Internet Privacy - Essay Examples And Topic Ideas For Free
Internet privacy refers to the right or expectation of privacy in the digital realm, encompassing issues related to the protection of personal data, confidentiality, and anonymity online. Essays on internet privacy could delve into the risks and challenges associated with digital surveillance, data breaches, or online tracking, the impact of laws and regulations on privacy, or the ways in which individuals and organizations can protect privacy online. They might also explore the ethical, social, and political implications of privacy in the digital age, or the tensions between privacy, security, and convenience online. A substantial compilation of free essay instances related to Internet Privacy you can find at PapersOwl Website. You can use our samples for inspiration to write your own essay, research paper, or just to explore a new topic for yourself.

Impact of Technology on Privacy
The 21st Century is characterized by the heavy impact technology has on us as a society while it continues to develop new devices and modernize technology. Millions of individuals around the world are now connected digitally, in other words, people globally rely heavily on smartphones tablets, and/ or computers that store or save a majority of their personal information. Critical and extremely personal data is available and collected in these smart technology such as credit card details, fingerprint layout, and […]
A World Without Internet
On the street is the 21st century. Almost all people on our planet have access to the Internet. And they are actively using it. But they forget that they use it almost around the clock. From watching the weather in the morning to texting on social media in the evening. Instead of writing an essay by hand, a modern student simply downloads it. People on the Internet are already looking for work, pay for housing and communal services, participate in […]
Positive and Negative Effects of Internet
The topic of the pros and cons of the Internet is one of the most controversial topics. People often cannot give a definite answer to it. The topic of the Internet is quite versatile. Let's look at it from the positive side first. The Internet is the greatest invention of mankind, which made life easier and continues to do it for us hundreds of times. Its first plus is, of course, the available information. Now you can find out any […]
We will write an essay sample crafted to your needs.
Security Versus Freedom?
Welcome to the Digital Age. In today’s connected world, we are living much of our live online. As a result, companies everywhere are creating large storehouses of data on all of us. The most obvious information being collected is social media data. Everything we post publicly and some cases privately, is being stored and analysed. But it is not just social media, there is now a digital record of everything we buy, everything we watch, where we go and what […]
Internet Access Restrictions May Vary
Fantastic. In most instances, they are placed on search quarries and are most prominent at education centers. This is simply to keep minds safe from content unsuitable for most ages (Gonchar). Although this is an effective plan with good intentions, it can become more effective by being enforced on younger ages rather than those who have already been exposed to the negative side of the internet. As you enter high school you have nearly done and seen everything there […]
Securing Cyberspace: Crafting Tomorrow’s Internet Privacy Laws
In an era where digital footprints shape our daily lives, the quest to safeguard personal privacy in the vast expanse of the internet has become more critical than ever before. Transitioning from the pixels that construct our online world to the intricate policies governing its boundaries signifies a pivotal juncture in the evolution of digital governance. As we navigate through this landscape of data, the formulation of robust internet privacy legislation emerges as a beacon of protection against the perils […]
Silent Struggle: Assessing Threats to Internet Privacy and Security
In today's digital age, the internet serves as the cornerstone of modern communication, commerce, and entertainment. However, amidst the convenience and connectivity it offers, lurks a pervasive and often invisible battle for privacy and security. From data breaches to surveillance, the threats to our online well-being are manifold and ever-evolving. One of the most concerning threats is the rampant collection and misuse of personal data by corporations and governments alike. Every click, search, and purchase leaves a digital footprint, eagerly […]
Safeguarding Cyberspace: the Vital Role of AI in Preserving Online Privacy
In an era where our digital footprints grow larger with every click, the question of how to protect our online privacy becomes increasingly pertinent. Enter Artificial Intelligence, our modern-day guardians in the complex realm of cyberspace. Far beyond mere machines crunching numbers, AI has evolved into a formidable force in the fight against privacy breaches. The first and foremost duty of AI guardians is to fortify our virtual boundaries. Picture them as vigilant sentinels stationed at the gates of our […]
Preserving Digital Integrity: a Scholarly Evaluation of Internet Privacy
In the contemporary digital epoch, where the internet serves as an omnipotent conduit for global interaction, commerce, and information dissemination, the concept of cyber privacy emerges as a pivotal concern. As an academic critic, entrusted with scrutinizing the intricacies of cyber privacy, it becomes essential to unravel the diverse facets of this intricate matter, ranging from its legal and ethical dimensions to its societal and technological reverberations. Cyber privacy fundamentally entails the right of individuals to govern their personal information […]
Additional Example Essays
- Positive Effects of Social Media
- Instagram and body dysmorphia
- The Negative Effects of Social Media On Mental Health
- The Mental Health Stigma
- How the Roles of Women and Men Were Portrayed in "A Doll's House"
- Psychiatric Nurse Practitioner
- Substance Abuse and Mental Illnesses
- Importance Of Accountability
- Are Electric Cars Better Than Petrol Diesel Cars?
- "A Doll's House" as a Modern Tragedy
- Poems “The Negro Speaks of Rivers” and “Still I Rise”
- The Unique Use of Literary Devices in The Tell-Tale Heart
1. Tell Us Your Requirements
2. Pick your perfect writer
3. Get Your Paper and Pay
Hi! I'm Amy, your personal assistant!
Don't know where to start? Give me your paper requirements and I connect you to an academic expert.
short deadlines
100% Plagiarism-Free
Certified writers
Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
How Americans View Data Privacy
1. views of data privacy risks, personal data and digital privacy laws, table of contents.
- Role of social media, tech companies and government regulation
- Americans’ day-to-day experiences with online privacy
- Personal data and information
- Feelings of concern, confusion and a lack of control over one’s data
- Privacy laws and regulation
- Americans largely favor more regulation to protect personal information
- Trust in social media executives
- Children’s online privacy: Concerns and responsibility
- Law enforcement and surveillance
- AI and data collection
- Trust in companies that use AI
- How people approach privacy policies
- How people are protecting their digital privacy
- How Americans handle their passwords
- Data breaches and hacks
- Identifying the most and least knowledgeable, confident and concerned
- Knowledge and privacy choices
- Confidence and privacy choices
- Concern and privacy choices
- The case of privacy policies
- Acknowledgments
- The American Trends Panel survey methodology
- Appendix A: Law enforcement’s use of technology in investigations
- Appendix B: Privacy outcomes by knowledge, confidence and concern
- Appendix C: Confident and independent use of digital devices, by age and education
Online privacy is complex, encompassing debates over law enforcement’s data access, government regulation and what information companies can collect. This chapter examines Americans’ perspectives on these issues and highlights how views vary across different groups, particularly by education and age.
When managing their privacy online, most Americans say they trust themselves to make the right decisions about their personal information (78%), and a majority are skeptical that anything they do will make a difference (61%).
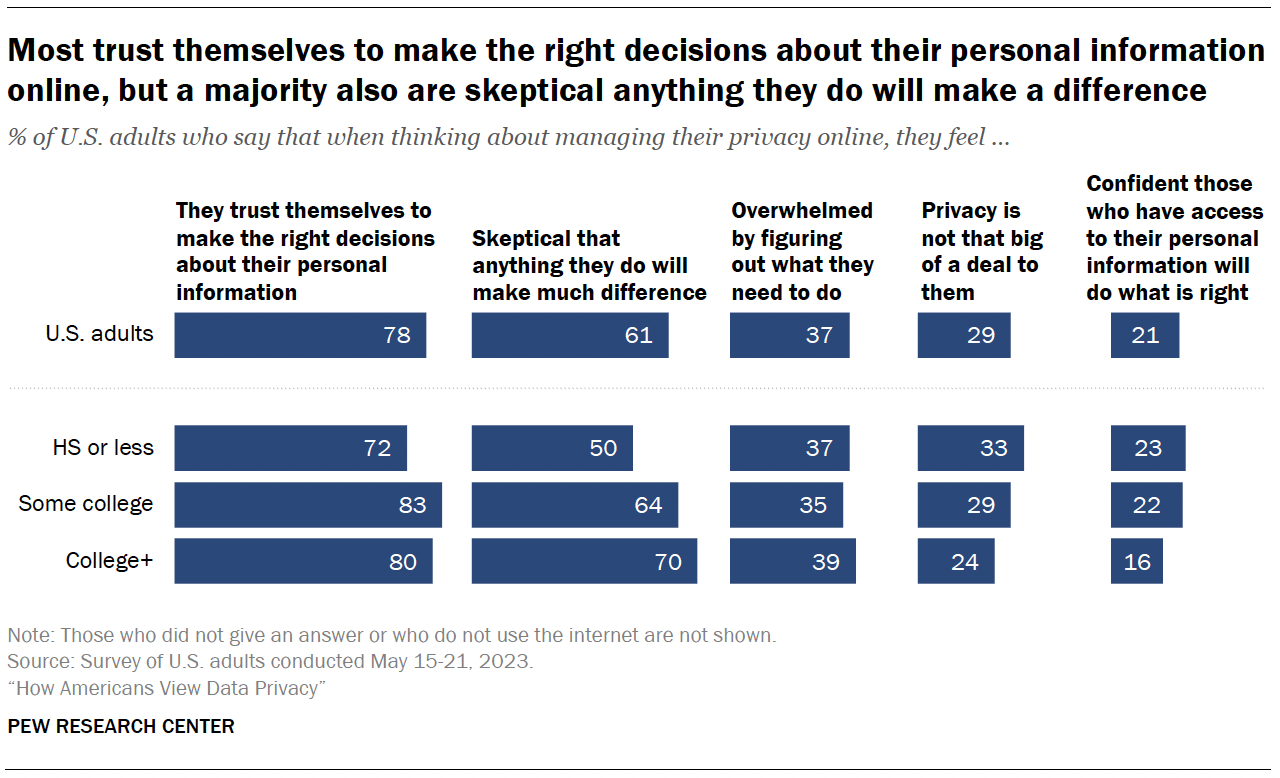
Far fewer mention being overwhelmed by figuring out what they need to do (37%) or say privacy is not that big of a deal to them (29%).
Another 21% are confident that those with access to their personal information will do what is right.
Education differences
- 81% of those with at least some college experience say they trust themselves to make the right decisions about their personal information online, compared with 72% of those with a high school diploma or less.
- 67% of those with at least some college are skeptical that anything they do to manage their online privacy will make a difference, compared with half of those with a high school diploma or less formal education.
On the other hand, those with a high school education or less are more likely than those with some college experience or more to say that privacy isn’t that big of a deal to them and that they are confident that those who have access to their personal information will do the right thing.
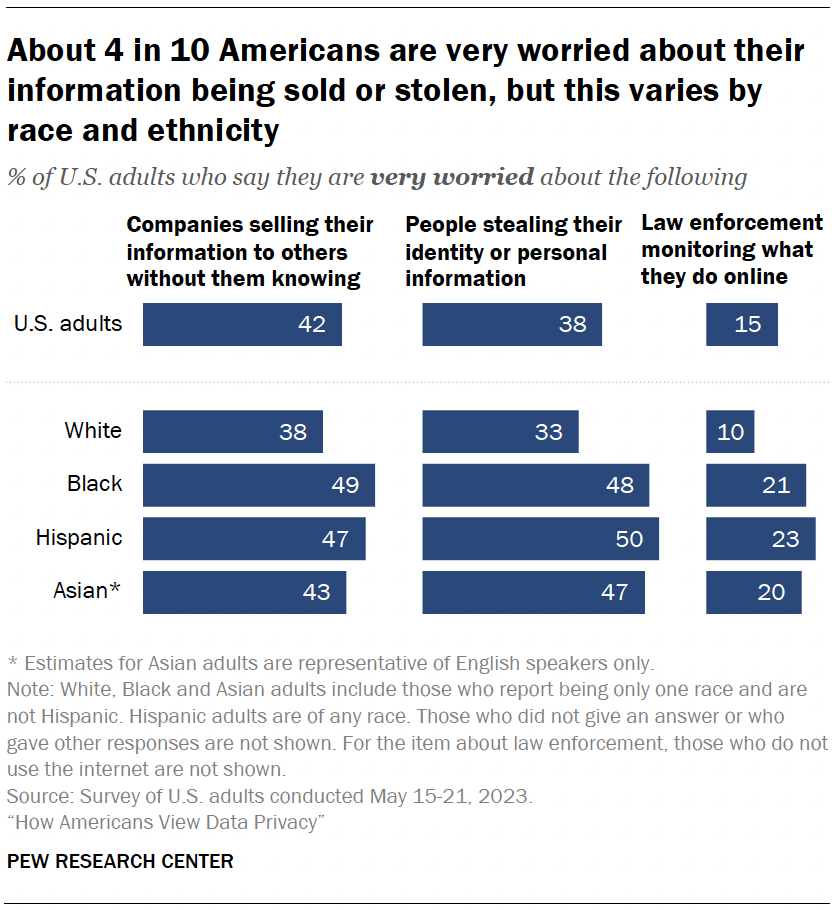
The survey also explores the concerns people have about data collection and security – specifically, how they feel about three scenarios around companies, law enforcement and identity theft.
Roughly four-in-ten Americans say they are very worried about companies selling their information to others without them knowing (42%) or people stealing their identity or personal information (38%). Fewer are apprehensive about law enforcement monitoring what they do online (15%).
Racial and ethnic differences
However, some of these shares are higher among Hispanic, Black or Asian adults: 1
- Roughly half of Hispanic, Black or Asian adults are very worried about people stealing their identity or personal information, compared with a third of White adults.
- About one-in-five of each group are very worried about law enforcement monitoring their online activity; 10% of White adults say this.
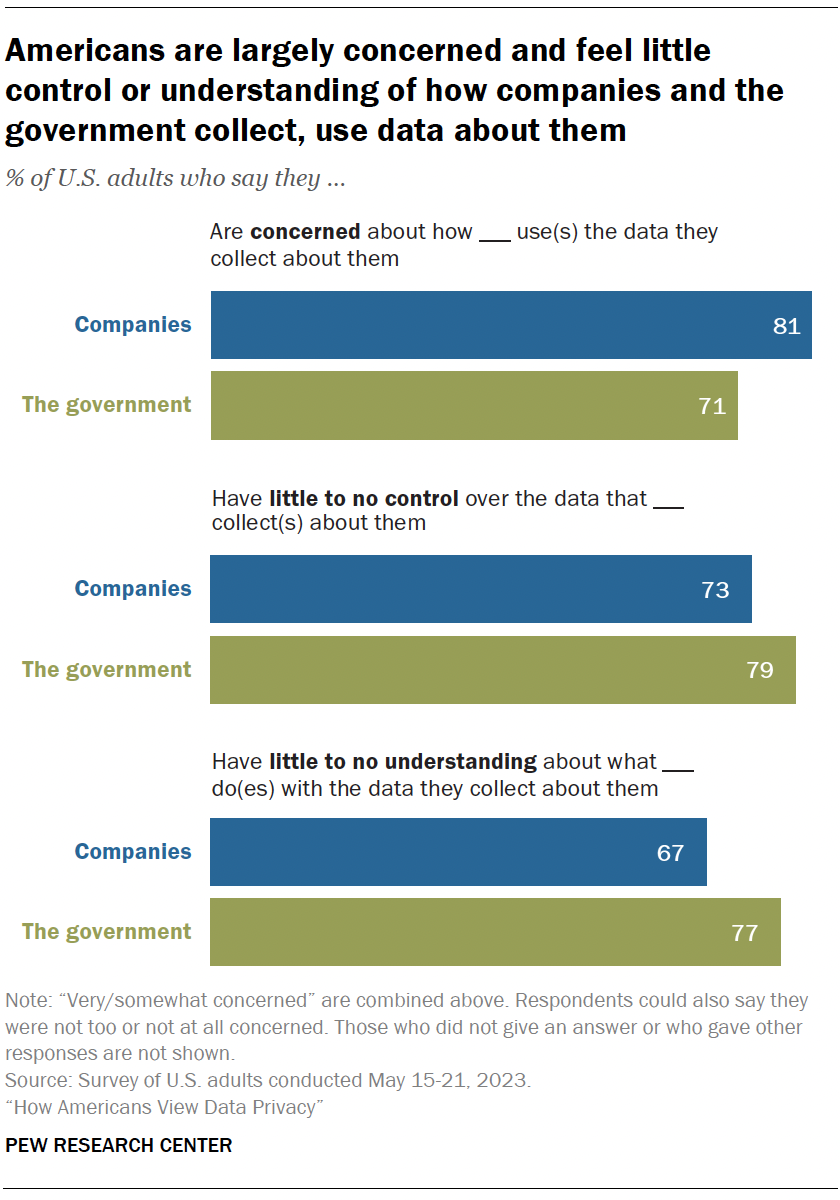
A majority of Americans say they are concerned, lack control and have a limited understanding about how the data collected about them is used. This is true whether it’s the government or companies using their data. Similar sentiments were expressed in 2019, when we last asked about this .
Concern is high: 81% say they feel very or somewhat concerned with how companies use the data they collect about them. Fully 71% say the same regarding the government’s use of data.
People don’t feel in control: Roughly three-quarters or more feel they have very little or no control over the data collected about them by companies (73%) or the government (79%).
Understanding is low: Americans also say they don’t understand what these actors are doing with the data collected about them. Majorities say they have very little or no understanding of this, whether by the government (77%) or companies (67%).
Americans are now less knowledgeable than before about how companies are using their personal data. The share who say they don’t understand this has risen from 59% in 2019 to 67% in 2023.
They have also grown more concerned about how the government uses the data it collects about them, with the share expressing concern up from 64% to 71% over this same period.
While these sentiments have not changed significantly since 2019 among Democrats and those who lean toward the Democratic Party, Republicans and GOP leaners have grown more wary of government data collection. Today, 77% of Republicans say they are concerned about how the government uses data it collects about them, up from 63% four years earlier.
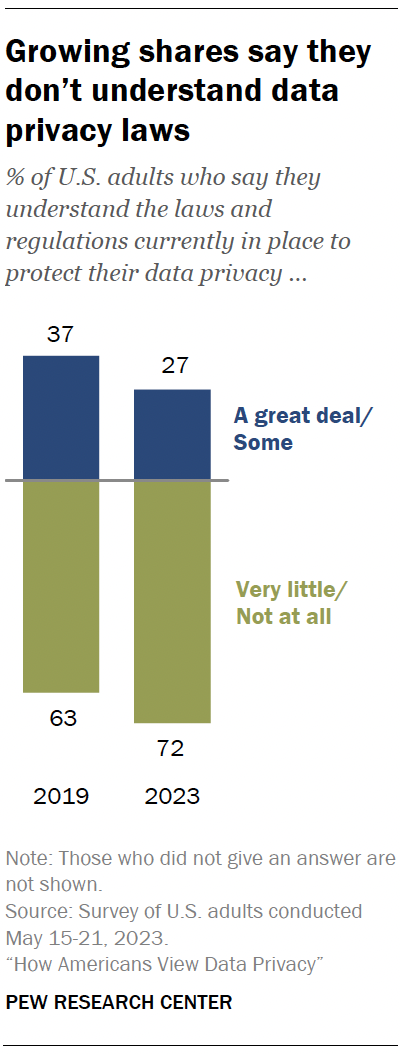
Americans are less knowledgeable about data privacy laws today than in the past.
Today, 72% of Americans say they have little to no understanding about the laws and regulations that are currently in place to protect their data privacy. This is up from 63% in 2019.
By comparison, the shares who say they understand some or a great deal about these laws decreased from 37% in 2019 to 27% in 2023.
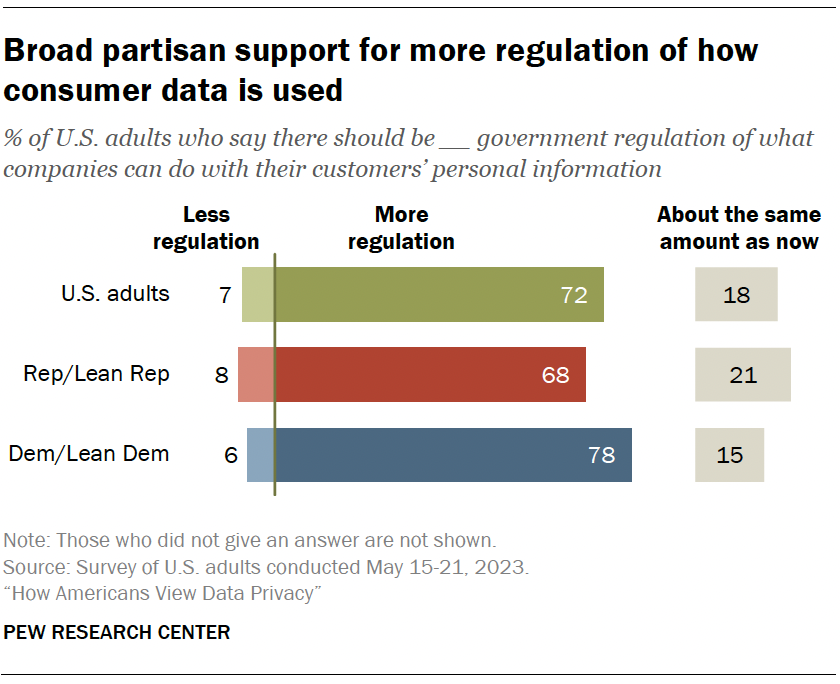
Overall, 72% say there should be more government regulation of what companies can do with their customers’ personal information. Just 7% say there should be less regulation. Another 18% say it should stay about the same.
Views by political affiliation
There is broad partisan support for greater involvement by the government in regulating consumer data.
A majority of Democrats and Republicans say there should be more government regulation for how companies treat users’ personal information (78% vs. 68%).
These findings are largely on par with a 2019 Center survey that showed strong support for increased regulations across parties.
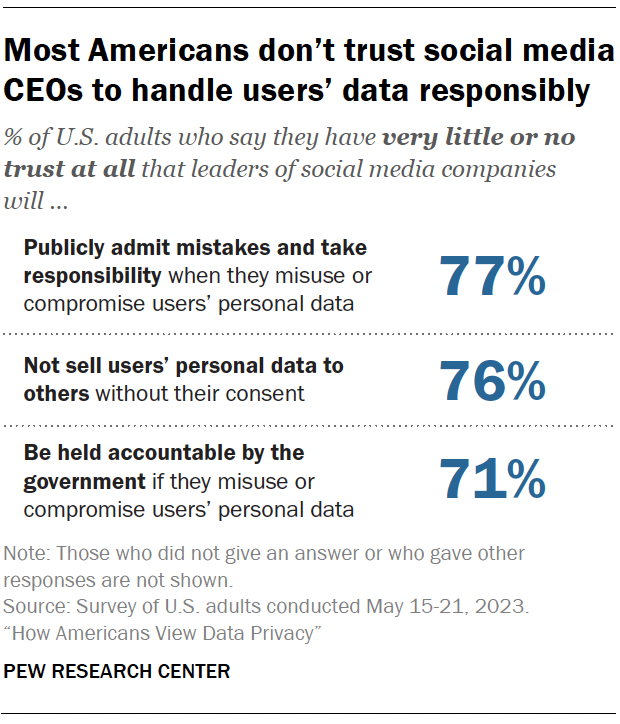
Majorities of Americans say they have little to no trust that leaders of social media companies will publicly admit mistakes regarding consumer data being misused or compromised (77%), that these leaders will not sell users’ personal data to others without their consent (76%), and that leaders would be held accountable by the government if they were to misuse or compromise users’ personal data (71%).
This includes notable shares who have no trust at all in those who are running social media sites. For example, 46% say they have no trust at all in executives of social media companies to not sell users’ data without their consent.
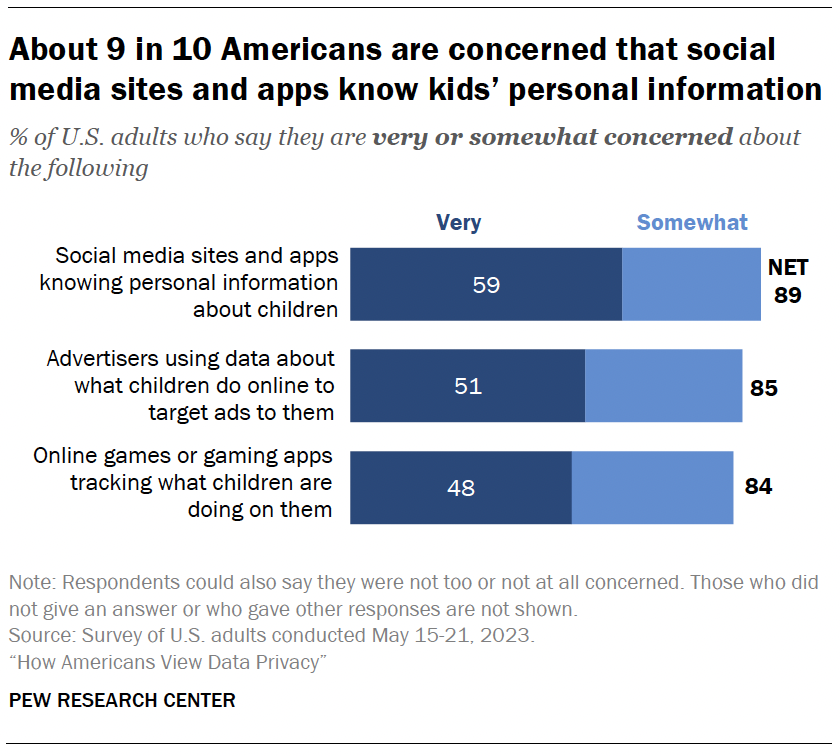
Most Americans say they are concerned about social media sites knowing personal information about children (89%), advertisers using data about what children do online to target ads to them (85%) and online games tracking what children are doing on them (84%).
Concern is widespread, with no statistically significant differences between those with and without children.
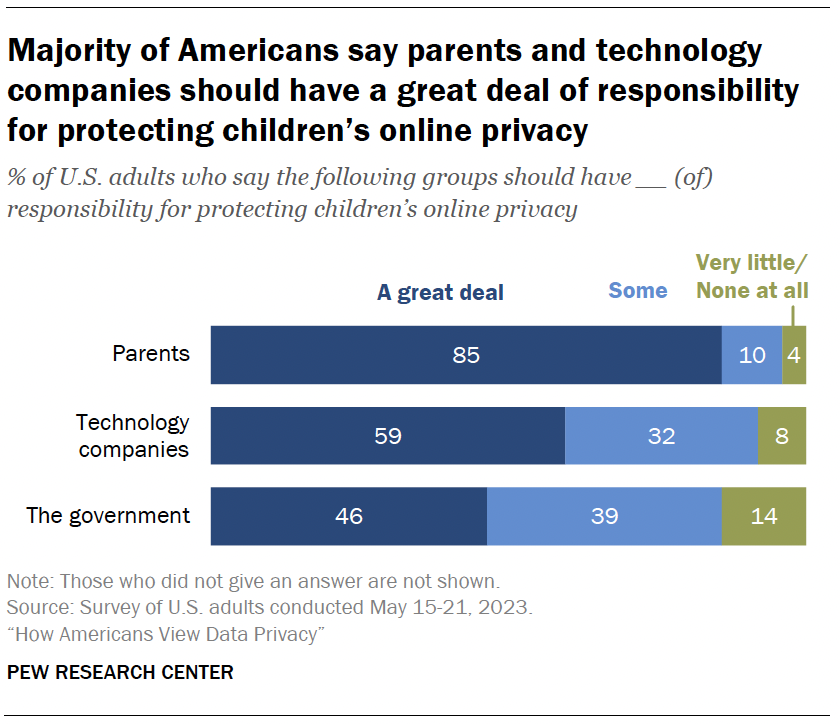
Another key question is who should be responsible for the actual protection of kids’ online privacy.
Fully 85% say parents bear a great deal of responsibility for protecting children’s online privacy. Roughly six-in-ten say the same about technology companies, and an even smaller share believe the government should have a great deal of responsibility.
The survey also measured how acceptable Americans think it is for law enforcement to use surveillance tools during criminal investigations.
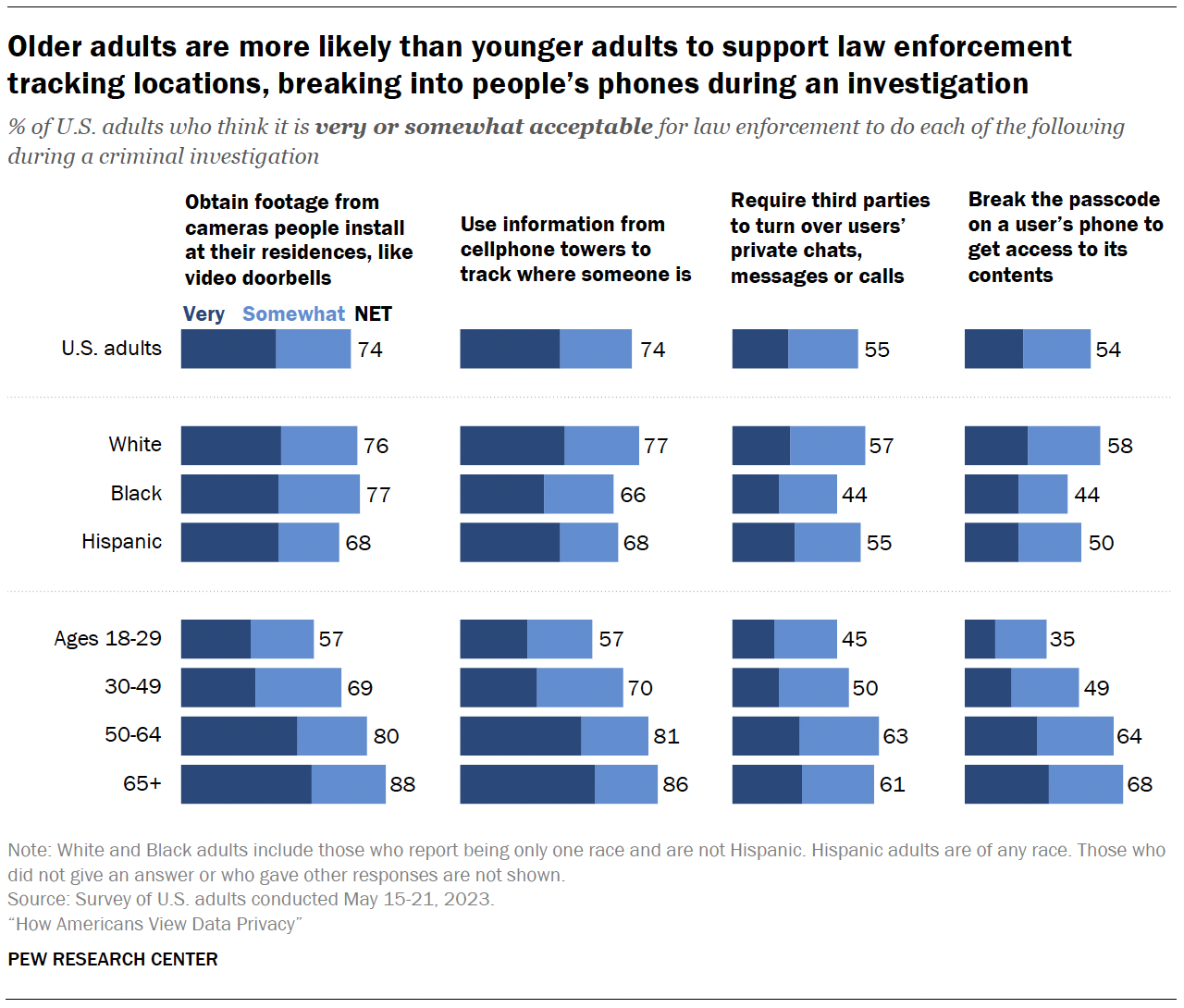
Roughly three-quarters of Americans say it’s very or somewhat acceptable for law enforcement to obtain footage from cameras people install at their residences during a criminal investigation or use information from cellphone towers to track where someone is.
By comparison, smaller shares – though still a slight majority – say it is acceptable to break the passcode on a user’s phone (54%) or require third parties to turn over users’ private chats, messages or calls (55%) during a criminal investigation. 2
About one-in-ten Americans say they aren’t sure how they feel about law enforcement doing each of these things.
Age differences
Older adults are much more likely than younger adults to say it’s at least somewhat acceptable for law enforcement to take each of these actions in criminal investigations.
For example, 88% of those 65 and older say it’s acceptable for law enforcement to obtain footage from cameras people install at their residences, compared with 57% of those ages 18 to 29.
In the case of a criminal investigation:
- White adults are more likely than Hispanic and Black adults to think it’s acceptable for law enforcement to use information from cellphone towers to track people’s locations and to break the passcode on a user’s phone to get access to its contents.
- White and Hispanic adults are more likely than Black adults to say it’s acceptable to require third parties to turn over users’ private chats, messages or calls.
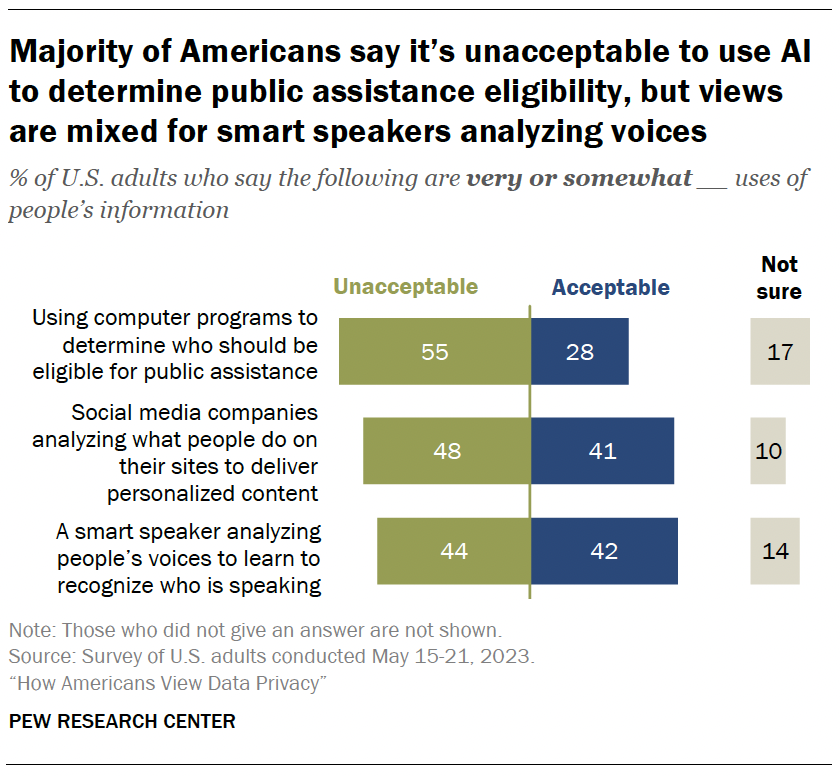
Artificial intelligence (AI) can be used to collect and analyze people’s personal information. Some Americans are wary of companies using AI in this way.
Fully 55% of adults say using computer programs to determine who should be eligible for public assistance is unacceptable. Roughly a quarter say it’s an acceptable use of AI.
Roughly half (48%) think it is unacceptable for social media companies to analyze what people do on their sites to deliver personalized content. Still, 41% are supportive of this.
Views are mixed when it comes to smart speakers analyzing people’s voices to learn who is speaking. Statistically equal shares say it’s unacceptable and acceptable (44% and 42%, respectively).
And some Americans – ranging from 10% to 17% – are uncertain about whether these uses are acceptable or not.
- 49% of adults 50 and older say it’s unacceptable for a smart speaker to analyze people’s voices to learn to recognize who’s speaking. This share drops to four-in-ten among adults under 50.
- Similarly, 56% of those 50 and older say social media companies analyzing what people do on their sites to deliver personalized content is unacceptable. But 41% of those under 50 say the same.
- There are no differences between those under 50 and those 50 and older over whether computer programs should be used to determine eligibility for public assistance.
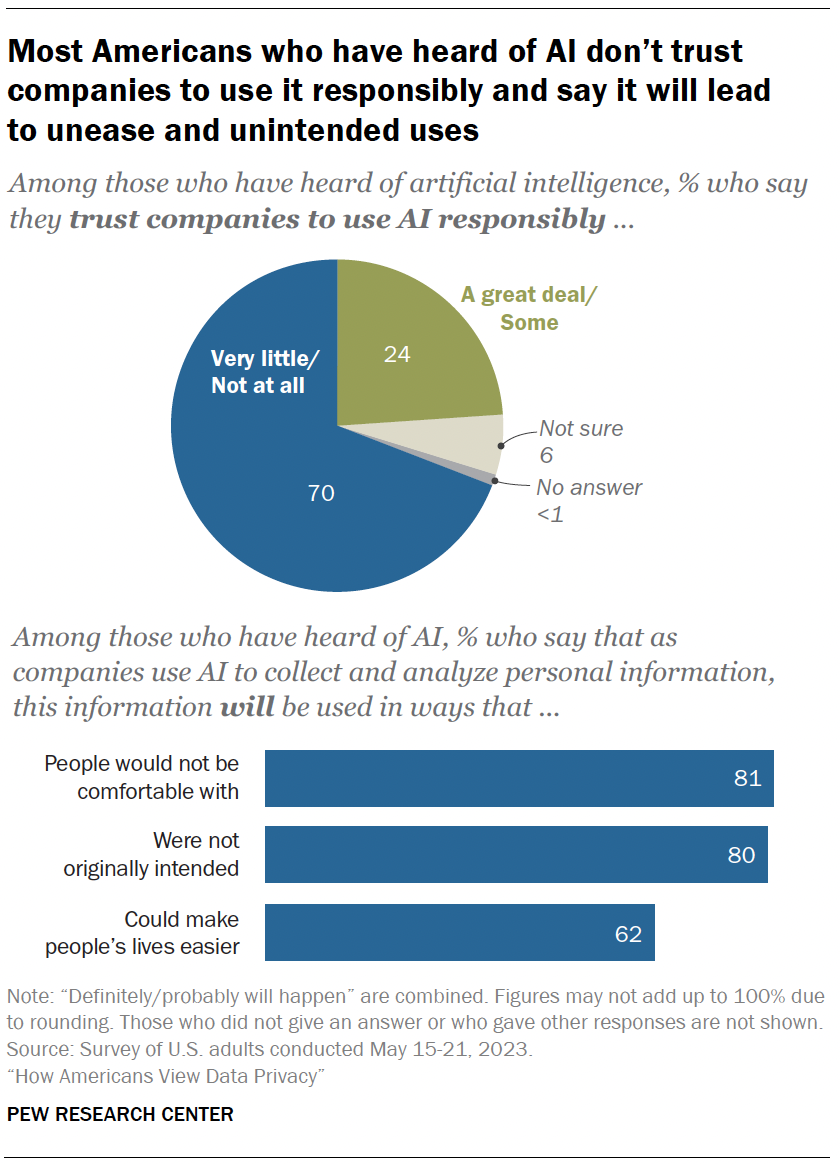
In addition to understanding people’s comfort level with certain uses of AI, the survey also measured the public’s attitudes toward companies that are utilizing AI in their products.
Among those who have heard of AI:
- 70% say they have little to no trust in companies to make responsible decisions about how they use AI in their products.
- Roughly eight-in-ten say the information will be used in ways people are not comfortable with or that were not originally intended.
- Views are more mixed regarding the potential that using AI to analyze personal details could make life easier. A majority of those who have heard of AI say this will happen (62%). Regarding differences by age, adults under 50 are more optimistic than those 50 and older (70% vs. 54%).
- 87% of those with a college degree or higher say companies will use AI to analyze personal details in ways people would not be comfortable with. Some 82% of those with some college experience and 74% with a high school diploma or less say the same.
- 88% of those with a bachelor’s degree or more say companies will use this information in ways that were not originally intended. This share drops to 80% among those with some college experience and 71% among those with a high school diploma or less.
- About three-quarters of those with a college degree or more (74%) say this information will be used in ways that could make people’s lives easier. But this share drops to 60% among those with some college experience and 52% among those with a high school diploma or less.
- This survey includes a total sample size of 364 Asian adults. The sample primarily includes English-speaking Asian adults and, therefore, it may not be representative of the overall Asian adult population. Despite this limitation, it is important to report the views of Asian adults on the topics in this study. As always, Asian adults’ responses are incorporated into the general population figures throughout this report. Asian adults are shown as a separate group when the question was asked of the full sample. Because of the relatively small sample size and a reduction in precision due to weighting, results are not shown separately for Asian adults for questions that were only asked of a random half of respondents (Form 1/Form 2). ↩
- Half of respondents were asked the questions above, and the other half received the same questions with the added context of it being a “criminal investigation where public safety is at risk.” Differences in response were largely modest. See Appendix A for these findings. ↩
Sign up for our weekly newsletter
Fresh data delivery Saturday mornings
Sign up for The Briefing
Weekly updates on the world of news & information
- Artificial Intelligence
- Online Privacy & Security
- Social Media
- Tech Companies
Social Media Fact Sheet
Teens and social media fact sheet, more americans are getting news on tiktok, bucking the trend seen on most other social media sites, life on social media platforms, in users’ own words, charting congress on social media in the 2016 and 2020 elections, most popular.
1615 L St. NW, Suite 800 Washington, DC 20036 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
Copyright 2024 Pew Research Center

Photo by Raghu Rai/Magnum
Privacy is power
Don’t just give away your privacy to the likes of google and facebook – protect it, or you disempower us all.
by Carissa Véliz + BIO
Imagine having a master key for your life. A key or password that gives access to the front door to your home, your bedroom, your diary, your computer, your phone, your car, your safe deposit, your health records. Would you go around making copies of that key and giving them out to strangers? Probably not the wisest idea – it would be only a matter of time before someone abused it, right? So why are you willing to give up your personal data to pretty much anyone who asks for it?
Privacy is the key that unlocks the aspects of yourself that are most intimate and personal, that make you most you, and most vulnerable. Your naked body. Your sexual history and fantasies. Your past, present and possible future diseases. Your fears, your losses, your failures. The worst thing you have ever done, said, and thought. Your inadequacies, your mistakes, your traumas. The moment in which you have felt most ashamed. That family relation you wish you didn’t have. Your most drunken night.
When you give that key, your privacy, to someone who loves you, it will allow you to enjoy closeness, and they will use it to benefit you. Part of what it means to be close to someone is sharing what makes you vulnerable, giving them the power to hurt you, and trusting that person never to take advantage of the privileged position granted by intimacy. People who love you might use your date of birth to organise a surprise birthday party for you; they’ll make a note of your tastes to find you the perfect gift; they’ll take into account your darkest fears to keep you safe from the things that scare you. Not everyone will use access to your personal life in your interest, however. Fraudsters might use your date of birth to impersonate you while they commit a crime; companies might use your tastes to lure you into a bad deal; enemies might use your darkest fears to threaten and extort you. People who don’t have your best interest at heart will exploit your data to further their own agenda. Privacy matters because the lack of it gives others power over you.
You might think you have nothing to hide, nothing to fear. You are wrong – unless you are an exhibitionist with masochistic desires of suffering identity theft, discrimination, joblessness, public humiliation and totalitarianism, among other misfortunes. You have plenty to hide, plenty to fear, and the fact that you don’t go around publishing your passwords or giving copies of your home keys to strangers attests to that.
You might think your privacy is safe because you are a nobody – nothing special, interesting or important to see here. Don’t shortchange yourself. If you weren’t that important, businesses and governments wouldn’t be going to so much trouble to spy on you.
You have your attention, your presence of mind – everyone is fighting for it. They want to know more about you so they can know how best to distract you, even if that means luring you away from quality time with your loved ones or basic human needs such as sleep. You have money, even if it is not a lot – companies want you to spend your money on them. Hackers are eager to get hold of sensitive information or images so they can blackmail you. Insurance companies want your money too, as long as you are not too much of a risk, and they need your data to assess that. You can probably work; businesses want to know everything about whom they are hiring – including whether you might be someone who will want to fight for your rights. You have a body – public and private institutions would love to know more about it, perhaps experiment with it, and learn more about other bodies like yours. You have an identity – criminals can use it to commit crimes in your name and let you pay for the bill. You have personal connections. You are a node in a network. You are someone’s offspring, someone’s neighbour, someone’s teacher or lawyer or barber. Through you, they can get to other people. That’s why apps ask you for access to your contacts. You have a voice – all sorts of agents would like to use you as their mouthpiece on social media and beyond. You have a vote – foreign and national forces want you to vote for the candidate that will defend their interests.
As you can see, you are a very important person. You are a source of power.
By now, most people are aware that their data is worth money. But your data is not valuable only because it can be sold. Facebook does not technically sell your data, for instance. Nor does Google. They sell the power to influence you. They sell the power to show you ads, and the power to predict your behaviour. Google and Facebook are not really in the business of data – they are in the business of power. Even more than monetary gain, personal data bestows power on those who collect and analyse it, and that is what makes it so coveted.
T here are two aspects to power. The first aspect is what the German philosopher Rainer Forst in 2014 defined as ‘the capacity of A to motivate B to think or do something that B would otherwise not have thought or done’. The means through which the powerful enact their influence are varied. They include motivational speeches, recommendations, ideological descriptions of the world, seduction and credible threats. Forst argues that brute force or violence is not an exercise of power, for subjected people don’t ‘do’ anything; rather, something is done to them. But clearly brute force is an instance of power. It is counterintuitive to think of someone as powerless who is subjecting us through violence. Think of an army dominating a population, or a thug strangling you. In Economy and Society (1978), the German political economist Max Weber describes this second aspect of power as the ability for people and institutions to ‘carry out [their] own will despite resistance’.
In short, then, powerful people and institutions make us act and think in ways in which we would not act and think were it not for their influence. If they fail to influence us into acting and thinking in the way that they want us to, powerful people and institutions can exercise force upon us – they can do unto us what we will not do ourselves.
There are different types of power: economic, political and so on. But power can be thought of as being like energy: it can take many different forms, and these can change. A wealthy company can often use its money to influence politics through lobbying, for instance, or to shape public opinion through paying for ads.
Power over others’ privacy is the quintessential kind of power in the digital age
That tech giants such as Facebook and Google are powerful is hardly news. But exploring the relationship between privacy and power can help us to better understand how institutions amass, wield and transform power in the digital age, which in turn can give us tools and ideas to resist the kind of domination that survives on violations of the right to privacy. However, to grasp how institutions accumulate and exercise power in the digital age, first we have to look at the relationship between power, knowledge and privacy.
There is a tight connection between knowledge and power. At the very least, knowledge is an instrument of power. The French philosopher Michel Foucault goes even further, and argues that knowledge in itself is a form of power . There is power in knowing. By protecting our privacy, we prevent others from being empowered with knowledge about us that can be used against our interests.
The more that someone knows about us, the more they can anticipate our every move, as well as influence us. One of the most important contributions of Foucault to our understanding of power is the insight that power does not only act upon human beings – it constructs human subjects (even so, we can still resist power and construct ourselves). Power generates certain mentalities, it transforms sensitivities, it brings about ways of being in the world. In that vein, the British political theorist Steven Lukes argues in his book Power (1974) that power can bring about a system that produces wants in people that work against their own interests. People’s desires can themselves be a result of power, and the more invisible the means of power, the more powerful they are. Examples of power shaping preferences today include when tech uses research about how dopamine works to make you addicted to an app, or when you are shown political ads based on personal information that makes a business think you are a particular kind of person (a ‘persuadable’, as the data-research company Cambridge Analytica put it, or someone who might be nudged into not voting, for instance).
The power that comes about as a result of knowing personal details about someone is a very particular kind of power. Like economic power and political power, privacy power is a distinct type of power, but it also allows those who hold it the possibility of transforming it into economic, political and other kinds of power. Power over others’ privacy is the quintessential kind of power in the digital age.
T wo years after it was funded and despite its popularity, Google still hadn’t developed a sustainable business model. In that sense, it was just another unprofitable internet startup. Then, in 2000, Google launched AdWords, thereby starting the data economy. Now called Google Ads, it exploited the data produced by Google’s interactions with its users to sell ads. In less than four years, the company achieved a 3,590 per cent increase in revenue.
That same year, the Federal Trade Commission had recommended to US Congress that online privacy be regulated. However, after the attacks of 11 September 2001 on the Twin Towers in New York, concern about security took precedence over privacy, and plans for regulation were dropped. The digital economy was able to take off and reach the magnitude it enjoys today because governments had an interest in having access to people’s data in order to control them. From the outset, digital surveillance has been sustained through a joint effort between private and public institutions.
The mass collection and analysis of personal data has empowered governments and prying companies. Governments now know more about their citizens than ever before. The Stasi (the security service of the German Democratic Republic), for instance, managed to have files only on about a third of the population, even if it aspired to have complete information on all citizens. Intelligence agencies today hold much more information on all of the population. To take just one important example, a significant proportion of people volunteer private information in social networks. As the US filmmaker Laura Poitras put it in an interview with The Washington Post in 2014: ‘Facebook is a gift to intelligence agencies.’ Among other possibilities, that kind of information gives governments the ability to anticipate protests, and even pre-emptively arrest people who plan to take part. Having the power to know about organised resistance before it happens, and being able to squash it in time, is a tyrant’s dream.
Tech companies’ power is constituted, on the one hand, by having exclusive control of data and, on the other, by the ability to anticipate our every move, which in turn gives them opportunities to influence our behaviour, and sell that influence to others. Companies that earn most of their revenues through advertising have used our data as a moat – a competitive advantage that has made it impossible for alternative businesses to challenge tech titans. Google’s search engine, for example, is as good as it is partly because its algorithm has much more data to learn from than any of its competitors. In addition to keeping the company safe from competitors and allowing it to train its algorithm better, our data also allows tech companies to predict and influence our behaviour. With the amount of data it has access to, Google can know what keeps you up at night, what you desire the most, what you are planning to do next. It then whispers this information to other busybodies who want to target you for ads.
Tech wants you to think that the innovations it brings into the market are inevitable
Companies might also share your data with ‘data brokers’ who will create a file on you based on everything they know about you (or, rather, everything they think they know), and then sell it to pretty much whoever is willing to buy it – insurers, governments, prospective employers, even fraudsters.
Data vultures are incredibly savvy at using both the aspects of power discussed above: they make us give up our data, more or less voluntarily, and they also snatch it away from us, even when we try to resist. Loyalty cards are an example of power making us do certain things that we would otherwise not do. When you are offered a discount for loyalty at your local supermarket, what you are being offered is for that company to conduct surveillance on you, and then influence your behaviour through nudges (discounts that will encourage you to buy certain products). An example of power doing things to us that we don’t want it to do is when Google records your location on your Android smartphone, even when you tell it not to.
Both types of power can also be seen at work at a more general level in the digital age. Tech constantly seduces us into doing things we would not otherwise do, from getting lost down a rabbit hole of videos on YouTube, to playing mindless games, or checking our phone hundreds of times a day. The digital age has brought about new ways of being in the world that don’t always make our lives better. Less visibly, the data economy has also succeeded in normalising certain ways of thinking. Tech companies want you to think that, if you have done nothing wrong, you have no reason to object to their holding your data. They also want you to think that treating your data as a commodity is necessary for digital tech, and that digital tech is progress – even when it might sometimes look worryingly similar to social or political regress. More importantly, tech wants you to think that the innovations it brings into the market are inevitable. That’s what progress looks like, and progress cannot be stopped.
That narrative is complacent and misleading. As the Danish economic geographer Bent Flyvbjerg points out in Rationality and Power (1998), power produces the knowledge, narratives and rationality that are conducive to building the reality it wants. But technology that perpetuates sexist and racist trends and worsens inequality is not progress. Inventions are far from unavoidable. Treating data as a commodity is a way for companies to earn money, and has nothing to do with building good products. Hoarding data is a way of accumulating power. Instead of focusing only on their bottom line, tech companies can and should do better to design the online world in a way that contributes to people’s wellbeing. And we have many reasons to object to institutions collecting and using our data in the way that they do.
Among those reasons is institutions not respecting our autonomy, our right to self-govern. Here is where the harder side of power plays a role. The digital age thus far has been characterised by institutions doing whatever they want with our data, unscrupulously bypassing our consent whenever they think they can get away with it. In the offline world, that kind of behaviour would be called matter-of-factly ‘theft’ or ‘coercion’. That it is not called this in the online world is yet another testament to tech’s power over narratives.
I t’s not all bad news, though. Yes, institutions in the digital age have hoarded privacy power, but we can reclaim the data that sustains it, and we can limit their collecting new data. Foucault argued that, even if power constructs human subjects, we have the possibility to resist power and construct ourselves. The power of big tech looks and feels very solid. But tech’s house of cards is partly built on lies and theft. The data economy can be disrupted. The tech powers that be are nothing without our data. A small piece of regulation, a bit of resistance from citizens, a few businesses starting to offer privacy as a competitive advantage, and it can all evaporate.
No one is more conscious of their vulnerability than tech companies themselves. That is why they are trying to convince us that they do care about privacy after all (despite what their lawyers say in court). That is why they spend millions of dollars on lobbying. If they were so certain about the value of their products for the good of users and society, they would not need to lobby so hard. Tech companies have abused their power, and it is time to resist them.
In the digital age, resistance inspired by the abuse of power has been dubbed a techlash. Abuses of power remind us that power needs to be curtailed for it to be a positive influence in society. Even if you happen to be a tech enthusiast, even if you think that there is nothing wrong with what tech companies and governments are doing with our data, you should still want power to be limited, because you never know who will be in power next. Your new prime minister might be more authoritarian than the old one; the next CEO of the next big tech company might not be as benevolent as those we’ve seen thus far. Tech companies have helped totalitarian regimes in the past, and there is no clear distinction between government and corporate surveillance. Businesses share data with governments, and public institutions share data with companies.
When you expose your privacy, you put us all at risk
Do not give in to the data economy without at least some resistance. Refraining from using tech altogether is unrealistic for most people, but there is much more you can do short of that. Respect other people’s privacy. Don’t expose ordinary citizens online. Don’t film or photograph people without their consent, and certainly don’t share such images online. Try to limit the data you surrender to institutions that don’t have a claim to it. Imagine someone asks for your number in a bar and won’t take a ‘No, thank you’ for an answer. If that person were to continue to harass you for your number, what would you do? Perhaps you would be tempted to give them a fake number. That is the essence of obfuscation, as outlined by the media scholars Finn Bruton and Helen Nissenbaum in the 2015 book of that name. If a clothing company asks for your name to sell you clothes, give them a different name – say, Dr Private Information, so that they get the message. Don’t give these institutions evidence they can use to claim that we are consenting to our data being taken away from us. Make it clear that your consent is not being given freely.
When downloading apps and buying products, choose products that are better for privacy. Use privacy extensions on your browsers. Turn your phone’s wi-fi, Bluetooth and locations services off when you don’t need them. Use the legal tools at your disposal to ask companies for the data they have on you, and ask them to delete that data. Change your settings to protect your privacy. Refrain from using one of those DNA home testing kits – they are not worth it. Forget about ‘smart’ doorbells that violate your privacy and that of others. Write to your representatives sharing your concerns about privacy. Tweet about it. Take opportunities as they come along to inform business, governments and other people that you care about privacy, that what they are doing is not okay.
Don’t make the mistake of thinking you are safe from privacy harms, maybe because you are young, male, white, heterosexual and healthy. You might think that your data can work only for you, and never against you, if you’ve been lucky so far. But you might not be as healthy as you think you are, and you will not be young forever. The democracy you are taking for granted might morph into an authoritarian regime that might not favour the likes of you.
Furthermore, privacy is not only about you. Privacy is both personal and collective. When you expose your privacy, you put us all at risk. Privacy power is necessary for democracy – for people to vote according to their beliefs and without undue pressure, for citizens to protest anonymously without fear of repercussions, for individuals to have freedom to associate, speak their minds, read what they are curious about. If we are going to live in a democracy, the bulk of power needs to be with the people. If most of the power lies with companies, we will have a plutocracy. If most of the power lies with the state, we will have some kind of authoritarianism. Democracy is not a given. It is something we have to fight for every day. And if we stop building the conditions in which it thrives, democracy will be no more. Privacy is important because it gives power to the people. Protect it.
Quantum theory
Quantum dialectics
When quantum mechanics posed a threat to the Marxist doctrine of materialism, communist physicists sought to reconcile the two
Jim Baggott

Folk music was never green
Don’t be swayed by the sound of environmental protest: these songs were first sung in the voice of the cutter, not the tree
Richard Smyth

Nations and empires
A United States of Europe
A free and unified Europe was first imagined by Italian radicals in the 19th century. Could we yet see their dream made real?
Fernanda Gallo

Stories and literature
On Jewish revenge
What might a people, subjected to unspeakable historical suffering, think about the ethics of vengeance once in power?
Shachar Pinsker

Building embryos
For 3,000 years, humans have struggled to understand the embryo. Now there is a revolution underway
John Wallingford

Design and fashion
Sitting on the art
Given its intimacy with the body and deep play on form and function, furniture is a ripely ambiguous artform of its own
Emma Crichton Miller

Essay on Internet Privacy
Students are often asked to write an essay on Internet Privacy in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Internet Privacy
Understanding internet privacy.
Internet privacy is about protecting your personal data online. It’s important because when you use the internet, you share information that others could misuse.
Why is Internet Privacy Important?
Internet privacy is crucial to protect your identity and personal information. Without it, strangers could access your data, leading to potential harm.
How to Maintain Internet Privacy?
You can maintain internet privacy by using strong passwords, enabling privacy settings on social media, and avoiding sharing sensitive information online. Always remember, your online safety is in your hands.
250 Words Essay on Internet Privacy
Introduction to internet privacy.
Internet privacy, often synonymous with online privacy, is a subset of data privacy focusing on the protection of personal information in the digital realm. As the internet becomes increasingly integral to our daily lives, privacy issues have surged to the forefront of societal discourse.
The Importance of Internet Privacy
Internet privacy is crucial for numerous reasons. It safeguards personal data, prevents identity theft, and preserves freedom of speech. In the era of digitalization, a breach in privacy can lead to damaging consequences, ranging from financial loss to emotional distress.
Threats to Internet Privacy
Threats to internet privacy are manifold. They include cybercriminal activities, surveillance by government agencies, data mining by corporations, and even seemingly innocuous social media platforms that collect and utilize user data.
Internet Privacy: A Human Right?
Many argue that internet privacy is a fundamental human right. This perspective highlights the need for stringent laws and policies to protect individuals from intrusive surveillance and unauthorized data collection.
The Role of Individuals in Protecting Privacy
While legislation plays a vital role, individuals must also take proactive steps to safeguard their online privacy. This can include using encrypted communication, regularly updating software, and being mindful of the information shared online.
Internet privacy is a complex and critical issue in the digital age. The collective efforts of individuals, corporations, and governments are necessary to ensure the protection of personal information in the online sphere. As we continue to navigate this interconnected world, the importance of internet privacy will only increase.
500 Words Essay on Internet Privacy
Internet privacy is a subcategory of data privacy, focusing on the protection of user information shared online. It is a significant concern in the digital age, where data is considered the new oil. Internet privacy concerns the safeguarding of personal, financial, and data information of a private individual or organization.
Internet privacy is crucial for numerous reasons. Primarily, it protects individuals’ identity and personal information from potential cybercriminals. With the rise of the digital economy, people are increasingly sharing their sensitive data online, making them vulnerable to identity theft, cyberstalking, and other forms of cybercrime. Internet privacy also ensures the freedom of speech and thought online, as it allows individuals to express their views without fear of being tracked or monitored.
Despite its importance, internet privacy is under constant threat. Cybercriminals often exploit security breaches to steal sensitive data. Also, many online platforms and services thrive on data collection, often without clear consent from users. Governments, too, may infringe upon internet privacy for surveillance and security purposes.
The Role of Legislation in Internet Privacy
Legislation plays a crucial role in protecting internet privacy. Laws like the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States are examples of attempts to regulate data collection and usage. However, enforcing these laws across borders is challenging, and loopholes often exist that allow for continued privacy infringements.
Individual Responsibility and Internet Privacy
While legislation is important, individual responsibility is equally critical in ensuring internet privacy. Users should be aware of the data they share online and the potential risks involved. They should also use privacy-enhancing tools, such as Virtual Private Networks (VPNs), secure browsers, and encryption, to protect their data.
Conclusion: The Future of Internet Privacy
The future of internet privacy is uncertain. On one hand, advancements in technology, such as blockchain and quantum computing, could potentially enhance data security. On the other hand, the increasing digitization of our lives threatens to erode privacy further. The challenge lies in finding a balance between the benefits of the digital age and the preservation of privacy. As we move forward, the discourse on internet privacy will remain a pivotal aspect of our digital lives.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Uses and Abuses of Internet
- Essay on These Days Exposure to Television and Internet
- Essay on Internet Influence on Kids
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

Home — Essay Samples — Law, Crime & Punishment — Privacy & Security — Internet Privacy
Essays on Internet Privacy
The importance of writing an essay on internet privacy.
Writing an essay on internet privacy is crucial in today's digital age. With the increasing use of the internet for communication, social networking, and online transactions, the issue of privacy has become more important than ever. It is essential to educate people about the potential risks and threats to their privacy online and to advocate for stronger privacy protections.
Internet privacy is a fundamental human right, and writing an essay on this topic can help raise awareness about the importance of protecting personal information online. It can also encourage individuals to take steps to safeguard their privacy and advocate for laws and regulations that protect their rights.
When writing an essay on internet privacy, it is important to research and gather relevant information from credible sources. This may include academic journals, government reports, and reputable news outlets. It is also important to consider different perspectives and arguments on the topic to provide a well-rounded and comprehensive analysis.
Additionally, it is crucial to clearly articulate the potential risks and threats to internet privacy, such as data breaches, online surveillance, and identity theft. Providing real-life examples and case studies can help illustrate the impact of these issues on individuals and society as a whole.
Furthermore, it is essential to offer practical tips and solutions for protecting internet privacy, such as using strong passwords, enabling two-factor authentication, and being cautious about sharing personal information online. By empowering individuals with the knowledge and tools to protect their privacy, the essay can have a positive impact on the reader and the broader community.
Writing an essay on internet privacy is important for raising awareness, advocating for stronger privacy protections, and empowering individuals to safeguard their personal information online. By conducting thorough research, considering different perspectives, and providing practical solutions, the essay can help contribute to a more privacy-conscious and informed society.
- The importance of internet privacy in the digital age
In today's technology-driven world, internet privacy has become a major concern for individuals and businesses alike. With the increasing amount of personal information being shared online, it is important to understand the importance of protecting one's privacy on the internet. This essay will delve into the reasons why internet privacy is important and the potential consequences of not safeguarding one's online information.
- The evolution of internet privacy laws
Over the years, there have been significant developments in internet privacy laws as governments and regulatory bodies have recognized the need to protect individuals' personal information online. This essay will explore the evolution of internet privacy laws, including the landmark legislation and regulations that have been enacted to safeguard online privacy rights.
- The impact of social media on internet privacy
Social media has revolutionized the way we communicate and share information, but it has also raised concerns about internet privacy. This essay will examine the impact of social media on internet privacy, including the risks associated with sharing personal information on social networking platforms and the measures individuals can take to protect their privacy online.
- The role of technology in internet privacy
Advancements in technology have both enhanced and compromised internet privacy. This essay will discuss the role of technology in internet privacy, including the development of encryption tools, the rise of data breaches, and the potential implications of emerging technologies on online privacy rights.
- The ethical considerations of internet privacy
As individuals and businesses navigate the digital landscape, ethical considerations surrounding internet privacy have come to the forefront. This essay will explore the ethical implications of internet privacy, including the ethical responsibilities of organizations to protect user data and the ethical dilemmas individuals face when sharing personal information online.
- The impact of data breaches on internet privacy
Data breaches have become a prevalent threat to internet privacy, as cybercriminals continue to target organizations to access sensitive personal information. This essay will examine the impact of data breaches on internet privacy, including the potential consequences for individuals and businesses and the measures that can be taken to mitigate the risks of data breaches.
- The future of internet privacy
As technology continues to evolve, the future of internet privacy remains uncertain. This essay will speculate on the future of internet privacy, including the potential challenges and opportunities that lie ahead as individuals and organizations strive to protect their online privacy rights.
- The intersection of internet privacy and cybersecurity
Internet privacy and cybersecurity are closely intertwined, as both are essential for protecting personal information online. This essay will explore the intersection of internet privacy and cybersecurity, including the measures that can be taken to safeguard online privacy and the role of cybersecurity in mitigating privacy risks.
- The global perspective on internet privacy
Internet privacy is a universal concern, and different countries have varying approaches to protecting online privacy rights. This essay will provide a global perspective on internet privacy, including the international laws and regulations that govern internet privacy and the challenges of ensuring privacy rights in a global digital landscape.
- The responsibility of individuals in protecting their internet privacy
Ultimately, individuals play a crucial role in protecting their internet privacy. This essay will discuss the responsibility of individuals in safeguarding their online privacy, including the best practices for maintaining internet privacy and the potential consequences of neglecting online privacy protection.
The Internet Makes Children Smarter
Is google making usupid summary, made-to-order essay as fast as you need it.
Each essay is customized to cater to your unique preferences
+ experts online
The Importance of Internet Privacy and Net Neutrality to Internet Users in The Modern Era
Why internet privacy should be protected, the importance of internet privacy, the importance of staying safe on social media, let us write you an essay from scratch.
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Cyber Crime and Internet Privacy
The crucial role of internet privacy for a user, a privacy aspect to the internet of things, identifying threats and vulnerabilities in home internet connection, get a personalized essay in under 3 hours.
Expert-written essays crafted with your exact needs in mind
Human Rights on The Digital Era
Brief history of cyber security, privacy issues in a smart city, the concepts and outcomes of net neutrality, the singaporean government's ideologically conservative view on the internet, enhancing online security: qr code-based authentication for banking, secure online auction system, iot: addressing security challenges and possible solutions, analysis of the benefits of internet censorship, internet censorship as a modern way to protect the youth, internet censorship as the new 'norm', internet censorship: beneficial, but restrictive, personal outlook on the issue of internet censorship, useful alternatives for internet censorship, wikipedia censorship: the advantage for governments authorities, the data protection: how your personal information is used by organisations, businesses or the government, protect your data. then hope for a tech revolution, how technological advancement is going to affect us, should the internet be regulated: exploring possibilites to follow, should the internet be regulated: is it about net neutrality, relevant topics.
- Domestic Violence
- Serial Killer
- War on Drugs
- Animal Cruelty
- Juvenile Delinquency
- Criminal Psychology
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free


30,000+ students realised their study abroad dream with us. Take the first step today
Here’s your new year gift, one app for all your, study abroad needs, start your journey, track your progress, grow with the community and so much more.

Verification Code
An OTP has been sent to your registered mobile no. Please verify

Thanks for your comment !
Our team will review it before it's shown to our readers.

Speech on Internet Privacy

- Updated on
- Jul 2, 2021

It is rightly said that today’s era is a digital era. We may not realize it now, but the internet has become a new necessity in our lives. It has witnessed a boom like never before. In today’s time, the internet is as important to us as food, water, air is. Having said that, internet or internet privacy does have a dark side about which we must be aware of. Internet users must be well-versed in the methods for safeguarding their data on the internet. In this blog, we have brought to you a speech on internet privacy that you can refer to for your English homework, assignments, and exams.
Table of contents
What is internet privacy, speech on internet privacy: sample 1 (200-300 words), speech on internet privacy: sample 2 (400-500 words), relatable links.
Must Read: Essay on Internet: Advantages and Disadvantages
Before actually skipping onto the speech on internet privacy, let us first discuss what is meant by internet privacy. The amount of privacy protection an individual has while connected to the Internet is defined as online privacy or internet privacy. It discusses the level of internet security accessible for personal and financial information, conversations, and preferences. Internet users frequently try to enhance their online privacy by using anti-virus software, creating strong passwords, disabling tracking, evaluating site security, and selecting for tougher privacy settings. Online privacy threats vary from phishing schemes to viruses, and issues with website security can lead to identity theft. Internet privacy is a complicated topic that encompasses how your personal information is utilized, gathered, shared, and kept on your own devices and when connected to the Internet. Personal information about your habits, purchasing, and location can be gathered and shared with third parties via your phone, GPS, and other devices. Users of the internet and mobile devices have the right to know how their information will be used and to examine online privacy policies.
Also Read: Cyber Security Courses: A Detailed Guide and Top 10 Cybersecurity Skills for Beginners
Good morning everyone! I am Aryaman and today I stand before you to present an insightful and informative speech on Internet Privacy. Privacy, whether offline or online, is definitely our right, which should be demanded and expected no matter what the cost, but one might wonder why there is so much concern centered around internet privacy. Most of our lives have become virtual in the pandemic era, and all activities that were previously done offline are now done online. Be it our bank details, legal discussions with CA , or our professional work-related details, there is no guarantee that privacy on the internet is guarded.
In the year 1997, the Consumer Internet Privacy Protection Act was passed by the government as per which the consumer information shared on the internet should be safeguarded at any cost, but still, it is a matter of utmost concern and importance because the internet offers various communication tools which are frequently used and there too, the information being shared can be tracked by someone who knows how to do it and also technology has grown at a steadfast level that even our old messages that are deleted can be easily retrieved because of availability of countless apps. Certain websites use cookies that record data while we sign up or log in and, even if we are anonymous, it is relatively easy in this technologically advanced era to know our true identity, personal details, and Internet Service Provider details as well.
As a result, whatever web-based email services we use, such as Yahoo, Hotmail, or Gmail, we must be familiar with the privacy policies of those services before signing up or logging in to protect our privacy, and we must not hesitate to take action against heinous cybercrimes if we become aware of any kind of cyber abuse.
Also Read: Safer Internet Day 2021
Good morning everyone! I am Aryaman and today I stand before you to present an insightful and informative speech on Internet Privacy. We can define internet privacy as safeguarding our personal, financial, and other important information when we are online. However, after decoding the definition, one must ask, “Is internet privacy a reality or a myth?”Let us further explore this problem and crack the code. Due to the pandemic, most of our lives have now taken a virtual turn and most of our tasks, be it our work meetings, binge-watching our favorite web series, chatting with friends, online business transactions, and banking transactions, are all done online.
In real life, we only disclose information that we believe is not confidential, but in the online world, simple information such as email IDs and passwords can be traced by a skilled individual, and technology has advanced to the point where the internet and mobile phones are available to children, making them just as vulnerable as adults. After understanding the gravity of the situation, we must explore the ways in which we can ensure our online privacy. To begin with, there are a plethora of software applications that ensure online privacy, such as anti-viruses and anti-malware, and it is critical that these software applications are updated to their most recent version to avoid any sort of privacy problem. Second of all, internet history must be cleared on a regular basis. Online investments and banking transactions must be done through reliable sources only. Thirdly, online shopping must be done on reliable websites only which have credibility and authenticity, and we must avoid giving our information to those websites which don’t seem to be genuine and authentic. Also, we must keep a strong password for our email IDs and for other accounts as well.
We must be well-versed in Internet privacy laws, and if we encounter any type of online privacy issue, we must report it immediately so that the problem does not worsen. After attaining a crystal clear understanding of internet privacy, we must continually educate ourselves about this problem and be aware and prevent ourselves from having any sort of online privacy problem. In the end, I would like to say my heartiest thanks to the audience for listening to my speech on internet privacy with patience.
- Speech on Indian Education System
- Speech on Importance of English
- Generation Gap Speech for Students
- Sample Essay & Speech on Fear for ASL
- Speech on Co-Education For School Students
How did you all find the speech? Do let us know your thoughts on the same in the comments section. Also, feel free to reach our experts at Leverage Edu , to seek guidance at every step of your study abroad education journey.
Team Leverage Edu
Leave a Reply Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Contact no. *

Leaving already?
8 Universities with higher ROI than IITs and IIMs
Grab this one-time opportunity to download this ebook
Connect With Us
30,000+ students realised their study abroad dream with us. take the first step today..

Resend OTP in

Need help with?
Study abroad.
UK, Canada, US & More
IELTS, GRE, GMAT & More
Scholarship, Loans & Forex
Country Preference
New Zealand
Which English test are you planning to take?
Which academic test are you planning to take.
Not Sure yet
When are you planning to take the exam?
Already booked my exam slot
Within 2 Months
Want to learn about the test
Which Degree do you wish to pursue?
When do you want to start studying abroad.
September 2024
January 2025
What is your budget to study abroad?

How would you describe this article ?
Please rate this article
We would like to hear more.
Search form
A for and against essay about the internet.
Look at the essay and do the exercises to improve your writing skills.
Instructions
Do the preparation exercise first. Then read the text and do the other exercises.
Preparation

Check your writing: grouping - ideas
Check your writing: gap fill - useful phrases, worksheets and downloads.
What's your opinion? Do you think the internet is bad for young people?

Sign up to our newsletter for LearnEnglish Teens
We will process your data to send you our newsletter and updates based on your consent. You can unsubscribe at any time by clicking the "unsubscribe" link at the bottom of every email. Read our privacy policy for more information.
Essay On Internet for Students and Children
500+ words essay on internet.
We live in the age of the internet. Also, it has become an important part of our life that we can’t live without it. Besides, the internet is an invention of high-end science and modern technology . Apart from that, we are connected to internet 24×7. Also, we can send big and small messages and information faster than ever. In this essay on the Internet, we are going to discuss various things related to the internet.

Reach of Internet
It is very difficult to estimate the area that the internet cover. Also, every second million people remain connected to it with any problem or issue. Apart from that, just like all the things the internet also has some good and bad effect on the life of people. So the first thing which we have to do is learn about the good and bad effect of the internet.
Good effects of the internet mean all those things that the internet make possible. Also, these things make our life easier and safer.
Bad effects of the internet mean all those things that we can no longer do because of the internet. Also, these things cause trouble for oneself and others too.
You can access in any corner of the world. Also, it is very easy to use and manage. In today’s world, we cannot imagine our life without it.
Get the huge list of more than 500 Essay Topics and Ideas
Uses Of Internet
From the time it first came into existence until now the internet has completed a long journey. Also, during this journey, the internet has adopted many things and became more user-friendly and interactive. Besides, every big and small things are available on internet and article or material that you require can be obtainable from internet.

Tim Berners-Lee can be called one of the main father of internet as he invented/discovered the WWW (World Wide Web) which is used on every website. Also, there are millions of pages and website on the internet that it will take you years to go through all of them.
The Internet can be used to do different things like you can learn, teach, research, write, share, receive, e-mail , explore, and surf the internet.
Read Essay on Technology here
Convenience Due To Internet
Because of internet, our lives have become more convenient as compared to the times when we don’t have internet. Earlier, we have to stand in queues to send mails (letters), for withdrawing or depositing money, to book tickets, etc. but after the dawn of the internet, all these things become quite easy. Also, we do not have to waste our precious time standing in queues.
Also, the internet has contributed a lot to the environment as much of the offices (government and private), school and colleges have become digital that saves countless paper.
Although, there is no doubt that the internet had made our life easier and convenient but we can’t leave the fact that it has caused many bigger problems in the past. And with the speed, we are becoming addict to it a day in will come when it will become our basic necessity.
{ “@context”: “https://schema.org”, “@type”: “FAQPage”, “mainEntity”: [ { “@type”: “Question”, “name”: “What are the limitation of internet?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “Although internet can help you with anything but there are certain limitation to it. First of it does not have a physical appearance. Secondly, it does not have emotions and thirdly, it can’t send you to a place where you can’t go (physically).” } }, { “@type”: “Question”, “name”: “What is the ideal age for using internet?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “Nowadays everybody from small kids to adult is internet addicts. So it is difficult to decide an ideal age for using internet. However, according to researches using internet from an early age can cause problems in the child so internet usage of small children should be controlled or banned.” } } ] }
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App

Advertisement
Supported by
Can Artificial Intelligence Make the PC Cool Again?
Microsoft, HP, Dell and others unveiled a new kind of laptop tailored to work with artificial intelligence. Analysts expect Apple to do something similar.
- Share full article

By Karen Weise and Brian X. Chen
Karen Weise reported from Microsoft’s headquarters in Redmond, Wash., and Brian X. Chen from San Francisco.
The race to put artificial intelligence everywhere is taking a detour through the good old laptop computer.
Microsoft on Monday introduced a new kind of computer designed for artificial intelligence. The machines, Microsoft says, will run A.I. systems on chips and other gear inside the computers so they are faster, more personal and more private.
The new computers, called Copilot+ PC, will allow people to use A.I. to make it easier to find documents and files they have worked on, emails they have read, or websites they have browsed. Their A.I. systems will also automate tasks like photo editing and language translation.
The new design will be included in Microsoft’s Surface laptops and high-end products that run on the Windows operating system offered by Acer, Asus, Dell, HP, Lenovo and Samsung, some of the largest PC makers in the world .
The A.I. PC, industry analysts believe, could reverse a longtime decline in the importance of the personal computer. For the last two decades, the demand for the fastest laptops has diminished because so much software was moved into cloud computing centers. A strong internet connection and web browser was all most people needed.
But A.I. stretches that long-distance relationship to its limits. ChatGPT and other generative A.I. tools are run in data centers stuffed with expensive and sophisticated chips that can process the largest, most advanced systems. Even the most cutting-edge chatbots take time to receive a query, process it and send back a response. It is also extremely expensive to manage.
Microsoft wants to run A.I. systems directly on a personal computer to eliminate that lag time and cut the price. Microsoft has been shrinking the size of A.I. systems, called models, to make them easier to run outside of data centers. It said more than 40 will run directly on the laptops. The smaller models are generally not as powerful or accurate as the most cutting-edge A.I. systems, but they are improving enough to be useful to the average consumer.
“We are entering a new era where computers not only understand us, but can anticipate what we want and our intents,” said Satya Nadella, Microsoft’s chief executive, at an event at its headquarters in Redmond, Wash.
Analysts expect Apple to follow suit next month at its conference for software developers, where the company will announce an overhaul for Siri , its virtual assistant, and an overall strategy for integrating more A.I. capabilities into its laptops and iPhones.
Whether the A.I. PC takes off depends on the companies’ ability to create compelling reasons for buyers to upgrade. The initial sales of these new computers, which cost more than $1,000, will be small, said Linn Huang, an analyst at IDC, which closely tracks the market. But by the end of the decade — assuming A.I. tools turn out to be useful — they will be “ubiquitous,” he predicted. “Everything will be an A.I. PC.”
The computer industry is looking for a jolt. Consumers have been upgrading their own computers less frequently, as the music and photos they once stored on their machines now often live online, on Spotify, Netflix or iCloud. Computer purchases by companies, schools and other institutions have finally stabilized after booming — and then crashing — during the pandemic.
Some high-end smartphones have already been integrating A.I. chips, but the sales have fallen short because the features “are still not sophisticated enough to catalyze a faster upgrade cycle,” Mehdi Hosseini, an analyst at Susquehanna International Group, wrote in a research note. It will be at least another year, he said, before enough meaningful breakthroughs will lead consumers to take note.
At the event, Microsoft showed new laptops with what it likened to having a photographic memory. Users can ask Copilot, Microsoft’s chatbot, to use a feature called Recall to look up a file by typing a question using natural language, such as, “Can you find me a video call I had with Joe recently where he was holding an ‘I Love New York’ coffee mug?” The computer will then immediately be able to retrieve the file containing those details because the A.I. systems are constantly scanning what the user does on the laptop.
“It remembers things that I forget,” said Matt Barlow, Microsoft’s head of marketing for Surface computers, in an interview.
Microsoft said the information used for this Recall function was stored directly on the laptop for privacy, and would not be sent back to the company’s servers or be used in training future A.I. systems. Pavan Davuluri, a Microsoft executive overseeing Windows, said that with the Recall system users would also be able to opt out of sharing certain types of information, such as visits to a specific website, but that some sensitive data, such as financial information and private browsing sessions, would not be monitored by default.
Microsoft also demonstrated live transcripts that translate in real time, which it said would be available on any video that streams across a laptop’s screen.
Microsoft last month released A.I. models small enough to run on a phone that it said performed almost as well as GPT-3.5, the much larger system that initially underpinned OpenAI’s ChatGPT chatbot when it debuted in late 2022.
(The New York Times sued OpenAI and Microsoft in December for copyright infringement of news content related to A.I. systems.)
Chipmakers have also made advances, like adjusting a laptop’s battery life to allow for the enormous number of calculations that A.I. demands. The new computers have dedicated chips built by Qualcomm, the largest chip provider for smartphones.
Though the type of chip inside the new A.I. computers, known as a neural processing unit, specializes in handling complex A.I. tasks, such as generating images and summarizing documents, the benefits may still be unnoticeable to consumers, said Subbarao Kambhampati, a professor and researcher of artificial intelligence at Arizona State University.
Most of the data processing for A.I. still has to be done on a company’s servers instead of directly on the devices, so it’s still important that people have a fast internet connection, he added.
But the neural processing chips also speed up other tasks, such as video editing or the ability to use a virtual background inside a video call, said Brad Linder, the editor of Liliputing, a blog that has covered computers for nearly two decades. So, even if people don’t buy into the hype surrounding artificial intelligence, they may end up getting an A.I. computer for other reasons.
Karen Weise writes about technology and is based in Seattle. Her coverage focuses on Amazon and Microsoft, two of the most powerful companies in America. More about Karen Weise
Brian X. Chen is the lead consumer technology writer for The Times. He reviews products and writes Tech Fix , a column about the social implications of the tech we use. More about Brian X. Chen
Explore Our Coverage of Artificial Intelligence
News and Analysis
Hoping to make the personal computer cool again, Microsoft, HP, Dell and others unveiled a new kind of laptop tailored to work with A.I.
Ilya Sutskever, the OpenAI co-founder and chief scientist who in November joined three other board members to force out Sam Altman before saying he regretted the move, is leaving the company .
OpenAI has unveiled a new version of its ChatGPT chatbot that can receive and respond to voice commands, images and videos.
The Age of A.I.
D’Youville University in Buffalo had an A.I. robot speak at its commencement . Not everyone was happy about it.
A new program, backed by Cornell Tech, M.I.T. and U.C.L.A., helps prepare lower-income, Latina and Black female computing majors for A.I. careers.
Publishers have long worried that A.I.-generated answers on Google would drive readers away from their sites. They’re about to find out if those fears are warranted, our tech columnist writes .
A new category of apps promises to relieve parents of drudgery, with an assist from A.I. But a family’s grunt work is more human, and valuable, than it seems.
Professor Jeffrey Gonzalez publishes review essay in “Public Books”
Posted in: English Department , Homepage News and Events

English professor Jeffrey Gonzalez recently published a review essay discussing Sonic Youth member Thurston Moore’s memoir, Sonic Life , in the online magazine Public Books . Professor Gonzalez’s review, which appeared on May 16, was included in Lithub’s “ LitHub Daily, ” whose editors describe their selections as “the best of the literary internet,” on May 20.

Retrace your steps with Recall
Search across time to find the content you need. Then, re-engage with it. With Recall, you have an explorable timeline of your PC’s past. Just describe how you remember it and Recall will retrieve the moment you saw it. Any photo, link, or message can be a fresh point to continue from. As you use your PC, Recall takes snapshots of your screen. Snapshots are taken every five seconds while content on the screen is different from the previous snapshot. Your snapshots are then locally stored and locally analyzed on your PC. Recall’s analysis allows you to search for content, including both images and text, using natural language. Trying to remember the name of the Korean restaurant your friend Alice mentioned? Just ask Recall and it retrieves both text and visual matches for your search, automatically sorted by how closely the results match your search. Recall can even take you back to the exact location of the item you saw.
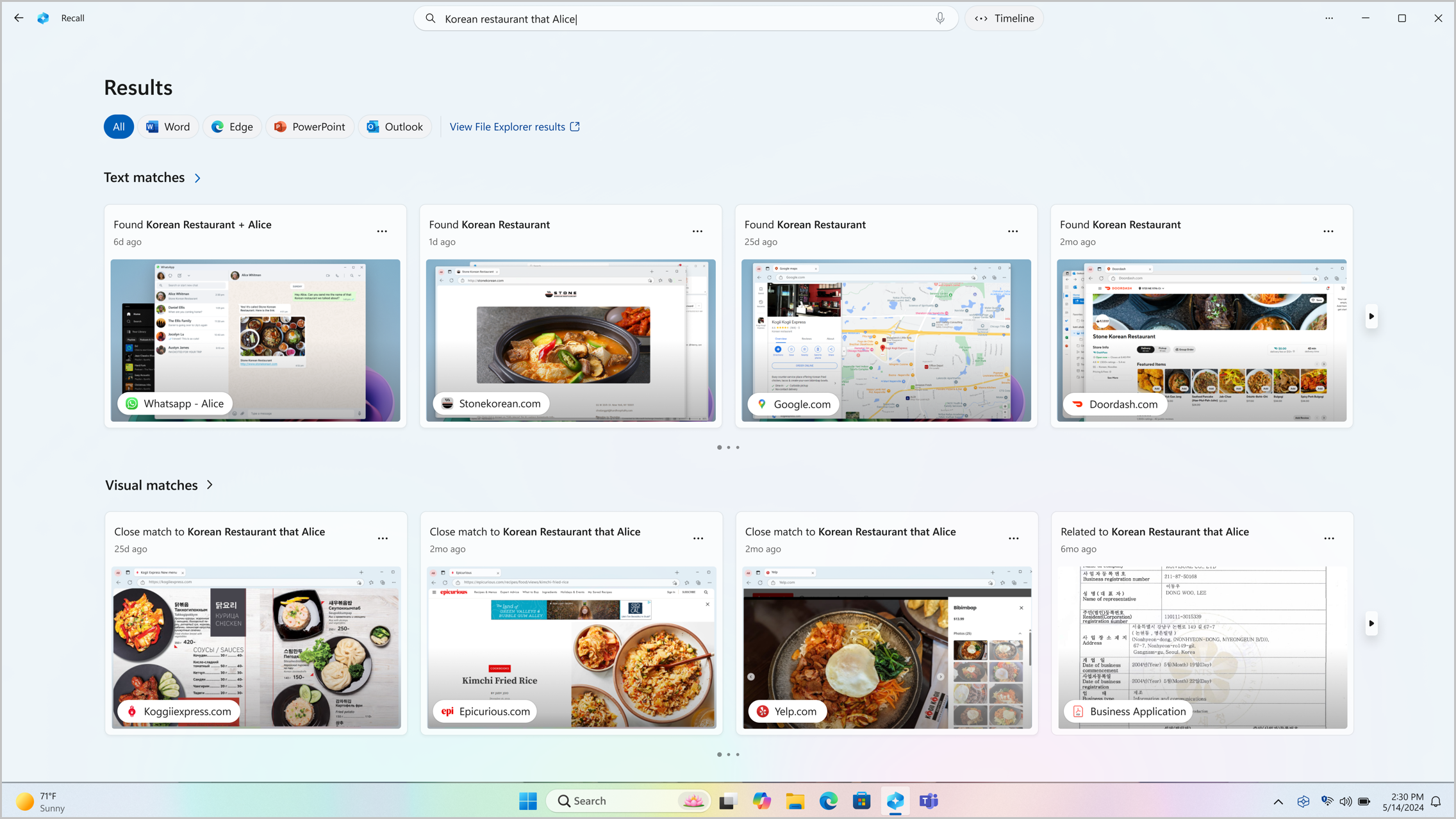
Note: Recall is optimized for select languages (English, Chinese (simplified), French, German, Japanese, and Spanish. Content-based and storage limitations apply. For more information, see https://aka.ms/nextgenaipcs .
System requirements for Recall
Your PC needs the following minimum system requirements for Recall:
A Copilot+ PC
8 logical processors
256 GB storage capacity
To enable Recall, you’ll need at least 50 GB of storage space free
Saving screenshots automatically pauses once the device has less than 25 GB of storage space
How to use Recall
To open Recall, use the keyboard shortcut +J , or select the following Recall icon on your taskbar:

Your timeline in Recall is broken up into segments, which are the blocks of time that Recall was taking snapshots while you were using your PC. You can hover over your timeline to review your activity in a preview window. Selecting the location on the timeline or selecting the preview window loads the snapshot where you can interact with the content .
Search with Recall
Maybe you wanted to make that pizza recipe you saw earlier today but you don’t remember where you saw it. Typing goat cheese pizza into the search box would easily find the recipe again. You could also search for pizza or cheese if you didn’t remember the specific type of pizza or cheese. Less specific searches are likely to bring up more matches though. If you prefer to search using your voice, you can select the microphone then speak your search query.
By default, results are shown from all apps where Recall found matches. You can narrow down your results by filtering the matches to a specific app by selecting an app from the list.
When the results are displayed, they will be listed under the headings of text matches and visual matches . Matches that are closer to your search are shown first. You’ll also notice that some items are listed as one of the following types of matches:
Close match : Close matches typically include at least one of the search terms or images that are representative of a term in your query.
Related match : Matches that share a commonality with the search terms would be considered related. For instance, if you searched for goat cheese pizza , you might also get related matches that include lasagna or cannelloni since they are Italian dishes too.
Interacting with content
Once you’ve found the item you want to see again, select the tile. Recall opens the snapshot and enables screenray, which runs on top of the saved snapshot. Screenray analyzes what’s in the snapshot and allows you to interact with individual elements in the snapshot. You’ll notice that when screenray is active, your cursor is blue and white. The cursor also changes shape depending on the type of element beneath it. What you can do with each element changes based on what kind of content screenray detects. If you select a picture in the snapshot, you can copy, edit with your default .jpeg app such as Photos , or send it to another app like the Snipping Tool or Paint . When you highlight text with screenray, you can open it in a text editor or copy it. For example, you might want to copy the text of a recipe’s ingredients list to convert it to metric.
Note: When you use an option that sends snapshot content to an app, screenray creates a temporary file in C:\Users\[username]\AppData\Local\Temp in order to share the content. The temporary file is deleted once the content is transferred over the app you selected to use.
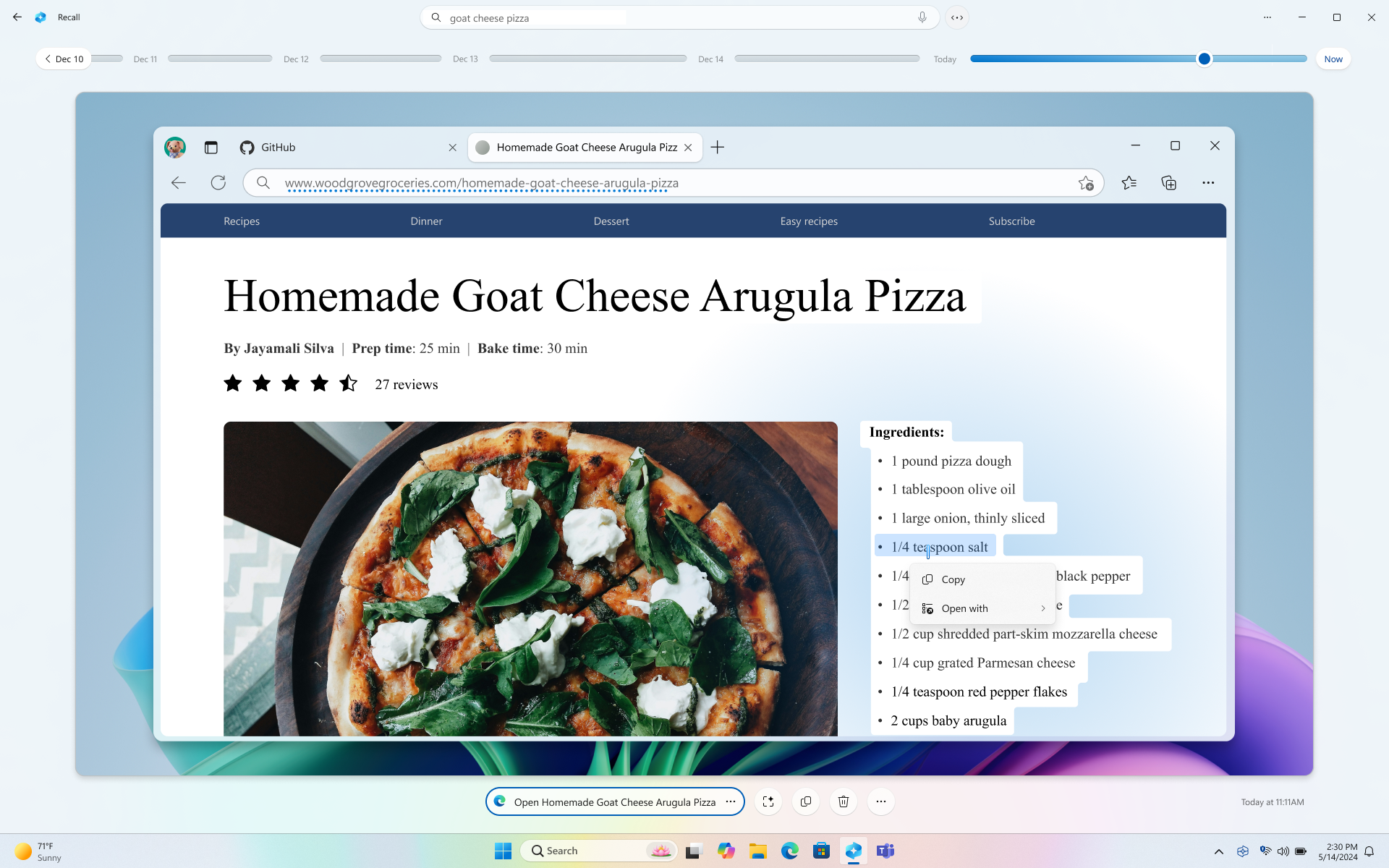
Below your selected snapshot, you have more snapshot options. In many cases, you can have Recall take you back to exact location of the item, such as reopening the webpage, PowerPoint presentation, or app that was running at the time the snapshot was taken. You can also hide screenray, copy the snapshot, delete the snapshot, or select … for more snapshot options.
Pause or resume snapshots
To pause recall, select the Recall icon in the system tray then Pause until tomorrow . Snapshots will be paused until they automatically resume at 12:00 AM. When snapshots are paused, the Recall system tray icon has a slash through it so you can easily tell if snapshots are enabled. To manually resume snapshots, select the Recall icon in the system tray and then select Resume snapshots . You can also access the Recall & snapshots settings page from the bottom of this window.
What if I don’t want Recall to save information from certain websites or apps?
You are in control with Recall. You can select which apps and websites you want to exclude, such as banking apps and websites. You’ll need to use a supported browser for Recall to filter websites and to automatically filter private browsing activity. Supported browsers, and their capabilities include:
Microsoft Edge: blocks websites and filters private browsing activity
Firefox: blocks websites and filters private browsing activity
Opera: blocks websites and filters private browsing activity
Google Chrome: blocks websites and filters private browsing activity
Chromium based browsers: For Chromium-based browsers not listed above, filters private browsing activity only, doesn’t block specific websites
To exclude a website:
Select … then Settings to open the Recall & snapshots settings page.
You can also go to Windows Settings > Privacy & Security > Recall & Snapshots to manage Recall.
Select Add website for the Websites to filter setting.
Type the website you want to filter into the text box. Select Add to add it to the websites to filter list.
To exclude an app:
Select … then Settings to open the Recall & snapshots settings page
Select Add app for the Apps to filter setting.
From the app list, select the app you want to filter from Recall snapshots.
In two specific scenarios, Recall will capture snapshots that include InPrivate windows, blocked apps, and blocked websites. If Recall gets launched, or the Now option is selected in Recall, then a snapshot is taken even when InPrivate windows, blocked apps, and blocked websites are displayed. However, these snapshots are not saved by Recall. If you choose to send the information from this snapshot to another app, a temp file will also be created in C:\Users\[username]\AppData\Local\Temp to share the content. The temporary file is deleted once the content is transferred over the app you selected to use.
Managing your Recall snapshots and disk space
You can configure how much disk space Recall is allowed to use to store snapshots. The amount of disk space you can allocate to Recall varies depending on how much storage your PC has. The following chart shows the storage space options for Recall:
You can change the amount of disk space used or delete snapshots from the Recall & snapshots settings page.
To change the storage space limit:
1. Expand the Storage settings.
2. Change the Maximum storage for snapshots limit by choosing the limit from the drop-down list. When the limit is reached, the oldest snapshots are deleted first.
To delete snapshots:
Expand the Delete snapshots settings.
You can choose to delete all snapshots or snapshots withing a specific timeframe.
To delete all snapshots, select Delete all .
To delete snapshots from a specific timeframe, select a timeframe from the drop-down list, then select Delete snapshots.
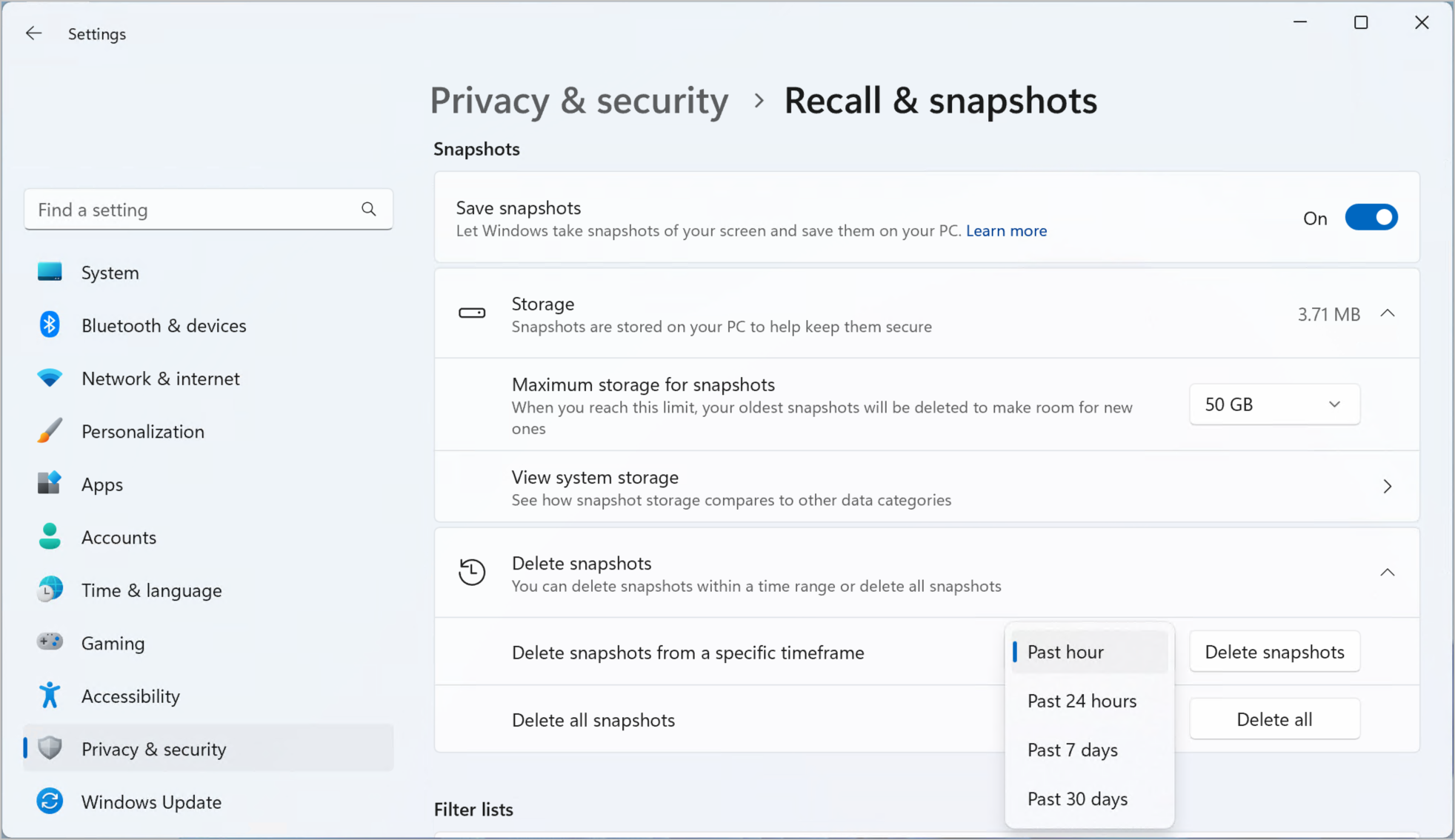
Keyboard shortcuts for Recall
You can use the following keyboard shortcuts in recall:, when interacting with a snapshot with screenray, you can use the following keyboard shortcuts:, microsoft’s commitment to responsible ai and privacy.
Microsoft has been working to advance AI responsibly since 2017, when we first defined our AI principles and later operationalized our approach through our Responsible AI Standard. Privacy and security are principles as we develop and deploy AI systems. We work to help our customers use our AI products responsibly, sharing our learnings, and building trust-based partnerships. For more about our responsible AI efforts, the principles that guide us, and the tooling and capabilities we've created to assure that we develop AI technology responsibly, see Responsible AI .
Recall uses optical character recognition (OCR), local to the PC, to analyze snapshots and facilitate search. For more information about OCR, see Transparency note and use cases for OCR . For more information about privacy and security, see Privacy and security for Recall & screenray .
We want to hear from you!
If there's something you like, and especially if there's something you don't like, about Recall you can submit feedback to Microsoft by selecting … then the Feedback icon in Recall to submit feedback on any issues that you run into.

Need more help?
Want more options.
Explore subscription benefits, browse training courses, learn how to secure your device, and more.

Microsoft 365 subscription benefits

Microsoft 365 training

Microsoft security

Accessibility center
Communities help you ask and answer questions, give feedback, and hear from experts with rich knowledge.

Ask the Microsoft Community

Microsoft Tech Community

Windows Insiders
Microsoft 365 Insiders
Was this information helpful?
Thank you for your feedback.
Government Internet Surveillance: Privacy Threat Essay
Introduction, the internet and surveillance, us government surveillance, surveillance efforts a threat to privacy and civil rights, justification for surveillance, discussion and conclusion.
The internet is the most important invention of the twentieth century and it has dramatically transformed human life. This invention has greatly increased the speed and efficiency with which communication occurs. Its unrivalled benefits in information processing have made this technology a part of most aspects of modern-daily activities.
Boghosian (2013) notes that while the internet plays a major role in improving life in our society, some sinister applications of this invention undermine privacy and civil rights. Perhaps the most troubling applications of the internet in current times are the mass surveillance efforts by the US government. This paper will argue that government internet surveillance is a threat to the privacy and civil rights of US citizens and it must therefore be mitigated.
Government surveillance has existed in various forms for centuries. Through this activity, the government has been able to obtain valuable public and secret information and act on it to aid governance. The internet age has dramatically increased the ability of government to engage in surveillance.
To begin with, the internet has become the most common medium of communication for many people. By monitoring this single communication network, the government has access to virtually all information that is communicated electronically including email habits, credit card, bank records, and phone records (Regan, 2014). The advancement in storage technology has contributed to the pervasive surveillance carried out by the US.
Today, the data that can be stored is nearly infinite due to the tremendous growth in storage capacity and the decline in storage prices. Intelligence agencies are therefore able to collect all available data since it is cheaper and easier than trying to determine what data should be stored and what should be ignored. At the same time, sophisticated computer algorithms make it possible for government agencies to analyze large amounts of data and derive meaning from it.
Scherer (2013) states that while electronic intelligence in the US historically focused on foreign governments, the events of 9/11 led to an increased focus on American citizens. Starting from that year, the NSA turned inward and shifted its focus to include private individuals. This shift was prompted by the understanding that the perpetrators of the 9/11 attacks had resided in the US and made their plans while living in the country. Since then, the government has engaged in widespread surveillance of its citizens in an attempt to prevent crime.
The internet has made it possible for the government to engage in mass surveillance. Through security apparatus such as the NSA, the American government can collect and analyze vast quantities of data about its citizens. These activities often take place without the consent or knowledge of the individual.
Revelations by Snowden showed that the government engaging in surveillance at a scale that a majority of society did not even think was possible (Scherer, 2013). Through US dedicates more than $52.6 billion each year to run a massive secret national security apparatus. This apparatus includes the NSA, which has over 30,000 employees and gathers and stores not only phone records in the US but also metadata on internet traffic.
To increase its surveillance abilities, the US government has engaged in programs aimed at influencing IT companies to provide the NSA with a back door to encrypted communications. Scherer (2013) documents that through such a program, the government denies private citizens of their right to create unbreakable encryption software.
Wide scale surveillance by the government has harmed the privacy rights of US citizens. Government internet surveillance efforts result in a violation of individual privacy as the government intercepts the personal information and communication from US citizens. For privacy to exist, an individual has to have control over himself and the information he shares with others.
Boghosian (2013) notes that attempts to safeguard the privacy of American have been compromised by the government’s demand for unrestricted access to information. Under the Patriot Act, the government has access to a wide array of personal information. Through the National Security Administration (NSA), the government has engaged in large-scale data collection on US citizens.
This data is then analyzed in an effort to identify suspects. However, this data can be used to obtain more information about the private lives of Americans thus violating individual privacy.
The right to free speech and association are affected by the existence of extensive internet surveillance programs. According to the freedom of speech right, an individual is entitled to communicate his personal opinion or ideas with others without the fear of repercussions. The freedom of association guarantees an individual the right to relate with persons or groups of his choosing without any external inhibitions.
Purkayastha and Bailey (2014) observe that mass surveillance undermines free speech as individuals may face retaliation action if they are critical of the government. The government may engage in steps to silence critics who are identified through the surveillance efforts. Private Citizens concerned that their communications may be under surveillance are likely to avoid making their opinions public out of fear of government reprisal. Internet surveillance will therefore have led to the violation of the civil rights of these US citizens.
Government surveillance violates the location privacy of an individual. Boghosian (2013) defines location privacy as the right of an American to move in public without being tracked on monitored. This right is violated by unrestricted surveillance by the government. By monitoring Global Positioning System (GPS) devices, the government can record the precise movement of an individual. His/her exact location at any time can be record and stored helping to create an elaborate profile on the individual’s movement patterns.
The Fourth Amendment, which guarantees Americans protection against unreasonable searchers and seizures is violated by the undiscriminating internet surveillance. Through this mass collection and scrutinizing of personal information, the government violates the requirements of the Fourth Amendment. Scherer (2013) confirms that unreasonable searches that take place with no justification characterize the internet surveillance carried out by the government. The government collects data from all citizens and then analyzes this information in the hope of finding patterns that will help identify criminals.
The US government has justified its aggressive surveillance activities as necessary efforts for the enhancement of national security. In a speech on the importance of surveillance, the US President Barack Obama asserts that these activities enable law enforcement officers to detect terrorists and prevent them from carrying out attacks against the US (Obama, 2014). Even ordinary US citizens recognize this positive role of internet monitoring.
While most Americans are opposed to government surveillance, there is a recognition that the government might need to engage in monitoring efforts in order to safeguard the homeland. Scherer (2013) notes that according to polls, a majority of Americans show continued willingness to give up some of their rights to privacy as part of efforts to combat terrorism.
Government surveillance of the internet helps to protect citizens from the dangers that an abuse of the internet can cause. The internet provides individual users with significant power due to the wide range of information contained on the network and the communication efficiency.
These attributes can be exploited for wrong purposes if the government does not police the network. Seidler (2013) confirms that the government might be forced to carry out secret activities for the benefit of its citizens. Through surveillance, the government can identify questionable activities by citizens and engage in further investigation. Such efforts might lead to the discovery and stopping of criminal elements before they carry out crime.
Under the Obama Administration, the US has continued and even expanded the electronic surveillance implemented by the Bush administration. The justification for this is that the surveillance regime is integral to protecting the US against Foreign and Homegrown terrorists. Even so, Obama (2014) admits that the prevalent internet monitoring creates a potential for abuse. Action therefore needs to be taken against government surveillance on its citizens.
According to the renowned American whistleblower, Edward Snowden, the important players in this issue include “the public, the technologist community, the U.S. courts, Congress and the Executive Branch” (Scherer, 2013, p.81). These bodies need to deliberate on the future of the country if government surveillance is allowed to go on uninhibited.
As it currently stands, Internet surveillance has given the government intrusive police power that can be used against innocent civilians. The liberties of Americans have been constricted by the deployment of the surveillance infrastructure. Action needs to be taken to address these issues and restore the privacy and civil liberties guaranteed to American citizens by the US Constitution.
Boghosian, H. (2013). The Business of Surveillance. Human Rights, 39 (3), 2-23.
Obama, B. (2014). Remarks by the President on Review of Signals Intelligence . Web.
Purkayastha, P., & Bailey, R. (2014). U.S. Control of the Internet Problems Facing the Movement to International Governance. Independent Socialist Magazine, 66 (3), 103-127.
Regan, L. (2014). Electronic Communications Surveillance. Independent Socialist Magazine, 66 (3), 32-42.
Scherer, M. (2013). Number Two Edward Snowden The Dark Prophet. Time, 182 (26), 78-89.
Seidler, N. (2013). A perspective on principles for Internet surveillance .
- National Security Agency and Privacy Violation
- Collecting the phone data logs of all citizens
- American National Security and Technology Evolution
- Has E-Government Failed?
- E-Government and Technological Change
- E-Government (M-Government) in Dubai
- Review and Analysis of the U.S. and UK Government Websites
- E-Government Initiatives: A Critical Discussion
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2020, March 25). Government Internet Surveillance: Privacy Threat. https://ivypanda.com/essays/government-internet-surveillance-privacy-threat/
"Government Internet Surveillance: Privacy Threat." IvyPanda , 25 Mar. 2020, ivypanda.com/essays/government-internet-surveillance-privacy-threat/.
IvyPanda . (2020) 'Government Internet Surveillance: Privacy Threat'. 25 March.
IvyPanda . 2020. "Government Internet Surveillance: Privacy Threat." March 25, 2020. https://ivypanda.com/essays/government-internet-surveillance-privacy-threat/.
1. IvyPanda . "Government Internet Surveillance: Privacy Threat." March 25, 2020. https://ivypanda.com/essays/government-internet-surveillance-privacy-threat/.
Bibliography
IvyPanda . "Government Internet Surveillance: Privacy Threat." March 25, 2020. https://ivypanda.com/essays/government-internet-surveillance-privacy-threat/.

VIDEO
COMMENTS
Get custom essay. Ultimately, the importance of internet privacy extends beyond individual convenience; it is a fundamental right that underpins our freedom, security, and individuality in the digital age. By recognizing the significance of internet privacy and taking meaningful steps to protect it, we can ensure that the digital landscape ...
The user should have knowledge of how his or her information is being collected, the purpose of collection and how the party is going to use the information.
9 essay samples found. Internet privacy refers to the right or expectation of privacy in the digital realm, encompassing issues related to the protection of personal data, confidentiality, and anonymity online. Essays on internet privacy could delve into the risks and challenges associated with digital surveillance, data breaches, or online ...
1. Views of data privacy risks, personal data and digital privacy laws. Online privacy is complex, encompassing debates over law enforcement's data access, government regulation and what information companies can collect. This chapter examines Americans' perspectives on these issues and highlights how views vary across different groups ...
Power over others' privacy is the quintessential kind of power in the digital age. T wo years after it was funded and despite its popularity, Google still hadn't developed a sustainable business model. In that sense, it was just another unprofitable internet startup. Then, in 2000, Google launched AdWords, thereby starting the data economy.
Companies and governments are gaining new powers to follow people across the internet and around the world, and even to peer into their genomes. The benefits of such advances have been apparent ...
After learning about the information that has come to light, students need the opportunity to explore their own thoughts and feelings on this important issue. These 50 new journal prompts offer students the chance to think about their own right to privacy, the government's motives for surveillance, and the ramifications of wide-scale public ...
The present paper has evaluated several methodologies through which users can guarantee privacy on the internet. Some of the methodologies discussed include employing strong passwords, making use of antivirus software, using secure systems, safe Internet browsing, avoiding fake websites and avoiding phishing sites.
Now that system, which ballooned into a $350 billion digital ad industry, is being dismantled. Driven by online privacy fears, Apple and Google have started revamping the rules around online data ...
A privacy guideline plays an important role with regard to personal information collected on the internet. Sound policies enable users to feel comfortable because it enables the user in identifying safe sites on the internet.
Internet privacy involves the right or mandate of personal privacy concerning the storage, re-purposing, provision to third parties, and display of information pertaining to oneself via the Internet. [1] [2] Internet privacy is a subset of data privacy .
Internet privacy is a subcategory of data privacy, focusing on the protection of user information shared online. It is a significant concern in the digital age, where data is considered the new oil. Internet privacy concerns the safeguarding of personal, financial, and data information of a private individual or organization.
Over 30 years ago, Mason (Citation 1986) voiced ethical concerns over the protection of informational privacy, or "the ability of the individual to personally control information about one's self" (Stone et al., Citation 1983), calling it one of the four ethical issues of the information age.Since the 1980s, scholars have remained concerned about informational privacy, especially given ...
Writing an essay on internet privacy is important for raising awareness, advocating for stronger privacy protections, and empowering individuals to safeguard their personal information online. By conducting thorough research, considering different perspectives, and providing practical solutions, the essay can help contribute to a more privacy ...
From 2010- 2012 it continues to rise beyond 350,000 per year, with a monetary loss of over $300 million per year. The top 5 internet scams per (Info-graphic Highlights) with the most complaints: 1. 14.4 % - Identity theft. 2. 13.2% - FBI-related scams. 3. 9.8% - Miscellaneous fraud.
Internet privacy is the security of a user's personal data that is stored or published on the internet. The internet is an important part of every individual's daily life. In today's society, the internet is used by many different people for many reasons. It can be used for research, communication, and purchasing items.
Internet privacy is a complicated topic that encompasses how your personal information is utilized, gathered, shared, and kept on your own devices and when connected to the Internet. Personal information about your habits, purchasing, and location can be gathered and shared with third parties via your phone, GPS, and other devices.
Internet security is important to protect our privacy, protect us from fraud, and from viruses that could destroy a piece of our technology. Internet privacy and security may be different but share a responsibility, but it is up to us to take personal responsibility to protect ourselves on the internet.
Even though most of this is true, there are plenty of good things to come from it. In this essay I will be writing about the internet and its privacy. The lack of privacy that comes with technology and the internet can and has prevented a lot of crimes to occur. It has made credit card fraud, once an easy crime much harder to get away with.
Worksheets and downloads. A for and against essay about the internet - exercises 592.59 KB. A for and against essay about the internet - answers 136.91 KB. A for and against essay about the internet - essay 511.93 KB. A for and against essay about the internet - writing practice 522.94 KB.
Get Started. We live in the age of the internet. And, it has become an important part of our life. Besides, internet is an invention of high-end science and modern technology. Apart from that, we are connected to internet 24x7. In this essay on Internet, we are going to discuss various things related to the internet.
The growing online presence also created an unprecedented visibility opportunities, which immediately raised privacy concerns. With the increasing number of controversies surrounding the safety of personal information, the Internet has been termed by some "the final blow to privacy.". However, I argue that while it certainly changed the way ...
The race to put artificial intelligence everywhere is taking a detour through the good old laptop computer. Microsoft on Monday introduced a new kind of computer designed for artificial ...
English professor Jeffrey Gonzalez recently published a review essay discussing Sonic Youth member Thurston Moore's memoir, Sonic Life, in the online magazine Public Books. Professor Gonzalez's review, which appeared on May 16, was included in Lithub's "LitHub Daily," whose editors describe their selections as "the best of the literary internet," on May 20.
Use this command to enable a security prompt when opening a workbook that contains a Python formula. It enables a Security Warning notice in the Excel business bar. reg add HKCU\software\policies\microsoft\office\16.0\excel\security /v PythonFunctionWarnings /t REG_DWORD /d 1 /f. Use this command to disable all Python functions from running.
To open Recall, use the keyboard shortcut +J, or select the following Recall icon on your taskbar: Your timeline in Recall is broken up into segments, which are the blocks of time that Recall was taking snapshots while you were using your PC. You can hover over your timeline to review your activity in a preview window.
Wide scale surveillance by the government has harmed the privacy rights of US citizens. Government internet surveillance efforts result in a violation of individual privacy as the government intercepts the personal information and communication from US citizens. For privacy to exist, an individual has to have control over himself and the ...
I am thrilled to announce that Windows 11 IoT Enterprise LTSC 2024 is here! - the next evolution in Microsoft's innovative IoT platform designed to empower device makers with unparalleled intelligence, security, and flexibility at the edge.