Cyber Security Essay for Students and Children
Cyber security essay.
Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today’s world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software. This software protects the data. Cybersecurity is important because not only it helps to secure information but also our system from virus attack. After the U.S.A. and China, India has the highest number of internet users.


Cyber Threats
It can be further classified into 2 types. Cybercrime – against individuals, corporates, etc.and Cyberwarfare – against a state.
Cyber Crime
Use of cyberspace, i.e. computer, internet, cellphone, other technical devices, etc., to commit a crime by an individual or organized group is called cyber-crime. Cyber attackers use numerous software and codes in cyberspace to commit cybercrime. They exploit the weaknesses in the software and hardware design through the use of malware. Hacking is a common way of piercing the defenses of protected computer systems and interfering with their functioning. Identity theft is also common.
Cybercrimes may occur directly i.e, targeting the computers directly by spreading computer viruses. Other forms include DoS attack. It is an attempt to make a machine or network resource unavailable to its intended users. It suspends services of a host connected to the internet which may be temporary or permanent.
Malware is a software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It usually appears in the form of code, scripts, active content, and other software. ‘Malware’ refers to a variety of forms of hostile or intrusive software, for example, Trojan Horses, rootkits, worms, adware, etc.
Another way of committing cybercrime is independent of the Computer Network or Device. It includes Economic frauds. It is done to destabilize the economy of a country, attack on banking security and transaction system, extract money through fraud, acquisition of credit/debit card data, financial theft, etc.
Hinder the operations of a website or service through data alteration, data destruction. Others include using obscene content to humiliate girls and harm their reputation, Spreading pornography, threatening e-mail, assuming a fake identity, virtual impersonation. Nowadays misuse of social media in creating intolerance, instigating communal violence and inciting riots is happening a lot.
Get the huge list of more than 500 Essay Topics and Ideas
Cyber Warfare
Snowden revelations have shown that Cyberspace could become the theatre of warfare in the 21st century. Future wars will not be like traditional wars which are fought on land, water or air. when any state initiates the use of internet-based invisible force as an instrument of state policy to fight against another nation, it is called cyberwar’.
It includes hacking of vital information, important webpages, strategic controls, and intelligence. In December 2014 the cyberattack a six-month-long cyberattack on the German parliament for which the Sofacy Group is suspected. Another example 2008 cyberattack on US Military computers. Since these cyber-attacks, the issue of cyber warfare has assumed urgency in the global media.
Inexpensive Cybersecurity Measures
- The simplest thing you can do to up your security and rest easy at night knowing your data is safe is to change your passwords.
- You should use a password manager tool like LastPass, Dashlane, or Sticky Password to keep track of everything for you. These applications help you to use unique, secure passwords for every site you need while also keeping track of all of them for you.
- An easy way for an attacker to gain access to your network is to use old credentials that have fallen by the wayside. Hence delete unused accounts.
- Enabling two-factor authentication to add some extra security to your logins. An extra layer of security that makes it harder for an attacker to get into your accounts.
- Keep your Softwares up to date.
Today due to high internet penetration, cybersecurity is one of the biggest need of the world as cybersecurity threats are very dangerous to the country’s security. Not only the government but also the citizens should spread awareness among the people to always update your system and network security settings and to the use proper anti-virus so that your system and network security settings stay virus and malware-free.
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App

Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
U.S. school security procedures have become more widespread in recent years but are still unevenly adopted

Many public K-12 schools in the United States have taken steps in recent years to tighten security, including outfitting classroom doors with interior locks, drafting active shooter preparedness plans and hiring sworn law enforcement officers to patrol buildings, according to recently released data from the National Center for Education Statistics (NCES). Still, school security protocols vary widely by type of school, geography and other factors.
The new data comes amid heightened attention to school security after a deadly shooting at an elementary school in Uvalde, Texas, in May. In the wake of the Uvalde shooting, here is a look at some of the most common school security measures and how the K-12 security landscape has changed in recent years.
This analysis relies on data collected by the federal government to assess the security measures that public K-12 schools in the United States have employed in recent years, as well as how the adoption of these protocols varies by type of school, region and other factors. The analysis draws on nearly two decades of survey data from the School Survey on Crime and Safety by the National Center for Education Statistics (NCES). The most recent data available for U.S. public schools is from the 2019-20 school year and includes responses from both traditional public schools and charter schools.
More information on the survey’s methodology can be found in the NCES report.
Building security
The vast majority of U.S. public K-12 schools (including traditional public schools and charter schools) reported taking steps to physically secure buildings and classrooms during the 2019-20 school year, the most recent year for which data is available. Almost all schools restricted entry by controlling access to buildings during school hours with measures such as locked or monitored doors and loading docks (97%), or by requiring visitors to sign or check in and wear a badge (98%). Around three-quarters (73%) had classrooms equipped with locks so that doors can be locked from inside.
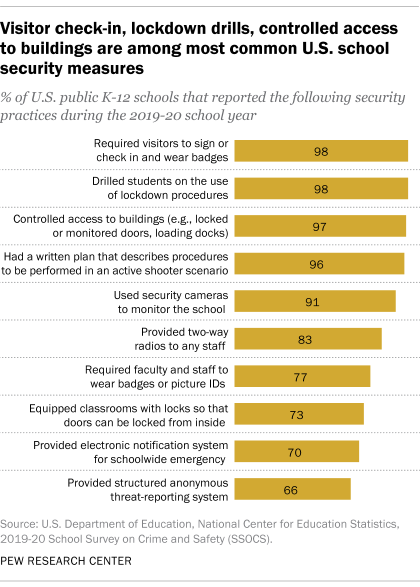
Restricting access to school buildings was pervasive across schools of all types. Nine-in-ten or more schools took this action, regardless of grade level, location, enrollment or student characteristics.
Classrooms are less likely to have locking doors in schools where greater shares of students come from households with lower incomes. One proxy measure of household income level is the share of students who qualify for free or reduced-price lunch. Among schools where at least three-quarters of students qualify for this program, 69% had locking doors in their classrooms in the 2019-20 school year, compared with 78% at schools where a quarter or fewer students qualify for free or reduced-price lunch.
Charter schools were 11 percentage points more likely than traditional public schools to have doors that lock from the inside in the 2019-20 school year (83% vs. 72%).
Active shooter response
Procedures to respond to threats are also prevalent across public schools. In 2019-20, 96% of all public K-12 schools had a written plan describing procedures to be performed in an active shooter situation, and 98% had conducted a lockdown drill with students that year. Lockdown procedures involve securing school buildings and grounds during incidents that pose an immediate threat of violence in or around the school.
The share of schools with written plans for an active shooter situation has increased from 79% in 2003-04, the earliest data available. (The NCES survey that year described active shooter scenarios as “shootings”; the 2019-20 data specifically referred to “active shooter” situations with “one or more individuals actively engaged in killing or attempting to kill people in a populated area.”)
Safety-related communications and technology
Many public schools used some form of security-related communication system or technology during the 2019-20 school year. The majority reported using security cameras to monitor the school (91%) or providing two-way radios to any staff (83%). Seven-in-ten schools provided an electronic notification system that automatically notifies parents in case of a school-wide emergency, and 66% provided a structured, anonymous threat-reporting system, such as an online submission form, telephone hotline or written submission form via drop box.
The share of schools with each of these communication systems and technologies has increased over the last decade. For example, the proportion of schools that have an anonymous threat-reporting system has nearly doubled since the 2009-10 school year, when 36% gave students this option. There has been a 30-point increase in the use of security cameras to monitor schools, up from 61% in 2009-10.
Though not as common as other measures, 40% of schools had “panic buttons” or silent alarms directly connected to law enforcement in 2019-20. That is an increase from 2015-16 (27%), the earliest data available.
There are some differences in adoption of these systems based on the school’s characteristics and the region of the country where it is located. In the 2019-20 school year, middle and high schools were more likely than elementary schools to have anonymous threat-reporting systems (77% of middle schools and 76% of high schools, vs. 59% of elementary schools) and security cameras (94% of middle schools and 97% of high schools, vs. 88% of elementary schools). Schools with greater shares of students who are racial and ethnic minorities were also more likely to use threat-reporting systems, and less likely to report using security cameras.
Panic buttons were more common in schools where relatively few students qualify for free or reduced-price lunch. For example, roughly half of schools (53%) where 25% of students or fewer qualify for free or reduced-price lunch programs used this technology, compared with around a third of schools (35%) where three-quarters of students or more qualified for the program.
Regionally, about three-quarters of schools in the West (76%) reported using security cameras in 2019-20, compared with more than nine-in-ten in the Northeast (93%), Midwest (95%) and South (98%). And around a quarter of schools in the West (27%) had installed panic buttons, compared with 43% each in the Midwest and South and about half of schools in the Northeast (49%).
Schools with higher enrollment are more likely than smaller ones to have each of the communications and technology measures asked about.
Security staff
About two-thirds of public K-12 schools (65%) had one or more security staff person present at the school at least once a week in 2019-20, up from 43% a decade earlier. In about half of schools (51%) in the 2019-20 school year, the security staff included at least one sworn law enforcement officer who routinely carried a firearm. In the 2009-10 school year, 28% of public schools reported having any security staff member who routinely carried a firearm.
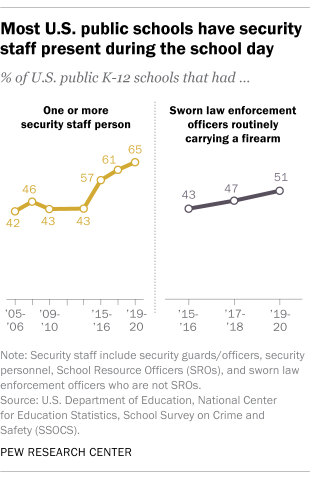
Security staff presence varies somewhat based on certain school characteristics. For instance, security staffers are more common at larger schools: 96% of schools with 1,000 or more students reported having one or more security staff person in 2019-20, compared with about half (48%) of schools with fewer than 300 students. More than eight-in-ten middle (82%) and high schools (84%) had security staff in the 2019-20 school year, compared with 55% of elementary schools.
There are similar patterns when it comes to whether the school’s security staff includes officers who carry firearms, but with a notable difference: Schools where more than three-quarters of the students are racial or ethnic minorities are the least likely to have an officer who carries a firearm (43% of these schools fall into that category, compared with 57% of schools where a quarter of students or fewer are minorities).
Threat assessment teams
During the 2019-20 school year, about two-thirds of schools (64%) reported having a threat assessment team in place. Threat assessment in this NCES survey was defined as “a formalized process of identifying, assessing and managing students who may pose a threat of targeted violence in schools.” A threat assessment team typically includes school staff such as administrators and school psychologists.
Again, certain types of schools were more likely to take this precaution. Schools in cities (67%) and suburbs (71%) more often had a threat assessment team than those in rural areas (56%). Threat assessment teams were also more common at the middle and high school level, at schools with higher enrollment numbers and at schools with a larger proportion of students who are racial or ethnic minorities.

Katherine Schaeffer is a research analyst at Pew Research Center .
A quarter of U.S. teachers say AI tools do more harm than good in K-12 education
Most americans think u.s. k-12 stem education isn’t above average, but test results paint a mixed picture, about 1 in 4 u.s. teachers say their school went into a gun-related lockdown in the last school year, about half of americans say public k-12 education is going in the wrong direction, what public k-12 teachers want americans to know about teaching, most popular.
1615 L St. NW, Suite 800 Washington, DC 20036 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
© 2024 Pew Research Center

An official website of the United States government, Department of Justice.
Here's how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
Making Schools Safe for Students

High-profile school shootings, like the one at Marjory Stoneman Douglas High School in Parkland, Florida, have raised concerns that schools can be dangerous places for students. Yet the data suggest that school crime rates have dropped nationwide since the early 1990s and that the student victimization rate declined by 70% from 1992 to 2013 ( see exhibit 1 ). [1]
To the general public, though, thoughts on school safety are often shaped by high-profile school shootings and other tragic incidents that dominate a news cycle. For educators, however, issues such as bullying, harassment, and school discipline policies are at the forefront of their thoughts and can affect school safety on a daily basis.
“It is very important that we continue working to understand and prevent mass shooter events,” said Phelan Wyrick, director of the Crime and Crime Prevention Research Division within NIJ’s Office of Research and Evaluation. “However, we cannot allow the saliency of mass shooter events to overshadow the importance of a wide range of more common safety issues that schools face.”
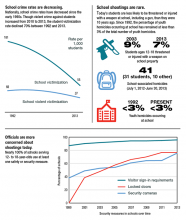
Shootings are just one of many traumatic events that children may face at school. They may also be threatened or injured by a weapon, be bullied, be physically assaulted, or be affected by natural disasters.
In support of stakeholder efforts to ensure that students are safe in school, NIJ has funded numerous initiatives over the years that evaluate school safety practices. These efforts range from how to prevent tragic incidents like school shootings to how to promote a positive school environment where day-to-day challenges, like bullying and harassment, can be reduced.
Historical School Safety Efforts
Although federal programs and policies related to school safety can be traced to the early 1970s, the United States did not begin collecting national data on school violence until 1989, [2] when the School Crime Supplement was added to the National Crime Victimization Survey. The School Crime Supplement was conducted for a second time in 1995 and then became a biannual survey starting in 1999.
A series of school shootings in the late 1990s, including the one that occurred at Columbine High School, led to new programs that examined the thinking, planning, and other pre-attack behaviors of school shooters. One such program was the Safe School Initiative led by the U.S. Department of Education and U.S. Secret Service.
As part of this initiative, NIJ supported a 2002 study that explored the behavior of student-attackers in an effort to identify information that could help communities prevent future attacks. [3] The study evaluated 37 incidents of targeted school violence in the United States between December 1974 and May 2000. It found that these 37 attacks were rarely sudden or impulsive. In 95% of the cases, the attacker had developed the idea to harm before the attack.
Perhaps most importantly, the study found that 93% of the evaluated attackers behaved in a way that caused others to be concerned or that indicated a need for help. In fact, in more than 75% of the cases examined, the attacker had told a friend, schoolmate, or sibling about the idea before taking action. But the person who was told about the attack rarely brought the information to an adult’s attention.
“That’s the critical element if we’re going to prevent, reduce, or head off these types of incidents from occurring,” Wyrick said. “We need to have mechanisms in place, school cultures amenable to folks reporting that information.”
The study also showed that there was no accurate profile of a school shooter. The shooters came from a variety of racial and ethnic backgrounds and ranged in age from 11 to 21 years old. Some came from intact families with ties to the community and others came from foster homes with histories of neglect. The academic performance of attackers ranged from excellent to failing.
Evaluating School Safety Technology
School security measures have increased since the Columbine shooting. Today, nearly 100% of schools serving 12- to 18-year-olds use at least one safety or security measure. [4] This includes locked doors, security cameras, hallway supervision, controlled building access, metal detectors, and locker checks. However, use of these measures varies by factors such as the school’s population and location.
NIJ has long supported studies on school safety technology, including one by Sandia National Laboratories. Released in 1999, The Appropriate and Effective Use of Security Technologies in U.S. Schools covered the effectiveness of a variety of school safety technologies. The report also provided basic guidelines for law enforcement agencies and school administrators as they decide which security technologies should be considered when developing safe school strategies. It helped schools and law enforcement partners analyze their vulnerability to violence, theft, and vandalism, and suggested possible technologies to address these problems effectively.
Overall, the report stated that security technologies are not the answer to all school security problems. No two schools will have identical and successful security programs, meaning that a security solution for one school cannot just be replicated at other schools with complete success. However, many pieces of technology can be excellent tools if applied appropriately.
More recently, NIJ has supported other school safety technology evaluations through the Comprehensive School Safety Initiative (CSSI). This initiative includes a report from the Library of Congress outlining federal school safety efforts between 1990 and 2016 and two complementary projects by the RAND Corporation and Johns Hopkins University, which assess current school technology and outline school needs.
These CSSI reviews of school safety technology shared a major conclusion: No one technology, school climate intervention, or other school safety strategy can guarantee school security or eliminate the underlying cause of school violence. An integrated approach that includes emergency response plans, drills, a positive school climate, and situational awareness is called for, and school security plans must be tailored to the needs of each individual school.
Comprehensive School Safety Initiative
Safety and security technology is just one tool in a comprehensive program that each school should develop to create a safe learning environment for students and staff. NIJ’s CSSI aims to make clear that there is no one solution to ensuring students are safe in school.
Developed following the tragedy at Sandy Hook Elementary School in 2012, CSSI is one of NIJ’s latest and largest investments in school safety research. Projects funded through CSSI examine different factors from the individual, school, community, and family levels that affect school safety.
A unique program of research for NIJ, CSSI provided funding for both implementation and evaluation as well as research projects that examine root causes. Under a directive from Congress, NIJ allocated approximately $75 million per year between fiscal years 2014 and 2017. Two-thirds of that funding went toward implementing school safety projects, and one-third went toward studying the impact of each program and the causes and consequences of school-related violence. Some CSSI projects have concluded and some are ongoing. They have covered or aim to address a wide range of school safety subjects, including school resource officer training, assessments of social media threats, bullying prevention, and positive behavioral interventions, among other topics.
This initiative will compile a large amount of information over a very short period of time, but the next few years will bring a wealth of knowledge on the effectiveness of school safety practices.
“We’re trying to move the field further and more quickly with so much information in such a short period of time,” said Mary Carlton, an NIJ social science analyst.
Through CSSI, NIJ has funded 96 studies with a focus on K-12 schools. These grant-funded projects are taking place in more than 30 states and more than 2,700 schools. The initial projects are still in the final stage, so it is too soon to assess the impact of the initiative. It may take six to seven years, if not longer, for the projects to reach their conclusions and for the results to be disseminated. Even after the last set of findings is published, taking that body of work and synthesizing it for the field may require another year or so of work, said Nadine Frederique, an NIJ senior social science analyst.
Moving Forward
School shootings are frightening and make headlines. However, today’s students are less likely to be threatened or injured with a weapon at school, including a gun, than they were 10 years ago.
But educators and public safety officials continue to grapple with the challenge of creating and maintaining a safe and healthy learning environment for students. Threats to schools and student safety continue from both inside and outside the school and from adults and other individuals, including students.
NIJ has sponsored numerous studies on the issues of school safety and school climate over the past 25 years and continues to support efforts to improve the safety of students in school. The outcomes of CSSI-funded research will provide valuable context for school officials in the coming years. The 96 projects funded through this effort examine a variety of school safety issues and offer an opportunity for educators, the community, and law enforcement to better understand the factors that most affect school safety.
About This Article
This article was published as part of NIJ Journal issue number 281 , released June 2019
[note 1] National Institute of Justice, “ School Safety: By the Numbers ,” Washington, DC: U.S. Department of Justice, National Institute of Justice, November 2017, NCJ 251173.
[note 2] Mary Poulin Carlton, Summary of School Safety Statistics , Comprehensive School Safety Initiative Report, Washington, DC: U.S. Department of Justice, National Institute of Justice, July 2017, NCJ 250610.
[note 3] Robert Fein et al., Threat Assessment in Schools: A Guide to Managing Threatening Situations and to Creating Safe School Climates , Washington, DC: U.S. Department of Education, Office of Elementary and Secondary Education, Safe and Drug-Free Schools Program, and U.S. Secret Service, National Threat Assessment Center, July 2004.
[note 4] Carlton, Summary of School Safety Statistics .
About the author
Blair Ames is a digital journalist and contractor with Leidos.
Cite this Article
Read more about:, related publications.
- Summary of School Safety Statistics
- NIJ Journal Issue No. 281
237 Cyber Security Essay Topics, Ideas, and Examples
🏆 best cybersecurity essay topics and examples, 💡 most interesting cybersecurity topics to write about, 👍 good essay topics on cybersecurity, ⭐ simple & easy cyber security essay topics, ✍️ cyber security topics for college, ⌨️ good cyber security essay examples and topics, 🖱️ compelling computer security research topics, ❓ cyber security paragraph questions.
- Ethical and Illegal Computer Hacking For the ethical hackers, they pursue hacking in order to identify the unexploited areas or determine weaknesses in systems in order to fix them.
- Computer Forensics Tools and Evidence Processing The purpose of this paper is to analyze available forensic tools, identify and explain the challenges of investigations, and explain the legal implication of the First and Fourth Amendments as they relate to evidence processing […]
- Importance of Army Cybersecurity This includes bringing awareness to the cybersecurity issue, involving more people to combat the problem of cyberattacks, and organizing the information based on specialty and tasks that must be completed.
- The Future Career in Cybersecurity During the interview, it is necessary to highlight the knowledge of working as a graph as a mathematical theory and the simple use of spanning trees in cybersecurity.
- Artificial Intelligence in Cybersecurity The use of AI is regulated by a large amount of documentation, which should take into account the current legislation in the country of use and ethical issues related to AI, many of which have […]
- Cybersecurity Workforce in Emergent Nations The lack of help from developed countries in the training and education of a cybersecurity workforce for developing nations can negatively affect the former. Public and private organizations also contribute to the development of cybersecurity […]
- Hacking: Positive and Negative Perception The possible advantage of cooperating with hackers for security systems mangers of international organizations and governmental organizations is the probability to recruit them and use their knowledge to empower different organizations to improve their security […]
- Cyber Security Issue: RansomWare Until the victim pays a specific amount of money to the attackers within a particular time, cybercriminals can use the virus mentioned above to access the user’s sensitive personal or organizational information. The infection and […]
- Sources of Digital Forensic Data With live system data, the aim of the investigator is to capture information concerning volatile data that may disappear when a device powers off or it is disconnected from the network.
- Benefits and Dangers of Ethical Hacking The advantages of ethical hacking The following are some of the advantages associated with the use of ethical hacking in an organization.
- Global Cybersecurity in the 21st Century Research Question: Is there a significant connection between the US President’s approach to cybersecurity and the actual presence of the given phenomenon?
- Public-Private Partnerships for Election Systems Cybersecurity In public contracts, the private sector provides the service directly to the public and bears all the associated end-user risks. Private parties can use all the gained knowledge and expertise to conduct security assessments of […]
- Cybersecurity and How It Impacts Identity Protection and/or Ransomware Firstly, organizational leadership should not undervalue the importance of cybersecurity since the risk of losing the data stored in the company’s database may harm the corporate reputation and trustworthiness.
- Sifers-Grayson Company: The Cybersecurity Breach Finally, the recommendations, as per the improvement of the incident response capability, are introduced to ensure the elimination of the identified drawbacks and the compliance of the engineering company with the security requirements presented by […]
- Hacking as a Crime and Related Theories The move to embrace the novel technology has led to the emergence of a new form of crime and behavior referred to as “hacking”. Today, the term is used to refer to individuals engaged in […]
- Computer Forensics: Identity Theft The forensics process that is maintained in the framework of computer-related technologies provides professionals with the opportunity to gather, analyze, and report on the information.
- Computer Forensics and Digital Evidence When electronic data has been collected to identify the kind of the incident and introduce evidence of the crime, it is important to organize a meeting with the witness who can provide details of the […]
- Assessment of Cybersecurity Program Maturity Padgett-Beale Financial Services must choose the appropriate framework and standards, determine required regulations and laws to comply with, and identify the best practices for maturity assessment to achieve an impenetrable cybersecurity management program.
- Banking Sector Cyber Wars and International Hacking Flaws in the network allow hackers to access the systems. In efforts to reduce hacking in the country, a number of police units have been formed.
- Technology Acceptance Model and Cybersecurity In this context, the implementation of TAM in the company is critical for the effective functioning of the organization. In this context, the introduction of TAM leads to the fact that satisfaction directly affects the […]
- Cybersecurity and Social Networks Recently, there have been many trends the security of information and communication technologies, in particular, due to the expansion of the reach of social media which increase the size of social network, which has taken […]
- The Impact of Mobile Devices on Cybersecurity The very popularity and extent of the use of mobile computing devices and the internet creates a special vulnerability to businesses.
- Information Security Fundamentals: Computer Forensics In addition, the paper provides an overview of the techniques used in obtaining evidence from the internet and web resources, the types of evidence that can be recovered from electronic and computer resources, and the […]
- The Department of Homeland Security’s Cybersecurity Mission Cybersecurity is evolving rapidly, and DHS’s cybersecurity mission is equipped with models adapting to the ever-changing security and information dynamics. The DHS cybersecurity mission is designed with models that adapt to changing dynamics and landscapes.
- Cybersecurity in the Financial Services Industry In reaction to ransomware attacks, a business such as a bank may have to spend a substantial amount of money, which may cause customers to lose faith in the safety of their funds.
- The Biggest Cybersecurity Treat to Expect First of all, all employees who somehow use the Internet of Things devices and have access to the corporate IoT network are to be trained to utilize it correctly.
- Securing Offboarded Employees: Modern Cybersecurity Strategies Disgruntled employees can be potentially dangerous to the whole company’s well-being due to cybercrimes that can affect the entire company’s work.
- Advanced Research Methods in Cybersecurity Performance measurements refer to the internal functions of the company and ways in which cybersecurity management contributes to the accomplishment of critical tasks within the firm.
- Gaps in Cyber Security Caused by BYOD In conclusion, these vulnerabilities caused by the insufficient regulation and general unpreparedness of organizational and public networks expose facilities that use BYOD to severe risks of data leaks and hacker attacks.
- Cybersecurity Threats in Physician Practice The purpose of the source is to inform readers of the strategies to help healthcare professionals identify, avoid and respond to ransomware dangers.
- Digital Forensic Analysis of Fitbit The comparison of the results and the analyses of the data as a result of the research gave the authors of the article a conclusion in regards to the methodology that has evidence-based results in […]
- Cybersecurity Contingency & Incident Review Process Next, it is necessary to implement various stages of digital transformation of cybersecurity, which include improving the maturity of enterprises in cybersecurity issues and the use of new solutions.
- Forensic Accounting and Cyber Security The recent trend of increased exposure due to the access of extended financial and fraud concerns by social media and the internet has necessitated the need to curb the tendency.
- Hacking Prevention: Mobile Phone Anti-Virus However, the less discussed and addressed subject is the cybersecurity of mobile phones, which are among the most used and vital devices for the majority of the population.
- Legal Risks of AI Cybersecurity in the European Union Thus, this paper seeks to fill the gap on whether or not safety and security can be covered in cybersecurity for AI by the same rules that are used in private law. The EU has […]
- Cyber Security: Critical Infrastructure Protection Objects of forensic science are storage mediums that are not part of other devices and which fulfill the function of information storage as the main one.
- Relation Between Cybersecurity and Cybercrime Meanwhile, one should not assume that cybersecurity is the prerogative of technicians and software engineers only since the consequences of a breach will affect the entire business or private life of those not associated with […]
- Cybersecurity in 2021-2022: Cybersecurity Advancements In IoT, Blockchain is being utilized to protect connected devices through decentralization and encryption, adding to the evolving nature of system security.
- Encryption and Hacking Techniques There are several advantages of text-based encryption, and they include the fact that the data can be used across different devices through the concept of multi-device encryption techniques.
- The US, Russia, and China Cybersecurity Conflict The current situation in the space of cybersecurity provides a significant example of how complicated this area of National Security and its influence on foreign politics can be.
- Cybersecurity and Geopolitics Relationship Provision of security to information technology and the tools used in the technology is also paramount. Cyber security is also described as measures and operations that are put in place to be to ensure that […]
- Cybersecurity and Corporations’ Input to It Whatever committee or board of directors is in charge of overseeing cybersecurity risks, the primary goal is for an organization to have an integrated approach to preparing for and protecting against cyber incidents and detecting […]
- Cybersecurity and Corporations’ Role First, it is worth indicating some of the key reasons for corporations to be in the center of cybersecurity discussion. In April, the company rejected the possibility of a data breach and apparently did not […]
- Cybersecurity and Geopolitical Issues Geopolitics is the study of integration and effect of earth geography and physical outlay on the political structures, and international relations and reforms that affect the same at different levels.
- Virtual Reality and Cybersecurity As a result, it is the mandate of the framework entities to establish solutions to the inherent barriers to the implementation of the business plan.
- Cybersecurity Policy Regarding Critical Infrastructures The article will explicitly analyze the processes behind cybersecurity development as well as the impact of the cybersecurity polies to the global security policies.
- Cybersecurity: Critical Infrastructure Control Systems The most vital stages of this nature include the analysis of the situation, the assessment of goals to make sure that they are realistic, and the expected effectiveness of implementing new policies.
- Cybersecurity in the United States Thus, the current research project is going to address the following question: Is there a significant connection between the US President’s approach to cybersecurity and the actual presence of the given phenomenon?
- Cybersecurity: The Matter of National Security However, if the security of cyberspace is critically evaluated and all the risks eliminated, cyberspace can be an asset that will continue to transform the world.
- Cybersecurity Advancements in Electric Power Systems Therefore, there will be an increase in the volume of work performed, a reduction in design time and an increase in the quality of work through the use of technology in the next five years.
- Cybersecurity Dangers and Their Analysis The officer clicks the file, and the malware attacks the system stealing the data and bypassing some security measures. The cyber security framework under the NIST is helping organizations to understand and manage cybersecurity.
- The US and Apple Relationship in the Field of Cybersecurity In this paragraph, an important aspect is to determine the degree of interaction between the two structures. This paper argues that in times of crisis, such powers should be surrendered to the more considerable public […]
- Data Management and Cybersecurity Namely, the principal standard of the HIPAA, as well as the concept of cybersecurity, have proven to factor into some of the key aspects of my professional and personal life.
- Cybercrime and Cybersecurity as Challenges One will also learn the defensive cyber security technologies and techniques used in modern organizations to protect systems data and achieve Knowledge of the maintenance and design of reliable and safe information systems.
- Digital Forensics Tools and Software One of the most famous software programs for digital forensics is Autopsy, a toolkit that examines the images present on a device’s hard drive.
- Tim Cook’s Leadership and Apple’s Cybersecurity In this paper, the main types of leadership that can be applied to the leadership style of Tim Cook are considered.
- Cybersecurity Weaknesses: The Case of LinkedIn The Internet has become the largest storage of personal and corporate information in the history of the world. The data relating to hundreds of millions of users was leaked online in the Dark Web segment […]
- The Importance of Leadership Skills in the Field of Cybersecurity The wider the information networks cover the world, the more frequent and dangerous cyber-attacks are, and the more cybersecurity specialists become in demand.
- White Hat and Black Hat Hacking On the other hand, White Hats work with companies and help them identify weaknesses in their systems and fix relevant vulnerabilities to ensure that attackers cannot illegally gain access to data.
- Modern Cybercrime: Most Recent Threats and Cybersecurity This is due to the fact that the Internet is a public open system in which data moves uncontrollably and can be discovered, intercepted, or stolen if the correct knowledge of the equipment is applied.
- Cybersecurity Strategy, Law, and Policy Team Assignment It may be critical to prevent cybersecurity breaches or data leaks to maintain the effective functioning of the government and ensure the sovereignty of the country.
- The Cybersecurity Threat Landscape The threats may come from different sources, and the criminals may focus on distinct vulnerabilities in the security of the system.
- Solving the Cybersecurity Workforce Crisis Since cyber security specialists are highly demanded in the current market, the private sector has been offering increased compensation in comparison with the government sector, which has led to decreased interest in IT positions in […]
- Cryptographic Algorithms: The Use in Cyber Security Cryptographic protection of a system depends on two factors, 1) the strength of the keys and effectiveness of associated protocols, and 2) protection of said keys via key management.
- Cybersecurity Implementation Plan for PBI-FS Therefore, the current plan will define the objectives, goals, and objectives, and scope of the implementation. The implementation of the cybersecurity management plan pursues both business and project goals and objectives.
- Facebook Compatibility With Padgett-Beale Cybersecurity Philosophy The purpose of this paper is to evaluate Facebook on the subject of cybersecurity and compatibility with Padgett-Beale’s cybersecurity philosophy and goals.
- Cybersecurity Issues in Industrial Critical Infrastructure This way, the author analyzes the potential impact of various cybersecurity threats capable of interrupting the stability of the supply of energy to communities and industries.
- Supply Chain’s Cybersecurity and Risk Analysis Since there are so many parties involved, it is crucial to assess every part of the process, from obtaining the raw material to the delivery to the customer. Cybersecurity is the critical answer to most […]
- Amazon Inc.’s Business Profile and Cybersecurity On the contrary, Amazon has continued to rise in the industry and has expanded from selling only books to trade in nearly any product and providing various services.
- Integrating Cybersecurity Framework With Information Technology Governance Frameworks ISMS builds a model of relationships between the aforementioned activities, and, as Almuhammadi and Alsaleh argue, companies “understand their cyber security risk management approach and what are the processes in place to manage the risk”.
- Cybersecurity, Ethics, and Privacy in the Global Business Environment Therefore, the purpose of this paper is to cover the types of possible threats and mitigation methods, explain the importance of a continuity plan, and outline ethical and privacy concerns for organizations.
- Cybersecurity: Multi-State Information Sharing and Analysis Center The MS-ISAC also advises the agencies on the best tools available in the market that provide the best protection of the government systems and data.
- Cybersecurity Strategy and Plan of Action Padgett-Beale’s primary intention of merging the company was to relocate the call epicenter to a property owned by the company roughly 10 miles from the company’s previous location and opposite the newly released Padgett-Beale resort.
- Digital Forensic Examination, DVR Another application would be to determine the network’s or a user’s IP and track their online activity. The information can be used to determine an unknown individual’s location and possibly identity, or for a known […]
- Cybersecurity in the Energy Sector The stable supply of energy is the key to the normal functioning of American society, as it fuels all essential industries that ensure the vitality of the nation.
- Cybersecurity for Open Data Initiatives Governments continue to play a vital role in the open data movement.Data.gov was developed under OPEN Government Data Act; this is Title II of Foundations for the Evidence-based Policymaking Act.
- Computer Forensic Incident All evidence should be collected in the presence of experts in order to avoid losing data as well as violating privacy rights.N.
- Cybersecurity Threats to Educational Institutions The rapid adoption of digital solutions is exposing schools to the cyber-security threat, which is currently the biggest concern that these institutions face as they make a complete shift from the analog to the digital […]
- Cybersecurity Necessity and Benefits Second, the exploration of human factors in the framework of cyber-security can assist in resolving the issues of understanding a defender’s cognitive state, possibilities for automation, and an attacker’s subjective traits.
- Cybersecurity Incident Response and Risk Minimization Such plan or strategy represents a list of steps, which should be immediately taken in case of a cyber-attack to limit the potential damage and reduce expenses.
- Internet Hacking and Cybersecurity Conundrum Analysis Many people have gained access to computer systems, the Internet, and related products and services, leading to the emergence of cyber-related threats. Cybersecurity improvements are vital to the continuous developments in information technology, national security, […]
- Internet Hacking and Cybersecurity Conundrum Therefore, the increasing number of attacks during the pandemic could be handled with the help of machine learning and have the numerous human workers assigned to less crucial tasks that actually require human judgment.
- Government and Private Sector in Cybersecurity Richards highlights the government’s leading role in the context of cyber threats while stating that the number of attacks is still on the increase.
- Ethical Hacking: Is It a Thing? Computer programmers implemented the term ‘hacker’ at the beginning of the 1960s in the framework of a positive definition for an individual of dexterous software development skill.
- Computer Network Security Legal Framework With the introduction of cloud computing, the need of data protection has been rising significantly within computer networks to facilitate the protection of Intellectual Property among the users.
- Computer Forensics and Audio Data Retrieval Advanced technology in the modern society has contributed to the increase in computer and computer supported criminal activities due to the soaring increases in the number of internet users across the world and computerization of […]
- Cyber Security: Security Audit On the issue of computers and laptops, I learned from the administration that each laptop was specifically assigned to a single person who was entrusted with a password known to him and the organization’s administration […]
- Computer Forensics: Data Acquisition Data acquisition is a branch of computer forensics concerned with the retrieval of data originally located on a suspect medium such as a hard drive.
- Computer Forensic Timeline Visualization Tool The necessity to save time in computer forensic investigations is the basis of the tool that Olssen and Boldt came up with.
- The Qatar Independence Schools’ Computer Network Security Control The result of the interviews mainly outlined several common themes and patterns in terms of the design of the proposed security system.
- Computer Sciences Technology and HTTPS Hacking Protection Many are assured when they see the SSL symbol of a lock at the bottom of the screen and feel their information is confidential and the website is protected.
- Moral Issues Surrounding the Hacking of Emails The devises to enter into another people’s email and steal information in the email is called Email Hacking. It should noted that stealing of valuable information through email hacking has become a phenomenon in both […]
- Hacking Government Website From the View of Right and Justice Computer crimes refers to the use of the computer system or the internet to commit criminal activities A computer crime is an unlawful act done via a computer or a network and some of the […]
- COBIT5 vs. ITIL4 in Cybersecurity Significantly, ITSM is the alignment of information systems and enterprise IT services with business and the needs of the customer who is the end-user.
- Cybercrime and Cybersecurity: Data Protection One of the biggest Constitutional concerns for electronic surveillance as well as search and seize of evidence is protected by the Fourth Amendment which limits any such activities against the private persons, property, or effects […]
- Cyber Security Threat and Its Impact on the UAE In 2018, the UAE government and private sector were the subject of a total of 230 cyber attacks, as The National UAE reports.
- Agility and Situational Awareness in the Context of Cyber Security As a result, measures should be implemented to create cyber security, which will protect the information resources of an organization from damage.
- Research Tools Used by Computer Forensic Teams Computer Forensics is a branch of digital forensics which is used in “identifying, preserving, recovering, analyzing and presenting facts and opinions about the information”.
- Business and Cybersecurity Research Thus, a more sophisticated theoretical approach is taken to represent the goals of cyber security. A mediating variable, in turn, is the effectiveness of cyber security measures perceived from theory- and practice-related standpoints.
- Quality Control of Digital Forensics The quality control over computer forensic products is necessary because of the growth of the Internet services. Thus, the investigator and the lab are challenged not only with solving a case but also providing the […]
- Windows Logs: Improving Cybersecurity The specified event points to the need to configure the current settings of the master browser in order to address possible security issues and close the loopholes that potentially make the computer vulnerable to malware.
- Cybersecurity: Weak and Strong Passwords The strong passwords have a low probability of being guessed because the amount of possible iterations and combinations is extremely high.
- “Evolution of Federal Cyber Security” by J. Roth Even after training, the GAO report continued to demonstrate system control deficiencies due to failures in the identification of enough boundary security mechanisms, breakdown in the need to know, insufficient restriction of physical access, and […]
- The Different Sides of Hacking In a general sense, computer hacking involves the intrusion of the computing privacy of other people, damage of the computing property of other people like files, software etc.or the theft of private information by unauthorized […]
- US Brokerage Hacking by India Issue The personal accounts of the defendants were used to purchase shares of stocks, following which they hacked into other people’s accounts and made good use of their passwords and usernames.
- Cyber Security in the Energy Sector The organization’s innovation can be catalytic for the change in the industry of energy since the largest sources of carbon emissions are power plants that generate energy by burning fossil fuels.
- Computer Forensics in Criminal Investigation In this section, this paper will address the components of a computer to photograph during forensic photography, the most emergent action an investigating officer should take upon arriving at a cyber-crime scene, the value of […]
- Computer Forensics and Cyber Crime Due to age characteristics, the insufficient educational activity of parents, the provision of unlimited opportunities in the online environment, and also due to the low media literacy of the population, people can become victims of […]
- Cyber Security: Shadow Brokers Hacker Group A concealed group of hackers stole several disks containing secret data belonging to the National Security Agency in 2013; In 2016, they announced an auction to sell off the data they had obtained illegally; […]
- Cybersecurity and Encryption Analysis: VPN, PKI & Firewalls The end-to-end encryption is the more complex process that can be discussed as the data encryption between the client application and the server provided with the help of additional technologies.
- Cybersecurity as a Leadership Challenge Cybercrime can lead to the leakage of important data, system interference, and the delivery of unsatisfactory services to consumers. This sophistication has amplified the insecurity of information systems to the extent of creating more threats […]
- Shadow Brokers Hacker Group and Cyber Security Industry Therefore, in order to prevent the recurrence of such attacks, the N.S.A.needs to strengthen the security system of particularly essential information to eliminate its diversion.
- Deutsche Telecom Company’s Cyber Security The present work deals with the issue of DDoS attacks and builds a case on one of the well-known IT companies to single out the problem, the immediate solutions and preventive practices, and the lessons […]
- Cybersecurity: Deutsche Telekom Company’s Case The example of Deutsche Telekom proves the importance of the development of cybersecurity programs and strategies to protect users and their interests.
- Cybersecurity Risks Affecting Enterprises From a national security standpoint, it is crucial to know and understand the nature of the enemy and be prepared for an increase in cyberterrorism attempts.
- Cyber Security and Employees The major factors that define the thriving of cyber ganging are the insufficient level of employees’ competence, the lack of knowledge about the technical side of information protection, and non-compliance with safety standards.
- Cybersecurity Directives and Laws Describe the National Strategy for the Physical Protection of Critical Infrastructures and Key Assets and how it attempts to protect cyber assets.
- Cybersecurity and Vital Elements The focus of any risk management effort is a standard system or a framework that help organizations and individuals to manage integrity, confidentiality, and data and ensure critical resources availability.
- Emerging Cyber Security Approaches and Technologies These emerging cyber security approaches and technologies are unique and new, and they look promising for securing critical infrastructures in the cyberspace.
- Cybersecurity Dilemmas: Technology, Policy and Incentives The value of the assets determines the amount of time and resources that can be invested to protect a particular system.
- Hacking: White, Black and Gray Hats Living in the era of the Internet and online technology increases the vulnerability of the information stored online and on electronic devices.
- A Duty of Care for Cyber Security Hence, the sensitive data can be easily accessed by cyber criminals in the event that the cloud service is breached by users.
- Digital Forensics: Open Source Tools The National Software Reference Library is a project at the National Institute of Standards and Technology, the primary goals of which are to store all existing software, file profiles, and file signatures and to provide […]
- Digital Forensic Methodology In the event that sufficient information is available, the required system configuration should be developed by ensuring that the forensic software and hardware are established and validated.
- Automotive Industry’s Cybersecurity and Threats It is significant to ensure the security of this system because it focuses not only on the audio and video entertainment but also allows to control navigation system and manipulate the behavior of the car.
- Cybersecurity and Risk Control Implementation The first component of the risk treatment framework refers to the decision not to go through with the procedures that may present a risk; the second one stands for the minimization of the possibility of […]
- Online Predators and Childrens’ Cybersecurity To win the battle against online predators it is important to craft laws that were created by people with a thorough understanding of how perpetrators utilize information systems and the Internet to commit sexually-related cyber […]
- Computer and Digital Forensics and Cybercrimes This has greatly affected the success of computer forensics and it is the main drawback in this area. The world is now safer due to the increasing usage of computer forensics in court cases.
- The Role of U.S. Government in Cybersecurity According to the government of the United States, cybersecurity is among the most serious economic and security challenges that the government needs to deal with.
- Cyber Security’s and Counter Terrorism’ Intersection Realization of national interests is the concern of many states in the current international and security is the main challenge that each government is trying to cope up with given the fact terrorists are ever […]
- Cybercrime, Digital Evidence, Computer Forensics The website “howstuffworks” carries an article discussing the basics of computer forensics, this is a good example of a website that is useful in explaining or understanding the reality of cybercrime and digital evidence. Not […]
- Middle East Cybersecurity, E-Government, Ecommerce The findings in the research revealed that five main issues led to the reluctance in the adoption of e-commerce and e-governance by the Emirates.
- Sony Corporation Hacking and Security System The organization had to stop the hackers and ensure information did not flow freely but it was unfortunate, as the company sought the services of the California court because it had no capacity to deal […]
- Growth Hacking and Marketing Methods As a result, it could be observed that the combination of the growth hacking methods and the permission-based marketing appear to be one of the most efficient techniques towards marketing that is low-cost and effective.
- Cybersecurity: Stuxnet Virus Cyber security is one of the major concerns of governments in the contemporary world. It is important to note that in case of Stuxnet the three aspects prove to be vulnerable.
- Ways to Stop Cell Phones Hacking Although it is in the view of many that their phones cannot be hacked as they only protect their computers from hacking, mobile phone operators are more predisposed to being hacked since a mobile operator […]
- The Threats of Cyber Security Under the PPD-21, the owners of the critical infrastructure will work with the government to hasten the process of strengthening the national critical infrastructure in terms of the much needed security.
- Two Greatest Hacking Systems in the USA Appropriating intellectual output of someone else is also a computer malpractice that is intolerable. Generally, Computer malpractice is seen when a person shows hasty and careless conducts or behaviors when making use of computer systems.
- Cybercrime: Gary McKinnon’s Hacking Event It is the lack of effective controls that accounts for most hacking incidences, as depicted by the case of Gary McKinnon who was able to gain unauthorized access to NASA and pentagon systems, deleting crucial […]
- Important Problem of Cybersecurity Simulations The information stored in the company’s database was encrypted to create confidence in the customers on the security of the data.
- Cyber Security Technologies The technology is regularly designed to alter the attack surface of a network, making it hard for attackers to access a system and reducing the susceptibilities and predictabilities available at any time.
- Analysis of Mandiant Cyber Security Company The company’s innovation theories and products need to accommodate other companies that do not view cyber crime as a major risk on their systems.
- Leadership: Mandiant Cyber Security Company Kevin Mandia is the founder and the CEO of the company. The achievements behind Mandiant Cyber Security Company owe its success to the leadership styles exhibited in the firm.
- Adrian Lamo’s Hacking: Is It Right? The example of Galileo introduces a theory about the construction of the Solar System that was the target of interest of the well-known scientist.
- Cyber Security Threat Posed by a Terrorist Group These among other features of the internet have been identified to form the basis of the cyber terrorism attacks. A comprehensive international collaboration among investigators and prosecution teams in cases of cyber attacks have also […]
- Computer Forensics Related Ethics Due to advancement in technology, individual information can be kept in databases, the risk of accessing this data is evident and this necessity the need of such a law so as to ensure security.
- The Cyber Security Act of 2009 Analysis This would contribute to enormous benefits to both the government and private stakeholders by ensuring a cyber security strategy that serves the interests of all.
- Air Force and Cyber Security Policies The use of technology in processing financial transactions implies that there is need to boost the trustworthiness, security, resilience, and reliability.
- The Role of Computer Forensics in Criminology In fact, since the development of the virtual machine monitors, the live-state analysis in digital forensics has become common and easy to understand.
- Ethical Hacking: Bad in a Good Way Introduction of personal computers led to the increase in the number of hackers as well as hacker targets were widened. Many hackers lack the skills to damage network systems in a major way.
- Hacking: Social Engineering Online The information is fed to the main web site that’s runs the hacking software, where the information is sorted according to various numbers.
- Cyber Security in Private and Public Sectors The US has the Health Insurance Portability and Accountability Act that ensures that patients’ data remain accessible only to the authorized segment of the staff.
- Cyber Crime and Necessity of Cyber Security This is one of the policies that has been proposed to curb cyber crimes and is being debated in the congress.
- Cybersecurity in the Energy Industry In this regard, in the event that a cyber attack is launched against the energy sector, it is bound to have far reaching consequences.
- Ethics in Computer Hacking Hacking by no means follows ethics; the infiltration is to the benefit of hacker and loss of users of computer system, network or website.
- Computer Forensics and Investigations It is crucial in the investigation of crimes that are related to the manipulation of computer systems. For digital evidence to be admissible in court, investigations should be conducted in a manner that adopts the […]
- Preparing a Computer Forensics Investigation Plan However, if the information is thought to be contained in the permanent storage, then a computer has to be shut down before transporting it to a laboratory for forensic analysis. The first step in the […]
- Basic Operations of Computer Forensic Laboratories All computer forensic laboratories in the US have to adhere to the national standards before they could be certified. Standard computer forensic equipment is used to support standard procedures and conditions in the laboratories.
- Kosovo 1999: Hacking the Military The paper addresses the motivation behind the attacks, the methods of attack, and the responses of the defenders to these attacks.
- Introducing Cybersecurity Policies: Challenges and Solutions The major purpose for establishing security guidelines is to set an organization’s data security standard and describe the role of employees in safeguarding the documents of the firm, as well as the significance of a […]
- Société Générale Bank: Effective Security Controls The management of the bank revealed that Kerviel exploited every loophole to hack the computer operations at the bank. It is also important to list the potential risks because it enables the security personnel to […]
- Computer Security Breaches and Hacking To avoid such an attack in the future, it is advisable to keep both the client and server applications up to date.
- Analysis of BJG Cybersecurity Consultants
- Analysis of Cybersecurity and Risk Management
- Analysis of Cybersecurity Metrics as Well a Governmental
- Analyzing the Impact of Mobile Devices on Cybersecurity
- Assessing the Impact of Cybersecurity Attacks on Power Systems
- Building Cybersecurity Awareness: What Should Both Companies and Consumers Do to Protect Themselves?
- Current Practice Analysis for IT Control and Security
- Why Cybersecurity Is Important?
- Cybersecurity in Banking Financial Services Secto
- Cybersecurity in the European Union: Resilience and Adaptability in Governance Policy
- Cyber Security : Is No Silver Bullet For Cybersecurity?
- Dealing With Cybersecurity Threats Posed by Globalized Information Technology Suppliers
- Emerging Technologies That Impact the Cybersecurity Field
- Hacker’s Culture and Cultural Aspects of Cybersecurity
- How Cybersecurity Is an Aspect of Security?
- How Cybersecurity Is Important Resources?
- How Policies, Laws and Regulations Affect the Cybersecurity Field?
- Is Cybersecurity a Big Deal?
- Risk Assessment Uncertainties in Cybersecurity Investments
- What Is Cybersecurity?
- When Cybersecurity Policy Is Discussed the Topics Often?
- Why Computer Scientists Should Care About Cybersecurity?
- Access Single Most Important Cybersecurity Vulnerability Facing IT Mangers
- Model for the Impact of Cybersecurity Infrastructure on Economic Development in Emerging Economies: Evaluating the Contrasting Cases of India and Pakistan
- Cybersecurity and Its Importance in the Modern World
- Architecture for Managing Knowledge on Cybersecurity in Sub-Saharan Africa
- Benefits of Using Cybersecurity
- Border and Cybersecurity in the United States
- Botching Human Factors in Cybersecurity in Business Organizations
- Companies Responsibilities in Enhancing Cybersecurity Chapter
- Cybersecurity and Law Enforcement
- Cybersecurity and Organizational Change Concept Map
- Cybersecurity at European Level: The Role of Information Availability
- Cybersecurity for Critical Infrastructure Protection
- Cybersecurity for Digital Financial Service
- Cybersecurity Policy Making at a Turning Point: Analysing a New Generation of National
- Effect of Bring Your Own Device (BYOD) on Cybersecurity
- Human Aspects in Cybersecurity on a Government Agency and a Private Organization
- Improvement of Cybersecurity Is Necessary
- Most Important Cybersecurity Vulnerability Facing It Managers Computer Knowledge
- Obama Administration’s Policy Views on Cybersecurity
- Review of Cybersecurity Risks of Medical Device Software
- Small Business Cybersecurity and the Public Cloud
- The Influence of Cybersecurity Define the Hacker Motives
- Effect of Cybersecurity on Higher Education
- Importance of Cybersecurity for The Future
- Role of Cybersecurity and Its Effects on the World
- Why Should Computer Scientists Care About Cybersecurity?
- What Are the Roles and Responsibilities of an Organization in Considering Cybersecurity?
- What Are Three Models for Sharing Cybersecurity Incident Information?
- What Are the Private Sector and Public Sector Cybersecurity Issues?
- How Do Policies, Laws, and Regulations Affect the Cybersecurity Field?
- How to Improving Password Cybersecurity Through Inexpensive and Minimally Invasive Means?
- What Kind Are International Cybersecurity Collaboration Initiatives and Multinational Cybersecurity?
- What Is the Most Important Cybersecurity Vulnerability Facing Managers in Computer Science?
- What Are New Concepts for Cybersecurity in Port Communication Networks?
- What Does Cyber Security Do?
- Is Cyber Security a Promising Career?
- What Are the Three Major Threats to Cyber Security Today?
- What Qualifications Do You Need for Cybersecurity?
- What Is a Cyber Security Example?
- What Are the Main Problems With Cyber Security?
- What Is the Biggest Threat to Cyber Security?
- What Are Cyber Security Tools?
- What Is the Risk in Cyber Security?
- What Is the Best Cyber Security?
- What Is Wireshark in Cyber Security?
- Which Are Fundamentals of Petroleum Energy & Mitigating Global Cybersecurity Attacks?
- Which International Cybersecurity Collaboration Initiatives and Multinational Cybersecurity?
- Which Vulnerability Assessments and Mitigating Global Cybersecurity Attacks on the Enterprise?
- Who Is the Founder of Cyber Security?
- What Are the Seven Types of Cyber Security?
- What Is the Most Significant Cybersecurity Company?
- Cryptocurrency Essay Ideas
- Identity Theft Essay Ideas
- Viruses Research Topics
- Cryptography Paper Topics
- Encryption Essay Titles
- Internet Privacy Essay Topics
- Digital Transformation Topics
- Software Engineering Topics
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, February 27). 237 Cyber Security Essay Topics, Ideas, and Examples. https://ivypanda.com/essays/topic/cybersecurity-essay-topics/
"237 Cyber Security Essay Topics, Ideas, and Examples." IvyPanda , 27 Feb. 2024, ivypanda.com/essays/topic/cybersecurity-essay-topics/.
IvyPanda . (2024) '237 Cyber Security Essay Topics, Ideas, and Examples'. 27 February.
IvyPanda . 2024. "237 Cyber Security Essay Topics, Ideas, and Examples." February 27, 2024. https://ivypanda.com/essays/topic/cybersecurity-essay-topics/.
1. IvyPanda . "237 Cyber Security Essay Topics, Ideas, and Examples." February 27, 2024. https://ivypanda.com/essays/topic/cybersecurity-essay-topics/.
Bibliography
IvyPanda . "237 Cyber Security Essay Topics, Ideas, and Examples." February 27, 2024. https://ivypanda.com/essays/topic/cybersecurity-essay-topics/.

Empowering Protection in the Digital Age
The Importance of Cyber Security in Today’s World
- By: Samuel Norris
- Time to read: 24 min.

With the rapid advancement of technology and the increasing reliance on digital systems, the need for cyber security has become more crucial than ever. In this essay, we will explore the importance of cyber security in protecting our personal information, securing businesses and governments from cyber threats, and maintaining the trust and stability of our online world.
The importance of cyber security in protecting personal information

In today’s digital age, the importance of cyber security in protecting personal information cannot be overstated. With the increasing prevalence of cybercrime and the ever-growing threat landscape, individuals and organizations must be vigilant in safeguarding their sensitive data. Cyber security measures are crucial not only to protect personal information from unauthorized access but also to maintain the integrity and confidentiality of data.
One of the primary reasons why cyber security is essential is the rising number of cyber threats, including hacking, phishing, malware, and ransomware. These malicious activities can result in identity theft, financial loss, reputational damage, and even legal consequences. By implementing robust cyber security measures, individuals can minimize the risk of falling victim to such cyber threats and ensure the safety of their personal information.
Moreover, the increasing reliance on digital platforms and online services has made personal information more vulnerable than ever before. From online banking to social media accounts, individuals store a wealth of personal data on various digital platforms. Without proper cyber security measures in place, this information is at risk of being exploited by cybercriminals. Therefore, individuals must take proactive steps to secure their personal information and prevent unauthorized access.
Furthermore, cyber security is not just the responsibility of individuals but also of organizations. Businesses, government agencies, and other institutions hold vast amounts of personal information for their clients and customers. Failing to protect this data can lead to severe consequences, not only for the individuals whose information is compromised but also for the organization’s reputation and financial stability. By investing in robust cyber security measures, organizations can demonstrate their commitment to protecting personal information and build trust with their stakeholders.
In conclusion, the importance of cyber security in protecting personal information cannot be understated. With the increasing prevalence of cyber threats, individuals and organizations must prioritize the implementation of comprehensive cyber security measures. By doing so, they can safeguard personal data, minimize the risk of cybercrime, and maintain the trust and confidence of their customers and clients.
Cyber attacks and their impact on businesses and economies

Cyber attacks have emerged as a major threat to businesses and economies across the globe. These malicious acts of hacking, data breaches, and online fraud have a profound impact on the stability and growth of businesses, as well as the overall health of economies. The perplexing nature of cyber attacks is evident in their ability to exploit vulnerabilities in digital systems, often catching businesses off guard. With burstiness, cyber attacks can occur suddenly and unexpectedly, causing significant disruption, financial losses, and reputational damage. Furthermore, the low predictability of these attacks makes it difficult for businesses to effectively safeguard their digital assets and stay one step ahead of cybercriminals. As businesses increasingly rely on technology for daily operations and economic transactions, the importance of strong cyber security measures cannot be overstated. Implementing robust security protocols, such as firewalls, encryption, and multi-factor authentication, is crucial for businesses to mitigate the risks posed by cyber attacks. Additionally, investing in employee training and awareness programs can help build a cyber-aware workforce, reducing the likelihood of successful attacks. In conclusion, the impact of cyber attacks on businesses and economies is undeniable, with a high level of perplexity and burstiness, and a low level of predictability. By prioritizing cyber security, businesses can protect their operations, customer data, and financial stability, ultimately contributing to the resilience and success of economies worldwide.
The role of cyber security in safeguarding national security

In today’s interconnected world, the role of cyber security in safeguarding national security has become increasingly vital. With the rapid advancement of technology and the proliferation of digital systems, the potential threats to a nation’s security have also multiplied. Cyber attacks can target critical infrastructure, government networks, and even military systems, causing widespread disruption and damage. Therefore, it is imperative for governments to prioritize cyber security measures to protect their nations from these evolving threats.
Cyber security plays a crucial role in safeguarding national security by preventing unauthorized access to sensitive information and networks. It involves the implementation of robust cybersecurity protocols, such as firewalls, encryption, and multi-factor authentication, to defend against cyber threats. By securing networks and systems, governments can ensure the confidentiality, integrity, and availability of critical data, thereby safeguarding national secrets, defense strategies, and citizen information.
Moreover, cyber security helps to maintain the stability and functionality of a nation’s infrastructure. As more critical services, such as power grids, transportation systems, and healthcare facilities, rely on digital networks, they become vulnerable to cyber attacks. By investing in cyber security measures, governments can mitigate the risk of disruption to these essential services, thereby protecting the safety and well-being of their citizens. Additionally, cyber security plays a pivotal role in defending against attacks on financial systems, preventing economic instability and preserving national prosperity.
Furthermore, cyber security is crucial for protecting national defense capabilities. Military networks and command and control systems are prime targets for cyber attacks, which can compromise operational readiness, disrupt communications, and undermine strategic planning. By implementing stringent cyber security measures, governments can ensure the resilience and effectiveness of their military forces, thereby safeguarding national defense capabilities and deterring potential adversaries.
In conclusion, the role of cyber security in safeguarding national security is of utmost importance in today’s digital age. By prioritizing and investing in robust cyber security measures, governments can protect critical infrastructure, defend against cyber attacks, and ensure the confidentiality and integrity of sensitive data. As the threat landscape continues to evolve, it is imperative for nations to stay ahead by continuously enhancing their cyber security capabilities and collaborating with international partners to combat cyber threats.

Click here to preview your posts with PRO themes ››
The evolving threat landscape and the need for stronger cyber security measures

In today’s rapidly evolving digital landscape, the threat of cyber attacks looms larger than ever before. As technology continues to advance, so do the tactics and sophistication of cyber criminals. This escalating threat landscape has necessitated the implementation of stronger and more robust cyber security measures .
Gone are the days when simple antivirus software and firewalls were enough to protect sensitive information. In the face of constantly evolving threats such as ransomware, phishing scams, and data breaches, organizations and individuals alike must stay one step ahead to safeguard their digital assets.
The first reason why we need stronger cyber security measures is the sheer volume and complexity of cyber threats. Cyber criminals are constantly devising new ways to exploit vulnerabilities in software, networks, and even human behavior. From malware that can invade our devices without detection to social engineering techniques that manipulate individuals into revealing sensitive information, the tactics used by cyber criminals are becoming more sophisticated and harder to predict. Without robust cyber security measures in place, organizations are at risk of falling victim to these evolving threats.
Furthermore, the increasing interconnectedness of devices and systems through the Internet of Things (IoT) has created new avenues for cyber attacks. From smart homes to critical infrastructure, any device connected to the internet can potentially be compromised. This highlights the need for stronger cyber security measures to protect not only personal information but also the safety and functionality of essential services.
Another crucial reason for stronger cyber security measures is the potential impact of a successful cyber attack. The consequences can be devastating, both financially and reputationally. Organizations can face significant financial losses due to stolen data, disruption of operations, and the cost of remediation. Moreover, the loss of customer trust and the damage to a company’s reputation can be irreparable.
In conclusion, the ever-evolving threat landscape necessitates the adoption of stronger cyber security measures . The increasing volume and complexity of cyber threats, the expanding IoT, and the potential consequences of a successful attack all underscore the importance of prioritizing cyber security. Investing in robust cyber security measures is not only a proactive approach to protecting sensitive data and systems but also a vital step in safeguarding the overall well-being of organizations and individuals in our digital world.
Cyber security best practices for individuals and organizations

Cyber security is not just a concern for governments and large corporations; it is equally crucial for individuals and small organizations. In today’s digital age, where cyber threats are constantly evolving, implementing best practices is essential to protect sensitive information and maintain data integrity. This article will discuss some of the top cyber security best practices that individuals and organizations should follow.
- Strong and Unique Passwords: One of the simplest yet most effective ways to enhance cyber security is by using strong and unique passwords. Avoid using common passwords or personal information that can be easily guessed. Consider using a password manager to generate and securely store complex passwords.
- Two-Factor Authentication: Enable two-factor authentication (2FA) whenever possible. This adds an extra layer of security by requiring a second verification step, such as a code sent to your mobile device, in addition to your password.
- Regular Software Updates: Keeping all software and operating systems up to date is crucial. Software updates often include patches for known vulnerabilities, which hackers can exploit. Set up automatic updates to ensure that you are always running the latest versions.
- Secure Wi-Fi Networks: Protect your home or office Wi-Fi network with a strong and unique password. Additionally, consider enabling network encryption, such as WPA2, to secure the communication between devices and the network.
- Employee Training and Awareness: Organizations should prioritize cyber security training and awareness programs for their employees. This helps ensure that everyone understands the importance of following security protocols and recognizes potential threats like phishing emails or suspicious links.
- Regular Data Backups: Regularly backing up important data is crucial in case of a cyber attack or data loss. Store backups on separate devices or in the cloud, and test the restoration process periodically to ensure the data can be recovered.
- Firewalls and Antivirus Software: Install and regularly update firewalls and antivirus software on all devices. These security tools provide an additional layer of protection against malware, viruses, and other cyber threats.
- Secure Web Browsing: Be cautious when browsing the internet. Avoid clicking on suspicious links or downloading files from untrusted sources. Use reputable web browsers and consider using browser extensions that provide additional security features.
By implementing these cyber security best practices, individuals and organizations can significantly reduce the risk of falling victim to cyber attacks and protect sensitive information from unauthorized access. Stay vigilant, stay informed, and stay secure!
The cost of cyber attacks and the value of investing in cyber security
In today’s digital age, the cost of cyber attacks is staggering. The value of investing in cyber security cannot be overstated. Cyber attacks not only lead to significant financial losses for businesses, but also result in reputational damage, legal consequences, and potential customer distrust. It is crucial for organizations to understand the true extent of the impact cyber attacks can have on their bottom line.
The financial cost of cyber attacks is multifaceted. The direct expenses include incident response, recovery, and potential ransom payments. However, the long-term financial repercussions often extend far beyond these immediate costs. Companies may suffer from lost revenue due to downtime, loss of intellectual property, or the need to invest in new security measures to prevent future attacks. Additionally, there are legal expenses and fines that can result from non-compliance with data protection regulations.
Furthermore, the intangible costs of cyber attacks are equally significant. A breach of customer data can lead to a loss of trust and loyalty, impacting customer retention and acquisition. The damage to reputation may result in decreased brand value and a loss of competitive advantage. Rebuilding trust and repairing a damaged reputation can be a time-consuming and expensive process.
Investing in cyber security is essential to mitigate the risks posed by cyber attacks. By implementing robust security measures and proactive monitoring, organizations can greatly reduce the likelihood and impact of successful attacks. The investment in cyber security is not just a cost, but rather an investment in the longevity and resilience of the business.
Cyber security measures include securing networks, implementing strong access controls, regularly updating and patching software, educating employees about security best practices, and conducting regular security audits. By staying ahead of evolving threats and investing in the right technology and expertise, organizations can enhance their ability to detect, respond to, and recover from cyber attacks.
In conclusion, the cost of cyber attacks is not limited to immediate financial losses. The long-term consequences, including reputational damage and legal ramifications, can be equally devastating. Investing in cyber security is not only a smart financial decision, but also a critical step in safeguarding the future of any organization. By understanding the true cost of cyber attacks and the value of investing in cyber security, businesses can make informed decisions to protect themselves and their stakeholders.
The correlation between cyber security and privacy in the digital age
In the fast-paced digital age, the correlation between cyber security and privacy has become increasingly intricate and crucial. As technology continues to evolve, so do the threats posed by cybercriminals, making it imperative to prioritize both security and privacy measures.
Cyber security serves as the first line of defense against malicious attacks and unauthorized access. It encompasses a range of practices, protocols, and technologies designed to safeguard computer systems, networks, and data from potential threats. By implementing robust cyber security measures, individuals and organizations can protect their sensitive information, prevent data breaches, and maintain the confidentiality and integrity of their digital assets.
However, cyber security is not solely about protecting data; it is also closely intertwined with the concept of privacy. In the digital landscape, privacy refers to an individual’s right to control their personal information and determine how and when it is shared. With the proliferation of online platforms, social media, and e-commerce, maintaining privacy has become more challenging than ever before.
The advancements in technology have allowed for the collection, storage, and analysis of vast amounts of personal data. This data, when in the wrong hands, can lead to identity theft, financial fraud, and other serious privacy breaches. Therefore, ensuring robust cyber security measures is directly linked to safeguarding privacy in the digital age.
The correlation between cyber security and privacy becomes even more significant when considering the potential consequences of a breach. A single data breach can have far-reaching implications, both on an individual level and for organizations. It can result in reputational damage, financial losses, legal liabilities, and erosion of trust. Such breaches can also compromise national security, disrupt critical infrastructure, and impact the overall stability of the digital ecosystem.
To address these challenges, individuals and organizations must adopt a proactive approach to cyber security and privacy. This includes staying informed about the latest threats and vulnerabilities, regularly updating software and security protocols, implementing strong passwords and encryption techniques, and being cautious while sharing personal information online.
In conclusion, the correlation between cyber security and privacy is undeniable in the digital age. Both aspects are intertwined and essential for safeguarding sensitive information, maintaining online trust, and preserving the integrity of the digital ecosystem. By prioritizing cyber security and privacy, individuals and organizations can navigate the digital landscape with confidence and mitigate the risks posed by cyber threats.
The role of government in promoting and enforcing cyber security regulations
In today’s digital age, the role of government in promoting and enforcing cyber security regulations is of paramount importance. With the increasing frequency and sophistication of cyber threats, it has become imperative for governments to actively intervene and safeguard their nations’ vital digital infrastructure and sensitive information. This article delves into the reasons why the government plays a crucial role in ensuring cyber security and the impact of their regulations on protecting individuals, businesses, and national security.
First and foremost, the government has the authority and resources to establish robust cyber security regulations that set standards and guidelines for all sectors. By creating a legal framework, they enforce compliance and hold organizations accountable for implementing appropriate security measures. This helps to create a culture of cyber security awareness and ensures that businesses prioritize the protection of valuable data.
Moreover, governments have access to intelligence and information sharing networks that enable them to identify emerging threats and vulnerabilities. By actively monitoring cyber activities, they can proactively respond to potential attacks and prevent major security breaches. This proactive approach not only protects individuals and businesses but also strengthens the overall resilience of the nation’s digital infrastructure.
Additionally, the government plays a vital role in promoting international cooperation and establishing global cyber security standards. Since cyber threats transcend national boundaries, collaboration between governments is essential to address these challenges collectively. By participating in international forums and treaties, governments can foster information exchange, capacity building, and joint efforts to combat cybercrime.
Furthermore, the government’s involvement in cyber security regulations is crucial for national security. Cyber attacks have the potential to disrupt critical infrastructure, compromise defense systems, and even manipulate elections. By establishing stringent regulations and investing in cyber defense capabilities, governments can safeguard their nation’s sovereignty and protect against potential cyber warfare.
However, it is important to strike a balance between promoting cyber security and ensuring individual privacy rights. Governments need to find the right balance between collecting necessary data for security purposes and protecting citizens’ privacy. This requires transparent and accountable governance, with checks and balances in place to prevent misuse of power.
In conclusion, the role of government in promoting and enforcing cyber security regulations is vital in today’s interconnected world. With the increasing complexity and severity of cyber threats, governments need to take proactive measures to protect their nations’ digital assets. By establishing robust regulations, fostering international cooperation, and investing in cyber defense capabilities, governments can create a safe and secure digital environment for individuals, businesses, and national security.
Emerging technologies and their impact on cyber security challenges
In today’s rapidly evolving technological landscape, emerging technologies have brought about immense advancements and opportunities. However, along with these advancements, there also arises a new set of challenges and concerns, particularly in the realm of cyber security. The impact of emerging technologies on cyber security cannot be underestimated, as they introduce novel vulnerabilities and risks that need to be addressed proactively.
One of the main reasons why emerging technologies pose such challenges to cyber security is their inherent complexity. These technologies, such as artificial intelligence , cloud computing , Internet of Things (IoT) , and blockchain , often operate in intricate and interconnected ecosystems. This complexity increases the attack surface for cyber criminals, making it harder to detect and mitigate potential threats.
Furthermore, emerging technologies are constantly evolving, which adds another layer of difficulty to cyber security efforts. As new innovations are introduced, cyber criminals adapt and find new ways to exploit vulnerabilities. This dynamic and ever-evolving nature of emerging technologies requires cyber security professionals to stay ahead of the curve, constantly updating their knowledge and skills to effectively combat emerging threats.
Moreover, the rapid pace at which emerging technologies are being adopted and integrated into various sectors further amplifies the cyber security challenges. Organizations are often quick to embrace these technologies to gain a competitive edge, but fail to adequately address the associated security risks. This creates a gap that cyber criminals can exploit, potentially leading to data breaches, financial losses, and reputational damage.
Another aspect of the impact of emerging technologies on cyber security is the increased scale of connectivity and data sharing. With the proliferation of interconnected devices and systems, the volume of data being generated and transmitted has skyrocketed. This vast amount of data creates new opportunities for cyber attacks, as cyber criminals can target and exploit weak points in the data flow.
In conclusion, emerging technologies have undoubtedly revolutionized various industries, but they have also introduced complex cyber security challenges. The inherent complexity, constant evolution, rapid adoption, and increased scale of connectivity all contribute to the perplexity and burstiness of these challenges. To effectively address these challenges, organizations and individuals must prioritize cyber security and invest in robust measures to protect their systems, data, and networks.
The future of cyber security: trends and predictions
The future of cyber security is an enigmatic landscape that is constantly evolving, filled with both promising advancements and daunting challenges. As technology continues to advance at an unprecedented rate, the need for robust cyber security measures becomes increasingly vital. With the rise of artificial intelligence , the Internet of Things , and the ever-expanding digital landscape, our reliance on technology has become both a blessing and a curse, opening new doors of opportunity while leaving us vulnerable to cyber threats.
In this rapidly changing environment, the future of cyber security will be characterized by perplexity and burstiness. Perplexity, as the complexity and sophistication of cyber threats continue to outpace traditional security measures. Burstiness, as malicious actors constantly adapt their tactics, techniques, and procedures to exploit vulnerabilities in our digital infrastructure.
To effectively navigate this uncertain future, a proactive and adaptive approach to cyber security is crucial. Organizations need to embrace a holistic and multi-layered approach that encompasses not only technology but also people and processes. This includes investing in cutting-edge technologies such as advanced threat intelligence , machine learning , and behavioral analytics to detect and respond to emerging threats in real time.
Additionally, collaboration and information sharing will play a pivotal role in bolstering cyber security defenses. Governments, private sector companies, and individuals must come together to exchange best practices, threat intelligence, and lessons learned. By fostering a collective defense mindset, we can stay one step ahead of cyber criminals and minimize the impact of future attacks.
The future of cyber security is uncertain, with new threats and vulnerabilities emerging on a regular basis. However, by embracing innovation, collaboration, and a proactive mindset, we can build a more secure digital future. It is essential that we invest in research and development, education and awareness, and the cultivation of a skilled cyber security workforce to tackle the challenges that lie ahead. Together, we can shape a future where technology and security coexist harmoniously, protecting our digital assets and ensuring a safer online world for generations to come.
What is cyber security?
Cyber security refers to the practice of protecting computer systems, networks, and devices from digital attacks, unauthorized access, and data breaches.
Why do we need cyber security?
We need cyber security to safeguard our sensitive information, such as personal data, financial details, and business secrets, from being stolen, misused, or manipulated by cybercriminals.
What are the common cyber threats?
Common cyber threats include malware (such as viruses and ransomware), phishing attacks, social engineering, hacking, and denial-of-service (DoS) attacks.
How can cyber security help individuals?
Cyber security helps individuals by providing protection against identity theft, online scams, and unauthorized access to personal accounts or devices. It allows for safe online banking, shopping, and communication.
Why is cyber security important for businesses?
Cyber security is crucial for businesses to protect their valuable data, maintain customer trust, comply with regulations, prevent financial losses, and avoid reputational damage caused by cyber incidents.
What are some best practices for cyber security?
Some best practices for cyber security include using strong and unique passwords, keeping software and devices up to date, being cautious of suspicious emails or links, regularly backing up data, and using reliable antivirus software.
Is cyber security a constant concern?
Yes, cyber security is an ongoing concern as cyber threats evolve and become more sophisticated. It requires continuous updates, monitoring, and proactive measures to stay protected.
Can individuals contribute to cyber security?
Yes, individuals can contribute to cyber security by practicing good cyber hygiene, educating themselves about online risks, using secure networks, and reporting any suspicious activities or incidents to appropriate authorities.
In conclusion, cyber security is crucial in today’s digital age. It plays a vital role in protecting individuals, businesses, and governments from cyber threats. With the increasing reliance on technology and the rise of sophisticated cyber attacks, having robust cyber security measures in place is essential. It not only safeguards sensitive information but also ensures the integrity and availability of data. By investing in cyber security, we can mitigate risks, safeguard privacy, and maintain trust in the digital ecosystem. Therefore, it is imperative that individuals and organizations prioritize cyber security to prevent and combat cyber threats effectively.
Related Posts

The Significance of Cyber Security Training
In today’s digital world, cyber security training has become crucial. With increasing cyber threats, organizations need to ensure their employees are equipped with the necessary skills to detect and prevent attacks. Training helps create awareness about potential risks, teaches best practices, and promotes a culture of security. It empowers individuals to safeguard sensitive data, mitigate threats, and contribute to a safe online environment.

The Importance of Cyber Security
Cyber security is more important than ever in today’s digital age. With the increasing number of cyber threats and attacks, it is crucial for individuals and businesses to protect their sensitive data. From financial transactions to personal information, cyber security ensures confidentiality, integrity, and availability. Learn why cyber security matters and how it impacts our daily lives.

Understanding Cyber Security Month: Importance and Impact
October is designated as Cyber Security Month, an annual campaign to raise awareness about the importance of online safety. Throughout the month, various organizations and individuals come together to promote cybersecurity practices and educate the public on how to protect themselves from cyber threats. Stay tuned for exciting events, informative resources, and practical tips to enhance your digital security this Cyber Security Month!
- CBSE Class 10th
- CBSE Class 12th
- UP Board 10th
- UP Board 12th
- Bihar Board 10th
- Bihar Board 12th
- Top Schools in India
- Top Schools in Delhi
- Top Schools in Mumbai
- Top Schools in Chennai
- Top Schools in Hyderabad
- Top Schools in Kolkata
- Top Schools in Pune
- Top Schools in Bangalore
Products & Resources
- JEE Main Knockout April
- Free Sample Papers
- Free Ebooks
- NCERT Notes
- NCERT Syllabus
- NCERT Books
- RD Sharma Solutions
- Navodaya Vidyalaya Admission 2024-25
- NCERT Solutions
- NCERT Solutions for Class 12
- NCERT Solutions for Class 11
- NCERT solutions for Class 10
- NCERT solutions for Class 9
- NCERT solutions for Class 8
- NCERT Solutions for Class 7
- JEE Main 2024
- MHT CET 2024
- JEE Advanced 2024
- BITSAT 2024
- View All Engineering Exams
- Colleges Accepting B.Tech Applications
- Top Engineering Colleges in India
- Engineering Colleges in India
- Engineering Colleges in Tamil Nadu
- Engineering Colleges Accepting JEE Main
- Top IITs in India
- Top NITs in India
- Top IIITs in India
- JEE Main College Predictor
- JEE Main Rank Predictor
- MHT CET College Predictor
- AP EAMCET College Predictor
- GATE College Predictor
- KCET College Predictor
- JEE Advanced College Predictor
- View All College Predictors
- JEE Advanced Cutoff
- JEE Main Cutoff
- JEE Advanced Answer Key
- JEE Advanced Result
- Download E-Books and Sample Papers
- Compare Colleges
- B.Tech College Applications
- KCET Result
- MAH MBA CET Exam
- View All Management Exams
Colleges & Courses
- MBA College Admissions
- MBA Colleges in India
- Top IIMs Colleges in India
- Top Online MBA Colleges in India
- MBA Colleges Accepting XAT Score
- BBA Colleges in India
- XAT College Predictor 2024
- SNAP College Predictor
- NMAT College Predictor
- MAT College Predictor 2024
- CMAT College Predictor 2024
- CAT Percentile Predictor 2023
- CAT 2023 College Predictor
- CMAT 2024 Answer Key
- TS ICET 2024 Hall Ticket
- CMAT Result 2024
- MAH MBA CET Cutoff 2024
- Download Helpful Ebooks
- List of Popular Branches
- QnA - Get answers to your doubts
- IIM Fees Structure
- AIIMS Nursing
- Top Medical Colleges in India
- Top Medical Colleges in India accepting NEET Score
- Medical Colleges accepting NEET
- List of Medical Colleges in India
- List of AIIMS Colleges In India
- Medical Colleges in Maharashtra
- Medical Colleges in India Accepting NEET PG
- NEET College Predictor
- NEET PG College Predictor
- NEET MDS College Predictor
- NEET Rank Predictor
- DNB PDCET College Predictor
- NEET Result 2024
- NEET Asnwer Key 2024
- NEET Cut off
- NEET Online Preparation
- Download Helpful E-books
- Colleges Accepting Admissions
- Top Law Colleges in India
- Law College Accepting CLAT Score
- List of Law Colleges in India
- Top Law Colleges in Delhi
- Top NLUs Colleges in India
- Top Law Colleges in Chandigarh
- Top Law Collages in Lucknow
Predictors & E-Books
- CLAT College Predictor
- MHCET Law ( 5 Year L.L.B) College Predictor
- AILET College Predictor
- Sample Papers
- Compare Law Collages
- Careers360 Youtube Channel
- CLAT Syllabus 2025
- CLAT Previous Year Question Paper
- NID DAT Exam
- Pearl Academy Exam
Predictors & Articles
- NIFT College Predictor
- UCEED College Predictor
- NID DAT College Predictor
- NID DAT Syllabus 2025
- NID DAT 2025
- Design Colleges in India
- Top NIFT Colleges in India
- Fashion Design Colleges in India
- Top Interior Design Colleges in India
- Top Graphic Designing Colleges in India
- Fashion Design Colleges in Delhi
- Fashion Design Colleges in Mumbai
- Top Interior Design Colleges in Bangalore
- NIFT Result 2024
- NIFT Fees Structure
- NIFT Syllabus 2025
- Free Design E-books
- List of Branches
- Careers360 Youtube channel
- IPU CET BJMC
- JMI Mass Communication Entrance Exam
- IIMC Entrance Exam
- Media & Journalism colleges in Delhi
- Media & Journalism colleges in Bangalore
- Media & Journalism colleges in Mumbai
- List of Media & Journalism Colleges in India
- CA Intermediate
- CA Foundation
- CS Executive
- CS Professional
- Difference between CA and CS
- Difference between CA and CMA
- CA Full form
- CMA Full form
- CS Full form
- CA Salary In India
Top Courses & Careers
- Bachelor of Commerce (B.Com)
- Master of Commerce (M.Com)
- Company Secretary
- Cost Accountant
- Charted Accountant
- Credit Manager
- Financial Advisor
- Top Commerce Colleges in India
- Top Government Commerce Colleges in India
- Top Private Commerce Colleges in India
- Top M.Com Colleges in Mumbai
- Top B.Com Colleges in India
- IT Colleges in Tamil Nadu
- IT Colleges in Uttar Pradesh
- MCA Colleges in India
- BCA Colleges in India
Quick Links
- Information Technology Courses
- Programming Courses
- Web Development Courses
- Data Analytics Courses
- Big Data Analytics Courses
- RUHS Pharmacy Admission Test
- Top Pharmacy Colleges in India
- Pharmacy Colleges in Pune
- Pharmacy Colleges in Mumbai
- Colleges Accepting GPAT Score
- Pharmacy Colleges in Lucknow
- List of Pharmacy Colleges in Nagpur
- GPAT Result
- GPAT 2024 Admit Card
- GPAT Question Papers
- NCHMCT JEE 2024
- Mah BHMCT CET
- Top Hotel Management Colleges in Delhi
- Top Hotel Management Colleges in Hyderabad
- Top Hotel Management Colleges in Mumbai
- Top Hotel Management Colleges in Tamil Nadu
- Top Hotel Management Colleges in Maharashtra
- B.Sc Hotel Management
- Hotel Management
- Diploma in Hotel Management and Catering Technology
Diploma Colleges
- Top Diploma Colleges in Maharashtra
- UPSC IAS 2024
- SSC CGL 2024
- IBPS RRB 2024
- Previous Year Sample Papers
- Free Competition E-books
- Sarkari Result
- QnA- Get your doubts answered
- UPSC Previous Year Sample Papers
- CTET Previous Year Sample Papers
- SBI Clerk Previous Year Sample Papers
- NDA Previous Year Sample Papers
Upcoming Events
- NDA Application Form 2024
- UPSC IAS Application Form 2024
- CDS Application Form 2024
- CTET Admit card 2024
- HP TET Result 2023
- SSC GD Constable Admit Card 2024
- UPTET Notification 2024
- SBI Clerk Result 2024
Other Exams
- SSC CHSL 2024
- UP PCS 2024
- UGC NET 2024
- RRB NTPC 2024
- IBPS PO 2024
- IBPS Clerk 2024
- IBPS SO 2024
- Top University in USA
- Top University in Canada
- Top University in Ireland
- Top Universities in UK
- Top Universities in Australia
- Best MBA Colleges in Abroad
- Business Management Studies Colleges
Top Countries
- Study in USA
- Study in UK
- Study in Canada
- Study in Australia
- Study in Ireland
- Study in Germany
- Study in China
- Study in Europe
Student Visas
- Student Visa Canada
- Student Visa UK
- Student Visa USA
- Student Visa Australia
- Student Visa Germany
- Student Visa New Zealand
- Student Visa Ireland
- CUET PG 2024
- IGNOU B.Ed Admission 2024
- DU Admission 2024
- UP B.Ed JEE 2024
- LPU NEST 2024
- IIT JAM 2024
- IGNOU Online Admission 2024
- Universities in India
- Top Universities in India 2024
- Top Colleges in India
- Top Universities in Uttar Pradesh 2024
- Top Universities in Bihar
- Top Universities in Madhya Pradesh 2024
- Top Universities in Tamil Nadu 2024
- Central Universities in India
- CUET DU Cut off 2024
- IGNOU Date Sheet
- CUET DU CSAS Portal 2024
- CUET Response Sheet 2024
- CUET Result 2024
- CUET Participating Universities 2024
- CUET Previous Year Question Paper
- CUET Syllabus 2024 for Science Students
- E-Books and Sample Papers
- CUET Exam Pattern 2024
- CUET Exam Date 2024
- CUET Cut Off 2024
- CUET Exam Analysis 2024
- IGNOU Exam Form 2024
- CUET PG Counselling 2024
- CUET Answer Key 2024
Engineering Preparation
- Knockout JEE Main 2024
- Test Series JEE Main 2024
- JEE Main 2024 Rank Booster
Medical Preparation
- Knockout NEET 2024
- Test Series NEET 2024
- Rank Booster NEET 2024
Online Courses
- JEE Main One Month Course
- NEET One Month Course
- IBSAT Free Mock Tests
- IIT JEE Foundation Course
- Knockout BITSAT 2024
- Career Guidance Tool
Top Streams
- IT & Software Certification Courses
- Engineering and Architecture Certification Courses
- Programming And Development Certification Courses
- Business and Management Certification Courses
- Marketing Certification Courses
- Health and Fitness Certification Courses
- Design Certification Courses
Specializations
- Digital Marketing Certification Courses
- Cyber Security Certification Courses
- Artificial Intelligence Certification Courses
- Business Analytics Certification Courses
- Data Science Certification Courses
- Cloud Computing Certification Courses
- Machine Learning Certification Courses
- View All Certification Courses
- UG Degree Courses
- PG Degree Courses
- Short Term Courses
- Free Courses
- Online Degrees and Diplomas
- Compare Courses
Top Providers
- Coursera Courses
- Udemy Courses
- Edx Courses
- Swayam Courses
- upGrad Courses
- Simplilearn Courses
- Great Learning Courses
Cyber Security Essay
Cyber security is one of the most important topics in today’s digital world. With technology evolving at an unprecedented pace and more companies going online than ever before, it’s essential that everyone understands the basics of cyber security. Here are some sample essays on cyber security.
- 100 Words Essay On Cyber Security
As a student in today's digital world, it's important to remember the importance of cyber security. Today, almost everything that we do is done online or through the internet, and that means our personal information, like our passwords, banking information, and even our school work, is vulnerable to cyber security threats.
200 Words Essay On Cyber Security
500 words essay on cyber security.

Cyber security is the practice of protecting networks, systems, and programs from digital attacks. These attacks can come from many different sources, including hackers, viruses, and even from other people. In order to stay safe online, it's essential to understand the basics of cyber security. Cyber security is an ever-evolving field, and it's important for school students to stay informed and take the necessary steps to protect themselves online.
School students are the future of our society, and it's important to teach them the importance of cyber security from an early age. Cyber security is an ever-increasing problem in our digital world, and it's up to us to ensure that our students are aware of the risks and dangers that come with the internet.
What Is Cyber Security?
Cyber security is the practice of protecting digital devices and networks from unauthorised access and malicious activities. With the rise of technology and its integration into our lives, cyber security has become an integral part of our lives, and it's important for school students to understand the need for cyber security measures.

How To Protect Yourself From Cyber Crime?
One of the most important ways to protect your devices and networks from cyber threats is to create strong passwords and never share them with anyone else. Passwords are the first line of defence against cyber attacks, and it's important that school students understand how to create and use strong passwords. Additionally, students should be taught to never share personal information online, such as passwords, credit card numbers, and bank account information.
Staying informed is the best way to stay ahead of the latest threats, and it's important for students to stay up-to-date on the latest cyber security news and updates.
Cyber security is the use of antivirus and anti-malware software. These programs are designed to detect and block malicious programs, such as viruses, worms, and Trojans, before they can do any damage to your devices and networks. By teaching our students about the importance of cyber security, we can ensure that they will be better prepared to protect themselves and their devices from cyber threats.
Cyber Security is essential for all those who regularly and frequently use electronic devices. With so much of our sensitive data and documents stored on these gadgets, it is essential to ensure their protection. There are several ways to protect your devices from cyber threats, such as using Antivirus and Antimalware software, and implementing End-User Protection solutions. Taking the necessary steps to secure your devices can help keep your data safe and secure.
Causes Of Cyber Crime
There are many different causes of cybercrime, but most can be categorised into one of three categories:
Personal gain | This is perhaps the most common motivation for cybercrime, as it can be very lucrative. Cybercriminals may engage in activities such as identity theft, phishing scams, and credit card fraud in order to make money.
Revenge or vandalism | Some cybercriminals commit crimes out of a desire for revenge or simply to cause havoc. They may engage in activities such as denial of service attacks, website defacement, or even doxxing (releasing personal information online).
Political or ideological motivations | In some cases, cybercrime is committed for political or ideological reasons. For example, hackers may attack a website in order to protest its content or disrupt its operations.
How To Increase Cyber Security
For school students, cyber security is especially important. Many students use the internet for their studies, making them more vulnerable to cyberattacks. Hackers may try to access school networks, steal student data, or even disrupt classes. It’s important for students to know how to protect themselves from cyber threats. There are some simple steps that you can take to ensure your safety and security.
The first step is to create strong passwords for all of your accounts. Passwords should be hard to guess and should never be shared with anyone. Make sure to use a combination of upper and lowercase letters, numbers, and symbols. It's also important to change your passwords regularly.
Next, you should be sure to protect your personal information. This means making sure that you don't share your passwords or other sensitive information online. Be sure to use an up-to-date antivirus program to scan your computer regularly for malicious software.
Finally, be sure to stay informed about the latest cyber security threats. Keeping up with the news and reading articles on cyber security can help you stay aware of the latest threats and how to protect yourself against them.
By following these tips, you can stay safe online and protect your personal information. Cyber security is an important issue and it's important to take it seriously. If you take the time to learn more about cyber security and make sure you take steps to protect yourself, you can stay safe online and enjoy the benefits of today's digital world.
Applications for Admissions are open.

Aakash iACST Scholarship Test 2024
Get up to 90% scholarship on NEET, JEE & Foundation courses

ALLEN Digital Scholarship Admission Test (ADSAT)
Register FREE for ALLEN Digital Scholarship Admission Test (ADSAT)

JEE Main Important Physics formulas
As per latest 2024 syllabus. Physics formulas, equations, & laws of class 11 & 12th chapters

PW JEE Coaching
Enrol in PW Vidyapeeth center for JEE coaching

PW NEET Coaching
Enrol in PW Vidyapeeth center for NEET coaching

JEE Main Important Chemistry formulas
As per latest 2024 syllabus. Chemistry formulas, equations, & laws of class 11 & 12th chapters
Download Careers360 App's
Regular exam updates, QnA, Predictors, College Applications & E-books now on your Mobile
Certifications
We Appeared in

Essay on Cyber Security
Students are often asked to write an essay on Cyber Security in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Cyber Security
Understanding cyber security.
Cyber security is about protecting computers, servers, mobile devices, electronic systems, networks, and data from digital attacks. It’s a critical area as our daily life, economic vitality, and national security rely on a stable, safe, and resilient cyberspace.
The Importance of Cyber Security
Cyber security is important because it helps protect sensitive information, like our personal data and banking details, from being stolen by hackers. It also safeguards against harmful viruses that can damage our devices.
Types of Cyber Threats
Common threats include malware, phishing, and ransomware. Malware is harmful software, phishing tricks people into revealing sensitive information, and ransomware locks users out until they pay a ransom.
Cyber Security Practices
Good practices include using strong passwords, regularly updating software, and not clicking on suspicious links. These can help protect us from cyber threats.
Also check:
- Paragraph on Cyber Security
- Speech on Cyber Security
250 Words Essay on Cyber Security
Introduction to cyber security.
Cybersecurity, a term that has gained paramount importance in the digital age, refers to the practice of protecting internet-connected systems, including hardware, software, and data, from digital attacks. Its significance is amplified by the increasing reliance on technology, which, while offering numerous benefits, also opens up new avenues for potential threats.
The digital landscape is a double-edged sword. On one hand, it facilitates communication, commerce, and innovation. On the other, it provides a fertile ground for cybercriminals to exploit vulnerabilities. Cybersecurity thus becomes crucial in safeguarding sensitive information, preventing unauthorized access, and maintaining system integrity.
Challenges in Cyber Security
However, the complexity and sophistication of cyber threats are growing at an alarming pace. Cybercriminals are using advanced techniques, such as AI and machine learning, to bypass traditional security measures. This necessitates the development of more robust, adaptive cybersecurity strategies.
The Future of Cyber Security
The future of cybersecurity lies in proactive defense mechanisms. By leveraging technologies like AI, predictive analytics, and blockchain, we can anticipate and neutralize threats before they cause harm. Furthermore, fostering a culture of cybersecurity awareness is equally important to empower individuals and organizations against cyber threats.
In conclusion, cybersecurity is a vital aspect of our digital existence. Its importance, challenges, and future prospects underline the need for continuous research, development, and education in this field. As the digital landscape evolves, so too must our approach to cybersecurity.
500 Words Essay on Cyber Security
Cyber security, also known as information technology security, focuses on protecting computers, networks, programs, and data from unintended or unauthorized access, damage, or destruction. In the digital era, the importance of cyber security is growing exponentially due to the increasing reliance on computer systems, the internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices like smartphones and televisions.
The significance of robust cyber security measures cannot be understated. Cyber attacks can lead to serious consequences like identity theft, extortion attempts, deletion of important data, and even the disruption of normal business operations. In more extreme cases, they can lead to the compromise of national security. Hence, cyber security is not just a concern for businesses or governments, but it is a potential threat to all internet users.
Cyber threats can be broadly divided into three categories: Cybercrime includes single actors or groups targeting systems for financial gain or to cause disruption; Cyber-attack often involves politically motivated information gathering; and Cyberterrorism is intended to undermine electronic systems to cause panic or fear. Examples of these threats are malware, phishing, ransomware, and social engineering.
Cyber Security Measures
In response to these threats, several cyber security measures are being employed. These include firewalls, intrusion detection systems, anti-virus software, and encryption. Furthermore, organizations are increasingly recognizing the importance of information assurance, where data integrity, confidentiality, and availability are assured.
As technology evolves, so does the complexity and sophistication of cyber threats. Hence, the future of cyber security lies in constant evolution and adaptation. Artificial Intelligence (AI) and Machine Learning (ML) are becoming integral in combating cyber threats. These technologies can learn and adapt to new threats, making them more efficient than traditional security measures.
In conclusion, cyber security is a crucial aspect of our digital lives, and its importance will only increase with time. To ensure a secure digital environment, individuals, organizations, and governments must understand the potential threats and employ robust security measures to counter them. The future of cyber security is promising, with the advent of AI and ML, but the road ahead is challenging, requiring constant vigilance and adaptation to new threats.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Cyber Bullying
- Essay on Customer Service
- Essay on Tourism in Kerala
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

- Undergraduate
- High School
- Architecture
- American History
- Asian History
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- Linguistics
- Criminal Justice
- Legal Issues
- Anthropology
- Archaeology
- Political Science
- World Affairs
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Pharmacology
- Earth science
- Agriculture
- Agricultural Studies
- Computer Science
- IT Management
- Mathematics
- Investments
- Engineering and Technology
- Engineering
- Aeronautics
- Medicine and Health
- Alternative Medicine
- Communications and Media
- Advertising
- Communication Strategies
- Public Relations
- Educational Theories
- Teacher's Career
- Chicago/Turabian
- Company Analysis
- Education Theories
- Shakespeare
- Canadian Studies
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
- Movie Review
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Marketing Plan
- Multiple Choice Quiz
- Personal Statement
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Reaction Paper
- Research Paper
- Research Proposal
- SWOT analysis
- Thesis Paper
- Online Quiz
- Literature Review
- Movie Analysis
- Statistics problem
- Math Problem
- All papers examples
- How It Works
- Money Back Policy
- Terms of Use
- Privacy Policy
- We Are Hiring
Security Measures in Transport and Logistics Management, Essay Example
Pages: 1
Words: 347
Hire a Writer for Custom Essay
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.
Transportation and logistics management continues to face new challenges as economic, social and political facets of business transform through the cycles of business. As markets introduce new technologies, processes and procedures, they expose themselves to a number of variables that influence the security of the transportation and logistics channels (Essig, Hu?lsmann, Kern, & Klein-Schmeink, 2013). These security issues affect all aspects of the supply and logistics chain from the producer to the consumer. The government has developed a number of strategies that are geared towards assisting government agencies identify and isolate threats in time.
With the threat of terrorism growing with each passing day, the transportation and logistics is a high-value target as not only is it essential in the transportation of goods from one place to another, it an integral sector of the economy. The government’s most notable initiative to this effect is the Customs-Trade Partnership against Terrorism (C-TPAT). C-TPAT is US Customs and Border Protection run voluntary program that develops cooperative relationships between government agencies and businesses to improve the security of the supply chain. The Certified Cargo Screening Program (CSSP) run by the Transportation Security Administration (TSA) is another significant measure by the government (Plunkett, 2012). This program ensures that all outbound cargo from the United States is screened.
In the continuous problem of improvement, a fragmented supply chain is one of the most significant problems. As the supply chain is divided into numerous players, integrating processes and standards would require extensive efforts from all market players. While the measures employed by the government have been largely effective, they significantly affect transportation and logistics management. Initiatives such C-TPAT aim to develop a well-connected and integrated supply chain. This would reduce the interruption of business in the case of a potential threat to the supply chain.
Essig, M., Hu?lsmann, M., Kern, E.-M., & Klein-Schmeink, S. (2013). Supply Chain Safety Management : Security and Robustness in Logistics. Berlin: Springer.
Plunkett, J. W. (2012). Plunkett’s transportation, supply chain & logistics industry almanac 2012 : the only comprehensive guide to the business of transportation, supply chain & logistics management (8th ed.). Houston: Plunkett Research.
Stuck with your Essay?
Get in touch with one of our experts for instant help!
Staying on Target, Case Study Example
Expanding the Scope of the Hazmat Compliance Envelope, Essay Example
Time is precious
don’t waste it!
Plagiarism-free guarantee
Privacy guarantee
Secure checkout
Money back guarantee

Related Essay Samples & Examples
Voting as a civic responsibility, essay example.
Words: 287
Utilitarianism and Its Applications, Essay Example
Words: 356
The Age-Related Changes of the Older Person, Essay Example
Pages: 2
Words: 448
The Problems ESOL Teachers Face, Essay Example
Pages: 8
Words: 2293
Should English Be the Primary Language? Essay Example
Pages: 4
Words: 999
The Term “Social Construction of Reality”, Essay Example
Words: 371
Data Security Measures Essays
Ar problem identification, the problems in the organization, popular essay topics.
- American Dream
- Artificial Intelligence
- Black Lives Matter
- Bullying Essay
- Career Goals Essay
- Causes of the Civil War
- Child Abusing
- Civil Rights Movement
- Community Service
- Cultural Identity
- Cyber Bullying
- Death Penalty
- Depression Essay
- Domestic Violence
- Freedom of Speech
- Global Warming
- Gun Control
- Human Trafficking
- I Believe Essay
- Immigration
- Importance of Education
- Israel and Palestine Conflict
- Leadership Essay
- Legalizing Marijuanas
- Mental Health
- National Honor Society
- Police Brutality
- Pollution Essay
- Racism Essay
- Romeo and Juliet
- Same Sex Marriages
- Social Media
- The Great Gatsby
- The Yellow Wallpaper
- Time Management
- To Kill a Mockingbird
- Violent Video Games
- What Makes You Unique
- Why I Want to Be a Nurse
- Send us an e-mail
We use cookies to enhance our website for you. Proceed if you agree to this policy or learn more about it.
- Essay Database >
- Essay Examples >
- Essays Topics >
- Essay on Disaster
Safety And Security Awareness Essay Examples
Type of paper: Essay
Topic: Disaster , Theater , Workplace , Cinema , Security , Employee , Movies , Safety
Published: 01/02/2020
ORDER PAPER LIKE THIS
Introduction
Safety and security issues are one of the most emphasized aspects of the day to day living. This is based on the fact that the issues are prerequisite around home, work, and other environments. In addition, it is necessary to ensure that people are aware of the safety measures they can take in case of an accident. This can be done through civil education or by availing posters in areas prone to insecurity so that everyone is aware of the safety measures to take. Management should ensure that everyone is aware of the security conditions surrounding them in their work place. It is important for everyone to be vigilant amid the global increase in insecurity.
Constant inspection
The management should ensure that there is inspection of the people and vehicles accessing the work place. This will ensure that the vehicles accessing the work place are thoroughly inspected. It will also ensure that only the vehicles with the gate pass will access the work place. This will also help to track down any unauthorized persons with malicious intentions. Constant inspection should include ordering all employees to produce their identity cards at the gate. This will ensure that only the authorized persons are granted entry at the work place.
Civil education on security and security
The management should conduct civil education at the work place on security and safety precautions. This will ensure that people are aware of the importance of security at the work place. It also helps to maintain vigilance at the work place. Employees are also well informed on the safety precautions, to take in the event of an accident. This would greatly reduce the number of casualties in case of an accident. This education ensures that all employees are conversant with all buildings. This way, they are able to access all emergency exits in the event of an accident. Employees familiarize themselves with all the safety precautions in their work place. This includes supplying all employees with copies safety rules and precautions. This will ensure that all employees are aware of all the safety precautions that are required to be maintained at the work place.
Installation of safety equipment
Installation of safety equipments is an important safety precaution in a movie theatre. This includes installation of metal detecting gadgets at the entrance. This will ensure that all persons accessing the movie theatre are thoroughly searched and that no one enters the premises with any weapon. Safety equipment that can be installed is fire alarms. This will ensure that everyone is alerted in case of fire in the building. Fire alarms are installed in areas accessible to all people. This will ensure that, in the event of fire, the alarm button is pressed promptly. This will ensure that people are quickly evacuated from the building, reducing the chances of having casualties. Installation of fire extinguishers in the movie theatre is also important. This will ensure that in case of fire break out it is easily put out. A movie theatre should also have enough emergency exits. This will ensure that, in case of an accident, people are quickly evacuated from the building. A movie theatre should also have a safety notice board where all safety rules and security awareness notices are put. This will ensure that everyone is aware of all the safety precautions to take. It will also notify people of any security threats.
Works Cited
Hilliard Davidson High School Theatre. (2012). Technical Theatre Safety/Policy Sheet. Retrieved from Davidson Theatre: http://davidsontheatre.com/Tech Handbook HM Government. (2006). Fire Safety Risk Assessment: Theatrers, Cinemas and Similar Premises. London: Info4local.gov.uk. Retrieved from http://www.communities.gov.uk/publications/fire/firesafetyrisk8

Cite this page
Share with friends using:
Removal Request

Finished papers: 219
This paper is created by writer with
ID 253633924
If you want your paper to be:
Well-researched, fact-checked, and accurate
Original, fresh, based on current data
Eloquently written and immaculately formatted
275 words = 1 page double-spaced

Get your papers done by pros!
Other Pages
Failure personal statements, keystone case studies, tilt case studies, pod case studies, fresco case studies, dwelling case studies, mouton case studies, affirmation case studies, how critical theory improves the study of international politics research paper example, example of essay on learning from the past in building a strong future the shaw memorial, goals report examples, engineering professions essay sample, example of research paper on mental disorders, example of consequences dissertation chapter, sociology course work sample, case study on trends in health information systems and applications, good power portrayal in the play ma raineys black bottom literature review example, free essay on western civilization breeds intolerance, should schools ban junk food essays example, free creative writing on a cambodian learning english in the united states of america, good example of essay on reading reaction, sample essay on vietnam war on american culture, other essays examples, hamlet study questions course work sample, good art research paper example, good islamic art article review example, uninhabitability essays, endocytic essays, fendt essays, enteroscopy essays, cathodic essays, condylar essays, ercp essays, amanitin essays, cormatrix essays, cryopreserved essays, betapropiolactone essays, bileaflet essays, brugada essays, atrioventricular essays, bellocq essays, catecholaminergic essays.
Password recovery email has been sent to [email protected]
Use your new password to log in
You are not register!
By clicking Register, you agree to our Terms of Service and that you have read our Privacy Policy .
Now you can download documents directly to your device!
Check your email! An email with your password has already been sent to you! Now you can download documents directly to your device.
or Use the QR code to Save this Paper to Your Phone
The sample is NOT original!
Short on a deadline?
Don't waste time. Get help with 11% off using code - GETWOWED
No, thanks! I'm fine with missing my deadline
Beyond Intractability

The Hyper-Polarization Challenge to the Conflict Resolution Field: A Joint BI/CRQ Discussion BI and the Conflict Resolution Quarterly invite you to participate in an online exploration of what those with conflict and peacebuilding expertise can do to help defend liberal democracies and encourage them live up to their ideals.
Follow BI and the Hyper-Polarization Discussion on BI's New Substack Newsletter .
Hyper-Polarization, COVID, Racism, and the Constructive Conflict Initiative Read about (and contribute to) the Constructive Conflict Initiative and its associated Blog —our effort to assemble what we collectively know about how to move beyond our hyperpolarized politics and start solving society's problems.
By Omario Kanji
October 2003
In the context of conflict resolution, the definition of "security" depends on one's perspective. At the simplest level, security may be defined as "the quality or state of being secure," "freedom from danger," or "freedom from fear or anxiety." Of the many other levels on which one can analyze security, the most relevant here are individual, group, regional, national, and global. Our task is then relatively simple; we consider how security is defined at these different levels. What emerges is a framework upon which security agreements are constructed and implemented.
Individual Security
On the individual level, security is most often understood as safety. This safety includes freedom from harm, whether physical or psychological. Threats to an individual's security can produce the fear or anxiety mentioned above. The United Nations Universal Declaration of Human Rights states that all people are entitled to "security of person." This declaration reinforces the concept of freedom from physical and psychological harm. Yet, what measures will be taken to protect an individual from harm? The most common forms of protection are legal structures that protect individuals from threats to their security. These include, but are not limited to, laws against murder, sex crimes, bodily harm, theft, and psychological harm such as coercion. The state assumes responsibility for constructing and implementing these legal regulations. In addition, security can be related to one's ability to attain the fundamental physical needs of a home, food, and socio-economic needs such as a job. The concept of individual security can therefore be linked to an individual's perception of her or his standard of living. The individual may thus equate security with a high standard of living.
Group Security
Discussing regional security requires us to first define the extent of the "region." Since we have placed the regional beneath the national level in this hierarchy, we are speaking of a physical area within a nation, which could be a collection of provinces, cities, or states. If there were certain religious, national, or ethnic groups that dominated a region, we would still speak of their security at the group level. What is regional security, then?
The simplest concept of security at the regional level could be economic, implying protection of regional interests. Perhaps a regional association with, or ownership of, a valued resource could provoke desires for security, and the responsibility for protecting that security would rest on the region. For example, labor or trade unions perform this function. Other notions of security at this level could be to maintain a certain standard of living. In this realm, members of a regional group might want to protect themselves from mass immigration, which could occur due to the region's coveted resources. The region might seek to ensure its security by campaigning against this immigration. Threats to security are often cited here, usually connected to issues of lowered living standards. On a more subtle level, religious, national, or ethnic groups may shrewdly promote their interests under the guise of regional security, and may elevate their group security to a regional priority level.
National Security
The definition of security at the group level shares many similarities with the definition of individual security; as the individual expects to have security of person, so does the group. But at the group level, an important aspect of security is freedom from discrimination . While an individual certainly can be mistreated for her or his affiliation with a religious, national, or ethnic group, this mistreatment is more obvious and perhaps more successfully prevented when an entire group is subject to the same mistreatment. We can define the group, i.e., why that group IS a group. Is it due to the similar nationality of its members? Are they a group because they share similar religious beliefs? Whatever the reason, group security may be interpreted as safety from threats to the group's identity . As with ensuring individual security, laws help ensure group security, although laws can also be discriminatory, which is actually one source of intractable conflict.
Regional Security
The national level of security is probably the most often examined and contentious definition of security. The nation-state often assumes the role of guarantor for individual security, group security, and perhaps regional security; for example, agricultural subsidies or steel tariffs are one way in which a nation-state protects a region within its boundaries from a foreign threat.
After ensuring individual, group, and regional security, how does the state define its own security? Lasso and Gonzalez state that "the entirety of conditions -- political, economic, military, social, and cultural -- necessary to guarantee the sovereignty, independence, and promotion of national interest..."[1] defines security. We can then ask what threatens those five conditions. Security from the military viewpoint is highly visible, and a nation will act when it is threatened militarily. Economic threats can also be simply defined, although domestic protectionism can often clash with international trade agreements signed by the same nation. A nation's claim that its protectionism helps ensure national economic security can cause international uproar. (For example, see the essay on Development and Conflict .)
Tension is introduced when a nation defines what in particular guarantees its political, socio-economic, and cultural security. For example, actions undertaken to protect cultures can easily be interpreted as discriminatory or racist. Cultural security is especially difficult to define and protect in heterogeneous, democratic societies such as the United States.
Socio-economic security can also assume controversial definitions and interpretations. Surely a rapidly aging population can threaten socio-economic security. A further question is what measures the state will undertake to solve the problem. Tension can again be introduced if the state or the society chooses to blame a specific group for the threat to socio-economic security. Here, security definitions are at odds since the state is protecting its own security by threatening a group's security.
Perhaps the most ambiguous aspect of security is that of political security, which may be very broadly defined. Often, a nation will react to threats to its political philosophies, as well as threats to its culture, society, or economy. The term "national security" has recently been used to justify "security" procedures within the United States as well as military action outside its borders. This widens the parameters for national security definitions, and implies a wide range of actions available to a nation.
Global Security
Global security is a relatively new concept, and conjures up images of organizations such as the United Nations. Global security, however, may be undermined by national security concerns; if one nation feels threatened by another, then global security cannot exist since members of the world are in disagreement. Global security is also undermined by negative judgment by one nation of another's philosophy of government. If nation A decides that nation B's governing methods are wrong, nation A will not submit to a global authority that allows nation B's methods to continue. Global security is thus a weak concept, since it assumes a supranational entity to whose judgment nations would yield in matters of disagreement. This is obviously a far-fetched goal, which is unlikely to be realized in the near future. As resources such as land, water, and oil are increasingly coveted by nations, global security has little chance to emerge as a durable concept in international relations.[2]
The Security Dilemma
At the national and global level, providing security creates a dilemma. It is generally thought that security is provided with a strong military that can deter attack. Yet, the development of military strength can be seen as a threat by the other side, which then increases its own military investment. This, then, actually decreases both sides' security, rather than increasing it. Security is actually a positive-feedback system. The more security I feel, the more secure my opponent(s) will feel, because I won't have to arm myself against them. But the less secure I feel, the more I will arm, and the less secure my opponent will feel as well. This security dilemma is what fueled the Cold War, the nuclear arms race, and indeed, it is much of what is fueling the conflict between Israel and the Palestinians, Indians and Pakistanis and North and South Korea. (There are other factors in all of those conflicts as well, but security is a big issue.)[3]
The concept of security, on all levels, is related to basic concepts of human psychology. If threatened, people will react and take necessary defensive measures. At the individual level, one can sometimes ward off threats by exercising caution in his or her daily life. He or she may arrange additional security measures, such as alarm systems, weapons, or perhaps changing residences. This same type of reaction may occur on the group or regional level. On the national and global levels, more formal structures of defense and security agreements exist. Nations might activate defense systems to react to overt threats, but this can threaten the other side, thereby reducing security, rather than increasing it. Furthermore, they might cooperate to create security agreements such as NATO, which foster cooperation and collaborative defense and security measures in the face of a perceived threat.
[1] L.H. Lasso, G. Gonzalez, in B.M. Bagley, S.A. Quezada, Eds. Mexico in Search of Security, (University of Miami Press, 1993), 4. < http://www.amazon.com/Mexico-Security-Bruce-M-Bagley/dp/1560006862 >; see also Brian J. Bow, and Arturo Santa Cruz, The State and Security in Mexico: Transformation and Crisis in Regional Perspective (Routledge, 2012). < http://books.google.com/books?id=Am9r_7ftVdoC >.
[2]. For further discussion of global security, including applications to the War in Iraq, Hurricane Katrina, and Weapons of Mass Destruction (WMDs), see: Peter Hough, Understanding Global Security , (Routledge, 2008). < http://books.google.com/books?id=c_B-qty22m8C >.
[3] This paragraph was added by Heidi Burgess. It was not part of the author's original essay, but as editor, I took the liberty of adding it.
Use the following to cite this article: Kanji, Omario. "Security." Beyond Intractability . Eds. Guy Burgess and Heidi Burgess. Conflict Information Consortium, University of Colorado, Boulder. Posted: October 2003 < http://www.beyondintractability.org/essay/security >.
Additional Resources
The intractable conflict challenge.

Our inability to constructively handle intractable conflict is the most serious, and the most neglected, problem facing humanity. Solving today's tough problems depends upon finding better ways of dealing with these conflicts. More...
Selected Recent BI Posts Including Hyper-Polarization Posts

- Massively Parallel Peace and Democracy Building Roles - Part 4 -- The last in a four-part series of MPP roles looking at those who help balance power so that everyone in society is treated fairly, and those who try to defend democracy from those who would destroy it.
- Massively Parallel Peace and Democracy Building Links for the Week of May 19, 2024 -- Another in our weekly set of links from readers, our colleagues, and others with important ideas for our field.
- Crisis, Contradiction, Certainty, and Contempt -- Columbia Professor Peter Coleman, an expert on intractable conflict, reflects on the intractable conflict occurring on his own campus, suggesting "ways out" that would be better for everyone.
Get the Newsletter Check Out Our Quick Start Guide
Educators Consider a low-cost BI-based custom text .
Constructive Conflict Initiative

Join Us in calling for a dramatic expansion of efforts to limit the destructiveness of intractable conflict.
Things You Can Do to Help Ideas
Practical things we can all do to limit the destructive conflicts threatening our future.
Conflict Frontiers
A free, open, online seminar exploring new approaches for addressing difficult and intractable conflicts. Major topic areas include:
Scale, Complexity, & Intractability
Massively Parallel Peacebuilding
Authoritarian Populism
Constructive Confrontation
Conflict Fundamentals
An look at to the fundamental building blocks of the peace and conflict field covering both “tractable” and intractable conflict.
Beyond Intractability / CRInfo Knowledge Base

Home / Browse | Essays | Search | About
BI in Context
Links to thought-provoking articles exploring the larger, societal dimension of intractability.
Colleague Activities
Information about interesting conflict and peacebuilding efforts.
Disclaimer: All opinions expressed are those of the authors and do not necessarily reflect those of Beyond Intractability or the Conflict Information Consortium.
Beyond Intractability
Unless otherwise noted on individual pages, all content is... Copyright © 2003-2022 The Beyond Intractability Project c/o the Conflict Information Consortium All rights reserved. Content may not be reproduced without prior written permission.
Guidelines for Using Beyond Intractability resources.
Citing Beyond Intractability resources.
Photo Credits for Homepage, Sidebars, and Landing Pages
Contact Beyond Intractability Privacy Policy The Beyond Intractability Knowledge Base Project Guy Burgess and Heidi Burgess , Co-Directors and Editors c/o Conflict Information Consortium Mailing Address: Beyond Intractability, #1188, 1601 29th St. Suite 1292, Boulder CO 80301, USA Contact Form
Powered by Drupal
production_1
More From Forbes
Will llm adoption demand more stringent data security measures.
- Share to Facebook
- Share to Twitter
- Share to Linkedin
the contrast between privacy concerns and data collection
The rise of large language models (LLMs) has significantly changed how we communicate, conduct research, and enhance our productivity, ultimately transforming society as we know it. LLMs are exceptionally skilled in natural language understanding and generating language that seems more accurate and human-like than their predecessor. However, they also pose new risks to data privacy and the security of personal information. Compared to narrow AI systems with LLMs, more complex issues like sophisticated phishing attacks, manipulation of online content, and breaches in privacy controls are emerging.
A recent study by MixMode analyzed data from the National Cyber Security Index (NCSI), the Global Cybersecurity Index (GCI), the Cybersecurity Exposure Index (CEI), and findings from Comparitech to assess cyber safety across 70 countries. Findings indicate that countries with the most robust cybersecurity infrastructures include Finland, Norway, and Denmark. The United Kingdom, Sweden, Japan, and the United States also maintain strong defenses against cyber threats. While the USA scores highest on the Global Cybersecurity Index, it only ranks ninth in overall safety. Similarly, Canada, with a strong Global Cybersecurity Index, ranks tenth overall in safety.
MixMode Global Cybercrime Report 20204
Worrisome are the countries that pose the highest risk for cyber-attacks. The threat exposure in these emerging countries includes the economic impact of potential financial losses for both public and private sectors, the threat to national security systems, particularly their vulnerability to cyber espionage, and attacks on critical infrastructure and national safety. These countries, more prone to data breaches, face the exposure of highly sensitive information, leading to identity theft, financial fraud, increased sources of cybercrime, and eroded investor and consumer confidence.
Global Cybercrime report 2024
NSA Warns iPhone And Android Users To Turn It Off And On Again
Donald trump 300 million poorer after guilty verdict as truth social stock sinks, trump still faces 54 more felony charges after hush money verdict.
With the rise of LLM adoption, the U.S. Biden administration reauthorized Section 702 of FISA into law in April, extending warrantless surveillance and impacting U.S. civil liberties amid widespread data collection concerns, further complicating the government’s role in creating safeguards and ensuring trust around artificial intelligence.
To discuss the vulnerabilities associated with large language models and the ramifications of the new law on individuals' data privacy rights and civil liberties, especially concerning emerging tech companies, I met with two experts: Saima Fancy, a data privacy expert and former privacy engineer at Twitter/X, and Sahil Agarwal, CEO of Enkrypt AI , an end-to-end solution for generative AI security.
The Perpetual Demand for Data
Between 2022 and 2023, there was a 20% increase in data breaches . Publicly reported data compromises rose by 78% year-over-year. The average cost of a data breach hit an all-time high last year at $4.45 million, marking a 15% increase from three years ago. Notably, 90% of organizations experienced at least one third-party vendor suffering a data breach. Globally, the number of victims in 2023 doubled compared to 2022.
Saima Fancy explained that the driving force behind these issues is the intense desire for data collection by organizations, often resulting in reckless behavior. Technologies like OpenAI, she indicated, are launched prematurely to maximize data collection. "These technologies are often released too early by design," she noted, "to accumulate as much data as possible. While they appear free, they're not truly free because you're providing your personal data, essential for training their models."
She added that organizations could have opted to legally acquire data and train their models in a structured manner. "Many tools were ready but weren't launched immediately because they were undergoing rigorous sandboxing and validation testing," she explained, noting the rush to release new technologies isn’t always deliberate but often fueled by enthusiasm and the pressure to innovate, which can lead to unintended consequences. "There's a race to release new technologies, which can inadvertently cause harm. It's often just a case of 'let's release it and see what happens.'"
Fancy also highlighted that many of these tools are rarely stable in their nascent form, and developers will fine-tune the models over time. "This means the initial outputs might not be accurate or what users expect. Despite this ongoing learning phase, these tools are already live on a global scale," she added.
LLMs and the Indiscriminate Scraping of PII
Given that LLMs have been developed from data gathered indiscriminately across web properties there's a risk of exposing sensitive details such as credentials, API keys, and other confidential information. Fancy believes that society’s susceptibility to security threats is unprecedented, observing, "The public is undoubtedly more vulnerable now than ever before. We're in the fifth industrial revolution, where generative AI is a relatively new phenomenon. As these tools are released publicly without adequate user education, the risk skyrockets. People input sensitive data like clinical notes into tools like chat GPT, not realizing that once their personal information is entered, they’re used to train models. This can lead to their data being potentially re-identified if they’re not properly protected."
She emphasized the risk extends beyond individual users to corporations as well, particularly if employees are not properly trained in using these technologies, including prompt engineering. "The vulnerability is extremely high, and for corporations, the risk is even greater because they risk losing public trust and they are not immune to data breaches. As these tools evolve, so do the techniques of malicious actors, who use them to refine their ransomware and phishing attacks, making these threats more sophisticated and costly to mitigate."
Today we are witnessing the swift emergence of regulation through the EU AI Act , the most comprehensive legislation on AI and the Biden Executive Order on Safe Secure and Trustworthy AI in late 2023. Sahil Agarwal, CEO of Enkrypt AI , points out, “Since the introduction of ChatGPT, there has been a significant increase in awareness among the public, legislators, and companies about the potential risks of AI. This heightened awareness has surpassed much of what we've seen over the past decade, highlighting both the potential and the dangers of AI technologies.”
He adds that the regulatory mandates are clear and if you’re handling customer data or distributing tools you need to be mindful and ensure these tools aren’t used for harmful purposes. As well, the penalties don’t randomly apply to any startup working with generative AI technology, instead he continues, “ ...they’re targeted at specific stage of a company’s development and certain types of general-purpose AI technologies, emphasizing, they’re there to guide more responsible innovation.”
Cyber Attacks are More Advanced
Today’s AI technology can enable highly convincing phishing emails or messages that may appear legitimate and trick individuals into revealing sensitive information. In addition, LLMs have enabled attackers to conduct more effective social engineering attacks by generating personalized messages or responses based on more extensive knowledge of the target’s online activity, their preferences and behaviors. We’ve also seen a rise in malicious content as LLMs can be used to generate fake news articles or reviews, which, in turn, can spread misinformation, manipulate public opinion or propagate malware. The speed at which LLMS can also automate certain stages of cyber-attacks by generating targeted queries, crafting exploit payloads, or bypassing security measures, is making it increasingly difficult to identify these before they’re implemented. In addition, the rise of adversarial networks can now manipulate the inputs to generate outputs with intention to deceive spam filters, fraud and malware detection systems.
Fancy explained that both personal and commercial levels are affected and that many systems are vulnerable due to outdated technology or inadequate security measures during transitions to cloud or hybrid systems. Startups often overlook security and privacy measures, which is a clear oversight, revealing, "From a privacy-by-design perspective, being proactive rather than reactive is crucial. Starting with security measures early in the software development life cycle is essential to prevent sophisticated attacks that can severely impact institutions like banks and hospitals."
She emphasized the naive thinking many startups have, believing they’re immune to attacks adding, "But what LLMs have done is dramatically broaden the attack landscape, making it easier for malicious actors to observe and eventually exploit vulnerabilities in a company's systems. It’s crucial for businesses, especially startups, to prioritize funding for security measures from the outset to protect against these threats. Regulations are also becoming more stringent globally, which could have severe repercussions for non-compliance."
Agarwal revealed his team has uncovered some serious safety issues and vulnerabilities with the top LLMs and agrees that perhaps these models are not ready for prime time. “Traditionally, cybersecurity and standard Data Loss Prevention (DLP) solutions have focused on monitoring specific keywords or personally identifiable information (PII) exiting the network. However, with the advent of generative AI, the landscape has shifted towards extensive in-context data processing.” He states that DLPs now should be tuned to the context of activities or potential security threats occurring, rather than just monitoring data outflows.
Agarwal added the need for safe adoption of these updated AI systems has yet to develop standard practices mainly because of the nascency of LLMs, “While many discuss the concept of responsible adoption, the specifics of implementing, measuring risks, and safeguarding against potential issues when using large language models and other generative technologies in businesses have not been fully established.
The Irony of AI Safety Amid the Reauthorization of Section 702, FISA into Law
The recent passage of Section 702 of the Foreign Intelligence Surveillance Act (FISA) into law has created this dichotomy that exists within the same U.S. government that has also mandated the development of trustworthy artificial intelligence. The law was established in 1978 to spy on foreign individuals, underwent significant changes after 9/11, allowing the broad sweeping of U.S. citizens' information without a warrant. This practice, known as " incidental collection ," meant that if such information was obtained, it would still be allowed. Key events include the 2013 revelations by NSA whistleblower Edward Snowden, who exposed the PRISM program and the involvement of major tech companies like Google and Facebook (at the time) in giving the government unfettered access to user data. This bulk collection of U.S. citizens' emails, mobile communications, and phone records was later ruled unconstitutional. Despite added provisions to increase oversight and minimize incidental collection, the law was renewed without amendments, resulting in more powerful surveillance capabilities than those considered during the initial AI hype eight years ago.
Fancy expressed the regrettable development of this renewal for companies that collect data and create models. “With laws like this being renewed for another two years, the implications are huge. Federal governments can compel companies to hand over data on a span of the population, which is essentially surveillance at another level. This is scary for regular folks and is justified under the guise of world state protection. It may seem necessary at face value, but it opens doors wide for abuse on a larger scale. It is unfortunate.”
While it may seem there is no way out of this mandate, companies like Signal and Proton claim they cannot access user data due to end-to-end encryption technology, which allows only users access to their own information. Could this absolve companies of their responsibility amidst the renewed government compliance? Fancy acknowledged, “There are data vaults where customers can store their data, and the company only works with the metadata. These vaults are locked and encrypted, accessible only by the customer. Blockchain technology is another method, where users hold the keys to their data. These methods can protect user data, but they also limit the company's ability to monetize the data. Nonetheless, they are valid use cases for protecting user information.”
Startups Need to be Proactive: Data Privacy and Security Should not be an Afterthought
Agarwal is adamant that innovation should not come at a human cost. He argues that startups creating technologies with potential adverse effects on customers need to integrate ethical guidelines, safety, security and reliability measures from the early development stages, adding, “We cannot adopt a wait-and-see approach, scaling up technology like GPT-4o to widespread use and only then addressing issues reactively. It's not sufficient to start implementing safety measures only after noticing misuse. Proactive incorporation of these safeguards is crucial to prevent harm and ensure responsible use from the start.”
Fancy emphasized that many out-of-the-box tools are available in the market to help companies implement new security measures within their cloud infrastructure. Whether it's a private or public cloud, these tools can manage data sets, create their own cloud classifications, categorize and bucket data for protection, and constantly monitor for infractions, loopholes, or openings within the cloud structure. However, she acknowledged that these tools are not readily affordable and require investment upfront as data is being brought in, whether unstructured or structured. As per Fancy, “It's crucial for companies to know where their data is located, as many big data companies admit to not knowing which data centers their data resides in, posing a significant risk.” Fancy also pointed out the importance of encryption, both for data at rest and in transit. Often, companies focus only on encrypting data at rest, however she points out, “...infractions frequently occur when data is traveling between data centers or from a desktop to a data center. You've got to make sure the encryption is happening there as well.”
She highlighted that we are in a favorable time of technological evolution, with many tools available to enhance data security. While these tools' costs are decreasing, it's still necessary for companies to allocate funds for privacy and security measures right from the start. "As your funding is coming in, you've got to set some money aside to be mindful of doing that," Fancy stated. Unlike major companies that can absorb the impact of regulatory actions, small startups must be proactive in their security measures to avoid severe consequences.
Startups, however, can initiate other measures to protect data privacy and security. Fancy suggests smaller startups should practice data minimization, ”and practice collecting data for the purpose that the data was collected. They can put robust consent management measures and audit logging in place that allows startups to manage logs effectively and monitor access controls to see who has access to the data.”
Fancy noted that there are healthy mechanisms and practices within data ecosystems that startups can adopt to enhance their security measures. She stated, “These practices can be a viable alternative for startups that cannot afford comprehensive security tools initially.” Startups could start with smaller features of these tools and expand their capabilities as their funds grow. By adopting these practical measures, startups can effectively enhance their data security and privacy protection without incurring significant initial costs.
Ethics is Now Mainstream
Where technology, compliance and brand risk collide is within the realization that the most compelling technology to date, brought to the masses by Open AI, the darling of large language models, heavily venture capital backed –is still flawed . Agarwal reveals when he recently spoke to a principle from private equity firm, they were experiencing a major scandal when articles they produced were leaked due to their decision to remove certain safeguards. He stressed, “This incident highlights that ethical considerations are not just about morality; they've become crucial to maintaining a brand's integrity. Companies are motivated to uphold ethical standards not solely for altruism but also to mitigate brand risks. This need for robust controls is why topics like generative AI security are gaining prominence. At events like the RSA conference, you'll find that one of the central themes is either developing security solutions for AI or employing AI to enhance security measures.”
Data Security Needs to be in Lock-Step with Advancing AI
The reauthorization of Section 702 of FISA underscores a significant tension between the pursuit of advanced AI technologies and the imperative of safeguarding data privacy. As large language models (LLMs) become increasingly integrated into various aspects of our lives, the potential for sophisticated cyber-attacks and the erosion of individual privacy grows. Saima Fancy and Sahil Agarwal emphasize the urgent need for robust cybersecurity measures, ethical guidelines, and proactive regulatory compliance to mitigate these risks.
Promoting AI innovation while ensuring data privacy and security presents a complex challenge prompting organizations to balance the benefits of cutting-edge technologies with the responsibility of protecting sensitive information. Ensuring AI safety, maintaining public trust, and adhering to evolving regulation and security standards are essential to responsible innovation. It’s early day but we’re already seeing organizations take the crucial steps to prioritize security and ethical considerations to foster a safer and more trustworthy world.
- Editorial Standards
- Reprints & Permissions
Join The Conversation
One Community. Many Voices. Create a free account to share your thoughts.
Forbes Community Guidelines
Our community is about connecting people through open and thoughtful conversations. We want our readers to share their views and exchange ideas and facts in a safe space.
In order to do so, please follow the posting rules in our site's Terms of Service. We've summarized some of those key rules below. Simply put, keep it civil.
Your post will be rejected if we notice that it seems to contain:
- False or intentionally out-of-context or misleading information
- Insults, profanity, incoherent, obscene or inflammatory language or threats of any kind
- Attacks on the identity of other commenters or the article's author
- Content that otherwise violates our site's terms.
User accounts will be blocked if we notice or believe that users are engaged in:
- Continuous attempts to re-post comments that have been previously moderated/rejected
- Racist, sexist, homophobic or other discriminatory comments
- Attempts or tactics that put the site security at risk
- Actions that otherwise violate our site's terms.
So, how can you be a power user?
- Stay on topic and share your insights
- Feel free to be clear and thoughtful to get your point across
- ‘Like’ or ‘Dislike’ to show your point of view.
- Protect your community.
- Use the report tool to alert us when someone breaks the rules.
Thanks for reading our community guidelines. Please read the full list of posting rules found in our site's Terms of Service.
- My View My View
- Following Following
- Saved Saved
The SEC's new cybersecurity disclosure rules decoded: what they mean for investors
- Medium Text

- Company Bernstein Litowitz Berger & Grossmann LLP Follow
The SEC's new cybersecurity disclosure rules
The sec's new disclosure rules in action, sec takes action for failures to disclose cyber incidents.
Sign up here.

Jonathan D. Uslaner is a partner at Bernstein Litowitz Berger & Grossmann LLP, where he prosecutes class and direct actions on behalf of institutional investor clients. He is based in the firm's Los Angeles office and can be reached at [email protected].

Jimmy Brunetto is an associate in the New York office of the firm, where he represents institutional investors in shareholder litigation. He can be reached at [email protected].
Read Next / Editor's Picks

Industry Insight Chevron

David Thomas

Mike Scarcella, David Thomas

Karen Sloan

Henry Engler

IMAGES
VIDEO
COMMENTS
Cyber Security Essay. Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today's world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software.
This analysis relies on data collected by the federal government to assess the security measures that public K-12 schools in the United States have employed in recent years, as well as how the adoption of these protocols varies by type of school, region and other factors.
Today, nearly 100% of schools serving 12- to 18-year-olds use at least one safety or security measure. [4] This includes locked doors, security cameras, hallway supervision, controlled building access, metal detectors, and locker checks. However, use of these measures varies by factors such as the school's population and location.
We will write a custom essay on your topic. As Hong et al. (2003) cautions, "security management is core to ensuring very long-phrase sustainability of any company, and the need for people educated in this field is developing each and every day". As far as human security is concerned, "employers have an obligation to shield the people ...
Cryptographic Algorithms: The Use in Cyber Security. Cryptographic protection of a system depends on two factors, 1) the strength of the keys and effectiveness of associated protocols, and 2) protection of said keys via key management. Cybersecurity Implementation Plan for PBI-FS.
Campus Security Measures The impact of mass shooting at Virginia Polytechnic Institute and State University (Virginia Tech) on April 16, 2007 continues to be felt across the United States and internationally due to a massacre that killed 27 students and five faculty members. Following the weeks after the shooting, the university conducted several extensive reviews and analysis to better ...
Learn why cyber security is crucial in today's digital age and how it protects our sensitive information from hackers and cyber attacks. Explore the importance of implementing effective cyber security measures and the potential risks and consequences of neglecting them. Discover the role of cyber security in safeguarding personal privacy, business operations, and national security.
school grounds. However, many of these security measures were implemented with little to no consultation of the empirical literature. This failure to enact evidence-based responses has had fiscal and latent consequences that are only now being discovered. This essay seeks to fill that void by examining the empirical evidence surround-
In their empirical study [3], Harrison and White utilize data gathered from the 2009 National Collegiate Cyber Defense Competition to validate the effectiveness of common security measures found ...
It involves managing both external and internal threats and managing the responses to those threats. Security management also plays a role in responses to damage and disaster. The role applies to any sector: government, private, and public. However, the primary definition of security management tends to focus on the corporate sector.
This essay seeks to fill that void by examining the empirical evidence surrounding common security measures enacted in response to well-publicized school shootings and calling for the use of an ...
200 Words Essay On Cyber Security. School students are the future of our society, and it's important to teach them the importance of cyber security from an early age. Cyber security is an ever-increasing problem in our digital world, and it's up to us to ensure that our students are aware of the risks and dangers that come with the internet.
This essay seeks to fill that void by examining the empirical evidence surrounding common security measures enacted in response to well-publicized school shootings and calling for the use of an evidence-based approach to school safety.
Effective computer security encompasses physical security measures, minimizing the risk of errors, failures, or loss through resilient backup strategies, implementing user authentication, and encrypting sensitive files. ... Students looking for free, top-notch essay and term paper samples on various topics. Additional materials, such as the ...
Security Measures Essays. Risks and Business Continuity Impacts of the Removal of the Indian Ocean High-Risk Area on the Shipping Industry: A Literature Review. The early literature on Somalian piracy gives much attention to the causes and origin of Somalian-based piracy (Duda & Szubrycht, 2009; Potgieter, 2008), both acknowledging that Somalia ...
Challenges in Cyber Security. However, the complexity and sophistication of cyber threats are growing at an alarming pace. Cybercriminals are using advanced techniques, such as AI and machine learning, to bypass traditional security measures. This necessitates the development of more robust, adaptive cybersecurity strategies.
Hackers and Security Measures. A diffuse group of people often called "hackers" has been characterised as unethical, irresponsible, and a serious danger to society for actions related to breaking into computer systems. In this essay I try to construct a picture of what is and includes a computer crime as well as a portray of hackers, their ...
Essays on Security Measures. 152 samples on this topic. To some college goers, writing Security Measures papers comes easy; others need the help of various kinds. The WowEssays.com database includes expertly crafted sample essays on Security Measures and relevant issues. Most definitely, among all those Security Measures essay examples, you ...
In law, people argue a lot about whether protecting someone's privacy or keeping the country safe is more important. This argument has been a central topic of legal talks for many years, with experts and decision-makers having different opinions on the middle ground.
These security issues affect all aspects of the supply and logistics chain from the producer to the consumer. The government has developed a number of strategies that are geared towards assisting government agencies identify and isolate threats in time. With the threat of terrorism growing with each passing day, the transportation and logistics ...
Data Security Measures Essays. The Problems in the Organization. Apple Inc. It has had a few fulfillment with its Human Resource Information System (HRIS); however, the agency has also needed to address a few hurdles and problems in this area (Mallin & Finkle 2011). These problems have impacted certain factors of HR management and require ...
Introduction. Safety and security issues are one of the most emphasized aspects of the day to day living. This is based on the fact that the issues are prerequisite around home, work, and other environments. In addition, it is necessary to ensure that people are aware of the safety measures they can take in case of an accident.
Global security - introductory essay. Welcome to Global Security: Health, Science, and Policy. This timely new journal encompasses a wide range of topics related to transnational threats to humankind, with an emphasis on public health repercussions. It examines both the nature of such threats and the means to mitigate and prevent them.
An overview of risk analysis should cover the following activities: Determining the value of the physical assets. Determining the vulnerabilities and threats for each asset. Evaluating the severity of the threat. Evaluating the fallout from the possibility of a threat coming to fruition. Implementation of possible preventative measures.
October 2003. In the context of conflict resolution, the definition of "security" depends on one's perspective. At the simplest level, security may be defined as "the quality or state of being secure," "freedom from danger," or "freedom from fear or anxiety." Of the many other levels on which one can analyze security, the most relevant here are ...
APTs are difficult to detect and counter, as they use advanced techniques and tools to evade security measures. For example, in February 2021, a cyber security firm called RedEcho revealed that a China-linked APT group had targeted 10 entities in India's power sector, with malware that could potentially cause power outages.
Between 2022 and 2023, there was a 20% increase in data breaches. Publicly reported data compromises rose by 78% year-over-year. The average cost of a data breach hit an all-time high last year at ...
A guide to Tenable's NIS2 risk management capabilities for the Risk Manager, the Vulnerability Manager and the OT Security ManagerThe NIS2 (Network and Information Systems Directive 2022/2555) is concerned with implementing risk-based security measures. These are applied differently depending on your role within your organisation.How can you ensure you have a robust risk governance program ...
The SEC's new disclosure rules also emphasize the importance of "cyber-hygiene." Specifically, they require public companies to disclose in their annual reports, filed with the SEC on Form 10-K ...
A guide to Tenable's NIS2 risk management capabilities for the Risk Manager, the Vulnerability Manager and the OT Security ManagerThe NIS2 (Network and Information Systems Directive 2022/2555) is concerned with implementing risk-based security measures. These are applied differently depending on your role within your organisation.How can you ensure you have a robust risk governance program ...