospitality IoT include:
- Smart Room Controls: A system that uses sensors and connectivity to allow guests to control lighting, temperature, and other room features from their smartphones or other devices.
- Asset Tracking: A system that uses sensors to track the location and condition of hotel assets, improving supply chain visibility and reducing the risk of theft or loss.
- Guest Analytics: A system that uses sensors to track guest behavior and preferences, allowing hotels to offer personalized recommendations and improve the guest experience.
11. Aerospace IoT
IoT technology can help aerospace companies improve safety, increase efficiency, and reduce costs. Some project ideas for aerospace IoT include:
- Predictive Maintenance: A system that uses sensors and data analytics to predict when aircraft equipment is likely to fail, allowing for maintenance to be performed before a breakdown occurs.
- Fuel Optimization: A system that uses sensors and data analytics to optimize fuel usage, reducing waste and increasing efficiency.
- Air Traffic Management: A system that uses sensors and data analytics to optimize air traffic flow, reducing congestion and improving safety.
Top Futuristic IoT Research Ideas
- Human-Computer Interaction: Develop interfaces that can interpret human behavior and emotions to enhance IoT systems' responsiveness and personalization.
- Augmented Reality and IoT: Combine IoT with augmented reality to create immersive experiences in areas such as education, entertainment, and marketing.
- Quantum Computing and IoT: Investigate how quantum computing can enhance IoT systems' performance, security, and scalability.
- Swarm Intelligence and IoT: Explore how swarm intelligence can be applied to IoT systems to enable self-organizing and self-healing networks.
- IoT and 5G: Investigate how 5G networks can enhance IoT systems' performance, reliability, and scalability.
- Smart Cities and IoT: Develop smart city solutions that can improve urban planning, transportation, energy efficiency, and citizen engagement.
Generalized Open IoT Research Topics
Here is a generalized open internet of things research paper topics listed based on different categories:
A. IoT Enabling Technologies
- IoT Large-Scale Pilots and Portability
- Sensor and Actuator Networks
- Artificial Intelligence and IoT
- IoT and Personal Data Protection
- IoT Protocols and Standards (IPv6, 6LoWPAN, RPL, 6TiSCH, WoT, oneM2M, etc.)
- Named Data Networking for IoT
B. IoT Applications, Services, and Real Implementations
- e-Health, Assisted Living and e-Wellness
- Smart Grid, Energy Management
- Cyber-physical systems, Context Awareness, Situation Awareness, Ambient Intelligence
- Industrial IoT Service Creation and Management Aspects
C. IoT Security, Privacy, and Data Protection
- Artificial Intelligence-based security and data protection
- Wireless Sensor Network for IoT Security
- IoT Privacy, data protection, and Security Concerns
- Security with QoS Optimization in IoT
- Security Standards in IoT
- Identification and Authentication Issues
D. IoT Pilots, Testbeds, and Experimentation Results
- Large-scale pilots on IoT
- Multi-Objective IoT System Modeling and Analysis—Performance, Energy, Reliability, Robustness
- IoT Interconnections Analysis—QoS, Scalability, Performance, Interference
- IoT Deployment at Government and ISPs
- IoT Interconnections among ISPs Analysis—QoS, Scalability, Performance, Interference
- Gaps Analysis for Real Deployment
- IoT and Future Internet Architectures
How to Choose the Best IoT Research Topic?
Choosing the best IoT research topic can be a challenging task. Here are some tips to help you choose the best IoT research topic:
- Think on how feasible and useful the research is: Choose a topic that aligns with your interests and passions to stay motivated and engaged throughout the research process.
- Identify emerging trends and challenges: Choose a topic that addresses emerging trends and challenges in the IoT industry to make a significant contribution to the field.
- Consider the feasibility and practicality of the research: Choose a topic that is feasible and practical to research given the available resources, expertise, and time constraints.
- Seek input from experts and mentors: Consult with experts and mentors in the field to get feedback and guidance on potential research topics.
- Evaluate the potential impact of the research: Choose a topic that has the potential to make a significant impact on the IoT industry or society as a whole.
Things to Consider While Choosing IoT Research Topics
Here are some additional things to consider while choosing IoT topics for research:
- Ethical considerations: Consider the ethical implications of the research, such as data privacy, security, and transparency.
- Interdisciplinary nature: Consider the interdisciplinary nature of IoT research and seek to collaborate with experts from different fields to broaden the scope of the research.
- Data management: Consider how to manage the massive amount of data generated by IoT devices and ensure the accuracy, reliability, and integrity of the data.
- Scalability: Consider how to design IoT systems that can scale up to accommodate the increasing number of devices and data.
IoT is a rapidly growing field that offers numerous opportunities for research and innovation. In this blog, we discussed the top 40 research topics on IoT for 2024, as well as some futuristic IoT research ideas. We also provided a comprehensive guide on how to choose the best IoT research topic and discussed some of the challenges and ethical considerations in IoT research. By choosing the right research topic and addressing emerging trends and challenges, you can make a significant contribution to the IoT industry and society as a whole. In addition to the project, you can also take advantage of KnowledgeHut Software Development Certification training to learn multiple programming languages and enhance your value in the job market.
Frequently Asked Questions (FAQs)
IoT research involves studying the technologies, applications, and challenges related to the Internet of Things (IoT) to develop new solutions and improve existing ones.
Some current trends in IoT research include edge computing, machine learning and artificial intelligence (AI), security and privacy, and smart cities.
IoT research can be used in industry to develop and improve products and services, optimize processes, and enhance customer experiences. It can also help companies to reduce costs, increase efficiency, and improve safety.
Some ethical considerations in IoT research include privacy, data security, transparency, consent, and the potential for bias or discrimination.
Some challenges in IoT research include interoperability, scalability, data management and analysis, energy efficiency, and the need for standardization and regulation.

Geetika Mathur
Geetika Mathur is a recent Graduate with specialization in Computer Science Engineering having a keen interest in exploring entirety around. She have a strong passion for reading novels, writing and building web apps. She has published one review and one research paper in International Journal. She has also been declared as a topper in NPTEL examination by IIT – Kharagpur.
Avail your free 1:1 mentorship session.
Something went wrong
The 10 Research Topics in the Internet of Things
Total Page: 16
File Type: pdf , Size: 1020Kb
- Abstract and Figures
- Public Full-text
- Internet of Things: a Scientometric Review S S symmetry Article Internet of Things: A Scientometric Review Juan Ruiz-Rosero 1,* ID , Gustavo Ramirez-Gonzalez 1 ID , Jennifer M. Williams 2 ID , Huaping Liu 2, Rahul Khanna 3 ID and Greeshma Pisharody 3 ID 1 Departamento de Telemática, Universidad del Cauca, Popayán, Cauca 190002, Colombia; [email protected] 2 School of Electrical Engineering and Computer Science, Oregon State University, Corvallis, OR 97331, USA; [email protected] (J.M.W.); [email protected] (H.L.) 3 Intel Corporation, 2111 NE 25th Ave., Hillsboro, OR 97124, USA; [email protected] (R.K.); [email protected] (G.P.) * Correspondence: [email protected] ; Tel.: +57-(2)-820-9900 Received: 31 August 2017; Accepted: 23 November 2017; Published: 6 December 2017 Abstract: Internet of Things (IoT) is connecting billions of devices to the Internet. These IoT devices chain sensing, computation, and communication techniques, which facilitates remote data collection and analysis. wireless sensor networks (WSN) connect sensing devices together on a local network, thereby eliminating wires, which generate a large number of samples, creating a big data challenge. This IoT paradigm has gained traction in recent years, yielding extensive research from an increasing variety of perspectives, including scientific reviews. These reviews cover surveys related to IoT vision, enabling technologies, applications, key features, co-word and cluster analysis, and future directions. Nevertheless, we lack an IoT scientometrics review that uses scientific databases to perform a quantitative analysis. This paper develops a scientometric review about IoT over a data set of 19,035 documents published over a period of 15 years (2002–2016) in two main scientific databases (Clarivate Web of Science and Scopus). [Show full text]
- Business Process Management & Enterprise Architecture Track BIO - Bioinformatics Track Track Co-Chairs: Juan Manuel Corchado, University of Salamanca, Spain Paola Lecca, University of Trento, Italy Dan Tulpan, University of Guelph, Canada An Insight into Biological Data Mining based on Rarity and Correlation as Constraints .............................1 Souad Bouasker, University of Tunis ElManar, Tunisia Drug Target Discovery Using Knowledge Graph Embeddings .........................................................................9 Sameh K. Mohamed, Insight Centre for Data Analytics, Ireland Aayah Nounu, University of Bristol, UK Vit Novacek, INSIGHT @ NUI Galway, Ireland Ensemble Feature Selectin for Biomarker Discovery in Mass Spectrometry-based Metabolomics ............17 Aliasghar Shahrjooihaghighi, University of Louisville, USA Hichem Frigui, University of Louisville, USA Xiang Zhang, University of Louisville, USA Xiaoli Wei, University of Louisville, USA Biyun Shi, University of Louisville, USA Craig J. McClain, University of Louisville, USA Molecule Specific Normalization for Protein and Metabolite Biomarker Discovery ....................................23 Ameni Trabelsi, University of Louisville, USA Biyun Shi, University of Louisville, USA Xiaoli Wei, University of Louisville, USA HICHEM FRIGUI, University of Louisville, USA Xiang Zhang, University of Louisville, USA Aliasghar Shahrajooihaghighi, University of Louisville, USA Craig McClain, University of Louisville, USA BPMEA - Business Process Management & Enterprise Architecture Track Track Co-Chairs: Marco Brambilla, Politecnico di [Show full text]
- Exploring Internet of Things, Mobile Computing and Ubiquitous Computing in Computer Science Education: a Systematic Mapping Study www.ijtes.net Exploring Internet of Things, Mobile Computing and Ubiquitous Computing in Computer Science Education: A Systematic Mapping Study Olga Fragou1, Anna Mavroudi2 1Hellenic Open University, Greece 2Νorwegian University of Science & Technology, Norway To cite this article: Fragou, O. & Mavroudi, A. (2020). Exploring internet of things, mobile computing and ubiquitous computing in computer science education: A systematic mapping study. International Journal of Technology in Education and Science (IJTES), 4(1), 72-85. The International Journal of Technology in Education and Science (IJTES) is a peer-reviewed scholarly online journal. This article may be used for research, teaching, and private study purposes. Authors alone are responsible for the contents of their articles. The journal owns the copyright of the articles. The publisher shall not be liable for any loss, actions, claims, proceedings, demand, or costs or damages whatsoever or howsoever caused arising directly or indirectly in connection with or arising out of the use of the research material. All authors are requested to disclose any actual or potential conflict of interest including any financial, personal or other relationships with other people or organizations regarding the submitted work. International Journal of Technology in Education and Science Volume 4, Issue 1, Winter 2020 ISSN: 2651-5369 Exploring Internet of Things, Mobile Computing and Ubiquitous Computing in Computer Science Education: A Systematic Mapping Study Olga Fragou, Anna Mavroudi Article Info Abstract Article History Ubiquitous computing, mobile computing and the Internet of Things (UMI) have been widely used in several application areas. To date, methods and techniques Received: for the application of these technologies in real life situations have continued to 17 June 2019 emerge; however, their use in education settings focusing on existing practices remain largely underexplored. [Show full text]
- Internet of Nano-Things, Things and Everything: Future Growth Trends future internet Review Internet of Nano-Things, Things and Everything: Future Growth Trends Mahdi H. Miraz 1 ID , Maaruf Ali 2, Peter S. Excell 3,* and Richard Picking 3 1 Centre for Financial Regulation and Economic Development (CFRED), The Chinese University of Hong Kong, Sha Tin, Hong Kong, China; [email protected] 2 International Association of Educators and Researchers (IAER), Kemp House, 160 City Road, London EC1V 2NX, UK; [email protected] 3 Faculty of Art, Science and Technology, Wrexham Glyndwrˆ University, Wrexham LL11 2AW, UK; [email protected] * Correspondence: [email protected] ; Tel.: +44-797-480-6644 Received: 22 June 2018; Accepted: 25 July 2018; Published: 28 July 2018 Abstract: The current statuses and future promises of the Internet of Things (IoT), Internet of Everything (IoE) and Internet of Nano-Things (IoNT) are extensively reviewed and a summarized survey is presented. The analysis clearly distinguishes between IoT and IoE, which are wrongly considered to be the same by many commentators. After evaluating the current trends of advancement in the fields of IoT, IoE and IoNT, this paper identifies the 21 most significant current and future challenges as well as scenarios for the possible future expansion of their applications. Despite possible negative aspects of these developments, there are grounds for general optimism about the coming technologies. Certainly, many tedious tasks can be taken over by IoT devices. However, the dangers of criminal and other nefarious activities, plus those of hardware and software errors, pose major challenges that are a priority for further research. Major specific priority issues for research are identified. [Show full text]
- Advancing the Industrial Internet of Things Advancing the Industrial Internet of Things An Industrial Internet Consortium and oneM2M™ Joint Whitepaper Authors Amar Deol (Huawei), Ken Figueredo (InterDigital Inc.), Shi-Wan Lin (Yo-i), Brett Murphy (RTI), Dale Seed (Convida Wireless), Jason Yin (Huawei) Editors Shi-Wan Lin (Yo-i) and Ken Figueredo (InterDigital Inc.) Contributors1 Josef Blanz (Qualcomm), Omar Elloumi (Nokia), Rajive Joshi (RTI), Peter Klement (XMPro), Sam Bhattarai (Toshiba), Atte Lansisalmi (Nokia) and Chuck Byers (IIC) 2019-12-12 1 Individuals who have provided valuable comments and inputs that have substantially improved the quality of this whitepaper. - i - 1 Context for Collaboration .................................................................................................. 1 2 Organizational Overviews ................................................................................................. 2 2.1 Overview of the IIC .............................................................................................................. 2 2.2 Overview of oneM2MTM....................................................................................................... 3 3 Alignment Between IIRA and oneM2M Architecture Frameworks ...................................... 6 3.1 IIC’s IIRA .............................................................................................................................. 7 3.2 oneM2M Architecture and Common Services Layer .............................................................. 9 3.2.1 Common Service Layer Functions [Show full text]
- Case Studies in Iot -Smart-Home Solutions Pedagogical Perspective Case Studies in IoT -Smart-Home Solutions Pedagogical Perspective with Industrial Applications and some latest Developments Hans-Petter Halvorsen, Alexander Jonsaas, Saba Mylvaganam, Josef Timmerberg, Jean-Marc Thiriet To cite this version: Hans-Petter Halvorsen, Alexander Jonsaas, Saba Mylvaganam, Josef Timmerberg, Jean-Marc Thiriet. Case Studies in IoT -Smart-Home Solutions Pedagogical Perspective with Industrial Applications and some latest Developments. EAEEIE 2017 - 27th EAEEIE Annual Conference on Innovation in Education for Electrical and Information Engineering, Jun 2017, Grenoble, France. hal-01658856 HAL Id: hal-01658856 https://hal.archives-ouvertes.fr/hal-01658856 Submitted on 7 Dec 2017 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Case Studies in IoT - Smart-Home Solutions Pedagogical Perspective with Industrial Applications and some latest Developments Hans-Petter Halvorsen, Alexander Jonsaas, Saba Josef Timmerberg Mylvaganam Jade University of Applied Sciences, D-26389 Wilhelmshaven, [email protected] ; Faculty of Technology, Department [Show full text]
- Recommending Privacy Settings for Internet-Of-Things Clemson University TigerPrints All Dissertations Dissertations December 2019 Recommending Privacy Settings for Internet-of-Things Yangyang He Clemson University, [email protected] Follow this and additional works at: https://tigerprints.clemson.edu/all_dissertations Recommended Citation He, Yangyang, "Recommending Privacy Settings for Internet-of-Things" (2019). All Dissertations. 2528. https://tigerprints.clemson.edu/all_dissertations/2528 This Dissertation is brought to you for free and open access by the Dissertations at TigerPrints. It has been accepted for inclusion in All Dissertations by an authorized administrator of TigerPrints. For more information, please contact [email protected] . Recommending Privacy Settings for Internet-of-Things A Dissertation Presented to the Graduate School of Clemson University In Partial Fulfillment of the Requirements for the Degree Doctor of Philosophy Computer Science by Yang He December 2019 Accepted by: Dr. Bart P. Knijnenburg, Committee Chair Dr. Larry F. Hodges Dr. Alexander Herzog Dr. Ilaria Torre Abstract Privacy concerns have been identified as an important barrier to the growth of IoT. These concerns are exacerbated by the complexity of manually setting privacy preferences for numerous different IoT devices. Hence, there is a demand to solve the following, urgent research question: How can we help users simplify the task of managing privacy settings for IoT devices in a user-friendly manner so that they can make good privacy decisions? To solve this problem in the IoT domain, a more fundamental understanding of the logic behind IoT users' privacy decisions in different IoT contexts is needed. We, therefore, conducted a series of studies to contextualize the IoT users' decision-making characteristics and designed a set of privacy-setting interfaces to help them manage their privacy settings in various IoT contexts based on the deeper understanding of users' privacy decision behaviors. [Show full text]
- Indoor Air Quality Monitoring Sensor for the Web of Things † Proceedings Indoor Air Quality Monitoring Sensor for the Web of Things † Daniel Ibaseta 1, Julio Molleda 2,*, Fidel Díez 1 and Juan C. Granda 2 1 CTIC Technological Centre, 33203 Gijón, Spain; [email protected] (D.I.); [email protected] (F.D.) 2 Department of Computer Science and Engineering, University of Oviedo, 33204 Gijón, Spain; [email protected] * Correspondence: [email protected] ; Tel.: +34-985-182-518 † Presented at 2nd International Research Conference on Sustainable Energy Engineering, Materials and Environment, Mieres, Spain, 25–27 July 2018. Published: 14 November 2018 Abstract: Many Internet of Things platforms use dedicated software coupled with proprietary devices and interfaces, creating silo solutions with no interoperability. The Web of Things paradigm promotes using open Web standards to connect physical objects to the Internet through an application layer. In this paper, we propose a low-cost, indoor air quality monitoring sensor implementing a minimal servient building block recommended by the Web of Things Working Group of the World Wide Web Consortium. The proposed sensor runs a Web server on a low-power system-on-chip microcontroller, which provides temperature, relative humidity and carbon dioxide measurements to the Internet through a REST API. Any client on the Internet able to manage the HTTP protocol may access this sensor, making it compatible with any air quality monitoring platform that uses HTTP. Keywords: IoT; WoT; REST API; air quality monitoring; SoC microcontroller 1. Introduction Embedded computing and low-power wireless communication provide physical objects with Internet connectivity, forming the Internet of Things (IoT) [1]. The IoT offers services that lay at the core of many fields, such as smart homes, smart cities, smart industries and smart agriculture. [Show full text]
- Table of Contents Table of Contents Scroll to the title and select a Blue link to open a paper. After viewing the paper, use the bookmarks to the left to return to the beginning of the Table of Contents. Theme: AI and Agents BIO - Bioinformatics Track Track Co-Chairs: Paola Lecca, University of Trento, Italy Dan Tulpan, University of Guelph, Canada Juan Manuel Corchado, University of Salamanca, Spain Track Editorial ..................................................................................................................................................... 1 An Insight into Biological Data Mining based on Rarity and Correlation as Constraints ........................... 3 Souad Bouasker, University of Tunis ElManar, Tunisia Sadok Ben Yahia, Tallinn University of Technology, Estonia Gayo Diallo, University of Bordeaux, France Drug Target Discovery using Knowledge Graph Embeddings ..................................................................... 11 Sameh K. Mohamed, National University of Ireland Galway, Ireland Aayah Nounu, University of Bristol, UK Vit Nováček, National University of Ireland Galway, Ireland Ensemble Feature Selectin for Biomarker Discovery in Mass Spectrometry-based Metabolomics .......... 19 AliAsghar ShahrjooiHaghighi, University of Louisville, USA Hichem Frigui, University of Louisville, USA Xiang Zhang, University of Louisville, USA Xiaoli Wei, University of Louisville, USA Biyun Shi, University of Louisville, USA Craig J. McClain, University of Louisville, USA Molecule Specific Normalization for Protein and Metabolite Biomarker [Show full text]
- A Wot Testbed for Research and Course Projects 6 CHAPTER A WOT TESTBED FOR RESEARCH AND COURSE PROJECTS 6 Mina Younan ∗, Sherif Khattab †, Reem Bahgat † Computer Science Department, Minia University, Minia, Egypt ∗ Computer Science Department, Cairo University, Cairo, Egypt † 6.1 WHAT YOU NEED TO GET STARTED The main objective of this chapter is to gain the required practical knowledge and skills for building simple physical testbeds for the WoT, which integrates the real world into the digital world. Concrete steps for building a WoT testbed are presented in the form of four experiments and a mini-project. Testbed evaluation is out of the scope of this chapter; our work elsewhere [1] discusses evaluation of an integrated WoT testbed. This chapter focuses on the interaction between microcontrollers, sen- sors, actuators, and PCs using HTTP and Zigbee protocols. The required platforms and devices for running examples in this chapter are as follows: • Platforms : C#, ASP.net, and Arduino programming language. • Devices: Examples in this chapter are for WoT-based smart home applications and will use the components listed in Table 6.1 . 6.2 INTRODUCTION Augmenting everyday’s objects (e.g., light bulbs, curtains, and appliances) with em- bedded computers or visual markers (e.g., LEDs and small LCD displays) allows things and information about them to be digitally accessible through the Web or mobile phones [1,2] . They become the Internet’s interface to the physical world by converging the physical world into digital world [3,4] . With a partial lack of efficient and scalable communication standards, the number of devices connected to the In- ternet will increase rapidly as soon as IP becomes the core standard in the field of embedded devices. [Show full text]
- Context Aware Computing for the Internet of Things: a Survey IEEE COMMUNICATIONS SURVEYS & TUTORIALS, VOL. X, NO. X, XXXX XXXX 1 Context Aware Computing for The Internet of Things: A Survey Charith Perera, Student Member, IEEE, Arkady Zaslavsky, Member, IEEE, Peter Christen, and Dimitrios Georgakopoulos, Member, IEEE Abstract—As we are moving towards the Internet of Things discuss briefly in Section III. The definitions for ‘context’ and (IoT), the number of sensors deployed around the world is ‘context-awareness’ that are widely accepted by the research growing at a rapid pace. Market research has shown a significant community today were proposed by Abowd et al. [3] in 1999. growth of sensor deployments over the past decade and has predicted a significant increment of the growth rate in the During the last two decades, researchers and engineers future. These sensors continuously generate enormous amounts have developed a significant amount of prototypes, systems, of data. However, in order to add value to raw sensor data and solutions using context-aware computing techniques. Even we need to understand it. Collection, modelling, reasoning, and though the focus varied depending on each project, one aspect distribution of context in relation to sensor data plays critical remained fairly unchanged: that is the number of data sources role in this challenge. Context-aware computing has proven to be successful in understanding sensor data. In this paper, we (e.g. software and hardware sources). For example, most of survey context awareness from an IoT perspective. We present the proposed solutions collect data from a limited number of the necessary background by introducing the IoT paradigm and physical (hardware) and virtual (software) sensors. [Show full text]
- A Survey on Internet of Things Architectures Journal of King Saud University – Computer and Information Sciences (2016) xxx, xxx–xxx King Saud University Journal of King Saud University – Computer and Information Sciences www.ksu.edu.sa www.sciencedirect.com A survey on Internet of Things architectures P.P. Ray Department of Computer Applications, Sikkim University, Sikkim 737102, India Received 4 July 2016; revised 24 September 2016; accepted 3 October 2016 KEYWORDS Abstract Internet of Things is a platform where every day devices become smarter, every day pro- Internet of Things (IoT); cessing becomes intelligent, and every day communication becomes informative. While the Internet Architecture; of Things is still seeking its own shape, its effects have already stared in making incredible strides as Cyber physical system a universal solution media for the connected scenario. Architecture specific study does always pave the conformation of related field. The lack of overall architectural knowledge is presently resisting the researchers to get through the scope of Internet of Things centric approaches. This literature surveys Internet of Things oriented architectures that are capable enough to improve the under- standing of related tool, technology, and methodology to facilitate developer’s requirements. Directly or indirectly, the presented architectures propose to solve real-life problems by building and deployment of powerful Internet of Things notions. Further, research challenges have been investigated to incorporate the lacuna inside the current trends of architectures to motivate the aca- demics and industries get involved into seeking the possible way outs to apt the exact power of Internet of Things. A main contribution of this survey paper is that it summarizes the current state-of-the-art of Internet of Things architectures in various domains systematically. [Show full text]

The Internet of Things (IoT) refers to a network of physical devices, vehicles, appliances, and other physical objects that are embedded with sensors, software, and network connectivity, allowing them to collect and share data.
IoT devices—also known as “smart objects”—can range from simple “smart home” devices like smart thermostats, to wearables like smartwatches and RFID-enabled clothing, to complex industrial machinery and transportation systems. Technologists are even envisioning entire “smart cities” predicated on IoT technologies.
IoT enables these smart devices to communicate with each other and with other internet-enabled devices. Like smartphones and gateways, creating a vast network of interconnected devices that can exchange data and perform various tasks autonomously. This can include:
- monitoring environmental conditions in farms
- managing traffic patterns with smart cars and other smart automotive devices
- controlling machines and processes in factories
- tracking inventory and shipments in warehouses
The potential applications of IoT are vast and varied, and its impact is already being felt across a wide range of industries, including manufacturing, transportation, healthcare, and agriculture. As the number of internet-connected devices continues to grow, IoT is likely to play an increasingly important role in shaping our world. Transforming the way that we live, work, and interact with each other.
In an enterprise context, IoT devices are used to monitor a wide range of parameters such as temperature, humidity, air quality, energy consumption, and machine performance. This data can be analyzed in real time to identify patterns, trends, and anomalies that can help businesses optimize their operations and improve their bottom line.
With ESG disclosures starting as early as 2025 for some companies, make sure that you're prepared with our guide.
Register for the playbook on smarter asset management
IoT is important for business for several reasons. Here are the core benefits of IoT:
By using IoT devices to automate and optimize processes, businesses can improve efficiency and productivity. For example, IoT sensors can be used to monitor equipment performance and detect or even resolve potential issues before they cause downtime, reducing maintenance costs and improving uptime.
IoT devices generate vast amounts of data that can be used to make better-informed business decisions and new business models. By analyzing this data, businesses can gain insights into customer behavior, market trends, and operational performance, allowing them to make more informed decisions about strategy, product development, and resource allocation.
By reducing manual processes and automating repetitive tasks, IoT can help businesses reduce costs and improve profitability. For example, IoT devices can be used to monitor energy usage and optimize consumption, reducing energy costs and improving sustainability.
By using IoT technology to gather data about customer behavior, businesses can create more personalized and engaging experiences for their customers. For example, retailers can use IoT sensors to track customer movements in stores and deliver personalized offers based on their behavior.
Several technologies come together to make IoT possible.
- Sensors and actuators: Sensors are devices that can detect changes in the environment, such as temperature, humidity, light, motion, or pressure. Actuators are devices that can cause physical changes in the environment, such as opening or closing a valve or turning on a motor. These devices are at the heart of IoT, as they allow machines and devices to interact with the physical world. Automation is possible when sensors and actuators work to resolve issues without human intervention.
- Connectivity technologies: To transmit IoT data from sensors and actuators to the cloud, IoT devices need to be connected to the internet. There are several connectivity technologies that are used in IoT, including wifi, Bluetooth, cellular, Zigbee, and LoRaWAN.
- Cloud computing: The cloud is where the vast amounts of data that is generated by IoT devices are stored, processed, and analyzed. Cloud computing platforms provide the infrastructure and tools that are needed to store and analyze this data, as well as to build and deploy IoT applications.
- Big data analytics: To make sense of the vast amounts of data generated by IoT devices, businesses need to use advanced analytics tools to extract insights and identify patterns. These tools can include machine learning algorithms, data visualization tools and predictive analytics models.
- Security and privacy technologies: As IoT deployments become more widespread, IoT security and privacy become increasingly important. Technologies such as encryption , access controls and intrusion detection systems are used to protect IoT devices and the data they generate from cyberthreats.
In the healthcare industry, IoT devices can be used to monitor patients remotely and collect real-time data on their vital signs, such as heart rate, blood pressure and oxygen saturation. This sensor data can be analyzed to detect patterns and identify potential health issues before they become more serious. IoT devices can also be used to track medical equipment, manage inventory and monitor medication compliance.
Industrial IoT devices can be used in manufacturing to monitor machine performance, detect equipment failures and optimize production processes. For example, sensors can be used to monitor the temperature and humidity in a manufacturing facility, ensuring that conditions are optimal for the production of sensitive products. IoT devices can also be used to track inventory, manage supply chains and monitor the quality of finished products. Industrial IoT is such an expansive new technology space, that it is sometimes referred to by its own abbreviation: IIoT (Industrial IoT).
In the retail industry, IoT devices can be used to track customer behavior, monitor inventory levels and optimize store layouts. For example, sensors can be used to track foot traffic in a store and analyze customer behavior, allowing retailers to optimize product placement and improve the customer experience. IoT devices can also be used to monitor supply chains, track shipments and manage inventory levels.
IoT devices can be used in agriculture to monitor soil conditions, weather patterns and crop growth. For example, sensors can be used to measure the moisture content of soil, ensuring that crops are irrigated at the optimal time. IoT devices can also be used to monitor livestock health, track equipment and manage supply chains. Low-power or solar-powered devices can often be used with minimal oversight in remote locations.
In the transportation industry, IoT devices can be used to monitor vehicle performance, optimize routes, and track shipments. For example, sensors can be used to monitor the fuel efficiency of connected cars, reducing fuel costs and improving sustainability. IoT devices can also be used to monitor the condition of cargo, ensuring that it arrives at its destination in optimal condition.
IoT offers many benefits, but it also poses several risks and challenges. Here are some of the most significant ones:
Security and privacy risks: As IoT devices become more widespread, security and privacy become increasingly important. Many IoT devices are vulnerable to hackers and other cyberthreats, which can compromise the security and privacy of sensitive data. IoT devices can also collect vast amounts of personal data, raising concerns about privacy and data protection.
Interoperability issues: IoT devices from different manufacturers often use different standards and protocols, making it difficult for them to perform what’s called “machine to machine” communication. This can lead to interoperability issues and create silos of data that are difficult to integrate and analyze.
Data overload: IoT devices generate vast amounts of data, which can overwhelm businesses that are not prepared to handle it. Analyzing this data and extracting meaningful insights can be a significant challenge, especially for businesses that lack the necessary analytics tools and expertise.
Cost and complexity: Implementing an IoT system can be costly and complex, requiring significant investments in hardware, software, and infrastructure. Managing and maintaining an IoT system can also be challenging, requiring specialized skills and expertise.
Regulatory and legal challenges: As IoT devices become more widespread, regulatory, and legal challenges are emerging. Businesses need to comply with various data protection, privacy and cybersecurity regulations, which can vary from country to country.
Managing IoT devices can be a complex and challenging task, but there are several best practices that businesses can follow to ensure that their IoT devices are secure, reliable, and optimized for performance. Here are some tips for managing IoT devices:
Plan your IoT strategy: Before deploying any IoT devices, businesses should have a clear understanding of their objectives, use cases and desired outcomes. This can help them choose the right devices, IoT platforms and technologies, and ensure that their IoT strategy is aligned with their business goals.
Choose secure IoT products: Security is a critical consideration for IoT solutions, as they can be vulnerable to cyberattacks. Businesses should choose devices that are designed with security in mind and implement appropriate security systems, such as encryption, authentication, and access controls.
Monitor and maintain devices: IoT devices need to be monitored and maintained regularly to ensure that they are performing optimally and are not vulnerable to security threats. This can involve monitoring device health and performance, updating firmware and software and conducting regular security audits and predictive maintenance.
Manage data effectively: IoT devices generate vast amounts of real-world data, which can be challenging to manage and analyze. Businesses should have a clear data management strategy in place, including data storage, analysis, and visualization. To ensure that they can extract meaningful insights from the data that is generated by their IoT devices.
Build an ecosystem: IoT devices are often part of a larger ecosystem that includes other devices, platforms, and technologies. Businesses should have a clear understanding of this ecosystem and ensure that their IoT devices can integrate effectively with other systems and technologies.
The future of IoT is promising, with many exciting developments for businesses on the horizon. Here are some of the trends and predictions for the future of IoT:
Growth: The number of IoT devices is expected to continue to grow rapidly, with estimates suggesting that there will be tens of billion IoT devices in use over the next few years. This growth will be driven by increased adoption across industries, as well as the development of new use cases and applications.
Edge computing: Edge computing is becoming increasingly important for IoT, as it allows data to be processed and analyzed closer to the source of the data, rather than in a centralized data center. This can improve response times, reduce latency and reduce the amount of data that needs to be transferred over IoT networks.
Artificial intelligence and machine learning: AI and machine learning are becoming increasingly important for IoT, as they can be used to analyze vast amounts of data that is generated by IoT devices and extract meaningful insights. This can help businesses make more informed decisions and optimize their operations.
Blockchain: Blockchain technology is being explored as a way to improve security and privacy in the IoT. Blockchain can be used to create secure, decentralized networks for IoT devices, which can minimize data security vulnerabilities.
Sustainability: Sustainability is becoming an increasingly important consideration for IoT, as businesses look for ways to reduce their environmental impact. IoT can be used to optimize energy usage, reduce waste and improve sustainability across a range of industries.
The future of IoT is exciting, with many new developments and innovations on the horizon, with providers of devices offering attractive pricing, as the cost of IoT device production declines. As the number of IoT devices continues to grow, businesses need to be prepared to adapt to new technologies and embrace new use cases and applications. Those that are able to do so will be positioned to reap the benefits of this transformative technology.
Intelligent asset management, monitoring, predictive maintenance and reliability in a single platform.
Enhance your application performance monitoring to provide the context you need to resolve incidents faster.
Compose and extend apps that take advantage of data and analytics from your connected devices and sensors.
This brewery used AI technology from IBM to improve their processes and minimize waste.
By applying Watson IoT to their manufacturing shops, L’Oreal was able to maximize flexibility, agility and product quality.
Powered by AI and IoT data, connected and intelligent assets can optimize performance, adapt to changing circumstances, and help ensure continuity.
The IoT journey has evolved over the last several years.; let's look at the four steps every organization needs to master to truly realize value from their IoT efforts.
This blog explores why data management is key to a viable IoT strategy, and how you can take the first steps in managing the data tidal wave.
Developers who want to make the most of the opportunities of IoT should foster skills across a range of key topic areas.
Unlock the full potential of your enterprise assets with IBM Maximo Application Suite by unifying maintenance, inspection and reliability systems into one platform. It’s an integrated cloud-based solution that harnesses the power of AI, IoT and advanced analytics to maximize asset performance, extend asset lifecycles, minimize operational costs and reduce downtime.
FIELD GRAND CHALLENGE article
Revisiting the internet of things: new trends, opportunities and grand challenges.

- 1 IoT Research Lab, ECSE, Ontario Tech University, Oshawa, ON, Canada
- 2 Cloud Computing and Distributed Systems (CLOUDS) Laboratory, School of Computing and Information Systems, University of Melbourne, Parkville, VIC, Australia
1 Introduction
The Internet of Things (IoT) is a conceptual paradigm that connects billions of Internet-enabled devices to exchange data among themselves and their surroundings to enable smart interactions and connect the physical infrastructure to digital systems. IoT represents a revolutionary paradigm that started to affect our lives in many positive ways. The term Internet of Things was first coined in 1999 by Kevien Ashton ( Ashton, 2009 ) and was initially designed to support RFID technology. However, nowadays IoT has reached far beyond its designers’ vision and become much popular for the new applications it opens up in many vital domains like healthcare, intelligent transportation, public safety, home automation, smart city, asset monitoring, industrial automation and much more. The evolution of IoT presented the long-awaited promise of ubiquitous data access in which people wanted to have access to real-time data on the go anywhere and anytime.
Even though there are many other relevant paradigms/model that intersect with the purpose of IoT (e.g., M2M: Machine to Machine), Web of Things, Internet of Everything (IoE), pervasive computing, etc. ), there are fundamental differences between them and IoT. The core values of IoT lies in the promise of helping businesses to increase their productivity, enhance control over their assets, and make informed business decisions based on the inference resulting from the processing of the fusion of big raw data acquired from the surroundings, including people themselves. Recent research statistics reveal over 10 billion connected IoT devices in 2021. This number is anticipated to reach 41 billion in 2027, expecting over 152,000 IoT devices to connect to the Internet per minute in 2025. Considering the global IoT market size, there was a 22% increase in the market size of IoT in 2021, hitting $157.9 billion. Smart home devices are the dominant components of IoT. The penetration rate of IoT varies concerning the application domain. For example, IoT analytics ( Lueth, 2020 ) argues that industrial applications occupy 22% of the global IoT projects, with transportation, energy, and healthcare occupying 15%, 14%, and 9%, respectively.
The main two types of devices that make up the most of IoT are: Sensors and Actuators. Sensors are physical devices that can sense/measure a certain phenomena and can communicate the sensed values to other parties (i.e., collect data and report internal states). A GPS and an ECG device are examples of IoT sensors. The constituent sensor nodes usually utilize small-scale embedded systems to achieve the cost-effectiveness criteria of IoT solutions, increasing their deployment in various domains. Sensor nodes often use 8-bit microcontrollers and inhibit small storage capacity, lowering their power sizing and allowing them to run for years on batteries. Coupled with the diversified networking protocols available to match the existing infrastructure or the operational conditions, this highly promotes the deployment of IoT solutions in different domains. Actuators are also physical devices that can affect a change on the physical environments (i.e., take actions) in response to a command or a recommendation such as an AC thermostat and a valve. These devices need to be connected to the Internet and are able to communicate to send or receive data so they can qualify as IoT devices.
The convergence of IoT, advanced data analytics and artificial intelligence opened up the door for the next generation of applications that support real-time decision making such as improved user experience and predictive maintenance. As such, data analytics has become a core component of any IoT deployment and will continue to gain popularity and relevance to businesses as much as data collection continues to grow and support intelligent decision making. In industrial manufacturing, for example, predictive maintenance can predict when maintenance is required in advance through the measurement of vibration levels, heat and other parameters to avoid production disruption. IoT data can also reveal rich information about customer behaviors (e.g., driving habits and shopping preferences) to support improved customer experience. Machine learning models and artificial intelligence techniques can learn from observations (IoT data collection) and recommend actions that lead into smart decisions (IoT actuation).
Although IoT promises to support intelligence decision making, enable better quality of life to citizens and make transformative changes in their daily lives, there remain grand challenges that hinder IoT from reaching its full potential such as privacy and security concerns, data heterogeneity and device interoperability, unrestricted access control and deployment in the open access domain. The heterogeneity and small footprint of IoT of sensors for example, comes with two major shortcomings: 1) The constraints of resources available on the sensor nodes render it infeasible to apply the conventional security mechanisms typically involved in capable computer systems, exposing the sensor nodes as a weak security point for the whole IoT system. 2) The many networking protocols available to communicate sensed information among IoT devices result in interoperability issues between IoT systems utilizing different communication protocols.
The first shortcoming of incapable sensor nodes results in the notorious “vertical silos,” where an IoT system is, in fact, a set of subsystems that lack information sharing among each other. That did not represent a significant concern at the early ages of IoT since the applications were relatively limited, and the IoT had not reached its maturity and big vision yet. However, the advent of cloud computing in the last decade, coupled with the advancements in artificial intelligence and its subdomains, has vowed the prospect of IoT in various domains. This necessitates the ability of collaborative IoT systems to build better-informed business decisions based on the fusion of inferences coming from multiple systems. However, the second shortcoming of IoT impedes the scalability of IoT systems, confining the usability of sensed information by IoT systems to the managed networks of their users without exposing this information to public networks. This comes at the cost of increased IoT systems outlay, unwanted redundancy of the same information sensed by non-interoperable systems, expanded storage footprint, high network bandwidth utilization, risen processing cost, and more elevated system latency. This paper provides deep analytical views on many aspects of IoT technologies including standard architecture, stack protocols, value proposition, different IoT applications, trending technologies, and challenges.
The rest of the paper is structured as follows. Section 2 discusses the IoT standard architecture, enabling technologies and stack protocols. Section 3 describes the different domains of application for IoT with the most prevailing deployments. Section 4 sheds the light on rising trends in IoT and the convergence between IoT and data analytics. Section 5 discusses the grand challenges for IoT that remain open for further research and deemed to decelerate its wide scale adoption. Lastly, Section 6 offers concluding remarks.
2 IoT standard layered architecture and protocols
From the engineering perspective, IoT is witnessing an increasing number of enabling technologies. This high diversity of IoT enabling technologies stem from the proliferation of IoT devices, their heterogeneity and uncertainty of operational environments, the advancements in chip manufacturing, and variety of communication protocols ( Bouguettaya et al., 2021 ). Nonetheless, the advent of artificial intelligence (AI) and associated machine learning (ML) techniques leverage the serendipity of IoT by providing insightful information from the fusion of raw data collected by heterogeneous sensors to support decision making and change how people carry out their everyday business. This adds up to the enabling technologies of IoT. Therefore, abstracting IoT systems in terms of building blocks helps to contrast the hazy boundaries between different enabling technologies and enhance the agility and robustness to achieve a successful paradigm for IoT systems ( Lin et al., 2017 ). The core elements of a typical layered IoT architecture, as depicted on Figure 1 , can be summarized as follows.
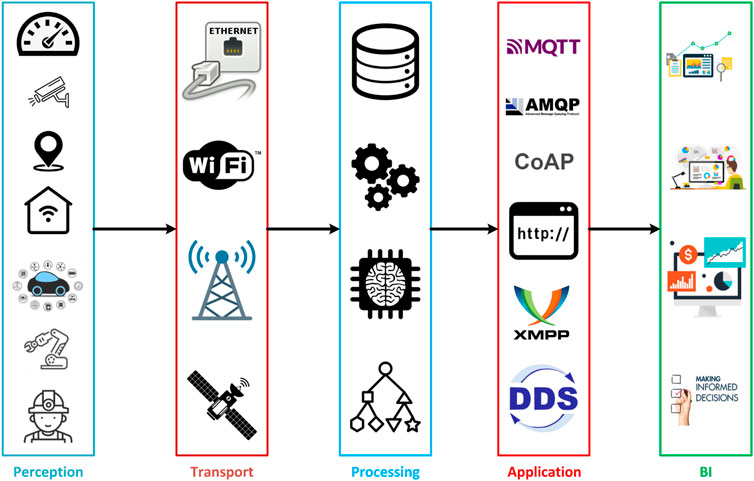
FIGURE 1 . IoT layered architecture.
2.1 Perception layer
The first layer of the IoT architecture is the perception layer, also denoted by the hardware, physical, or infrastructure layer. This layer encompasses the constituent physical devices of an IoT system that are typically responsible for: 1) sensing the environment in their vicinity and sending the raw sensed data to the next upper layer for processing, such as environmental sensors; 2) transforming the logical decisions coming from the upper inference layer into physical actions applied to corresponding devices, such as actuators and servo motors. It is worth noting that, and as the name of IoT implies, the constituent devices that form an IoT system embed some form of communication by which they can be directly or indirectly, with the help of a gateway, connected to the Internet. Moreover, IoT devices typically include some form of identification that helps differentiate the data passed to the upper layers of the IoT architecture. This identification can be either burnt into the device firmware by the manufacturer [such as the unique identifier (UUID)], set up by the user through configurable menus or DIP switches, or provided by the communication subsystem that the devices utilize (like the MAC address or the Bluetooth identifier).
2.2 Transport layer
The transport layer, also denoted by the communication and network layer, and as its name implies, is responsible for connecting IoT devices in the perception layer to the upper layers of the IoT architecture, which are typically hosted over the Internet using cloud computing technologies. This layer utilizes a wide range of communication technologies, like cellular, Wi-Fi, Bluetooth, Zigbee, etc. Besides, the transport layer is responsible for maintaining the confidentiality of the data exchange between the perception layer and the upper layers. Nonetheless, with its potential promise and anticipated ubiquity and prevalence, IoT is the motivating force behind recent research in enabling communication technologies. For example, IPv6 has been identified such that it can provide network addresses to the anticipated enormous smart objects connected to the Internet, which exceeds the already depleted IPv4 addresses. Similarly, the 6LoWPAN communication standard has been mainly developed to enable IPv6 packet transmission for power-constrained smart objects communicating over IEEE 802.15.4.
The transport layer securities typically used for IP-based networking, namely Transport Layer Security (TLS) and Datagram TLS (DTLS), provide the essential means for secure end-to-end communication. However, these technologies are not always feasible for deployment in resource-constrained embedded IoT devices due to the induced increased processing, storage, and power consumption overhead associated with these security mechanisms. This, in turn, usually delegates the authentication and the data integrity tasks of exchanged information in IoT systems to be arbitrarily carried out by the application layer based on the required security level and device capabilities. Besides, it exposes these poorly-secured IoT devices as a weak point for malicious users to penetrate the underlying critical network infrastructure or exploit them for botnet attacks to prevent the availability of network resources, aka distributed denial of service (DDoS). Derived by the proliferation of IoT devices, recent statistics anticipate that more than %25 of all cyberattacks against businesses will be IoT-based by 2025. This slows down the adoption of IoT and makes businesses reluctant to expose the reachability of sensed information by their IoT systems beyond their managed networks, adding up to the “isolated islands” dilemma of IoT systems.
2.3 Processing layer
The processing layer, also denoted as the middleware layer, encompasses advanced features that could not be embedded within the inherently resource-constrained devices at the perception layer. This includes storage, processing, computing, and action-taking capabilities. Besides, the middleware layer facilitates IoT systems’ scalability and interoperability across the computing continuum from the edge to a remote cloud data centre. It typically provides interfaces, like APIs, for other systems and third-party services to leverage the gathered raw data from the IoT devices or the insight obtained by the middleware layer after data processing. Based on the agreed tradeoff between device loads and bandwidth during the system design phase, the middleware layer can be either embedded within an on-site capable embedded platform, sometimes denoted as an IoT gateway, or hosted over the cloud. The former requires utilizing a medium-to-large scale embedded device to act as a gateway. Nonetheless, it typically utilizes a Linux kernel-based OS to mask the complexity of the underlying hardware interfacing to the perception layer devices. The latter, however, depends on relaying the raw data from the perception layer to cloud-hosted servers. This comes at the cost of higher bandwidth utilization and increased latency.
The emergence of a cloud-hosted middleware layer for IoT systems represents a bottleneck considering the security concerns of IoT. Cloud computing is the only candidate to digest the enormous amount of IoT data coming from perception layer devices. However, cloud providers are also principal targets for cyberattacks and single points of failure for IoT systems. A successful cyberattack could expose an enormous amount of sensitive information to hackers and render the IoT system unfunctional. This puts system designers in a tradeoff of choosing between the capability, cost-effectiveness, and ease of access associated with cloud computing technologies on one hand and the panic of potential data leakage in case of a successful cloud attack on the other hand.
2.4 Application layer
The application layer defines the domains by which IoT systems are deployed. This includes smart homes, smart cities, smart agriculture, etc. The application layer manages the logical processes to be taken based on the inference coming from the middleware layer and the system requirements. This includes sending emails, activating alarms, turning a device on or off, setting parameters, etc. Therefore, the application layer represents the user interface to interact with the other layers below it, facilitating human-machine interactions. Since the application layer is meant to be used by people, it inhibits a wide surface area exposed to good actors and bad actors. The common vulnerabilities usually encountered in the application layer include distributed denial of service (DDoS), HTTP floods, SQL injections, and cross-site scripting. Although large-scale cybersecurity attacks are dangerous, the effect of small-scale cybersecurity attacks, usually encountered in IoT systems, can be even more dangerous. This is because they do not have unique ecosystems, their cyber defense has not yet reached maturity, and they can be gone unnoticed for a long time. The security mechanisms applied at the application layer are meant to fulfill the CIA triad, namely confidentiality, integrity, and availability. This implies keeping the secrecy of exchanged information between communicating parties, ensuring that no alterations have been maliciously carried out on the information from its source to destination, and making the information always available to authorized users requiring it.
In contrast to the vulnerabilities in the lower layers of the IoT architecture mentioned above which can also affect the upper layers, security breaches in the application layer do not affect the lower layers. In capable computer systems, however, security mechanisms are applied in parallel to different layers to tighten the system’s safety. Nevertheless, for a market usually biased towards the price and the convenience rather than the security, this is not usually valid for constrained embedded devices often encountered in IoT systems. Security practices for IoT systems often delegate the security measures to be applied at the application layer based on the system requirements or even delegated to the third-party firewall appliances managing the network. Security measures in IoT systems usually come at trade-offs regarding the capacity of the constituent IoT devices utilized by the system. Moreover, with the diverse application domains of IoT, security mechanisms can even affect the system’s effectiveness. For example, a VoIP-based IoT solution can be adversely affected by the induced latency of the security mechanism in action. On the other hand, this latency pales for confidentiality- and integrity-critical applications, like financial and medical applications, where the effect of a security breach would be catastrophic.
2.5 Business intelligence layer
A successful IoT system depends on the utilized enabling technologies and how inference is delivered to the user abstractly and efficiently. The business intelligence layer is meant to fulfill this task by providing the user with visualized representations of the information coming from the middleware layer, masking its complexity and making it easier for the user to make informed business decisions.
The business intelligence layer is not affected by the constituent embedded IoT devices utilized by the system. It does not deal directly with the constituent IoT devices. However, it deals with the inference from the middleware layer after processing the raw data from the IoT devices through the application layer protocols. Therefore, the security of the business intelligence layer depends on the typical user-level security mechanisms found in capable computer systems. The user-level security can be applied to different entities constructing the layer. This includes files, databases, or any other resources. The user-level security is meant to implement a fine-grained authorization control over accessible information to different users based on their credibility.
3 IoT applications
IoT can be seen in different real-world applications and services such as home automation, intelligent transportation, smart cities, digital healthcare, remote health monitoring, smart agriculture, and industrial automation ( Gubbi et al., 2013 ). In each application domain, several sensors are triggered to independently gather data, transmit information, and initiate and execute services with minimum human intervention ( Sarkar et al., 2014 ). The main objective of integrating IoT technology into real-world applications is to enhance the quality of life. For example, in the domain of smart city services, we find IoT applications used for increasing city safety, efficient mobility, and enhancing smart energy usage ( Weber and Podnar Žarko, 2019 ). On the other hand, IoT technology has introduced remote medical monitoring systems in the healthcare domain which empower physicians to provide superior care to patients ( Selvaraj and Sundaravaradhan, 2020 ). Numerous research proposes different IoT-based solutions and innovations under three application domains shown in Figure 2 ( Sarkar et al., 2014 ).
FIGURE 2 . IoT application domains and related services.
3.1 Smart city
IoT technology assists cities to enhance mobility services, improve public safety, and control and automate household systems. Intelligent transportation, for example, focuses on solutions that manage road infrastructure and improve route planning for drivers. Furthermore, it provides innovative solutions to monitor and manage traffic systems using smart traffic signals and sensors, throughout the road network to smooth the traffic flow and reduce congestion. The concept of smart city services is not restricted to transportation, but also involves other aspects of human life, such as public safety, green and clean environment, smart grid, efficient delivery of municipal services and connecting the physical infrastructure to the digital world. In the following we shed the light on some of these aspects.
3.1.1 Traffic management
IoT-based traffic management systems mainly monitor road traffic conditions to solve the problem of increased traffic congestion and predict traffic status ( Poslad et al., 2015 ). These systems assist drivers by informing them about the traffic conditions at a given location and time. For example, an adaptive traffic signal control (ATSC) system that captures the traffic volume level can significantly reduce traffic congestion ( Saarika et al., 2017 ). Equipping roads with advanced sensors that capture real-time traffic data assists in determining the duration of traffic light signals across intersections. The ATSC system not only eases the traffic flow at intersections but also reduces travel time and fuel consumption, contributing positively to green environments. Research on IoT-based real-time ATSC systems at an intersection describes the coordinated approach as it is used to track the movements of vehicles and pedestrians ( Eom and Kim, 2020 ; Jamil et al., 2020 ). It also uses the deep reinforcement learning (DRL) method which is commonly used in ATSC systems to teach/educate traffic controllers how to make proper decisions. DRL simulates the effect of a traffic signal’s action and the resulting changes in traffic status. It would be classified as an appropriate action in that given situation if the action improved traffic conditions, and as a negative action otherwise ( Jamil et al., 2020 ). Furthermore, IoT-based traffic management systems can facilitate smart parking in public spaces such as on-street parking, and lot parking. According to Libelium company ( Dujić Rodić et al., 2020 ), parking spaces play critical roles in reducing traffic volume, and gas emissions. In smart parking, drivers can easily locate an empty parking place using smart parking maps. These smart maps use IoT sensors and cameras to detect and manage the likelihood of parking space in a given area. An example of a real-time traffic occupancy system for smart parking is called SplitParking which is managed by the city of Split in Croatia ( Weber and Podnar Žarko, 2019 ). The SplitParking system places sensors integrated with an IoT technology within its parking spaces to monitor space occupancy andlert the end user of the parking availability through a user-friendly mobile application ( Weber and Podnar Žarko, 2019 ).
3.1.2 Intelligent transportation
The emergence of IoT has provided a new perspective for intelligent traffic systems development. This is because the IoT paradigm satisfies the public’s demand towards an “always connected” model by relying on the interconnection of our daily physical objects using the Internet. Hence, allowing it to collect, process and transfer data creating smart intelligent systems without human intervention.
In the traffic domain, IoT requires every element such as roads, tunnels, bridges, traffic lights, vehicles and roadside infrastructures to be Internet-connected for identification and management purposes. This can be done using sensor-enabled devices, for instance, RFID devices, Infrared sensors, GPS and many others. Intelligent traffic systems that are IoT-based can efficiently improve traffic conditions, reduce traffic congestion and are unaffected by weather conditions. Moreover, IoT allows for dynamic real-time interactions, since it facilitates the incorporation of communication, control and data processing across the transportation systems. Beyond any doubt, IoT is causing a noticeable shift in the transportation sector.
The rapid advancements within information and communication technologies have also paved the way for developing more self-reliable and intelligent transportation systems. These include striding advancements in hardware, software, sensor-enabled and wireless communications technologies. Therefore, moving towards a new era of connected intelligent transportation systems, where the demand for on-going and future real-time traffic data continues to rise ( Abdelkader and Elgazzar, 2020 ). This enforces several challenging requirements on the traffic information systems. Among these requirements is broadcasting real-time, user-friendly, and precise traffic data for users. These traffic data including color-coded maps showing congestion, calculated traffic time intervals between arbitrary points on the road network. In addition to traffic density estimations that should be easily interpreted by users in a very short time. Moreover, demonstrating real-time routes for drivers based on the embedded navigation systems such as Global Positioning Systems (GPS). Another challenging requirement lies in storing huge amounts of traffic information generated from progressively complex networks of sensors, where Big data comes into play. However, collecting and storing this amount of traffic information is not enough. It is crucial to correlate based on game theory methodology, validate and make use of data in real-time. Hence providing valuable, relevant data extraction and insightful predictions of upcoming patterns and trends based on historical data. As an example, providing drivers with real-time traffic information to assist them in finding out the best road routes. This is why the subsequent role of predictive analytics for the whole transportation is needed. Consequently, traffic information systems require participation of all of the above components to interact and integrate through a common infrastructure. It allows immediate transmission of real time traffic information to any part of the system ( Abdelkader et al., 2021 ).
Even with the aforementioned benefits and challenges that come along with the integration of IoT into the transportation sector. IoT provides a paradigm shift that changes the transit services into intelligent groundbreaking systems, where numerous cutting edge technologies are incorporated. This creates a wide suite of intelligent transportation applications that have road users’ experience and safety at its core. A widely adopted IoT applications in the automotive industry include: the integration of sensors such as weight measurements and real-time fleet location sensors-based tracking to help fleet operators efficiently manage their fleets. Another use case that IoT technologies have shown great impact is predictive analytics. In this context, drivers are provided with early in advance vehicle maintenance alerts in cases of failure of a specific vehicle component. This is because these components are equipped with sensors that collect and share real-time information on the vehicle’s status with their vendors. It avoids any sudden or abrupt failure that can cause a life-hazard situation. Last, but not least with a precise focus on the integration of IoT with connected mobility. Figure 3 showcases a predictive maintenance scenario, where an in-vehicle monitoring system acquires IoT sensing data from the faulty in-vehicle sensor. The vehicular data is sent to the Diagnostics and Prognostics cloud services for analyzing and predicting maintenance issues. Repair recommendations are then sent back to the drivers ( Kshirsagar and Patil, 2021 ).
FIGURE 3 . An IoT-based predictive maintenance use-case scenario.
3.1.3 Emergency response
Crisis management is one of the critical situations that face many governments, first responders, emergency dispatchers and others who provide necessary first aid/assistance at the least possible time. In such situations, the design of the required infrastructure to handle emergencies becomes a critical requirement. With the introduction of IoT technologies to the safety systems where a suite of sensors are connected to provide real-time data to crisis management officials. This includes the use of sensors to monitor the water levels in cases of flood situations to provide insights that can support real-time data analytics to manage flooding crises. Real-time information can contribute to improving crisis management response time. Hence, reducing or eliminating the costs of crisis-related damages. Firefighting is considered a viable use case that finds value in IoT applications. Heat-proof sensors placed in indoor buildings can provide real-time information about the initial starting point of a fire, spreading patterns and intensity levels ( Mekni, 2022 ). It also extends to provide additional safety measures for firefighters as they use IoT-based safety alert devices that can accurately detect their motions. These devices are equipped with acoustic transmitters which act as beacons to allocate firefighters within the building and embedded sensors that can monitor their vital health conditions. Besides protecting firefighters, IoT-based sensors are employed to sustain indoors electrical systems and smartly pre-identify any active heat sources through abrupt temperature spikes. Immediate alerts are then subsequently sent for rapid and instant inspections. Fire systems based on IoT solutions can be actively intelligent to detect and promptly put off small fires through the use of smart sprinklers. Other emerging solutions that aid firefighters in fire crisis situations include computer-aided dispatch data such as precise fire locations, environmental conditions and others. Augmented reality-IoT based firefighter helmets ( Choi et al., 2021 ) are another innovative solution that can effectively guide firefighters to navigate in low-visibility conditions.
Emergency responders and dispatchers are leveraging the benefits of IoT-based solutions when dealing with daily traffic accidents. Numerous automotive industrial solutions such as GM OnStar provide a myriad of applications and services to assist first aid dispatchers. This could be achieved through utilizing cellular networks in conjunction with GPS and IoT technologies. Leveraging Vehicle to Infrastructure (V2I) communication-based technologies to provide critical information incases of traffic accidents. These include avoidance crash response, where drivers in crash situations can connect to OnStar call center by requesting the appropriate help to be provided to the vehicle’s location. The ecall can be activated manually (using a push-button) or automatically through data collected from on-board sensors. Other applications include stolen vehicle assistance which help the authorities in locating the stolen vehicle by activating several functionalities. This includes halting the restart option upon reactivation of the remote ignition block and transmitting a slowdown signal to let the vehicle come to a stop eventually ( Abboud et al., 2016 ). Other use cases include amber alert notifications sent to the public by integrating IoT and cellular network technologies. Amber alerts provide new means of aiding emergency responders and authority officials in risky situations such as child abduction. Officials collect crowdsourcing witness information from people within close event proximity to assist in their investigations. The alerts usually include event description (time and location). In addition to the Kidnappers’ detailed information (e.g, vehicle’s information, license plate number and their description) as well as child description. However, inability to correctly track the suspects’ vehicle or missed notifications by the public may contribute and lead to inefficient amber alert-based systems ( Zhang et al., 2018 ).
Traditionally, infrastructure failures and power outages are other use cases implying sudden and abrupt crisis situations that may be disruptive to emergency officials. Based on leveraging IoT technologies that aim at providing preventive and predictive maintenance. Hence, avoiding sudden breakdowns, anomalies and damages of the infrastructure. This could be achieved through continuous supervision and monitoring. For instance, smart bridges include a modular and IoT-sensor based system for monitoring, evaluating and recording any changes of the bridge structure in near real-time. Embedded sensors in the core structure of the bridge can then relay measurable information to management officials for further analysis. This includes humidity, temperature and corrosion status of the structure. Such data is considered valuable to constantly assess and evaluate the health structure and provide necessary measures such as intervention and predictive measures strategies ( Yang, 2003 ).
3.2 Home automation
Home automation and control systems are essential components of smart cities and have played a significant part in the advancement of our home environments. They have several applications for different usage at home, such as entertainment and smart living, surveillance, and safety management ( Alhafidh and Allen, 2016 ). Home automation is described as a standard home environment equipped with IoT technological infrastructure to provide a safe and comfortable lifestyle ( Khoa et al., 2020 ). Home automation is based on an intelligent, self-adaptive system that analyzes and evaluates stakeholder behaviors and has the capability to predict the stakeholder’s future actions and interact accordingly. Home automation systems use image detection and facial recognition models that are embedded in an intelligent control system connected to different sensors such as light sensors, motion sensors, water leak sensors, smoke sensors, and CCTV cameras ( Pavithra and Balakrishnan, 2015 ). These devices communicate with each other through a gateway that is distributed throughout a home area network. The home control system will connect different subsystems that cooperate in modeling the stakeholder’s actions and the environment’s information such as temperature, humidity, noise, visibility, and light intensity to enhance the learning process. For example, lights and AC temperature can be controlled and automated to adapt to the stakeholders’ needs and their movements in the home environment. This would conserve energy while also effectively monitoring energy consumption ( Vishwakarma et al., 2019 ). Research on home automation is not restricted to energy optimization; it involves health monitoring and security measures. By using innovative IoT technologies, we can connect to surveillance cameras in the home environment via a mobile device. Additionally, stakeholders can have access to doors and window sensors to maintain home safety and security remotely ( Alsuhaym et al., 2021 ).
3.3 Industrial sector
Industrial IoT leverages IoT capabilities in business and economic sectors to automate previously complex manual operations in order to satisfy consumer needs and reduce production costs. Warehouse operations, logistical services, supply chain management, and agricultural breeding can have machine-to-machine (M2M) intercommunication to ensure optimal industrial operations ( Pekar et al., 2020 ). Figure 4 illustrates a scenario of the IoT communication sensors in a smart agricultural system. This smart agriculture system monitors and analyzes the environmental parameters using soil moisture and harvesting sensors such as ZigBee, EnOcean, Z-wave and ANT ( Tang et al., 2018 ). These sensors are automated to diagnose the status of a plant and gather this data through an IoT platform to take the proper action such as when to irrigate in consultation with a weather forecasting service available in the Cloud; thus ensuring the efficient use of water resources.
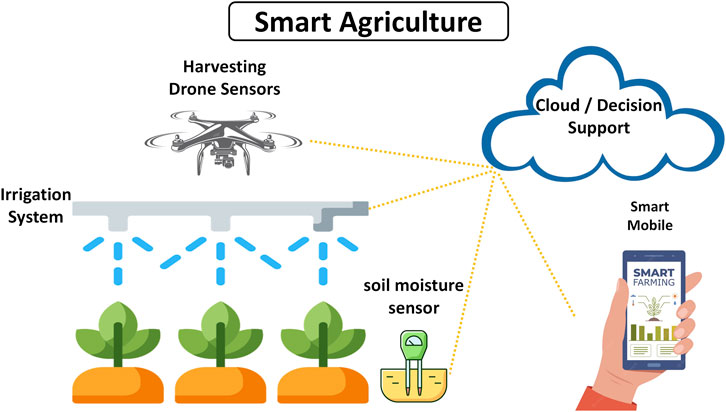
FIGURE 4 . Illustration of a smart agriculture system.
3.4 Logistics and supply chain
Supply Chain Management (SCM) is a crucial service in our world. Since 1900 ( Lummus and Vokurka, 1999 ), humanity has evolved SCM to meet the market needs. Figure 5 highlights SCM milestones. Before 1900, SCM was restricted to the local areas. However, due to the revolution in railways, goods now can reach far beyond local borders. Between 1900 and 1950, global SCM attracted large players and organizations like UPS began providing their services in the SCM field. Industry leaders started to look for how we could improve the mechanization of the SCM process. From 1950 to 1970, the SCM community gained a superior experience by analyzing the military logistics of the First World War. DHL and FedEx were established as logistics enterprises, and IBM built the first computerized inventory management that was capable of handling complex inventory problems and making stock forecasts. In 1975, JCPenney designed the first Real-Time Warehouse Management System (WMS) that monitors the warehouse stock in real-time. Seven years later, Keith Oliver introduced the Supply Chain Management term. In the 90s, the technological revolution was triggered when many enterprises deployed computers to manage their processes and the internet to reach their customers through the World Wide Web. In the 90s, Amazon started running the e-commerce website. The 4.0 industrial revolution, including the internet of things, began growing in the last decade. Although the IoT looks like a promising technology to be adopted in the SCM field, deploying IoT in SCM faces many challenges. The main hindrance ( Haddud et al., 2017 ) is the integration of different supply chain processes due to The heterogeneity of technologies used in various supply chain stages.
FIGURE 5 . Supply chain milestones.
COVID-19 ( de Vass et al., 2021 ) uncovered a new factor that magnifies the importance of relying on information and communications technology to run the SCM systems. Businesses had to switch to remote working due to the pandemic. The lockdown and physical distancing requirements imposed on suppliers reduced their labors in their plants and sometimes obliged to shut down to limit the virus spreading. As a result, consumers face product shortages due to reduced production volumes during the pandemic. To date ( Ozdemir et al., 2022 ), the world is still suffering from the devastating effects of COVID-19 on the supply chain. Therefore, decision-makers ( Baldwin and Di Mauro, 2020 ; Baldwin and Tomiura, 2020 ) started exploring how we could deploy new technologies, such as IoT, for managing remote operations.
3.5 Healthcare
IoT sensors and devices shifted the landscape of portable and wearable medical devices from fitness and wellness devices to medical-grade devices qualified for usage at hospitals and healthcare providers. This shift accelerated the integration of remote patient monitoring in hospitals to accommodate patients with chronic diseases ( Casale et al., 2021 ). Therefore, numerous efforts have been conducted to advance remote patient monitoring (RPM) systems with the help of well-established IoT infrastructures and standards in the healthcare domain ( El-Rashidy et al., 2021 ). The RPM systems are expected to match or exceed the performance of the existing monitoring and examinations administered at hospitals and healthcare facilities ( Casale et al., 2021 ). For example, continuous heart rate monitoring and immediate heartbeat detection necessitate patients to be hospitalized and/or connected to a Holter monitor or similar devices for long-term cardiac diagnosis. However, this setup would hinder patient mobility due to the limitations of the existing devices in terms of size and the number of attached wires. Moreover, hospitals dedicate significant resources to providing long-term cardiac monitoring that, in some cases, is unavailable, especially in low or middle-income countries. Therefore, RPM systems effectively reduce death from chronic diseases (e.g., heart diseases, diabetes). IoT platforms and devices significantly accelerated the development and integration of RPM systems into existing healthcare infrastructures. To that extent, a typical RPM implementation constitutes various services but is not limited to data acquisition, tracking, communication, automated analysis, diagnoses, and notification systems ( Miller et al., 2021 ).

4 Rising trends in sensor data analytics
In recent years, the IoT domain has witnessed increasing interest by the research community and rising demands from the industrial sector to embed real-time data analytics tools into the core of IoT standards. While the real value proposition of IoT is shifting from providing passive data monitoring and acquisition services to autonomous IoT applications with real-time decision-making services. Consequently, real-time data analytics is no longer an add-on service and has become integral to any IoT application rollout. For example, remote patient monitoring (RPM) and real-time data analytics have significantly contributed to enhancing ECG monitoring and enabling healthcare providers to gain 24/7 access to their patients remotely, especially for patients with coronary diseases ( Mohammed et al., 2019 ). However, sensor data acquisition and collections are mapped as the foundation of IoT applications yet are considered passive techniques due to the absence of intelligence or decision-making. The main goals of IoT application at the early stages were to collect and monitor significant information regarding specific applications as initially proposed in 1999 ( Butzin et al., 2016 ) while developing supply chain optimization at Procter & Gamble. Nearly after 2 decades, the goals of using IoT applications and their expectations are on the rise, demanding proactive and active decisions made on sensor data collected in real-time. Accordingly, data analytics permits various applications to focus on performing real-time diagnoses, predictive maintenance, automated decision-making, and theoretically improving the productivity and efficiency of the intended applications. Meanwhile, modern stream processing engines (e.g., Apache Kafka and Apache Pulsar) come with built-in APIs ready for data analytics integrations ( Martín et al., 2022 ). Moreover, most cloud services provide ready-made end-to-end event processing and real-time data analytics tools (i.e., Google DataFlow).
4.1 Real-time vs. offline data analytics: Differences, needs, and potential use
In an IoT-driven society, applications and services integrate smart learning approaches for analyzing insightful patterns and trends that result in improved decision-making. For more effectively optimized analytics, several IoT data-specification characteristics should be considered. These include dealing with huge volumes of data streamed from sensor-based devices deployed for IoT applications and services. It requires new means of big data analytics that can deal with huge volumes of sensor-generated data. In this context, conventional hardware/software methods for storage, data analytics and management purposes cannot handle such huge volumes of streaming data. Moreover, information collected from heterogeneous devices result in three significant common features among IoT Data. These features include data heterogeneity and association of time/space stamps based on the sensors’ locations. The third feature is the subjectivity of IoT data associated with the high noise levels during acquisition and transmission processes.
Beyond such characteristics that utilize big data analytics approaches, a new suite of applications and services arise that demand prompt actions in real-time analytics. This is primarily due to its time sensitive and fast streaming of IoT data that is generated within short time intervals for instant decision making and actions. These insightful decisions are time stringent, where IoT streaming data analytics need to be delivered within a range of hundreds of milliseconds to only a few seconds. As such, life-saving applications demand fast and continuous streams of incoming data associated in some cases with real-time multi-modal data sources for efficient decision making. For instance, connected and autonomous vehicles require data fusion of real-time sensor data from different sources (e.g., Lidars and cameras), V2X communication and road entities (e.g., traffic lights) for safe perception decision making. Transmitting traffic data to the cloud servers for real-time analytics will be liable to network and communication latency that are not well-suited for time sensitive applications, which may result in fatal traffic accidents. However, analyzing real-time streaming data on powerful cloud computing platforms that adopt data parallelism and incremental processing techniques can reduce the end-to-end delay associated with two-way data transmissions. A more optimized approach could reside in solutions such as edge computing, where data analytics are closer to the data sources (e.g., edge or IoT-based devices) for faster data analytics ( Goudarzi et al., 2021 ). However, these solutions are still prone to a number of limitations including limited computation, power and storage resources on IoT devices. The rising trends towards real-time data analytics are also striving in non-critical business applications.
4.2 Decision making
Leading IoT-based business sectors rely heavily on well-analyzed real-time data inferred from their IoT-enabled products. For critical and unbiased decision making, real-time data analysis by machine learning algorithms can assist in eliminating/reducing junk information and estimating learning useful patterns. Data-driven analytics will provide more in depth insights for optimizing customers’ experiences through daily behaviors and patterns analysis. As an example, Apple watches can monitor our daily exercises and sleeping patterns in real-time and assist in providing customized preference notifications. Uber can also make informed decisions based on analyzing real-time demands for traffic trips. This determines their pricing rates that proportionately increase in rush hours. Other examples may include placing sensors within oil tanks for real-time monitoring of oil fluid levels, temperature and humidity. This initiates automated decision making such as oil reordering and planning pre-scheduled maintenance ( Moh’d Ali et al., 2020 ).
Decision making-based systems can be classified according to the different levels of system complexity. This includes visual analytics systems that help business practitioners to analyze and interpret gathered IoT data. Business intelligence embedded dashboards aid in presenting the retrieved IoT information in a meaningful manner. Automated and warnings-based systems conduct a predefined data analysis that assists in highlighting risky situations through alerts and warnings. For example, IoT-based real-time environmental monitoring systems can track pollutants and chemicals’ levels in the air within an industrial city. Warning notifications are then subsequently sent to citizens within the affected geofenced area indicating health risk hazards. Reactive-based systems may take a step forward towards performing actions described through rule-based languages that are carried out when specific conditions are met. For instance, smart lighting IoT-based systems may switch off the lights in a specific building area if no one is present, which is indicated by infrared occupancy sensors ( Wang et al., 2017 ).
4.3 Predictive maintenance
Utilizing IoT applications has incredibly reduced maintenance costs, in particular in the industrial sector. For example, industrial equipment manufacturing that embed sensors in heavy machinery integrate with analytical tools to monitor the operational efficacy, detect faults or failures, and provide a full assessment of the operating condition ( Mobley, 2002 ). This comprehensive performance evaluation occurs on a regular basis to maintain the system’s efficiency and initiates maintenance if needed. This procedure is known as Predictive Maintenance (PdM), or condition-based maintenance, and it employs diagnostics and prognostics data to spot early signs of failure, allowing the system to operate as intended ( Zonta et al., 2020 ). Furthermore, PdM can estimate degradation of the equipment and predict the remaining useful life (RUL) of equipment, which reduces the maintenance costs to the minimum and assures service availability. According to Selcuk ( Selcuk, 2017 ), IoT-based predictive maintenance increases the return on investment by 10 times, where this approach increases the total production by 15%–70% and reduces the maintenance costs by 25%–30%. Although PdM successfully reduces the cost of production and maintenance, it is expensive to implement due to the high cost of the hardware and software required to effectively incorporate the PdM into the system. Moreover, the quality of the training services and the amount of data required to ensure the efficacy of the PdM performance can be challenging ( Compare et al., 2019 ).
4.4 Operation optimization and automation
Industry 4.0 is transitioning from a concept-based approach into a market reality. Through the integration of intelligent and computerized robotic devices into many aspects of industry verticals (e.g., 3D printing, E-sports) that can assist in automating and optimizing the manufacturing operations. This allows accurate, timely and cost effective completed manufacturing processes among a set of machines with minimal or no human interventions. In addition to decrease in cost-related operations through effective inventory management and energy consumption optimization. Effective inventory management in logistics and supply chain sectors is obtained through the integration of IoT with Radio Frequency Identification (RFID) ( Tan and Sidhu, 2022 ) and barcode scanners.
Furthermore, IoT technologies within business automation can efficiently be used for controlling and monitoring machines’ manufacturing operations, performance and rate of productivity through internet connectivity. Moreover, real-time analysis generated from onsite IoT-based sensors provides valuable insights to initiate more efficient ways for decreasing cost-related operational expenses and safety-related/unplanned maintenance issues. For example, incases of machine operational failures, an IoT-based system can promptly send a machine repair request to the maintenance department for handling the issue. Furthermore, with the introduction of IoT technologies, business revenues are subsequently expected to increase due to the incremental rise in operational productivity. This can be achieved through analyzing three critical aspects including operational data, timing and the reasons for any production issues. This allows business leaders to be focused on their high-level core business objectives with a well-defined automated workflow.
4.5 Enhanced customer experience
Connected environments enable businesses to adopt a user-centric approach which utilizes IoT technologies for enhanced overall customer experience and extend the customers’ loyalty towards their services and products. IoT-driven businesses are the gateway to futuristic enhanced digital customer experience and prolonged loyalty which are considered one of the primary laser-focus objectives by many brands. The drive towards more personalized services and applications by customers urge many enterprises to increase services for customer engagement through the use of artificial intelligence-based customer support systems for real-time assistance.
The aforementioned notion of providing level up services that incorporate personalized experiences initiated many innovative applications and services. As such, omnichannel customers’ applications and products such as smart-based home appliances and devices including Alexa-supported devices, Nest Thermostat and intelligent Ring Doorbell cameras that enable customers to use voice assisted technologies along with IoT to control various aspects of their home intelligently. Moreover, ubiquitous smart wearable devices such as fitness trackers that collect real-time health data related to customer behavior and daily routines to enhance customer experience. For instance, providing customers with real-time personalized notifications according to their daily activities. Figure 6 demonstrates the users-centric experience among various IoT services and applications.
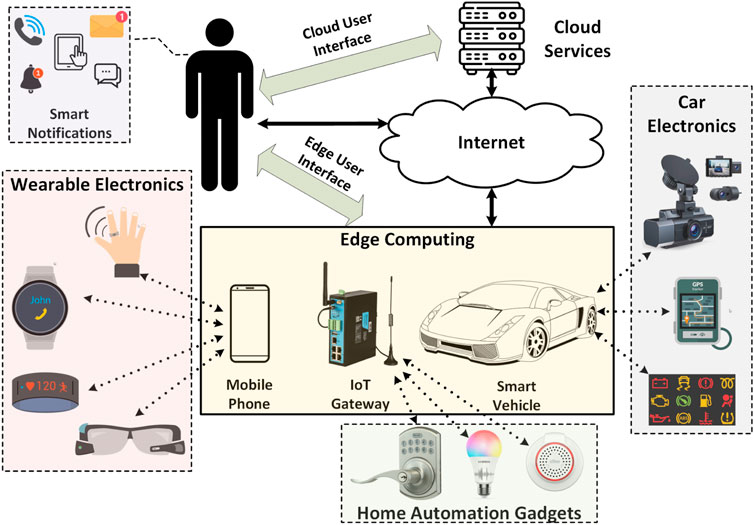
FIGURE 6 . User-centric IoT application scenarios.
However, privacy and security data leakage are still considered a major challenge that many researchers and developers are trying to find innovative and tangible solutions to secure personal information when shared for improved service and application experiences.
4.6 Asset tracking and monitoring
Introducing artificial intelligence (AI) into IoT applications has created significant opportunities for innovations in automation and asset tracking domains. Companies and labour-intensive corporations are investing in autonomous working environments with less human interaction, and the demand for AI and context-aware systems has drastically increased. Whereas in times similar to the coronavirus pandemic, factories and workplaces have entirely shut down because of lockdown measures to prevent human interactions. The fusion between AI and IoT transitioned traditional industry models to the industry 5.0 revolution. AI and IoT as core technologies to industry 5.0 along with wireless sensor networks result in more benefits to industries like using analytical techniques to provide predictive maintenance notifications directly affecting downtime, improving workforce and increasing production efficiency. IoT sensors and devices can perceive and sense their environment through high-level technologies, such as laser scanners, cameras and image processing, movement and proximity. Therefore, real-time decisions are made autonomously regarding object identification and asset tracking by coupling these technologies (i.e., image-recognition software). Similarly, IoT applications based on AI algorithms can learn and think logically about different operations that require problem-solving schemes. Autonomous applications operate based on the receding-strategy approach, where new and old control inputs are carried out simultaneously through computing the new control inputs and executing the old ones. The application creates these control inputs to provide real-time performance based on three hierarchical levels. The higher level is concerned with defining complex operations, for example, GPS waypoints for an autonomous device (e.g., robot) to follow. The other two (mid and lower) levels are precisely related to creating and tracking a reference trajectory for this course, respectively. The safety of the robot is the responsibility of the mid-level controller ( Vaskov et al., 2019 ). More concisely, safety concerning collision avoidance among a group of automated robots performing a specific task can be avoided by sharing their perceived data. Other communications that involve Human-Robotic communication are based on the models, such as imitative learning and artificial neural networks.
5 Open challenges
5.1 device and data heterogeneity.
The versatility of IoT devices and sensor nodes in various fields has given rise to many applications. While deep learning, AI, and many other enabling technologies assist IoT devices in learning by experience and adapting to new environmental inputs to be able to conduct complex operations. However, the reliance on receiving data representing the context of the environment surroundings specific to the IoT application requires a significant number of different sensors and devices. Individual sensors or applications provide limited cognition and visibility of the surrounding environments. Therefore, integrating various sensors is essential in context-aware applications. Furthermore, the diversification of sensor nodes and devices raised numerous challenges in the research community and the industry with respect to unification and standardization. In public sensing, different types of sensors are used (e.g., RFID, Ultrasonic, Cameras, Lidars, etc. ) to solve designated issues like real-time counting of people waiting to be served at a specific service provider. The same extends to IoT applications similar to the public sensing domain like traffic management and predictions. Therefore, the demand for modular platforms with unified application programming interfaces (APIs), transmission protocols, data transformation and storage is growing. Moreover, data conversion and normalization operations carried out in applications with heterogeneous devices increase exponentially due to the diversified number of sensors utilized just for one application (e.g., autonomous vehicles).
Behmann ( Behmann and Wu, 2015 ) described current IoT solutions as point solutions where they are isolated and cannot interact with each other. Collaborative IoT (C-IoT) ( Behmann and Wu, 2015 ) is a recent trend that is still unsaturated and needs more effort to be deployed in real-world scenarios. Sharing the infrastructure and data becomes inevitable to pave the way for C-IoT systems. C-IoT can create an expandable ecosystem, and the IoT community will solve complicated problems by relying on the collaboration between IoT systems. For instance, an ambulance in the emergency state can always have a green light on its way if the emergency service can share the ambulance’s route with the city’s intelligent traffic system using the shared infrastructure of C-IoT. Recently, an active movement to have a unified standard in different IoT layers has been raised for a few years to mitigate incompatibility challenges faced by the C-IoT trend.
5.2 Interoperability
The diversity of IoT devices in the perception layer brings the flexibility to build customized IoT solutions and cherrypick the appropriate device for a specific task that matches constraints regarding the accuracy, cost, compatibility with the existing infrastructure, etc. However, this also comes at the cost of the absence of a unified ecosystem for IoT. This results in interoperability issues between different IoT systems and increased development time to get diverse IoT devices to act as a coherent system. Besides, it leads to the notorious “isolated islands” of miniature IoT subsystems based on the brand of devices or their enabling technologies, hindering the utilization of sensed information by different systems to its maximum and impeding the potential promise of IoT.
5.3 User and data privacy
The constituent IoT gadgets of an IoT system typically consist of consumer electronics (e.g., smart TVs) and wearable devices (e.g., smart watches) that gather a lot of information about people, which was previously hard to collect. Gathered data by IoT devices may include personal information of the users (e.g., name, birthdate, etc. ), their biometric information (e.g., fingerprint, voice recognition, etc. ), and their preferences (e.g., eating habits, preferred movie genres, etc. ), which are usually part of the device’s initial setup, registration to its cloud platform, or for the device to be able to perform its smart designated task efficiently. Moreover, advanced IoT systems typically involve the aggregation of numerous pieces of information from heterogeneous smart objects, which is known as “sensor fusion” ( Abdelmoneem et al., 2018 ) to provide accurate and comprehensive data about the environment, including people themselves, to help make better informed decisions. Thanks to the advancements in artificial intelligence (AI) domain technologies which can leverage granular data collected by smart objects to generate inferences that would not be achievable with coarser data from individual smart objects. This intelligence imparted to IoT catalyzes its wide adaption and makes it quite useful in different application domains. However, user privacy concerns are still an open challenge to IoT that impedes its widespread adoption and limits its potential promise. IoT systems can disclose identifiable information about people without their consent. Therefore, amidst the potential promise of IoT to change the way we deal with our surroundings, users are mostly worried about the potential of private information leakage ( Chanal and Kakkasageri, 2020 ). They are worried about who owns their data and how it is utilized. Nonetheless, the notorious correlation between service providers and device vendors on one hand, and data brokers on the other hand, raises concerns about the possibility of their personal information being disclosed for non-public interest objectives. People frequently alter their behavior when they suspect that their identifiable information and activity footprints are being monitored, which reduces their freedom, changes their lifestyle, and makes them sceptical of IoT. In the following subsections, we review data privacy concerns that are associated with IoT.
5.3.1 De-identification of IoT data
Generally, it is prohibited to make datasets that include identifiable personal information publicly accessible. One common way to prevent exposing personal information in datasets is to avoid gathering information that could be used to identify people in the first place and whenever possible. For example, PIR sensors could be used for occupancy detection rather than surveillance cameras. However, given the penetration of IoT in a lot of domains with differentiated requirements, it is usually hard, or even impossible, to preclude the inclusion of identifiable information in gathered datasets by IoT. In this context, de-identification ( Kim and Park, 2022 ) is the process used to anonymize identifiable personal information from datasets, which is quite challenging. Hashing algorithms are commonly used to pseudonymize identifiable information in datasets by replacing identified people in a dataset with their unique hash token. However, since different datasets often have a lot in common, it is usually easy to figure out who the hashed information belongs to using inference techniques.
5.3.2 Consent
Consent ( O’Connor et al., 2017 ) is the typical justification for businesses to collect, use, and disclose personal information. However, consent often matters more than just unconsciously clicking the “I agree” button by the end user on the “Terms and Conditions” statement page of a device. Rather, consent that is meaningful and effective requires well-defined and finely-grained structured objectives that the user should be able to choose from. Moreover, one can not presume that consent will last forever. Therefore, consent methods should represent a single acceptance at a single moment in time, which may not be suitable for the continual nature of IoT. Also, given the interoperability nature of the IoT, where a smart sensor node may be utilised by different systems with different privacy policies, an individual can not grant meaningful permission for the use of their personal data for vague or broad purposes.
5.4 Vendor lock-in
IoT vendors and service providers typically maintain the security of their active devices or services by regularly providing firmware patches and system updates that address security vulnerability issues that continually emerge. However, they often have different expectations about how long their products or services will last than the people who buy them. For instance, vendors may terminate technical support or firmware maintainability of a device, or the service provider may discontinue the service that the device relies on to operate, far before the end user plans to retire the device. This usually comes at the cost of possible security holes, privacy issues, and vendor lock-in ( Fantacci et al., 2014 ). Therefore, customers would have to stick with their active line of products and services to keep their systems safe and operational because suppliers would no longer care about security and privacy issues with their retired devices or have the skills to deal with them.
5.5 Device management
The “plug and play” feature that usually accompanies IoT devices makes them user-friendly since customers can seamlessly get them up and running effortlessly without the need for complicated setup procedures. However, this sometimes comes at the cost of potential user privacy exposure since the default setup of devices usually comes with insufficient privacy and security precautions. Nonetheless, the fact that a gadget is an IoT device that can collect personal information and send it to third parties over the cloud may not be even realized by the majority of non-technically savvy customers by default. In addition, most IoT customers find it hard and time-consuming to adjust the privacy settings for each device in the system. This is because IoT does not have a standard ecosystem and is often made up of many devices from different manufacturers, each with their own user experience interface.
5.6 Accountability
The extensive and distributed nature of IoT systems, which typically include different service providers that handle the collected data to achieve the designated task of the system, makes it challenging to precisely determine who is responsible for what. In order to achieve a robust and highly reliable IoT system architecture, system designers usually follow a common system architectural model that is known as “microservices” ( Butzin et al., 2016 ). They divide the ultimate task of the system into small independent tasks, each of which may utilize numerous services from different service providers that communicate over well-defined APIs. However, this raises privacy concerns because the collected data, which may contain personally identifiable information about users, is now handled and commonly stored by various third-party organizations with hazy boundaries that may apply different privacy policies.
5.7 Transparency
The tiny size of most IoT devices in use today without a screen, or at least an adequate screen size to display a lot of textual information, makes it difficult for users to review their privacy policies before they start using them. In order to review the privacy policies of these devices, however, users should login to the website of the manufacturer of the device or use a proprietary software or a mobile application for the device. However, in either case, given the heterogeneous nature of the IoT and the anticipated large number of IoT devices people use on a daily basis, it looks extremely challenging to follow the privacy policy of each encountered device. Also, a lot of privacy policies for IoT devices seem vague to the majority of people. Moreover, some IoT devices that exist in organizations and public settings are usually anonymous without details about the type of information they collect or how this information is utilized and for which objectives. Also, most of the time, users do not have the option to stop the collection.
5.8 Security (data and device vulnerability)
IoT devices exchange data with millions of devices through the internet which implicitly exposes the IoT devices to the vulnerabilities and security threats of the Internet protocol stack ( Ilyas et al., 2020 ). The amount of data collected, stored and shared between IoT devices and the service providers are expected to grow significantly. Besides the extraordinary amount of data produced by IoT devices, they induce evidently high-security risks and potential cyberattacks destabilizing many applications and industries.
IoT networks come with their unique security challenges ( Khanam et al., 2020 ), where each layer is exposed to certain types of attacks ( Hassija et al., 2019 ), like Distributed Denial of Service attacks (DDoS) on the network layer. To that extent, a multitude of surveys citerefs2 and studies have been conducted to expose existing security threats and vulnerabilities in current IoT applications. Recent surveys on IoT data and device security emphasize that the gap between applying existing security techniques to emerging IoT applications is growing significantly. The security gaps in IoT applications are categorized into vendor-related security issues and available resources or capabilities on the IoT nodes. IoT vendors for sensors and devices are moving towards low-cost manufacturing that lack security features. Similarly, the heterogeneity of the IoT applications, protocols, and hardware increases the security scope of threats in IoT applications ( Hassija et al., 2019 ). On the other hand, IoT applications are inherently constrained by the limited processing and storage capabilities of devices to carry out sophisticated security techniques. Therefore, new security measures are introduced for IoT resource-constrained devices using robust ML techniques like the TinyML framework. The concepts introduced behind the integration of ML is to increase the flexibility of IoT nodes in defending against emerging security threats ( Dutta and Kant, 2021 ). IoT devices can then train the deployed ML models to work against new security threats.
5.9 Open deployments and access control
Mentioning the access control usually flashed RFID (Radio-frequency identification) cards. RFID technology sparked the existence of the IoT term coined by Kevin Ashton, who considered RFID a vital component in The IoT systems. Access control as an open challenge is a multifaceted challenge that has been raised due to other issues. In this section, we use a wallet holding many RFID cards as an example to discuss the access control issues:
• Heterogeneity: Having many cards to access different purposes itself is due to the heterogeneity of the systems. There are chances to have a consensus among some corporations to unify their access cards to mitigate this challenge. For instance, Google Pay is an android application that offers contactless purchases on the smartphone with a built-in Near Field Communication NFC module. Users can register debit or credit cards and use them in their daily in-person shopping instead of holding many bank cards in wallets. Due to systems heterogeneity, we still face a challenge in making all services accessible from unified access.
• Security: Giving accessibility to banks a counting using contactless RFID bank cards looks a very smooth user experience in transactions instead of writing sixteen digits in card readers. However, card skimming devices can clone contactless bank cards.
To discuss the other issues in access control, we use a smart home application as another example facing access control challenges:
• Interoperability: Recently, users can simply control their IoT devices in their houses, such as smart TV, fridge, coffee machine, and adapted light systems. The interoperability between these devices is still very challenging due to the lack of standardization. For instance, a coffee machine starts pouring coffee on a cup if the adapted light senses a motion in the living room, and there is a collaborative integration between these devices. ThingsDriver ( Elewah et al., 2022 ) is a beginning to have A Unified Interoperable messaging protocol that, if adopted by cooperates, can pave the way to have a collaborative environment.
• Privacy: All these smart home devices become remotely accessible through user-friendly user interfaces such as a smartwatch or phone. On the other side, the flexibility of accessibility raises privacy concerns. Residents’ data are highly vulnerable to being breached by unauthorized access.
6 Conclusion
In this paper, we review the Internet of Things technology from different architectural, technological, operational and value-proposition perspectives. We first shed the light on the definition, acclaimed value and potential, and unique features and characteristics compared to similar previous technologies and standard layered architecture. We then highlight the different applications of IoT in various life domains that primarily benefit from its realization as a novel computing paradigm. We outlined the grand challenges facing IoT which may cause slowdown in its widespread adoption at the individual, organizational and governmental levels.
We believe the IoT will continue to grow as a disruptive technology that changed the world and it will never be the same again. There is a continuously increasing reliance on IoT technology in different sectors of our life for its convenience and innovative applications stemming out of it. Individuals and enterprises started to gain confidence in the technology and overlook or ignore the downsides of its security and privacy aspects. However, we also believe that the emergence of Edge computing in its different forms and shapes has contributed to lower the adoption barriers of IoT and increased interest in its technology and smart services. We anticipate that in the next few years IoT will continue to penetrate deeper in various sectors and tape into more industrial and governmental settings.
Author contributions
All authors listed have made a substantial, direct, and intellectual contribution to the work and approved it for publication.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Abboud, K., Omar, H. A., and Zhuang, W. (2016). Interworking of dsrc and cellular network technologies for V2X communications: A survey. IEEE Trans. Veh. Technol. 65, 9457–9470. doi:10.1109/tvt.2016.2591558
CrossRef Full Text | Google Scholar
Abdelkader, G., and Elgazzar, K. (2020). “Connected vehicles: Towards accident-free intersections,” in 2020 IEEE 6th World Forum on Internet of Things (WF-IoT) ( IEEE ), 1–2.
Abdelkader, G., Elgazzar, K., and Khamis, A. (2021). Connected vehicles: Technology review, state of the art, challenges and opportunities. Sensors 21, 7712. doi:10.3390/s21227712
PubMed Abstract | CrossRef Full Text | Google Scholar
Abdelmoneem, R. M., Shaaban, E., and Benslimane, A. (2018). “A survey on multi-sensor fusion techniques in IoT for healthcare,” in 2018 13th International Conference on Computer Engineering and Systems (ICCES) ( IEEE ), 157–162.
Alhafidh, B., and Allen, W. (2016). Design and simulation of a smart home managed by an intelligent self-adaptive system. Int. J. Eng. Res. Appl. 6, 64–90.
Google Scholar
Alsuhaym, F., Al-Hadhrami, T., Saeed, F., and Awuson-David, K. (2021). “Toward home automation: An IoT based home automation system control and security,” in 2021 International Congress of Advanced Technology and Engineering (ICOTEN) ( IEEE ), 1–11.
Ashton, K. (2009). That ‘internet of things’ thing. RFID J.
Baldwin, R., and Di Mauro, B. W. (2020). Economics in the time of COVID-19: A new eBook , 2–3. London: VOX CEPR Policy Portal .
Baldwin, R., and Tomiura, E. (2020). Thinking ahead about the trade impact of COVID-19. Econ. Time COVID- 19 59, 59–71.
Behmann, F., and Wu, K. (2015). Collaborative internet of things (C-IoT): For future smart connected life and business . John Wiley & Sons .
Bouguettaya, A., Sheng, Q. Z., Benatallah, B., Neiat, A. G., Mistry, S., Ghose, A., et al. (2021). An internet of things service roadmap. Commun. ACM 64, 86–95. doi:10.1145/3464960
Butzin, B., Golatowski, F., and Timmermann, D. (2016). “Microservices approach for the internet of things,” in 2016 IEEE 21st International Conference on Emerging Technologies and Factory Automation (ETFA) ( IEEE ), 1–6.
Casale, P. N., Vyavahare, M., Coyne, S., Kronish, I., Greenwald, P., Ye, S., et al. (2021). The promise of remote patient monitoring: Lessons learned during the COVID-19 surge in New York city. Am. J. Med. Qual. 36, 139–144. doi:10.1097/01.jmq.0000741968.61211.2b
Chanal, P. M., and Kakkasageri, M. S. (2020). Security and privacy in iot: A survey. Wirel. Pers. Commun. 115, 1667–1693. doi:10.1007/s11277-020-07649-9
Choi, M., Li, G., Todrzak, R., Zhao, Q., Raiti, J., and Albee, P. (2021). “Designing a LoRa-based smart helmet to aid in emergency detection by monitoring bio-signals,” in 2021 IEEE Global Humanitarian Technology Conference (GHTC) ( IEEE ), 72–75.
Compare, M., Baraldi, P., and Zio, E. (2019). Challenges to IoT-enabled predictive maintenance for industry 4.0. IEEE Internet Things J. 7, 4585–4597. doi:10.1109/jiot.2019.2957029
de Vass, T., Shee, H., and Miah, S. J. (2021). IoT in supply chain management: Opportunities and challenges for businesses in early industry 4.0 context. OSCM. Int. J. 14, 148–161. doi:10.31387/oscm0450293
Dujić Rodić, L., Perković, T., Županović, T., and Šolić, P. (2020). Sensing occupancy through software: Smart parking proof of concept. Electronics 9, 2207. doi:10.3390/electronics9122207
Dutta, A., and Kant, S. (2021). “Implementation of cyber threat intelligence platform on internet of things (IoT) using TinyML approach for deceiving cyber invasion,” in 2021 International Conference on Electrical, Computer, Communications and Mechatronics Engineering (ICECCME) ( IEEE ), 1–6.
El-Rashidy, N., El-Sappagh, S., Islam, S. R., El-Bakry, H., and Abdelrazek, S. (2021). Mobile health in remote patient monitoring for chronic diseases: Principles, trends, and challenges. Diagnostics 11, 607. doi:10.3390/diagnostics11040607
Elewah, A., Ibrahim, W. M., Rafıkl, A., and Elgazzar, K. (2022). “ThingsDriver: A unified interoperable driver for IoT nodes,” in 2022 International Wireless Communications and Mobile Computing (IWCMC) ( IEEE ), 877–882.
Eom, M., and Kim, B.-I. (2020). The traffic signal control problem for intersections: A review. Eur. Transp. Res. Rev. 12, 50–20. doi:10.1186/s12544-020-00440-8
Fantacci, R., Pecorella, T., Viti, R., and Carlini, C. (2014). A network architecture solution for efficient IoT WSN backhauling: Challenges and opportunities. IEEE Wirel. Commun. 21, 113–119. doi:10.1109/mwc.2014.6882303
Goudarzi, M., Wu, H., Palaniswami, M., and Buyya, R. (2021). An application placement technique for concurrent IoT applications in edge and fog computing environments. IEEE Trans. Mob. Comput. 20, 1298–1311. doi:10.1109/tmc.2020.2967041
Gubbi, J., Buyya, R., Marusic, S., and Palaniswami, M. (2013). Internet of things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 29, 1645–1660. doi:10.1016/j.future.2013.01.010
Haddud, A., DeSouza, A., Khare, A., and Lee, H. (2017). Examining potential benefits and challenges associated with the internet of things integration in supply chains. J. Manuf. Technol. Manag. 28, 1055–1085. doi:10.1108/jmtm-05-2017-0094
Hassija, V., Chamola, V., Saxena, V., Jain, D., Goyal, P., and Sikdar, B. (2019). A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access 7, 82721–82743. doi:10.1109/access.2019.2924045
Ilyas, M. U., Ahmad, M., and Saleem, S. (2020). Internet-of-Things-Infrastructure-as-a-Service: The democratization of access to public internet-of-things infrastructure. Int. J. Commun. Syst. 33, e4562. doi:10.1002/dac.4562
Jamil, A. R. M., Ganguly, K. K., and Nower, N. (2020). Adaptive traffic signal control system using composite reward architecture based deep reinforcement learning. IET Intell. Transp. Syst. 14, 2030–2041. doi:10.1049/iet-its.2020.0443
Khanam, S., Ahmedy, I. B., Idris, M. Y. I., Jaward, M. H., and Sabri, A. Q. B. M. (2020). A survey of security challenges, attacks taxonomy and advanced countermeasures in the internet of things. IEEE Access 8, 219709–219743. doi:10.1109/access.2020.3037359
Khoa, T. A., Nhu, L. M. B., Son, H. H., Trong, N. M., Phuc, C. H., Phuong, N. T. H., et al. (2020). Designing efficient smart home management with IoT smart lighting: A case study. Wireless Communications and mobile computing 2020 .
Kim, J., and Park, N. (2022). De-identification mechanism of user data in video systems according to risk level for preventing leakage of personal healthcare information. Sensors 22, 2589. doi:10.3390/s22072589
Kshirsagar, A., and Patil, N. (2021). “IoT based smart lock with predictive maintenance,” in 2021 12th International Conference on Computing Communication and Networking Technologies (ICCCNT) ( IEEE ), 1–6.
Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H., and Zhao, W. (2017). A survey on internet of things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J. 4, 1125–1142. doi:10.1109/jiot.2017.2683200
Lueth, K. L. (2020). Top 10 IoT applications in 2020. IoT analytics .
Lummus, R. R., and Vokurka, R. J. (1999). Defining supply chain management: A historical perspective and practical guidelines . Bingley, United Kingdom: Industrial Management & Data Systems .
Martín, C., Langendoerfer, P., Zarrin, P. S., Díaz, M., and Rubio, B. (2022). Kafka-ML: Connecting the data stream with ML/AI frameworks. Future Gener. Comput. Syst. 126, 15–33. doi:10.1016/j.future.2021.07.037
Mekni, S. K. (2022). “Design and implementation of a smart fire detection and monitoring system based on IoT,” in 2022 4th International Conference on Applied Automation and Industrial Diagnostics (ICAAID) ( IEEE ), 1, 1–5.
Miller, J. C., Skoll, D., and Saxon, L. A. (2021). Home monitoring of cardiac devices in the era of COVID-19. Curr. Cardiol. Rep. 23, 1–9. doi:10.1007/s11886-020-01431-w
Mobley, R. K. (2002). An introduction to predictive maintenance . Elsevier .
Mohammed, K., Zaidan, A., Zaidan, B., Albahri, O. S., Alsalem, M., Albahri, A. S., et al. (2019). Real-time remote-health monitoring systems: A review on patients prioritisation for multiple-chronic diseases, taxonomy analysis, concerns and solution procedure. J. Med. Syst. 43 (7), 1–21. doi:10.1007/s10916-019-1362-x
Moh’d Ali, M. A., Basahr, A., Rabbani, M. R., and Abdulla, Y. (2020). “Transforming business decision making with internet of things (IoT) and machine learning (ML),” in 2020 International Conference on Decision Aid Sciences and Application (DASA) ( IEEE ), 674–679.
O’Connor, Y., Rowan, W., Lynch, L., and Heavin, C. (2017). Privacy by design: Informed consent and internet of things for smart health. Procedia Comput. Sci. 113, 653–658. doi:10.1016/j.procs.2017.08.329
Ozdemir, D., Sharma, M., Dhir, A., and Daim, T. (2022). Supply chain resilience during the COVID-19 pandemic. Technol. Soc. 68, 101847. doi:10.1016/j.techsoc.2021.101847
Pavithra, D., and Balakrishnan, R. (2015). “IoT based monitoring and control system for home automation,” in 2015 Global Conference on Communication Technologies (GCCT) ( IEEE ), 169–173.
Pekar, A., Mocnej, J., Seah, W. K., and Zolotova, I. (2020). Application domain-based overview of IoT network traffic characteristics. ACM Comput. Surv. 53, 1–33. doi:10.1145/3399669
Poslad, S., Ma, A., Wang, Z., and Mei, H. (2015). Using a smart city IoT to incentivise and target shifts in mobility behaviour—is it a piece of pie? Sensors 15, 13069–13096. doi:10.3390/s150613069
Saarika, P., Sandhya, K., and Sudha, T. (2017). “Smart transportation system using IoT,” in 2017 International Conference on Smart Technologies for Smart Nation (SmartTechCon) ( IEEE ), 1104–1107.
Sarkar, C., Nambi, S. A. U., Prasad, R. V., and Rahim, A. (2014). “A scalable distributed architecture towards unifying IoT applications,” in 2014 IEEE World Forum on Internet of Things (WF-IoT) ( IEEE ), 508–513.
Selcuk, S. (2017). “Predictive maintenance, its implementation and latest trends,” in Proceedings of the Institution of Mechanical Engineers, Part B: Journal of Engineering Manufacture , 231, 1670–1679. doi:10.1177/0954405415601640
Selvaraj, S., and Sundaravaradhan, S. (2020). Challenges and opportunities in IoT healthcare systems: A systematic review. SN Appl. Sci. 2, 139–148. doi:10.1007/s42452-019-1925-y
Tan, W. C., and Sidhu, M. S. (2022). Review of RFID and IoT integration in supply chain management . Amsterdam, Netherlands: Operations Research Perspectives , 100229.
Tang, X., Wang, X., Cattley, R., Gu, F., and Ball, A. D. (2018). Energy harvesting technologies for achieving self-powered wireless sensor networks in machine condition monitoring: A review. Sensors 18, 4113. doi:10.3390/s18124113
Vaskov, S., Kousik, S., Larson, H., Bu, F., Ward, J., Worrall, S., et al. (2019). Towards provably not-at-fault control of autonomous robots in arbitrary dynamic environments. arXiv Preprint arXiv:1902.02851
Vishwakarma, S. K., Upadhyaya, P., Kumari, B., and Mishra, A. K. (2019). “Smart energy efficient home automation system using IoT,” in 2019 4th International Conference on Internet of Things: Smart Innovation and Usages (IoT-SIU) ( IEEE ), 1–4.
Wang, X., Tjalkens, T., and Linnartz, J.-P. (2017). “Smart office lighting control using occupancy sensors,” in 2017 IEEE 14th International Conference on Networking, Sensing and Control (ICNSC) ( IEEE ), 453–458.
Weber, M., and Podnar Žarko, I. (2019). A regulatory view on smart city services. Sensors 19, 415. doi:10.3390/s19020415
Yang, S. (2003). A condition-based failure-prediction and processing-scheme for preventive maintenance. IEEE Trans. Reliab. 52, 373–383. doi:10.1109/tr.2003.816402
Zhang, Q., Zhang, Q., Shi, W., and Zhong, H. (2018). Distributed collaborative execution on the edges and its application to amber alerts. IEEE Internet Things J. 5, 3580–3593. doi:10.1109/jiot.2018.2845898
Zonta, T., Da Costa, C. A., da Rosa Righi, R., de Lima, M. J., da Trindade, E. S., and Li, G. P. (2020). Predictive maintenance in the industry 4.0: A systematic literature review. Comput. Industrial Eng. 150, 106889. doi:10.1016/j.cie.2020.106889
Keywords: internet of things, IoT challenges, IoT new trends, IoT applications, IoT grand vision
Citation: Elgazzar K, Khalil H, Alghamdi T, Badr A, Abdelkader G, Elewah A and Buyya R (2022) Revisiting the internet of things: New trends, opportunities and grand challenges. Front. Internet. Things 1:1073780. doi: 10.3389/friot.2022.1073780
Received: 18 October 2022; Accepted: 07 November 2022; Published: 21 November 2022.
Edited and reviewed by:
Copyright © 2022 Elgazzar, Khalil, Alghamdi, Badr, Abdelkader, Elewah and Buyya. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Khalid Elgazzar, [email protected]
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
Information
- Author Services
Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Journal Proposal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Article Menu

- Subscribe SciFeed
- Recommended Articles
- Author Biographies
- Google Scholar
- on Google Scholar
- Table of Contents
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
JSmol Viewer
Floatingblue: a delay tolerant networks-enabled internet of things architecture for remote areas combining data mules and low power communications.

1. Introduction
- Innovative architecture: development of a new WSN architecture that expands network coverage through data mules communicating via DTN, while reducing energy consumption at terminal nodes by utilizing an optimized BLE protocol.
- Real-world validation: practical implementation and extensive testing in a real-world scenario in the Amazon, demonstrating the viability and efficiency of the “FloatingBlue” architecture in adverse environments.
- Energy consumption optimization: development of optimized firmware for BLE devices, resulting in significantly lower energy consumption than traditional approaches, which is crucial for extending the lifespan of sensors in remote areas.
2. Related Studies
3. floatingblue, 4. implementation, 4.1. hardware, 4.2. embedded software, 5.1. energy consumption analysis experiments for sns, 5.2. functional experiments of the floatingblue architecture, 5.3. sn communication range experiments, 5.4. discussions, 6. conclusions and future work.
- The requirement for line-of-sight conditions for efficient communication between sensor nodes and DMs, which can be compromised in scenarios with many obstacles, such as dense forests or rugged terrain. Investigation: incorporate LoRa radio technology into the physical layer of the DM to increase communication range;
- Data security during transmission was not investigated, and future work could focus on implementing protocols to ensure data integrity and confidentiality. Investigation: developing an application-level security protocol to protect data transmitted by EN;
- The dependency on batteries for the sensor nodes, as battery power can quickly deplete under conditions of high transmission frequency. Investigation: adopting a protocol that allows storage and transmission of messages from SN in multiple advertising packets.
- The need for scalability testing with more SNs and DMs. Investigation: conduct studies through computer network simulations to analyze and verify the network’s behavior on a large scale.
Author Contributions
Institutional review board statement, informed consent statement, data availability statement, acknowledgments, conflicts of interest, abbreviations.
| AA | Application Agent |
| BLE | Bluetooth Low Energy |
| CLA | Convergence Layer Adapter |
| DM | Data Mule |
| DTN | Delay Tolerant Networks |
| IEEE | Institute of Electrical and Electronics Engineers |
| IoT | Internet of Things |
| LDO | Low-Dropout |
| LPWAN | Low-Power Wide-Area Network |
| PDA | Public Device Addresses |
| PDR | Packet Delivery Ratio |
| PDU | Packet Data Unit |
| PPE | Personal Protective Equipment |
| RAM | Random Access Memory |
| RFC | Request for Comments |
| RTOS | Real-Time Operating System |
| SDK | Software Development Kit |
| SN | Sensor Node |
| SoC | System-on-a-Chip |
| TCPCL | Transmission Control Protocol Convergence-Layer |
| UAV | Unmanned Aerial Vehicles |
| WSNs | Wireless Sensor Networks |
| WuR | Wake-up Radio |
- Murrins Misiukas, J.; Carter, S.; Herold, M. Tropical Forest Monitoring: Challenges and Recent Progress in Research. Remote Sens. 2021 , 13 , 2252. [ Google Scholar ] [ CrossRef ]
- Boehm, M.; Wermser, D. Sensor Networks for Forestry Applications operating with Limited Power Supply using LPWAN COTS Equipment. In Proceedings of the Mobile Communication—Technologies and Applications, 27th ITG-Symposium, Osnabrueck, Germany, 10–11 May 2023; pp. 85–90. [ Google Scholar ]
- Zheng, K.; Luo, R.; Liu, X.; Qiu, J.; Liu, J. Distributed DDPG-Based Resource Allocation for Age of Information Minimization in Mobile Wireless-Powered Internet of Things. IEEE Internet Things J. 2024 , 11 , 29102–29115. [ Google Scholar ] [ CrossRef ]
- Myagmardulam, B.; Miura, R.; Ono, F.; Kagawa, T.; Shan, L.; Nakayama, T.; Kojima, F.; Choijil, B. Performance Evaluation of LoRa 920 MHz Frequency Band in a Hilly Forested Area. Electronics 2021 , 10 , 502. [ Google Scholar ] [ CrossRef ]
- Finnegan, J.; Brown, S. A comparative survey of LPWA networking. arXiv 2018 , arXiv:1802.04222. [ Google Scholar ]
- Baumgärtner, L.; Lieser, P.; Zobel, J.; Bloessl, B.; Steinmetz, R.; Mezini, M. LoRAgent: A DTN-based Location-aware Communication System using LoRa. In Proceedings of the 2020 IEEE Global Humanitarian Technology Conference (GHTC), Seattle, WA, USA, 29 October–1 November 2020; pp. 1–8. [ Google Scholar ] [ CrossRef ]
- Höchst, J.; Baumgärtner, L.; Kuntke, F.; Penning, A.; Sterz, A.; Freisleben, B. Lora-based device-to-device smartphone communication for crisis scenarios. In Proceedings of the 17th International Conference on Information Systems for Crisis Response and Management (ISCRAM), Blacksburg, VA, USA, 24–27 May 2020. [ Google Scholar ]
- Baumgärtner, L.; Penning, A.; Lampe, P.; Richerzhagen, B.; Steinmetz, R.; Freisleben, B. Environmental monitoring using low-cost hardware and infrastructureless wireless communication. In Proceedings of the 2018 IEEE Global Humanitarian Technology Conference (GHTC), San Jose, CA, USA, 18–21 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–8. [ Google Scholar ]
- Palma, D.; Zolich, A.; Jiang, Y.; Johansen, T.A. Unmanned Aerial Vehicles as Data Mules: An Experimental Assessment. IEEE Access 2017 , 5 , 24716–24726. [ Google Scholar ] [ CrossRef ]
- Mertens, J.; Milotta, G.; Nagaradjane, P.; Morabito, G. SDN-(UAV) ISE: Applying software defined networking to wireless sensor networks with data mules. In Proceedings of the 2020 IEEE 21st International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Cork, Ireland, 31 August–3 September 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 323–328. [ Google Scholar ]
- Sugiura, S.; Yamada, Y.; Yoshizaki, T.; Naitot, K. Proposal of service framework for information sharing based on delay tolerant networks. In Proceedings of the 2020 IEEE 17th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–2. [ Google Scholar ]
- Djidi, N.E.H.; Gautier, M.; Courtay, A.; Berder, O.; Magno, M. On-demand LoRa: Asynchronous TDMA for energy efficient and low latency communication in IoT. Sensors 2021 , 21 , 733. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Solpico, D.; Tan, M.; Manalansan, E.; Zagala, F.; Leceta, J.; Lanuza, D.; Bernal, J.; Ramos, R.; Villareal, R.; Cruz, X.; et al. Application of the V-HUB standard using LoRa beacons, mobile cloud, UAVs, and DTN for disaster-resilient communications. In Proceedings of the 2019 IEEE Global Humanitarian Technology Conference (GHTC), Seattle, WA, USA, 17–20 October 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–8. [ Google Scholar ]
- Bujari, A.; Calafate, C.T.; Cano, J.C.; Manzoni, P.; Palazzi, C.E.; Ronzani, D. A location-aware waypoint-based routing protocol for airborne DTNs in search and rescue scenarios. Sensors 2018 , 18 , 3758. [ Google Scholar ] [ CrossRef ]
- Jeon, K.E.; She, J.; Soonsawad, P.; Ng, P.C. Ble beacons for internet of things applications: Survey, challenges, and opportunities. IEEE Internet Things J. 2018 , 5 , 811–828. [ Google Scholar ] [ CrossRef ]
- Gomez-de Gabriel, J.M.; Fernández-Madrigal, J.A.; Lopez-Arquillos, A.; Rubio-Romero, J.C. Monitoring harness use in construction with BLE beacons. Measurement 2019 , 131 , 329–340. [ Google Scholar ] [ CrossRef ]
- Ayele, E.D.; Meratnia, N.; Havinga, P.J. Towards a new opportunistic IoT network architecture for wildlife monitoring system. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–5. [ Google Scholar ]
- Szymczyk, M.; Augustyniak, P. Selected Energy Consumption Aspects of Sensor Data Transmission in Distributed Multi-Microcontroller Embedded Systems. Electronics 2022 , 11 , 848. [ Google Scholar ] [ CrossRef ]
- Muteba, F.; Djouani, K.; Olwal, T. A comparative survey study on LPWA IoT technologies: Design, considerations, challenges and solutions. Procedia Comput. Sci. 2019 , 155 , 636–641. [ Google Scholar ] [ CrossRef ]
- Dian, F.J. An analytical scheme for power consumption of battery-operated peripheral BLE nodes. In Proceedings of the 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1021–1026. [ Google Scholar ]
- Soubelet, A.; Pathinarupothi, R.K.; Rangan, E.S.; Durga, P.; Menon, K.U. Internet-of-things based respiratory rate monitoring for early detection of cardiovascular and pulmonary diseases. In Proceedings of the 5th EAI International Conference on IoT Technologies for HealthCare, Guimarães, Portugal, 21–23 November 2018; Springer: Berlin/Heidelberg, Germany, 2020; pp. 97–106. [ Google Scholar ]
- Alfian, G.; Syafrudin, M.; Ijaz, M.F.; Syaekhoni, M.A.; Fitriyani, N.L.; Rhee, J. A personalized healthcare monitoring system for diabetic patients by utilizing BLE-based sensors and real-time data processing. Sensors 2018 , 18 , 2183. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Schrader, R.; Ax, T.; Röhrig, C.; Fühner, C. Advertising power consumption of bluetooth low energy systems. In Proceedings of the 2016 3rd International Symposium on Wireless Systems within the Conferences on Intelligent Data Acquisition and Advanced Computing Systems (IDAACS-SWS), Offenburg, Germany, 26–27 September 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 62–68. [ Google Scholar ]
- Aguilar, S.; Vidal, R.; Gomez, C. Opportunistic sensor data collection with bluetooth low energy. Sensors 2017 , 17 , 159. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Bdiri, S.; Derbel, F. A nanowatt Wake-Up Receiver for industrial production line. In Proceedings of the 2014 IEEE 11th International Multi-Conference on Systems, Signals & Devices (SSD14), Barcelona, Spain, 11–14 February 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 1–6. [ Google Scholar ]
- Piyare, R.; Murphy, A.L.; Kiraly, C.; Tosato, P.; Brunelli, D. Ultra low power wake-up radios: A hardware and networking survey. IEEE Commun. Surv. Tutor. 2017 , 19 , 2117–2157. [ Google Scholar ] [ CrossRef ]
- Ahmad, K.; Fathima, M.; Hossen, M.S.; Ahamed, J.; Ahmad, K.A.B. Opportunistic Networks: An Empirical Research of Routing Protocols and Mobility Models. SN Comput. Sci. 2023 , 4 , 652. [ Google Scholar ] [ CrossRef ]
- Warthman, F. Delay-and disruption-tolerant networks (DTNs). In A Tutorial, Version 3.2 ; Interplanetary Internet Special Interest Group: Reston, VA, USA, 2012; pp. 5–9. [ Google Scholar ]
- Herlin, A.; Brunberg, E.; Hultgren, J.; Högberg, N.; Rydberg, A.; Skarin, A. Animal Welfare Implications of Digital Tools for Monitoring and Management of Cattle and Sheep on Pasture. Animals 2021 , 11 , 829. [ Google Scholar ] [ CrossRef ]
- Povlsen, P.; Bruhn, D.; Durdevic, P.; Arroyo, D.O.; Pertoldi, C. Using YOLO Object Detection to Identify Hare and Roe Deer in Thermal Aerial Video Footage—Possible Future Applications in Real-Time Automatic Drone Surveillance and Wildlife Monitoring. Drones 2024 , 8 , 2. [ Google Scholar ] [ CrossRef ]
- Sangaiah, A.K.; Yu, F.N.; Lin, Y.B.; Shen, W.C.; Sharma, A. UAV T-YOLO-Rice: An Enhanced Tiny Yolo Networks for Rice Leaves Diseases Detection in Paddy Agronomy. IEEE Trans. Netw. Sci. Eng. 2024 , 1–16. [ Google Scholar ] [ CrossRef ]
- Liu, X.; Li, B.; Chen, M.; Wang, X.; Zou, Q. Research on DTN Based Interconnecting ZigBee Network Techniques. In Proceedings of the 2011 7th International Conference on Wireless Communications, Networking and Mobile Computing, Wuhan, China, 23–25 September 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 1–4. [ Google Scholar ]
- Kulla, E.; Shintani, K.; Matsuo, K. Mobility-Aware Narrow Routing Protocol for Underwater Wireless Sensor Networks. In Proceedings of the Advances in Internet, Data & Web Technologies: The 10th International Conference on Emerging Internet, Data and Web Technologies (EIDWT-2022), Okayama, Japan, 24–26 February 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 245–253. [ Google Scholar ]
- Mallorquí, A.; Zaballos, A.; Serra, D. The Antarctic Delay Tolerant Network. In Proceedings of the 2022 IEEE Symposium on Computers and Communications (ISCC), Rhodes, Greece, 30 June–3 July 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–7. [ Google Scholar ]
- Ochiai, H.; Ishizuka, H.; Kawakami, Y.; Esaki, H. A DTN-based sensor data gathering for agricultural applications. IEEE Sens. J. 2011 , 11 , 2861–2868. [ Google Scholar ] [ CrossRef ]
- Mota, V.F.; Cunha, F.D.; Macedo, D.F.; Nogueira, J.M.; Loureiro, A.A. Protocols, mobility models and tools in opportunistic networks: A survey. Comput. Commun. 2014 , 48 , 5–19. [ Google Scholar ] [ CrossRef ]
- Khalil, A.; Abou Haidar, N.; Bassil, G.; Chbeir, R. Adaptive resource management solution for ad-hoc opportunistic networks. Wirel. Pers. Commun. 2021 , 117 , 1931–1958. [ Google Scholar ] [ CrossRef ]
- Tsai, Y.R.; Chen, Y.C. Opportunistic Connectionless Undirected Information Dissemination Based on Bluetooth Low Energy Advertising Technology on Smartphones. IEEE Access 2021 , 9 , 155851–155860. [ Google Scholar ] [ CrossRef ]
- Chen, J.; Dai, Z.; Chen, Z. Development of radio-frequency sensor wake-up with unmanned aerial vehicles as an aerial gateway. Sensors 2019 , 19 , 1047. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Rahmadhani, M.A.; Yovita, L.V.; Mayasari, R. Energy Consumption and Packet Loss Analysis of LEACH Routing Protocol on WSN Over DTN. In Proceedings of the 2018 4th International Conference on Wireless and Telematics (ICWT), Nusa Dua, Indonesia, 12–13 July 2018; pp. 1–5. [ Google Scholar ] [ CrossRef ]
- Banerjee, N.; Corner, M.D.; Levine, B.N. An energy-efficient architecture for DTN throwboxes. In Proceedings of the IEEE INFOCOM 2007-26th IEEE International Conference on Computer Communications, Anchorage, AK, USA, 6–12 May 2007; IEEE: Piscataway, NJ, USA, 2007; pp. 776–784. [ Google Scholar ]
- Sheshashayee, A.V.; Buczek, J.; Petrioli, C.; Basagni, S. Experimental Evaluation of Wake-up Radio Ranges for UAV-assisted Mobile Data Collection. In Proceedings of the 2022 IEEE Wireless Communications and Networking Conference (WCNC), Austin, TX, USA, 10–13 April 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 716–721. [ Google Scholar ]
- Trotta, A.; Di Felice, M.; Bononi, L.; Perilli, L.; Scarselli, E.F.; Cinotti, T.S. Throughput Enhancement in UAV-aided Wireless Sensor Networks via Wake-Up Radio Technology and Priority-based MAC Scheme. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [ Google Scholar ]
- Trotta, A.; Di Felice, M.; Perilli, L.; Scarselli, E.F.; Cinotti, T.S. BEE-DRONES: Ultra low-power monitoring systems based on unmanned aerial vehicles and wake-up radio ground sensors. Comput. Netw. 2020 , 180 , 107425. [ Google Scholar ] [ CrossRef ]
- Komarov, M.; Moltchanov, D. System design and analysis of UAV-assisted BLE Wireless Sensor Systems. In Proceedings of the Wired/Wireless Internet Communications: 14th IFIP WG 6.2 International Conference, WWIC 2016, Thessaloniki, Greece, 25–27 May 2016; Proceedings 14. Springer: Berlin/Heidelberg, Germany, 2016; pp. 284–296. [ Google Scholar ]
- Sipos, B.; Demmer, M.; Ott, J.; Perreault, S. Delay-Tolerant Networking TCP Convergence-Layer Protocol Version 4. Brandin Court Fremont, CA, USA, RFC 9174, 2022. Available online: https://www.rfc-editor.org/info/rfc9174 (accessed on 10 September 2024).
Click here to enlarge figure
| Work | Year | End-Node Technology | DTN/OppNet | Sleep Mode | Tx Mode | Range (m) |
|---|---|---|---|---|---|---|
| [ ] | 2019 | Zigbee | [ ] | 50 µW | 15 mW | 7 |
| [ ] | 2018 | Zigbee | [✓] | 181 mW | 825 mW | 100 |
| [ ] | 2007 | Zigbee | [✓] | 80 mW | NA | 1000 |
| [ ] | 2020 | LoRa | [✓] | 72 µW | 648 uW | NA |
| [ ] | 2020 | LoRa | [✓] | 231 mW | 660 mW | NA |
| [ ] | 2018 | LoRa | [✓] | 24 mW | 27 mW | NA |
| [ ] | 2022 | IEEE 802.11 | [ ] | 9 µJ | 41 µJ | 25 |
| [ ] | 2020 | IEEE 802.11 | [ ] | 14 µW | 494 µJ | NA |
| [ ] | 2011 | Various | [✓] | 633 nJ | 100 mW | 5 |
| [ ] | 2018 | BLE | [✓] | NA | NA | 200 |
| [ ] | 2017 | BLE | [✓] | 3.5 µJ | 120 µJ | 200 |
| [ ] | 2016 | BLE | [ ] | NA | 57 mW | NA |
| Firmware | Sleep Mode (µJ) | Tx Mode (µJ) |
|---|---|---|
| RTOS | 13.4 | 24 |
| Bare-Metal | 2.25 | 11.8 |
| Description | Parameter |
|---|---|
| Discovery Protocol | IPV4 e IPV6 |
| Websocket | ws://0.0.0.0:8080/ws |
| CLA protocol | TCPCL |
| Routing Algorithm | Epidemic |
| Node-id | dtn://node-name/ |
| Work | Year | End-Node Technology | DTN/OppNet | Sleep Mode | Tx Mode | Range (m) |
|---|---|---|---|---|---|---|
| [ ] | 2019 | Zigbee | [ ] | 50 µW | 15 mW | 7 |
| [ ] | 2018 | Zigbee | [✓] | 181 mW | 825 mW | 100 |
| [ ] | 2007 | Zigbee | [✓] | 80 mW | NA | 1000 |
| [ ] | 2020 | LoRa | [✓] | 72 µW | 648 µW | NA |
| [ ] | 2020 | LoRa | [✓] | 231 mW | 660 mW | NA |
| [ ] | 2018 | LoRa | [✓] | 24 mW | 27 mW | NA |
| [ ] | 2022 | IEEE 802.11 | [ ] | 9 µJ | 41 µJ | 25 |
| [ ] | 2020 | IEEE 802.11 | [ ] | 14 µW | 494 µJ | NA |
| [ ] | 2011 | Various | [✓] | 633 nJ | 100 mW | 5 |
| [ ] | 2018 | BLE | [✓] | NA | NA | ~200 |
| [ ] | 2017 | BLE | [✓] | 3.5 µJ | 120 µJ | ~200 |
| [ ] | 2016 | BLE | [ ] | NA | 57 mW | NA |
| FloatingBlue | 2024 | BLE | [✓] | 2.25 µJ | 11.8 µJ | ~200 |
| The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
Share and Cite
Teixeira, R.C.M.; Carvalho, C.B.; Calafate, C.T.; Mota, E.; Fernandes, R.A.; Printes, A.L.; Nascimento, L.B.F. FloatingBlue: A Delay Tolerant Networks-Enabled Internet of Things Architecture for Remote Areas Combining Data Mules and Low Power Communications. Sensors 2024 , 24 , 6218. https://doi.org/10.3390/s24196218
Teixeira RCM, Carvalho CB, Calafate CT, Mota E, Fernandes RA, Printes AL, Nascimento LBF. FloatingBlue: A Delay Tolerant Networks-Enabled Internet of Things Architecture for Remote Areas Combining Data Mules and Low Power Communications. Sensors . 2024; 24(19):6218. https://doi.org/10.3390/s24196218
Teixeira, Ruan C. M., Celso B. Carvalho, Carlos T. Calafate, Edjair Mota, Rubens A. Fernandes, Andre L. Printes, and Lennon B. F. Nascimento. 2024. "FloatingBlue: A Delay Tolerant Networks-Enabled Internet of Things Architecture for Remote Areas Combining Data Mules and Low Power Communications" Sensors 24, no. 19: 6218. https://doi.org/10.3390/s24196218
Article Metrics
Article access statistics, further information, mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Evolution of topics and trends in emerging research fields: multiple analyses with entity linking, Mann–Kendall test and burst methods in cloud computing
- Published: 26 September 2024
Cite this article

- Mario Coccia 1 &
- Saeed Roshani ORCID: orcid.org/0000-0001-5851-2867 2
The principal goal of this study is to analyze the evolution of topics and trends in emerging research fields by a combination of entity linking, Mann–Kendall test, and burst detection techniques. Multiple methods are applied here in the emerging field of cloud computing by focusing on the frequency of critical topics from 2004 to 2021. Statistical analysis reveals that the Internet of Things exhibits a significant scientific growth compared to other subject areas within the research field of cloud computing. Other emerging topics with rapid growth are computer networks, encryption, big data, distributed computing, and interaction of cloud computing with virtual machine research. The combination of different techniques can better show the complex dynamics and complementary aspects of scientific topics and trends underlying evolutionary pathways in emerging fields, such as the science and technology advances of architecture, hardware, and software components in the field of cloud computing. In scientometrics, the analysis with multiple techniques provides comprehensive scientific and technological information driving new directions in the evolution of research fields to guide R&D investments towards growing topics and technologies having the potential of supporting fruitful scientific and technological change.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Subscribe and save.
- Get 10 units per month
- Download Article/Chapter or eBook
- 1 Unit = 1 Article or 1 Chapter
- Cancel anytime
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others
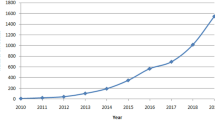
Emerging trends and global scope of big data analytics: a scientometric analysis
A bibliometric approach to tracking big data research trends.
An overview of cloud computing in SMEs
Explore related subjects.
- Artificial Intelligence
Data availability statement
Data Availability at the Web of Science 2022. Documents. https://www.webofscience.com/wos/woscc/basic-search (Accessed in February 2022).
Alhomdy, S., Thabit, F., Abdulrazzak, F. A. H., Haldorai, A., & Jagtap, S. (2021). The role of cloud computing technology: A savior to fight the lockdown in COVID 19 crisis, the benefits, characteristics and applications. International Journal of Intelligent Networks, 2 , 166–174. https://doi.org/10.1016/j.ijin.2021.08.001
Article Google Scholar
Ali, O., Shrestha, A., Osmanaj, V., & Muhammed, S. (2020). Cloud computing technology adoption: An evaluation of key factors in local governments. Information Technology & People, 34 (2), 666–703. https://doi.org/10.1108/ITP-03-2019-0119
Ali, R. O., & Abubaker, S. R. (2019). Trend analysis using Mann–Kendall, Sen’s slope estimator test and innovative trend analysis method in Yangtze River basin, China. International Journal of Engineering & Technology, 8 (2), 110–119.
Google Scholar
Al-Ruithe, M., Benkhelifa, E., & Hameed, K. (2018). Key issues for embracing the cloud computing to adopt a digital transformation: A study of Saudi public sector. Procedia Computer Science, 130 , 1037–1043.
Ayaz, A., Celik, K., & Ozyurt, O. (2021). Pattern detection in cloud computing: Bibliometric mapping of publications in the field from past to present. COLLNET Journal of Scientometrics and Information Management, 15 (2), 469–494.
Baumann, M. (2015). Historic and potential technology transition paths of grid battery storage: Co-evolution of energy grid, electric mobility and batteries (No. 02/2015). Universidade Nova de Lisboa, IET/CICS. NOVA-Interdisciplinary Centre on Social Sciences, Faculty of Science and Technology.
Bird, A. (2022). Thomas Kuhn. In E.N. Zalta (Ed.), The Stanford encyclopedia of philosophy (Spring 2022 Edition). https://plato.stanford.edu/archives/spr2022/entries/thomas-kuhn/ .
Blei, D. M., Lafferty, J. D. (2006). Dynamic topic models. In Proceedings of the 23rd international conference on machine learning (pp. 113–120). https://doi.org/10.1145/1143844.1143859
Blei, D. M. (2012). Probabilistic topic models. Communications of the ACM, 55 (4), 77–84. https://doi.org/10.1145/2133806.2133826
Blei, D. M., Ng, A. Y., & Jordan, M. I. (2003). Latent Dirichlet allocation. The Journal of Machine Learning Research, 3 , 993–1022.
Brem Petra A., Nylund Saeed, Roshani. (2023). Unpacking the complexities of crisis innovation: a comprehensive review of ecosystem-level responses to exogenous shocks. Abstract Review of Managerial Science 18 (8), 2441–2464. https://doi.org/10.1007/s11846-023-00709-x
Burgin, M., Eberbach, E., & Mikkilineni, R. (2019). Cloud computing and cloud automata as a new paradigm for computation. Computer Reviews Journal, 4 , 113–134.
Buyya, R., Yeo, C. S., Venugopal, S., Broberg, J., & Brandic, I. (2009). Cloud computing and emerging IT platforms: Vision, hype, and reality for delivering computing as the 5th utility. Future Generation Computer Systems, 25 (6), 599–616.
Cai, Y., Lu, W., Wang, L., & Xing, W. (2015). Cloud computing research analysis using bibliometric method. International Journal of Software Engineering and Knowledge Engineering, 25 (03), 551–571.
Chen, B., Tsutsui, S., Ding, Y., & Ma, F. (2017). Understanding the topic evolution in a scientific domain: An exploratory study for the field of information retrieval. Journal of Informetrics, 11 (4), 1175–1189. https://doi.org/10.1016/j.joi.2017.10.003
Coccia, M. (2017). Sources of technological innovation: Radical and incremental innovation problem-driven to support competitive advantage of firms. Technology Analysis & Strategic Management, 29 (9), 1048–1061. https://doi.org/10.1080/09537325.2016.1268682
Coccia, M. (2018). Classification of innovation considering technological interaction. Journal of Economics Bibliography, 5 (2), 76–93. https://doi.org/10.1453/jeb.v5i2.1650
Coccia, M. (2018a). General properties of the evolution of research fields: a scientometric study of human microbiome evolutionary robotics and astrobiology. Scientometrics, 117 (2), 1265–1283. https://doi.org/10.1007/s11192-018-2902-8
Coccia, M. (2019). What is technology and technology change? A new conception with systemic-purposeful perspective for technology analysis. Journal of Social and Administrative Sciences, 6 (3), 145–169. https://doi.org/10.1453/jsas.v6i3.1957
Coccia, M. (2020). Destructive technologies for industrial and corporate change. In A. Farazmand (Ed.), Global encyclopedia of public administration, public policy, and governance. Cham: Springer. https://doi.org/10.1007/978-3-319-31816-5_3972-1
Chapter Google Scholar
Coccia, M. (2020a). The evolution of scientific disciplines in applied sciences: dynamics and empirical properties of experimental physics. Scientometrics, 124 (1), 451–487. https://doi.org/10.1007/s11192-020-03464-y
Coccia, M. (2024a). Converging artificial intelligence and quantum technologies: Accelerated growth effects in technological evolution. Technologies, 12 (5), 66. https://doi.org/10.3390/technologies12050066
Coccia, M. (2024b). The general theory of scientific variability for technological evolution. Science, 6 (2), 31. https://doi.org/10.3390/sci6020031
Coccia M., Bozeman B. (2016). Allometric models to measure and analyze the evolution of international research collaboration. Scientometrics, 108 (3), 1065–1084. https://doi.org/10.1007/s11192-016-2027-x
Coccia, M. (2021). Technological innovation. In G. Ritzer & C. Rojek (Eds.), The Blackwell encyclopedia of sociology. Wiley. https://doi.org/10.1002/9781405165518.wbeost011.pub2
Coccia, M. (2022). Probability of discoveries between research fields to explain scientific and technological change. Technology in Society, 68 , 101874. https://doi.org/10.1016/j.techsoc.2022.101874
Coccia, M. 2024. Technological trajectories in quantum computing to design a quantum ecosystem for industrial change. Technology Analysis & Strategic Management, 36 (8), 1733–1748. https://doi.org/10.1080/09537325.2022.2110056
Coccia M; Roshani M. (2024). Path-breaking directions in quantum computing technology: A patent analysis with multiple techniques. Journal of the Knowledge Economy . https://doi.org/10.1007/s13132-024-01977-y
Costas, R., Corona-Sorbino, C., Robinson-Garcìa, N. (2024). Handbook of meta-research could ORCID play a key role in meta-research? Discussing new analytical possibilities to study the dynamics of science and scientists. Edward Elgar Publishing 215–232
Coccia M., Roshani, S. (2024a). General laws of funding for scientific citations: how citations change in funded and unfunded research between basic and applied sciences. Journal of Data and Information Science, 9 (1), 1–18. https://doi.org/10.2478/jdis-2024-0005
Coccia, M., Roshani, S. (2024b). Research funding and citations in papers of nobel laureates in physics, chemistry and medicine, 2019-2020. Journal of Data and Information Science, 9 (2), 1–25. https://doi.org/10.2478/jdis-2024-0006
Coccia Lili M, Wang (2016) Evolution and convergence of the patterns of international scientific collaboration. Significance Proceedings of the National Academy of Sciences, 113 (8), 2057–2061. https://doi.org/10.1073/pnas.1510820113
Coccia, M., Watts J. 2020. A theory of the evolution of technology: technological parasitism and the implications for innovation management. Journal of Engineering and Technology Management, 55 , 101552, https://doi.org/10.1016/j.jengtecman.2019.11.003
Coccia, M., Roshani S., Mosleh M. (2021). Scientific developments and new technological trajectories in sensor. Research Sensors, 21 (23), 7803. https://doi.org/10.3390/s21237803
Coccia, M., Mosleh, M., & Roshani, S. (2024). Evolution of quantum computing: Theoretical and innovation management implications for emerging quantum industry. IEEE Transactions on Engineering Management, 71 , 2270–2280. https://doi.org/10.1109/TEM.2022.3175633
Coccia, M., & Roshani, S. (2024). Evolutionary phases in emerging technologies: Theoretical and managerial implications from quantum technologies. IEEE Transactions on Engineering Management . https://doi.org/10.1109/TEM.2024.3385116
Coccia, M., Roshani, S., & Mosleh, M. (2022). Evolution of sensor research for clarifying the dynamics and properties of future directions. Sensors, 22 (23), 9419. https://doi.org/10.3390/s22239419
Cornolti, M., Ferragina, P., & Ciaramita, M. (2013). A framework for benchmarking entity-annotation systems. In Proceedings of the 22nd international conference on World Wide Web (pp. 249–260).
Cresswell, K., Hernández, A. D., Williams, R., & Sheikh, A. (2022). Key challenges and opportunities for cloud technology in health care: Semistructured interview study. JMIR Human Factors, 9 (1), e31246.
Curiac, C. D., & Micea, M. V. (2023). Identifying hot information security topics Using LDA and multivariate Mann–Kendall test. IEEE Access, 11 , 18374–18384.
Cuzzola, J., Jovanović, J., Bagheri, E., & Gašević, D. (2015). Evolutionary fine-tuning of automated semantic annotation systems. Expert Systems with Applications, 42 (20), 6864–6877.
Darwish, A., Hassanien, A. E., Elhoseny, M., Sangaiah, A. K., & Muhammad, K. (2019). The impact of the hybrid platform of internet of things and cloud computing on healthcare systems: Opportunities, challenges, and open problems. Journal of Ambient Intelligence and Humanized Computing, 10 , 4151–4166.
Dernis, H., Squicciarini, M., & de Pinho, R. (2016). Detecting the emergence of technologies and the evolution and co-development trajectories in science (DETECTS): A ‘burst ’analysis-based approach. The Journal of Technology Transfer, 41 , 930–960.
Ebadi, A., Tremblay, S., Goutte, C., & Schiffauerova, A. (2020). Application of machine learning techniques to assess the trends and alignment of the funded research output. Journal of Informetrics, 14 (2), 101018.
Erdogmus, H. (2009). Cloud Computing: Does Nirvana Hide Behind the Nebula? IEEE Software, 26 (2), 4–6.
Falagas, M. E., Pitsouni, E. I., Malietzis, G. A., & Pappas, G. (2008). Comparison of PubMed, Scopus, web of science, and Google scholar: Strengths and weaknesses. The FASEB Journal, 22 (2), 338–342.
Ferragina, P., & Scaiella, U. (2010). Tagme: On-the-fly annotation of short text fragments (by wikipedia entities). In Proceedings of the 19th ACM international conference on Information and knowledge management (pp. 1625–1628).
Ghazinoori, S., Roshani, S., Hafezi, R., & Wood, D. A. (2023). Bursting into the Public Eye: Analyzing the Development of Renewable Energy Research Interests. Renewable Energy Focus, 47 , 100496.
Gohr, A., Hinneburg, A., Schult, R., & Spiliopoulou, M. (2009). Topic evolution in a stream of documents. In Proceedings of the 2009 SIAM international conference on data mining (Vol. 1, pp. 859–870). https://doi.org/10.1137/1.9781611972795.74
Hafezi, R., Zare, S. G., Taghikhah, F. R., & Roshani, S. (2024). How Universities Study the Future: A Critical View. Futures, 103439.
Hamed, K. H., & Rao, A. R. (1998). A modified Mann–Kendall trend test for autocorrelated data. Journal of Hydrology, 204 (1–4), 182–196.
Hassanzadeh, A., Namdarian, L., Majidpour, M., & Elahi, S. B. (2015). Developing a model to evaluate the impacts of science, technology and innovation foresight on policy-making. Technology Analysis & Strategic Management, 27 (4), 437–460.
Heilig, L., & Voß, S. (2014). A scientometric analysis of cloud computing literature. IEEE Transactions on Cloud Computing, 2 (3), 266–278.
Hoberg, P., Wollersheim, J. & Krcmar, H. (2012). The business perspective on cloud computing—A literature review of research on cloud computing. In AMCIS 2012 Proceedings (Vol. 5). http://aisel.aisnet.org/amcis2012/proceedings/EnterpriseSystems/5
Hofmann, T. (1999). Probabilistic latent semantic indexing. In Proceedings of the 22nd annual international ACM SIGIR conference on Research and development in information retrieval (pp. 50–57).
Huang, J. Y., & Chen, R. C. (2019). Exploring the intellectual structure of cloud patents using non-exhaustive overlaps. Scientometrics, 121 (2), 739–769.
Hussain, M., & Mahmud, I. (2019). pyMannKendall: A python package for non-parametric Mann Kendall family of trend tests. Journal of Open Source Software, 4 (39), 1556. https://doi.org/10.21105/joss.01556
Huang, Hung-Tu., Hsu, Jia-Yen. (2017). Technology–function matrix based network analysis of cloud computing. Scientometrics, 113 (1), 17-44. https://doi.org/10.1007/s11192-017-2469-9
Jacobides, M. G., Brusoni, S., & Candelon, F. (2021). The evolutionary dynamics of the artificial intelligence ecosystem. Strategy Science, 6 (4), 412–435.
Kale, M., & Mente, R. (2017). Impact of cloud computing on education system. International Journal of Electronics, Electrical and Computational System IJEECS, 6 (11), 139–144.
Kendall, M. G. (1975). Rank correlation methods (4th ed.). Charles Griffin.
Kleinberg, J. (2002). Bursty and hierarchical structure in streams. In Proceedings of the eighth ACM SIGKDD international conference on knowledge discovery and data mining (pp. 91–101).
Kuhn T. (1962). The structure of scientific revolutions (1970, 2nd ed., with postscript). University of Chicago Press.
Landauer, T. K., Foltz, P. W., & Laham, D. (1998). An introduction to latent semantic analysis. Discourse Processes, 25 (2–3), 259–284.
Latifian, A. (2022). How does cloud computing help businesses to manage big data issues. Kybernetes: the International Journal of Systems & Cybernetics, 51 (6), 1917–1948. https://doi.org/10.1108/K-05-2021-0432
Linnenluecke, M. K., Marrone, M., & Singh, A. K. (2020). Conducting systematic literature reviews and bibliometric analyses. Australian Journal of Management, 45 (2), 175–194.
Liu, Y., & Wang, T. (2022). Quality factors and performance outcome of cloud-based marketing system. Kybernetes, 51 (1), 485–503. https://doi.org/10.1108/K-11-2020-0778
Liu, Z., Liu, Y., Guo, Y., & Wang, H. (2013). Progress in global parallel computing research: A bibliometric approach. Scientometrics, 95 (3), 967–983.
Lyu, Y., Li, W., Guo, Q., & Wu, H. (2024). Mapping knowledge landscapes and emerging trends of Marburg virus: A text-mining study. Heliyon, 10(8), e29691. https://doi.org/10.1016/j.heliyon.2024.e29691
Madlock-Brown, C. R. (2014). A framework for emerging topic detection in biomedicine . The University of Iowa.
Mane, K. K., & Börner, K. (2004). Mapping topics and topic bursts in PNAS. Proceedings of the National Academy of Sciences, 101 (Suppl_1), 5287–5290.
Mann, H. B. (1945). Nonparametric tests against trend. Econometrica, 13(3), 245. https://doi.org/10.2307/1907187
Marrone, M. (2020). Application of entity linking to identify research fronts and trends. Scientometrics, 122 (1), 357–379. https://doi.org/10.1007/s11192-019-03274-x
Marrone, M., Lemke, S., & Kolbe, L. M. (2022). Entity linking systems for literature reviews. Scientometrics . https://doi.org/10.1007/s11192-022-04423-5
Mell, P., & Grance, T. (2010). The NIST Definition of Cloud Computing. Communications of the ACM, 53 (6), 50.
Mosleh, M., Roshani, S., & Coccia, M. (2022). Scientific laws of research funding to support citations and diffusion of knowledge in life science. Scientometrics, 127 (4), 1931–1951. https://doi.org/10.1007/s11192-022-04300-1 .
Nallola, S. R., & Ayyasamy, V. (2023). Insights on cloud computing: A bibliometric analysis [Preprint]. In Review. https://doi.org/10.21203/rs.3.rs-3012428/v1
Nederhof, A., & Van Wijk, E. (1997). Mapping the social and behavioral sciences world-wide: Use of maps in portfolio analysis of national research efforts. Scientometrics, 40 (2), 237–276.
NIST. (2022). Final version of NIST cloud computing. Updated January 8, 2018. Retrieved February 2022, from https://www.nist.gov/news-events/news/2011/10/final-version-nist-cloud-computing-definition-published .
Padilla, R. S., Milton, S. K., & Johnson, L. W. (2015). Components of service value in business-to-business cloud computing. J Cloud Comp, 4 , 15. https://doi.org/10.1186/s13677-015-0040-x
Papazoglou M. P., & Vaquero L. M. (2012). Knowledge-intensive cloud services: Transforming the cloud delivery stack, knowledge service engineering handbook (pp. 449–494). Taylor & Francis Group.
Roshani, S., Coccia, M., Mosleh, M. (2022). Sensor technology for opening new pathways in diagnosis and therapeutics of breast lung colorectal and prostate cancer. HighTech and Innovation Journal, 3 (3), 356–375. https://doi.org/10.28991/HIJ-2022-03-03-010
Saheb, T., Dehghani, M., & Saheb, T. (2022). Artificial intelligence for sustainable energy: A contextual topic modeling and content analysis. Sustainable Computing: Informatics and Systems, 35 , 100699.
Sci2 Team. (2009). Science of Science (Sci2) Tool. Indiana University and SciTech Strategies. Retrieved November 24, 2016, from https://Sci2.cns.iu.edu .
Sharma, D., Kumar, B., & Chand, S. (2019). A trend analysis of machine learning research with topic models and Mann–Kendall test. International Journal of Intelligent Systems and Applications., 11 (2), 70–82. https://doi.org/10.5815/ijisa.2019.02.08
Singh, V. K., Singh, P., Karmakar, M., Leta, J., & Mayr, P. (2021). The journal coverage of web of science, Scopus and dimensions: A comparative analysis. Scientometrics, 126 , 5113–5142.
Sun, X., Kaur, J., Milojevic’, S., Flammini, A., & Menczer, F. (2013). Social dynamics of science. Scientific Reports, 3 (1069), 1–6. https://doi.org/10.1038/srep01069
Wagiu, EB., Liu, C. -M., Palopak, Y. (2024). Mapping technological trajectories of edge computing: A citation graph analysis. IEEE Internet of Things Journal, 11 (9), 16545–16560. https://doi.org/10.1109/JIOT.2024.3355056
Wang, Y., Agichtein, E., & Benzi, M. (2012). TM-LDA: Efficient online modeling of latent topic transitions in social media. In Proceedings of the 18th ACM SIGKDD international conference on knowledge discovery and data mining (pp. 123–131). https://doi.org/10.1145/2339530.2339552
Wang, J., & Hsu, C. C. (2021). A topic-based patent analytics approach for exploring technological trends in smart manufacturing. Journal of Manufacturing Technology Management, 32 (1), 110–135.
Wang, N., Liang, H., Jia, Y., Ge, S., Xue, Y., & Wang, Z. (2016). Cloud computing research in the IS discipline: A citation/co-citation analysis. Decision Support Systems, 86 , 35–47.
Web of Science (WOS). (2021). Documents. Retrieved November 20, 2021, from https://www.webofscience.com/wos/woscc/basic-search
Xu, S., Hao, L., Yang, G., Lu, K., & An, X. (2021). A topic models based framework for detecting and forecasting emerging technologies. Technological Forecasting and Social Change, 162 , 120366.
Yang, H., & Tate, M. 2012. A descriptive literature review and classification of cloud computing research. Communications of the Association for Information Systems . https://doi.org/10.17705/1CAIS.03102
Zhang, S., & Lu, X. X. (2009). Hydrological responses to precipitation variation and diverse human activities in a mountainous tributary of the lower Xijiang, China. CATENA, 77 (2), 130–142.
Zhao, W., Chen, J. J., Perkins, R., et al. (2015). A heuristic approach to determine an appropriate number of topics in topic modeling. BMC Bioinformatics, 16 (Suppl 13), S8. https://doi.org/10.1186/1471-2105-16-S13-S8
Download references
Acknowledgements
We thank two anonymous referees for helpful comments to improve this study and Dr. Mauricio Marrone from Macquarie University for his guidance and instruction in the entity linking method implementation. The numerical calculations were carried out on Yggdrasil at the computing cluster of the University of Geneva. We also acknowledge that portions of this manuscript have been shared on pre-print servers.
This research received no external funding.
Author information
Authors and affiliations.
CNR, National Research Council of Italy, IRCRES-CNR, Turin Research Area of CNR, Strada delle Cacce, 73, 10135, Torino, Italy
Mario Coccia
Department of Management, Science and Technology, Amirkabir University of Technology, Tehran, Iran
Saeed Roshani
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Saeed Roshani .
Ethics declarations
Conflict of interest.
The authors declare no conflict of interest.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Coccia, M., Roshani, S. Evolution of topics and trends in emerging research fields: multiple analyses with entity linking, Mann–Kendall test and burst methods in cloud computing. Scientometrics (2024). https://doi.org/10.1007/s11192-024-05139-4
Download citation
Received : 11 October 2023
Accepted : 19 August 2024
Published : 26 September 2024
DOI : https://doi.org/10.1007/s11192-024-05139-4
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Science evolution
- Technological forecasting
- Entity linking
- Burst analysis
- Mann–Kendall test
- Topic evolution
- Trend analysis
- Emerging technology
- Science dynamics
- Scientific development
- Cloud computing
- Cloud technology
- Find a journal
- Publish with us
- Track your research
- DOI: 10.1117/12.2684197
- Corpus ID: 259177311
Research and application of smart home-based care system based on Internet of Things technology
- Bingzhan Liu , Liangliang Wang
- Published in Other Conferences 14 June 2023
- Engineering, Computer Science, Medicine
14 References
Related papers.
Showing 1 through 3 of 0 Related Papers

IMAGES
VIDEO
COMMENTS
Since the term first coined in 1999 by Kevin Ashton, the Internet of Things (IoT) has gained significant momentum as a technology to connect physical objects to the Internet and to facilitate machine-to-human and machine-to-machine communications. Over the past two decades, IoT has been an active area of research and development endeavors by many technical and commercial communities. Yet, IoT ...
The 10 Research Topics in the Internet of Things Wei Emma Zhang1, Quan Z. Sheng 2, Adnan Mahmood , Dai Hoang Tran 2, Munazza Zaib , Salma Abdalla Hamad 2, Abdulwahab Aljubairy , Ahoud Abdulrahmn F. Alhazmi , Subhash Sagar2, and Congbo Ma1 1School of Computer Science, The University of Adelaide, SA 5005, Australia Email: [email protected] 2Department of Computing, Macquarie University ...
Zhang, WE, Sheng, QZ, Mahmood, A, Tran, DH, Zaib, M, Hamad, SA, Aljubairy, A, Alhazmi, AAF, Sagar, S & Ma, C 2020, The 10 research topics in the Internet of Things. in Proceedings - 2020 IEEE 6th International Conference on Collaboration and Internet Computing, CIC 2020. Proceedings - 2020 IEEE 6th International Conference on Collaboration and Internet Computing, CIC 2020, Institute of ...
The 10 Research Topics in the Internet of Things. Since the term first coined in 1999 by Kevin Ashton, the Internet of Things (IoT) has gained significant momentum as a technology to connect physical objects to the Internet and to facilitate machine-to-human and machine-to-machine communications. Over the past two decades, IoT has been an ...
10 key research topics of the Internet of Things are identified and the research problems and opportunities within these topics are discussed. Since the term first coined in 1999 by Kevin Ashton, the Internet of Things (IoT) has gained significant momentum as a technology to connect physical objects to the Internet and to facilitate machine-to-human and machine-to-machine communications.
Request PDF | The 10 Research Topics in the Internet of Things | Since the term first coined in 1999 by Kevin Ashton, the Internet of Things (IoT) has gained significant momentum as a technology ...
Over the past two decades, IoT has been an active area of research and development endeavours by many technical and commercial communities. Yet, IoT technology is still not mature and many issues need to be addressed. In this paper, we identify 10 key research topics and discuss the research problems and opportunities within these topics.
In this paper, we identify 10 key research topics and discuss the research problems and opportunities within these topics. Since the term first coined in 1999 by Kevin Ashton, the Internet of Things (IoT) has gained significant momentum as a technology to connect physical objects to the Internet and to facilitate machine-to-human and machine-to ...
Top IoT Research Projects. Come let's discuss the top 10 IoT-based research topics and ideas in detail for 2024. 1. Smart Homes. The idea of a smart home is gaining popularity, and with IoT technology, it has become possible to control and automate various devices in a house. Some of the popular smart home projects include smart lighting ...
Artificial Intelligence of Things (AIoT), Explainable Machine Learning for IoT, Intelligent Edge. Research on the unique IoT challenges in security, reliability and privacy. High-level policy languages for specifying permissible communication patterns. Device software development, such as minimal operating systems. IoT in Cloud-to-thing-Continuum.
The 10 Research Topics in the Internet of Things. Wei Emma Zhang1, Quan Z. Sheng2, Adnan Mahmood2, Dai Hoang Tran2, Munazza Zaib2, Salma Abdalla Hamad2, Abdulwahab Aljubairy2, Ahoud Abdulrahmn F. Alhazmi2, Subhash Sagar2, and Congbo Ma1 1School of Computer Science, The University of Adelaide, SA 5005, Australia Email: [email protected] 2Department of Computing, Macquarie University, NSW 2109 ...
Socio-technical Cybersecurity and Resilience in the Internet of Things. Oktay Cetinkaya. Shan Jiang. Peter Novitzky. 17,995 views. 8 articles. An innovative journal which captures state-of-the-art research in architectures, technologies, and applications of the Internet of Things, opening the door to new interactions between things and hu...
paper, we identify 10 key research topics and discuss the research. problems and opportunities within these topics. Index T erms —Internet of Things, Energy Harvesting, Rec-. ommendation, Search ...
The Internet of things (IoT) describes the network of physical objects—"things"—that are embedded with sensors, software, and other technologies for the purpose of connecting and ...
Since the term first coined in 1999 by Kevin Ashton, the Internet of Things (IoT) has gained significant momentum as a technology to connect physical objects to the Internet and to facilitate machine-to-human and machine-to-machine communications. Over the past two decades, IoT has been an active area of research and development endeavors by many technical and commercial communities. Yet, IoT ...
Many technical communities are vigorously pursuing research topics that contribute to the Internet of Things (IoT). Nowadays, as sensing, actuation, communication, and control become even more sophisticated and ubiquitous, there is a significant overlap in these communities, sometimes from slightly different perspectives. More cooperation between communities is encouraged. To provide a basis ...
The Internet of Things (IoT) refers to a network of physical devices, vehicles, appliances, and other physical objects that are embedded with sensors, software, and network connectivity, allowing them to collect and share data. IoT devices—also known as "smart objects"—can range from simple "smart home" devices like smart ...
This number is anticipated to reach 41 billion in 2027, expecting over 152,000 IoT devices to connect to the Internet per minute in 2025. Considering the global IoT market size, there was a 22% increase in the market size of IoT in 2021, hitting $157.9 billion. Smart home devices are the dominant components of IoT.
First, we will explore perspectives on the definition of the Internet of Things (IoT) followed by key constructs and concepts underlying IoT including a general research framework for conceptualising IoT. Then, we will delve into a further level of granularity and present a selection of IoT Reference Architectures before concluding.
two categories, namely, i) General challenges: which. include common challenges between IoT and traditional. network such as communication, heterogeneity, QoS, scalability, virtualization, data ...
Monitoring vast and remote areas like forests using Wireless Sensor Networks (WSNs) presents significant challenges, such as limited energy resources and signal attenuation over long distances due to natural obstacles. Traditional solutions often require extensive infrastructure, which is impractical in such environments. To address these limitations, we introduce the "FloatingBlue ...
As an emerging technology, the Internet of Things (IoT) revolutionized the global network comprising of people, smart devices, intelligent objects, data, and information. The development of IoT is still in its infancy and many related issues need to be solved. IoT is a unified concept of embedding everything. IoT has a great chance to make the world a higher level of accessibility, integrity ...
The principal goal of this study is to analyze the evolution of topics and trends in emerging research fields by a combination of entity linking, Mann-Kendall test, and burst detection techniques. Multiple methods are applied here in the emerging field of cloud computing by focusing on the frequency of critical topics from 2004 to 2021. Statistical analysis reveals that the Internet of ...
A home-based care system based on the Internet of Things technology is built, which provides a reference prototype for the service model and realization path of smart care, and can meet the actual needs of smart home- based care services. As the overwhelming choice of Chinese families, home-based care has the advantages of convenience, economy and high efficiency. However, there are also some ...