- Newsletters
- Account Activating this button will toggle the display of additional content Account Sign out

Internet Safety Is the New Internet Freedom
And it comes with a cost..
On Jan. 25, 2011, protests erupted across Egypt against the regime of Hosni Mubarak. As an estimated 2 million people protested at Tahrir Square in Cairo, the government tried to control the narrative by first blocking Twitter and then Facebook. Within a couple of days, Egypt’s telecom services would go dark. According to reports at the time, “the shutdown caused a 90 percent drop in data traffic to and from Egypt, crippling an important communications tool used by antigovernment protesters and their supporters to organize and to spread their message.”
Egypt’s digital shutdown sent shock waves across the world , leading people to one conclusion: Internet freedom was under threat. In a speech, U.S. Secretary of State Hillary Clinton said that internet freedom “is about whether we live on a planet with one internet, one global community, and a common body of knowledge that benefits and unites us all, or a fragmented planet in which access to information and opportunity is dependent on where we live and the whims of censors.”
A decade later, the picture is quite different—because the world and the internet have both changed dramatically. In 2011, it was Facebook that was celebrated for accelerating Egypt’s awakening ; in 2021, Facebook is vilified for seeming to do little to moderate posts in the world’s most violent countries, or for its struggles to contain insurrectionists’ posts . Today’s internet has become one that calls for safety rather than freedom, and governments are ready to step in, as evidenced by privacy-invading legislation in Canada, Australia, the U.K., and beyond.
Since the Enlightenment, public safety has been seen as the first duty of government. For the government’s guarantee of safety and security, Enlightenment thinkers observed, individuals would abandon the free state of nature. Hobbes wrote about this: “The end for which one man giveth up, and relinquisheth to another, or others, the right of protecting and defending himself by his own power, is the security which he expecteth thereby, of protection and defense from those to whom he doth so relinquish it.” For Enlightenment philosophers, security was central to the concessions people would make for the state.
Fighting misinformation (especially during a pandemic) and extremist content, seeking to expose child abusers who use internet services—all of these issues easily fall under the notion of “public safety,” and they provide the state with justification for intervention. If sovereignty is conditional upon the sovereign’s ability to ensure the safety and security of the people, then the state should have every right to act on any of these issues.
However, in practice, internet safety is opposed to the most fundamental benefits of the internet: empowering citizens, global interconnectedness, and opening new avenues for innovation. Whereas we once sought a more global and open internet, internet safety represents a movement that is inward-looking, fragmented—and often dangerously misguided.
The Online Safety Bill in the United Kingdom is a prime example. Promising to make “ the UK the safest place in the world to be online ,” the broad and unfocused bill contains threats to freedom of expression, privacy, security, and the internet. The bill’s main goal, to fight illegal and harmful content, would be accomplished by imposing a “duty of care” on internet service providers. The duty of care would also extend to users, who could face up to two years in prison for sending messages or posting content that causes “psychological harm” to others . If the bill passes, the U.K. government, in collaboration with the Office of Communication, the bill’s uberregulator, will need to introduce “ codes of practice to specify different levels of the duty of care and liability .” (At the moment, the scope and reach of the duty of care remain unclear.) Furthermore, the bill would ban end-to-end encrypted communication services in the name of safety. Service providers would be criminally liable for the acts of their users if law enforcement agencies do not manage to get access to encrypted communications data. Finally, the Online Safety Bill would justify the criminal prosecution of tech executives who fail to address how their algorithms cause harm. “Remove your harmful algorithms today and you will not be subjected—named individuals—to criminal liability and prosecution,” said U.K. culture secretary Nadine Dorries.
Australia faces a similar situation. Freedom House’s Freedom on the Net 2021 report says that “Internet freedom in Australia [has] regressed” thanks in particular to the passage of its own Online Safety Act. Enacted in June, the legislation introduces a set of “basic online safety expectations” that internet service providers, social media platforms, and other online parties are expected to uphold. These include protecting minors from certain content, responding to user complaints about cyberbullying targeting Australian children and the sharing of nonconsensual content, and removing content that is abusive toward Australians in general.
Finally, in Canada, elections put a temporary pause on a legislative proposal that targets five different categories of harmful content: hate speech, child sexual abuse, terrorism, incitement to violence, and the nonconsensual sharing of intimate images. The main focus is on big platforms (such as Facebook, YouTube, TikTok, and Pornhub), which will be required to take reasonable steps to block such content in Canada; once content has been identified as harmful and/or illegal, it will need to be removed within 24 hours. The act also gives law enforcement agencies discretionary powers “ in identifying public safety threats .” On the Mozilla blog, Owen Bannett writes that “in its proposal that platforms take down more content in ever-shorter periods of time, the government’s approach merely responds to symptoms and not structural causes of online harms. Worse still, the government’s proposal includes some suggested policy ideas that would have the opposite effect of making online spaces healthier and more inclusive.” For instance, Bannett says, “The government’s apparent ‘zero-tolerance’ approach to objectionable content … manifests through the proposal that online services must report instances of ‘potentially criminal content’ to national security agencies. This … will incentivize greater and more invasive monitoring of individuals by platforms (e.g. upload filtering; real-name policies) and have a disparate impact on those individuals and communities who already face structural oppression in the criminal justice system.” The legislation is slated to return under the new government, and there is nothing to indicate it will not pass when it gets reintroduced.
In the name of safety, governments are placing conditions that make it increasingly difficult for internet actors to prioritize security. Encryption is a clear example. Encryption tools constitute important security building blocks and are a sign of a healthy network. So, when government interventions in the name of safety compromise encryption’s integrity, they create islands of insecure networks that will find it difficult to interconnect with secure ones, further fragmenting the internet.
Safety and freedom are not irreconcilable, and they should not be treated as such. Benjamin Franklin famously said , “Those who would give up essential Liberty, to purchase a little temporary Safety, deserve neither Liberty nor Safety.” It is the responsibility of government to find the balance between safety and freedom. In its current application, however, the focus on safety facilitates the creation of central chokepoints that allow the state to intervene. Given that the global nature of the internet is a feature and not a bug, this intervention leads to fragmentation and conflict.
So why, then, is internet safety such a popular idea?
There is a practical reason, and it concerns the market’s failure to self-regulate and effectively address issues of safety. The very companies that were seen as beacons of internet freedom around the world 10 years ago are currently depicted as the causes of an unsafe internet environment. Data leaks , ransomware attacks , a wave of misinformation and disinformation , and various cybersecurity incidents have made us all feel less safe and, often, less free. For instance, earlier this year news broke that the Israeli surveillance company NSO Group was selling hacking software to authoritarian governments around the world to target human rights activists, journalists, politicians, and lawyers. With no solution coming from the market, governments had no option but to intervene, mainly through regulations that perpetuate the tension between safety and freedom. In fact, the Freedom on the Net 2021 report found that “while some democratic governments have made good faith attempts to regulate the technology industry, state intervention in the digital sphere worldwide has contributed to the 11 th consecutive year of global decline in internet freedom.”
No one wants an internet where illegal or harmful acts occur, where networks are accessed without authorization, where phishing and email frauds are rampant, and where sexual abuse and terrorism proliferate. Equally, we should not want an internet that is less global, is insecure, or where basic human rights are not respected. The problem is not with the term internet safety , per se. It is more about the way the phrase is being abused and, often, used as an excuse for control over global communications.
We must observe the way internet safety is used and call out the instances it is abused. The future of the internet might depend on it.
Future Tense is a partnership of Slate , New America , and Arizona State University that examines emerging technologies, public policy, and society.

Essay on Internet Safety
Students are often asked to write an essay on Internet Safety in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Internet Safety
Understanding internet safety.
Internet safety means being secure online. When we use the internet, we should be careful, just like when crossing the road. It’s important to keep personal information private, like your full name, address, and school.
Creating Strong Passwords
A strong password is like a secure lock. It keeps your online information safe. Use a mix of letters, numbers, and symbols. Don’t use easy words like your pet’s name because others might guess it.
Avoiding Strangers Online
On the internet, not everyone is friendly. Some people pretend to be someone else. Never meet up with someone you met online without a trusted adult.
Safe Sharing
Think before you post photos or share your location. Ask yourself if it’s something you’d want everyone to see. Once it’s online, it’s hard to take it back.
Asking for Help
250 words essay on internet safety, what is internet safety.
Internet safety is about being secure online. When we go online, we can talk to friends, play games, and learn new things. But just like we look both ways before crossing the street, we need to be careful on the internet too.
Keeping Personal Information Private
Imagine your personal information is like a secret treasure. You wouldn’t want strangers to find it. Online, don’t share your full name, address, phone number, or school name with people you don’t know. It’s like giving them a map to your treasure.
Strong Passwords
A strong password is like a locked door to your online house. Use a mix of letters, numbers, and symbols to make it hard for others to guess. Don’t use easy passwords like “1234” or “password,” and never share your passwords with anyone except your parents.
Being Kind Online
The internet is a place where you can meet people from all over the world. Always be kind and respectful, just like you would be in person. If someone is mean to you, tell an adult you trust.
Staying Away from Strangers
If a stranger tries to talk to you online, don’t answer them. Tell a parent or teacher right away. Just like in the real world, not everyone online is a friend.
500 Words Essay on Internet Safety
Internet safety is about being protected online. When we use the internet, we share information about ourselves, sometimes without knowing it. It’s like leaving the door to your house open; if you’re not careful, someone you don’t want inside might come in. So, it’s important to keep that door closed and locked by being smart about how we act on the internet.
One key part of staying safe online is to keep your personal information private. This means not telling strangers your full name, where you live, your phone number, or where you go to school. It’s like not telling a person you just met all your secrets. Only share personal details with people and websites you trust, and even then, only when it’s necessary.
Safe Passwords
Be careful what you click.
When you’re online, you’ll see lots of things to click on, like ads or links in emails. But not all of them are safe. Some can be tricks to take your information or put bad software on your computer. This is like picking up a piece of candy from the ground – it’s not a good idea. If something looks strange or too good to be true, it’s best not to click on it.
Online Strangers
Just like in the real world, you might meet people you don’t know on the internet. Be cautious when talking to strangers online. They might not be who they say they are. It’s like talking to someone with a mask on; you can’t be sure of who’s behind it. Never agree to meet someone in person that you’ve only talked to online without a trusted adult.
Using Social Media Wisely
Ask for help.
If something online makes you feel uncomfortable or if you’re not sure if something is safe, ask a trusted adult for help. This could be a parent, teacher, or an older sibling. It’s like when you’re not sure about crossing the street; you ask for someone’s hand.
Remember, being safe on the internet is a lot like being safe in everyday life. By keeping your information to yourself, using strong passwords, being careful about what you click, being cautious with strangers, using social media wisely, and asking for help, you can enjoy all the good things the internet has to offer without worry. Stay alert and stay safe!
That’s it! I hope the essay helped you.
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Youth Internet Safety: Risks, Responses, and Research Recommendations
- Download the paper
- Download the paper (Portuguese)
- Download the paper (Spanish)
Subscribe to the Center for Technology Innovation Newsletter
Adina farrukh , af adina farrukh rebecca sadwick , and rs rebecca sadwick john villasenor john villasenor nonresident senior fellow - governance studies , center for technology innovation.
October 21, 2014
As Internet use by children and teenagers increases, so do concerns about their online safety. Providing a safe environment requires an in-depth understanding of the types and prevalence of online risks young Internet users face, as well as the potential solutions for mitigating risks.
Despite the significant amount of research on these risks, improving child/youth Internet safety remains a challenge. In part, this is because definitions of terms and categories relevant to online safety (such as “cyberbullying”) often vary, making the comparison of statistics and findings among sources imprecise. In addition, there are complex overlaps among different online safety subtopics.
Overall, these factors can make identifying the specific gaps in existing research and knowledge difficult. If these gaps can be better identified and filled, a data-based understanding of issues facing youth could play a key role in driving policy decisions regarding online safety.
In this paper, Adina Farrukh, Rebecca Sadwick and John Villasenor provide:
- an overview of existing online safety research across a wide range of categories
- an analysis of major findings
- an identification of knowledge gaps, and
- a set of recommendations for specific areas of research that can further the policy dialog regarding online safety
Governance Studies
Center for Technology Innovation
Nicol Turner Lee, Jennifer Huddleston , Christopher Wood
January 29, 2024
Nicol Turner Lee, Stephen Balkam, Kara Sundby
November 20, 2023
Ariel Gelrud Shiro, Richard V. Reeves
August 26, 2021

- PUBLICATIONS
- SCRUTINY TOOLBOX
How the internet can harm us, and what can we do about it?
The internet has received much negative news coverage in recent years.

Written by Gianluca Quaglio,
The internet has received much negative news coverage in recent years. Articles focus on major privacy scandals and security breaches, the proliferation of fake news, rampant harmful behaviours like cyber-bullying, cyber-theft, revenge porn, the exchange of child porn and internet predation, internet addiction, and the negative effects of the internet on social relations and social cohesion. Nevertheless, some 87 % of European households have internet access at home, and 65 % use mobile devices to access the internet. Europeans aged 16 to 24 years spend 168 minutes per day on mobile internet, dropping to 30 minutes for 55 to 64-year olds. Around 88 % of 15 to 24-year olds use social media, 80 % on a daily basis.
While the social and economic benefits of the internet cannot be denied, some of these developments can severely affect such European values as equality, respect for human rights and democracy. Technology companies are under increasing pressure to mitigate these harmful effects, and politicians and opinion leaders are advocating drastic measures.
The recently published STOA study on ‘Harmful internet use’ covers the damage associated with internet use on individuals’ health, wellbeing and functioning, and the impact on social structures and institutions. While the study does not attempt to cover all possible societal harm relating to the internet, Part I focuses on one specific cause of harm, internet addiction, and Part II covers a range of harmful effects on individuals and society that are associated with internet use. The report concludes with policy options for their prevention and mitigation.
Other studies have already extensively discussed some harmful effects, and these are already subject to a history of policy actions. These include harm to privacy, harm related to cybersecurity and cybercrime, and damage resulting from digital divides. In contrast, this study covers the less-studied but equally important harmful effects that concern individuals’ health, wellbeing and functioning, the quality of social structures and institutions, and equality and social inclusion.
Internet addiction and problematic internet use
Internet addiction and problematic internet use prevalence rates vary across studies and countries. The noteworthy discrepancy in prevalence estimates has a number of causes, including the different populations studied, as well as the various diagnostic tools and assessment criteria utilised. With this in mind, it appears that roughly 4 % of European adolescents demonstrate a pathological use of the internet that affects their life and health, while 13 % of adolescents engage in maladaptive behaviour when using the internet. Similar numbers are reported for adults.
Part I of the study focuses on generalised internet addiction, online gaming addiction, and online gambling addiction. Clinical presentations, patient profiling, comorbidities, instruments, interventions, and prognoses are different across these three potential addiction disorders. The study states that the individual, cultural and media-use context significantly contributes to the experience and severity of internet addiction.
The study proposes a set of preventive actions, and evidence to support future policies . It states that offering information, screening tools and campaigns to students in secondary schools and at universities regarding internet-use-related addiction problems can help, especially regarding gaming addiction in adolescent populations. This will require allocating research and resources for schools and their staff, and for families, as well as the establishment of working relationships with health professionals and services.
Harmful social and cultural effects associated with internet use
Part II of the study identifies a number of different harmful social and cultural effects associated with internet use. The evidence points to the occurrence of significant damage to both individuals and society. Some of these harmful effects are described briefly below:
Information overload: Having too much information to be able to adequately understand an issue or make effective decisions. Information overload is associated with loss of control, feelings of being overwhelmed, reduced intellectual performance, and diminished job satisfaction. Studies show that information overload affects up to 20-30% of people.
Damage to social relationships: Extensive internet use, of social media in particular, is correlated with loneliness and social isolation. Intimate relationships can be degraded by internet use, particularly due to viewing online pornography. Malicious online behaviour, particularly cyber-bullying, cyber-stalking and online predation, affects a significant percentage of internet users.
Impaired public/private boundaries: The way in which the internet and smartphones blur the distinction between private and public, and between different spheres of life, including work, home life and leisure, harms the boundaries between people’s public and private lives. Harmful effects that can result from such permeations include loss of quality of life, lack of privacy, decreased safety and security, and harm to social relations – when friends and family members feel they are left behind by new technology.
Harmful effects on cognitive development: Empirical evidence suggests that internet use can have both positive and negative impacts on cognitive development, depending on the person and the circumstances. There is evidence that children’s cognitive development can be damaged by prolonged internet use, including the development of memory skills, attention span, abilities for critical reasoning, language acquisition, reading, and learning abilities. More research is however needed to draw more reliable conclusions.
Damage to communities: Many off-line communities suffer through the partial migration of human activities – shopping, commerce, socialising, leisure activities, professional interactions – to the internet. Online communities sometimes extend off-line communities and sometimes replace them. They are often inadequate replacements, however, as they do not possess some of the valuable or the strongest qualities of off-line communities, and communities may consequently suffer from impoverished communication, incivility, and a lack of trust and commitment.
The study identifies a number of broad policy options for preventing and mitigating these harmful effects. They include, among other things:
- promoting technology that better protects social institutions, stimulating or requiring tech companies to introduce products and services that better protect social institutions and internet users;
- education about the internet and its consequences;
- stronger social services support for internet users: this policy option involves strengthening social services dedicated to internet users to prevent or mitigate harmful effects such as internet addition, antisocial online behaviour or information overload;
- incentivising or requiring employers to develop policies that protect workers against harmful effects of work-related internet use, such as information overload and the blurring of lines between public and private life;
- establishing governmental units and multi-stakeholder platforms at EU level,to address the problems of the internet’s harmful social and cultural effects.
Problematic use of the internet (PUI) research network
Finally, in relation to internet-caused damage, it is worth mentioning the recent article published by the European Science-Media Hub (ESMH) on the European Problematic Use of Internet (PUI) research network. The project, funded by the European Commission, gathers over 120 psychologists, psychiatrists and neuroscientists, with the objective of reaching a better definition of diagnostic criteria, the role of genetics and personality traits, and the brain-based mechanisms behind internet related disorders.
Scientific Foresight (STOA)
European parliament plenary session – september 2024, taxing the super-rich – answering citizens’ concerns, how has parliament supported the green deal ambition to cut transport emissions, how has parliament kept human rights sanctions at the top of the eu agenda, how has parliament responded to the rise of artificial intelligence, arrest of captain paul watson in greenland – answering citizens’ concerns, identifying data gaps in the textile industry and assessing current initiatives to address them, the role of research and innovation in ensuring a safe and sustainable supply of critical raw materials in the eu , end the cage age – answering citizens’ concerns, european parliament constitutive session – july 2024, how does parliament support ukraine, how has parliament protected workers at risk of poverty.
Comments are closed for this post.
- What Europe does for me

EU legislation in progress

Download the EPRS App

- EP Plenary Sessions
- Cost of Non-Europe reports
- Latest Media
- Climate Change
- Russia's war on Ukraine
We write about
- Replies to campaigns from citizens
- What Europe does for you
- Economic and Social Policies
- EU Financing / Budgetary Affairs
- Institutional and Legal Affairs
- International Relations
- Policy Cycle
- Structural and Cohesion Policies
RSS Link to Scientific Foresight (STOA)
Social media.
- EP Think Tank
- Write to the European Parliament
- EP Library catalogue
Disclaimer and Copyright statement
The content of all documents (and articles) contained in this blog is the sole responsibility of the author and any opinions expressed therein do not necessarily represent the official position of the European Parliament. It is addressed to the Members and staff of the EP for their parliamentary work. Reproduction and translation for non-commercial purposes are authorised, provided the source is acknowledged and the European Parliament is given prior notice and sent a copy. For a comprehensive description of our cookie and data protection policies, please visit Terms and Conditions page. Copyright © European Union, 2014-2024. All rights reserved.
Discover more from Epthinktank
Subscribe now to keep reading and get access to the full archive.
Type your email…
Continue reading

- Privacy Overview
- Strictly Necessary Cookies
- Cookie Policy
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
More information about our Cookie Policy .
The present website is hosted by WordPress.com, a service by Automattic. Automattic is a global company with thousands of servers located in several separate data centres around the world. While Automattic takes care of the security of the platform , we, the European Parliamentary Research Service, own the content of the blog. For more detailed information about the compliance of Automattic products and services with the EU General Data Protection Regulation (GDPR), please see their dedicated page .
Data collected
We do not collect any personal data that could identify an individual user. The users that are registered in WordPress.com should consult wordpress.com terms of service . We do collect anonymised aggregate data for statistical purposes. The data collected for this purposes include: number of visits/visitors per page, the country of the user, and aggregate numbers of incoming and outgoing clicks.
We determine unique page counts by using a “hashed” version of the visitor’s IP address. The visitor’s full IP address is deleted from our logs after a little over a month. That timeframe is how long the data is needed in order to allow us to calculate your stats on a monthly basis and no longer.
We collect your email address only if you proactively requested to be notified about the updates on the blog. You can always contact us to remove your email address from our records or unsubscribe from the notification service.
We can also see your name and email address if you made a comment to one of our posts. We do not make the email address visible on the comment. Nevertheless, on request, we can delete your comments.
We collect cookies only to facilitate your browsing experience, such as enabling you to share our posts via social media or comment on the post. The majority of cookies will be used only if you are a registered WordPress.com user. In this case, you are bound to WordPress.com terms of service .
Some pages embed content from third parties. In this case, you will need to actively consent to their terms in order to see the content.
We do not collect cookies to show advertisement nor resell any information collected with cookies to third parties. Read more about the wordpress.com cookie policy and the way to control cookies on their dedicated page .
Essay Service Examples Technology Internet
Essay About Internet Safety
Table of contents
Introduction, illegal access, adult content, monetary fraud and fake identity, online harassment, banking cyberattacks.
- Proper editing and formatting
- Free revision, title page, and bibliography
- Flexible prices and money-back guarantee

Our writers will provide you with an essay sample written from scratch: any topic, any deadline, any instructions.
Cite this paper
Related essay topics.
Get your paper done in as fast as 3 hours, 24/7.
Related articles

Most popular essays
- Effects of Technology
From 2005 to 2017, a survey for those ages 12-17 showed a 52% increase in reports of symptoms of...
- Technology in Education
Formerly, around ten years ago or maybe even less, we were not familiar with the notorious term...
- Social Media
The “Virtual World” the perfect connotation for today’s scenario. In the age of 21st century, we...
- Advantages of Technology
Nowadays world is fully dependent on the Internet in all areas of activity. It is used to interact...
- Cyber Crimes
- Cyber Security
There are some processes and technologies that are formed for the security of computers, software,...
SMEs face a severe issue when it comes to cyber security, the issue faces all kinds of...
Contemporary world comes with many technological changes and improvements. The biggest invention...
I chose this topic because as a teenager myself, I’ve grown up in a world that has invariably...
Have you ever thought about how the Internet affects our cognitive abilities and changes our way...
Join our 150k of happy users
- Get original paper written according to your instructions
- Save time for what matters most
Fair Use Policy
EduBirdie considers academic integrity to be the essential part of the learning process and does not support any violation of the academic standards. Should you have any questions regarding our Fair Use Policy or become aware of any violations, please do not hesitate to contact us via [email protected].
We are here 24/7 to write your paper in as fast as 3 hours.
Provide your email, and we'll send you this sample!
By providing your email, you agree to our Terms & Conditions and Privacy Policy .
Say goodbye to copy-pasting!
Get custom-crafted papers for you.
Enter your email, and we'll promptly send you the full essay. No need to copy piece by piece. It's in your inbox!
- Health Science
- Business Education
- Computer Applications
- Career Readiness
- Teaching Strategies
« View All Posts
Digital Citizenship
What Is Internet Safety and Why Is It Important to Teach?
- Share This Article
June 12th, 2019 | 12 min. read
Print/Save as PDF
Internet safety is the practice of following actionable guidelines, understanding modern technology, and protecting your digital devices so you can defend against malicious parts of the online world.
It’s one of the main parts of a strong digital citizenship program in any school.
That’s because the internet provides near-instant satisfaction when looking up answers to questions, instructions on how to accomplish a task, and more.
But it’s also packed with potential dangers. Malware, phishing, scams, drive-by downloads, misrepresentation, and old-fashioned lies hide in every possible corner online, just waiting for an opportunity to strike.
So how can you prepare children and teens to successfully navigate this minefield of information?
It’s not easy — but the first step to teaching i nternet safety is understanding it yourself!
What Does Internet Safety Entail?
Internet safety requires you to have a firm comprehension of the internet, what’s on it, how it’s used, and how it operates.
It also emphasizes understanding the lesser-known areas of the internet, like code, webpage interactions, and secure connections.
In general, you can break down internet safety into two categories — behavior and knowledge .
If you’ve never had to teach internet safety before, we recommend starting with seven behavior ideas that work in middle school and high school :
- Verifying someone’s identity
- Verifying a link is safe
- Identifying an online scam
- Protecting privacy
- Creating and using passwords
- Identifying cyberbullying
- Becoming a good digital citizen
Internet safety is truly an expansive space, and it requires a knowledge component as well — the kind of knowledge that helps you use safe technology .
That includes:
- Understanding code
- Using ad blockers
- Identifying secure connections
- Using virtual personal networks (VPNs)
- Understanding your data and its value
- Knowing when your data is being collected
- Understanding how your data is used to advertise
Because these two lists are pretty long, we’ll dive into each one separately.
Let’s start with making safe choices!
Making Safe Choices
The most important part of internet safety is learning how to make safe choices.
That requires a lot of background knowledge, but it’s all actionable information that your students can use any time.
Using the points below, you can teach your students how to stay safe online by making the smartest and best choices available.
1. Verifying someone’s identity
The internet makes it a snap for anyone to falsify their identity.
All it takes is an email address, made-up name, and social media profile. With that done, any person on Earth can impersonate someone else.
Students can verify identities by searching someone’s name in search engines and multiple social networks — especially LinkedIn .
Why is LinkedIn special?
Because it’s one of the hardest social profiles to fake!
LinkedIn essentially requires you to upload a full-fledged resume to join the network. Any LinkedIn profile with minimal information is immediately suspicious.
Facebook profiles with no friends, Twitter profiles with no followers, and Instagram profiles with only selfies are also suspicious.
Essentially, if someone seems very into themselves but doesn’t have the online friends to show for it, that person may be an imposter!
2. Verifying a link is safe
In addition to verifying the identity of a stranger, students also need to know how to “read” a URL or link.
You can do this a couple of different ways.
First, students should understand the letters that start a URL — HTTP and HTTPS.
The easy to way to think of these is that HTTP is unsecure and HTTPS is secure .
That means the URL goes to a trusted and well-maintained website, as opposed to a throwaway website that’s being used maliciously.
Second, students should also know about hovering. Hovering is when you place your mouse cursor over a link (without clicking it) to see the link embedded in the text.
99% of the time, these will be the same URLs. But 1% of the time, you may see that a link shows a different URL when hovering with your mouse cursor.
Don’t click these links! They may be deceptive, especially if the text of a link looks like you’ll go to one website but the embedded URL will send you somewhere else!
3. Identifying an online scam
Online scams often take the form of unsolicited emails, instant messages, or text messages.
Basically, they’re messages that come from unknown sources that tell the recipient to do something, like click a link.
As tempting or promising as the offer may be, students need to know not to click the link !
Simply opening the link could subject the student’s computer to malware, viruses, ransomware, or some other villainous software.
4. Protecting privacy
Privacy is another key area of understanding where students make crucial choices.

Today, every social network asks for a name, email address, phone number, and more!
So where can you draw the line?
In the event your students choose to create social media profiles, it’s crucial that they’re careful about publicly posting their personal information.
They should hide their phone numbers. Their email addresses shouldn’t be searchable. In some networks, students may even be able to remove themselves from search results entirely, protecting them from random friend requests and online invasions of privacy.
As a rule of thumb, students should always keep their addresses and contact information secret, even from social networks that ask for them.
5. Creating and using passwords
Passwords are used in every account-based service online, from social networks to banks.
As a result, they’re crucial in maintaining the privacy and integrity of any student’s information.
This opens the door for you to teach your students about best practices when creating passwords.
Strong passwords tend to be:
- 10+ characters long
- Include letters, numbers, and other characters
- Unrelated to personal information
- Easy to remember
- Hard to guess
Creating good, unique passwords is a challenge for anyone — especially if they’re not tech-savvy.
If you’d like your students to practice passwords before making them, you can use the LastPass password tester in your class.
6. Identifying cyberbullying
Because social networking and messaging is easier than ever, it’s also easier to harass people as well.
This unfortunate side-effect of the internet is called cyberbullying , and it’s been a hot-button topic in schools for years now.
Cyberbullying is essentially insulting or harassing someone via the internet. While it’s mostly discussed in the context of children, teens, and young adults, it’s shockingly prevalent across all age ranges.
The major takeaway for students is identification . Insults, jokes at someone’s expense, and repeated harassment are all callsigns of cyberbullying.
The effects can be devastating on the victims. Social media has a tendency to permeate our lives, and that’s amplified for teens and pre-teens who are highly involved in their social circles.
To prevent feelings of isolation, self-doubt, and worse outcomes, it’s crucial for students to know cyberbullying when they see it so they can do their part to stop the harassment.
7. Becoming a good digital citizen
Good digital citizenship means students know how to make safe choices when using the internet.
It also entails a general knowledge of technology, how the internet works, and warning signs that something may have gone wrong.
In that respect, making smart choices on the internet is just the first step on the road for your students as they become responsible digital citizens.
The next key area of internet safety is using — and understanding — safe technology.
Using Safe Technology
Using safe technology helps protect a student’s devices.
Understanding safe technology helps protect a student’s life .
While this requires more information and a thorough digital citizenship curriculum , it also gives your students the essential knowledge they need to protect themselves from digital pitfalls for the rest of their lives.
You can start by talking about code.
1. Understanding code
Code is the back-end, written text that developers use to create webpages and webpage elements.
With it, developers can tell a webpage to show a certain image at a certain point. They can denote where a video should go and whether it should play automatically.
The options are nearly limitless!
Most of the code on the internet is in a language called Hypertext Markup Language , or HTML. For the most part, HTML is a safe coding language that has very little opportunity to harm someone’s computer or steal someone’s information.
Other languages include Java , CSS , Python , Ruby , and more. These languages all have their strengths and weaknesses, and some of them can be used maliciously.
Thankfully, these languages don’t show up too often except for in special online applications.
The best way for students to learn about code is to learn how to code . Once students use the coding languages themselves, they’ll have a sharper idea of how those languages can be used online.
2. Using ad blockers
Ads are everywhere these days. Unfortunately, very few ad providers actually check their advertisers to ensure they’re providing clean, safe ads on webpages.
This is where a lot of websites run into trouble. It’s possible for them to unknowingly serve malware or virus-infected ads that prompt what’s called a drive-by download .
That means someone just needs to open a webpage and their browser will start downloading viruses, spyware, malware, or ransomware in the background — and nobody knows until it’s too late!
The best thing to do is to show students how to use ad blocker extensions in common web browsers, like Google Chrome or Mozilla Firefox.
Yes, ads play a vital role in helping companies keep the lights on.
But so few companies perform quality assurance checks on their ads for malicious code, and cybercriminals will always strive to stay one step ahead of the people who may catch them.
As a result, the best solution is for your students to use ad blockers!
3. Identifying secure connections
Secure connections are essential to ensuring someone’s personal information goes directly to a website and isn’t intercepted, decrypted, or misused by malicious third parties.
Thankfully, secure connections are easy to identify. Just look for the HTTPS at the beginning of a website’s URL.
The S indicates that the website uses something called secure socket layers , which is essentially an extra layer of security that protects information as it goes from a student’s computer to the website’s servers.
You can also teach students about virtual personal networks , or VPNs. These are encrypted micro-networks that add even more security to information that’s transmitted from someone’s device to another area.
With HTTPS websites and an always-on VPN equipped to a device, students can protect themselves from almost all of the internet’s dangers when it comes to transmitting data.
4. Using virtual personal networks (VPNs)
Speaking of VPNs, it’s important to understand how they work.
A VPN establishes a secure connection between someone’s device and a proxy location. In addition, the VPN creates a digital “shell” that protects that connection.
So if you imagine a standard internet connection as a copper wire, a VPN internet connection would be like that copper wire covered in a thick layer of rubber for protection and waterproofing.
In addition, VPNs prevent internet service providers (ISPs) from tracking a lot of your browsing activity online. This is important because it’s legal for ISPs to sell anyone’s browsing information to marketing firms to create targeted advertising.
VPNs stop that dead in its tracks. It’s just a safer way to use the internet!
5. Understanding your data and its value
So why should you and your students care that ISPs, social networks, and third-party operators have access to your data?
Because in today’s fast-paced, information-based world, personal data is a valuable commodity .
Packages of data are sold among companies just like any other product. The most recent example of this is the Facebook-Cambridge Analytica scandal that revealed enormous breaches of personal privacy and dozens of security concerns.
Essentially, every student in your classroom is valuable to an advertiser. Because of that, their information has value for the social networks, ISPs, and other companies that collect it.
The less a student tells these websites about themselves, the less likely they’ll be to have their information packaged and sold to the highest bidder.
6. Knowing when your data is being collected
How do you know when your or your students’ data is being collected?
Because of a European law called the General Data Protection Regulation (GDPR), any website that has traffic or customers in Europe must disclose when someone is being tracked.
The method of this tracking is often through something called a “cookie,” or a unique identifying code that makes one person stand out against the millions who may visit a website.
So while American or Asian websites don’t have to disclose their tracking information by law, they still do it to accommodate their European usership.
As a result, you’ll often see websites with popups that say they’re currently tracking you.
7. Understanding how your data is used to advertise
Finally, it’s essential that students understand how their data is used to advertise to them.
As we established before, third-party agencies will collect and sell anyone’s information for a price. Then, the people who buy that information can use it to deliver targeted advertisements to individuals through different means.
Have you ever talked to your friend about a brand or product only to open your Facebook account and see an ad for it right away?
Have you ever texted someone about a book you wanted to read and then saw it as an ad at the top of Amazon?
This isn’t an accident. Advertisers have never had more access to information about you, your students, or anyone else in the world.
As a result, they have a very sharp idea about what they can offer people.
If you or your students see ads on social networks or shopping websites, remember that they’re not there by accident!
Those ads are placed through a complex series of identification and delivery systems. Even if they show something that you want, it’s smartest not to click on them since you also don’t know where the ad may lead!
Teach Internet Safety as Part of a Digital Citizenship Curriculum
Learning and practicing internet safety is critical for your students to stay safe in a technologically-driven world. But without the right curriculum resources, your students are at risk of not learning essential information that will help them become good digital citizens.
When you teach the internet safety concepts in this article, you’ll be well on your way to ensuring your students are prepared to work in the digital world.
But how can you be sure you meet your standards for internet safety and other critical digital citizenship topics? Consider adopting a comprehensive curriculum system such as iCEV.
The iCEV curriculum includes material to help meet your standards for internet safety, digital citizenship, and more.
Visit the curriculum page to learn more about topics you can teach with iCEV to decide if it’s right for your classroom.

Cyber Security Essay for Students and Children
Cyber security essay.
Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today’s world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software. This software protects the data. Cybersecurity is important because not only it helps to secure information but also our system from virus attack. After the U.S.A. and China, India has the highest number of internet users.

Cyber Threats
It can be further classified into 2 types. Cybercrime – against individuals, corporates, etc.and Cyberwarfare – against a state.
Cyber Crime
Use of cyberspace, i.e. computer, internet, cellphone, other technical devices, etc., to commit a crime by an individual or organized group is called cyber-crime. Cyber attackers use numerous software and codes in cyberspace to commit cybercrime. They exploit the weaknesses in the software and hardware design through the use of malware. Hacking is a common way of piercing the defenses of protected computer systems and interfering with their functioning. Identity theft is also common.
Cybercrimes may occur directly i.e, targeting the computers directly by spreading computer viruses. Other forms include DoS attack. It is an attempt to make a machine or network resource unavailable to its intended users. It suspends services of a host connected to the internet which may be temporary or permanent.
Malware is a software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It usually appears in the form of code, scripts, active content, and other software. ‘Malware’ refers to a variety of forms of hostile or intrusive software, for example, Trojan Horses, rootkits, worms, adware, etc.
Another way of committing cybercrime is independent of the Computer Network or Device. It includes Economic frauds. It is done to destabilize the economy of a country, attack on banking security and transaction system, extract money through fraud, acquisition of credit/debit card data, financial theft, etc.
Hinder the operations of a website or service through data alteration, data destruction. Others include using obscene content to humiliate girls and harm their reputation, Spreading pornography, threatening e-mail, assuming a fake identity, virtual impersonation. Nowadays misuse of social media in creating intolerance, instigating communal violence and inciting riots is happening a lot.
Get the huge list of more than 500 Essay Topics and Ideas
Cyber Warfare
Snowden revelations have shown that Cyberspace could become the theatre of warfare in the 21st century. Future wars will not be like traditional wars which are fought on land, water or air. when any state initiates the use of internet-based invisible force as an instrument of state policy to fight against another nation, it is called cyberwar’.
It includes hacking of vital information, important webpages, strategic controls, and intelligence. In December 2014 the cyberattack a six-month-long cyberattack on the German parliament for which the Sofacy Group is suspected. Another example 2008 cyberattack on US Military computers. Since these cyber-attacks, the issue of cyber warfare has assumed urgency in the global media.
Inexpensive Cybersecurity Measures
- The simplest thing you can do to up your security and rest easy at night knowing your data is safe is to change your passwords.
- You should use a password manager tool like LastPass, Dashlane, or Sticky Password to keep track of everything for you. These applications help you to use unique, secure passwords for every site you need while also keeping track of all of them for you.
- An easy way for an attacker to gain access to your network is to use old credentials that have fallen by the wayside. Hence delete unused accounts.
- Enabling two-factor authentication to add some extra security to your logins. An extra layer of security that makes it harder for an attacker to get into your accounts.
- Keep your Softwares up to date.
Today due to high internet penetration, cybersecurity is one of the biggest need of the world as cybersecurity threats are very dangerous to the country’s security. Not only the government but also the citizens should spread awareness among the people to always update your system and network security settings and to the use proper anti-virus so that your system and network security settings stay virus and malware-free.
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App

Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, generate accurate citations for free.
- Knowledge Base
- How to write an argumentative essay | Examples & tips
How to Write an Argumentative Essay | Examples & Tips
Published on July 24, 2020 by Jack Caulfield . Revised on July 23, 2023.
An argumentative essay expresses an extended argument for a particular thesis statement . The author takes a clearly defined stance on their subject and builds up an evidence-based case for it.
Instantly correct all language mistakes in your text
Upload your document to correct all your mistakes in minutes
Table of contents
When do you write an argumentative essay, approaches to argumentative essays, introducing your argument, the body: developing your argument, concluding your argument, other interesting articles, frequently asked questions about argumentative essays.
You might be assigned an argumentative essay as a writing exercise in high school or in a composition class. The prompt will often ask you to argue for one of two positions, and may include terms like “argue” or “argument.” It will frequently take the form of a question.
The prompt may also be more open-ended in terms of the possible arguments you could make.
Argumentative writing at college level
At university, the vast majority of essays or papers you write will involve some form of argumentation. For example, both rhetorical analysis and literary analysis essays involve making arguments about texts.
In this context, you won’t necessarily be told to write an argumentative essay—but making an evidence-based argument is an essential goal of most academic writing, and this should be your default approach unless you’re told otherwise.
Examples of argumentative essay prompts
At a university level, all the prompts below imply an argumentative essay as the appropriate response.
Your research should lead you to develop a specific position on the topic. The essay then argues for that position and aims to convince the reader by presenting your evidence, evaluation and analysis.
- Don’t just list all the effects you can think of.
- Do develop a focused argument about the overall effect and why it matters, backed up by evidence from sources.
- Don’t just provide a selection of data on the measures’ effectiveness.
- Do build up your own argument about which kinds of measures have been most or least effective, and why.
- Don’t just analyze a random selection of doppelgänger characters.
- Do form an argument about specific texts, comparing and contrasting how they express their thematic concerns through doppelgänger characters.
Receive feedback on language, structure, and formatting
Professional editors proofread and edit your paper by focusing on:
- Academic style
- Vague sentences
- Style consistency
See an example
An argumentative essay should be objective in its approach; your arguments should rely on logic and evidence, not on exaggeration or appeals to emotion.
There are many possible approaches to argumentative essays, but there are two common models that can help you start outlining your arguments: The Toulmin model and the Rogerian model.
Toulmin arguments
The Toulmin model consists of four steps, which may be repeated as many times as necessary for the argument:
- Make a claim
- Provide the grounds (evidence) for the claim
- Explain the warrant (how the grounds support the claim)
- Discuss possible rebuttals to the claim, identifying the limits of the argument and showing that you have considered alternative perspectives
The Toulmin model is a common approach in academic essays. You don’t have to use these specific terms (grounds, warrants, rebuttals), but establishing a clear connection between your claims and the evidence supporting them is crucial in an argumentative essay.
Say you’re making an argument about the effectiveness of workplace anti-discrimination measures. You might:
- Claim that unconscious bias training does not have the desired results, and resources would be better spent on other approaches
- Cite data to support your claim
- Explain how the data indicates that the method is ineffective
- Anticipate objections to your claim based on other data, indicating whether these objections are valid, and if not, why not.
Rogerian arguments
The Rogerian model also consists of four steps you might repeat throughout your essay:
- Discuss what the opposing position gets right and why people might hold this position
- Highlight the problems with this position
- Present your own position , showing how it addresses these problems
- Suggest a possible compromise —what elements of your position would proponents of the opposing position benefit from adopting?
This model builds up a clear picture of both sides of an argument and seeks a compromise. It is particularly useful when people tend to disagree strongly on the issue discussed, allowing you to approach opposing arguments in good faith.
Say you want to argue that the internet has had a positive impact on education. You might:
- Acknowledge that students rely too much on websites like Wikipedia
- Argue that teachers view Wikipedia as more unreliable than it really is
- Suggest that Wikipedia’s system of citations can actually teach students about referencing
- Suggest critical engagement with Wikipedia as a possible assignment for teachers who are skeptical of its usefulness.
You don’t necessarily have to pick one of these models—you may even use elements of both in different parts of your essay—but it’s worth considering them if you struggle to structure your arguments.
Regardless of which approach you take, your essay should always be structured using an introduction , a body , and a conclusion .
Like other academic essays, an argumentative essay begins with an introduction . The introduction serves to capture the reader’s interest, provide background information, present your thesis statement , and (in longer essays) to summarize the structure of the body.
Hover over different parts of the example below to see how a typical introduction works.
The spread of the internet has had a world-changing effect, not least on the world of education. The use of the internet in academic contexts is on the rise, and its role in learning is hotly debated. For many teachers who did not grow up with this technology, its effects seem alarming and potentially harmful. This concern, while understandable, is misguided. The negatives of internet use are outweighed by its critical benefits for students and educators—as a uniquely comprehensive and accessible information source; a means of exposure to and engagement with different perspectives; and a highly flexible learning environment.
The body of an argumentative essay is where you develop your arguments in detail. Here you’ll present evidence, analysis, and reasoning to convince the reader that your thesis statement is true.
In the standard five-paragraph format for short essays, the body takes up three of your five paragraphs. In longer essays, it will be more paragraphs, and might be divided into sections with headings.
Each paragraph covers its own topic, introduced with a topic sentence . Each of these topics must contribute to your overall argument; don’t include irrelevant information.
This example paragraph takes a Rogerian approach: It first acknowledges the merits of the opposing position and then highlights problems with that position.
Hover over different parts of the example to see how a body paragraph is constructed.
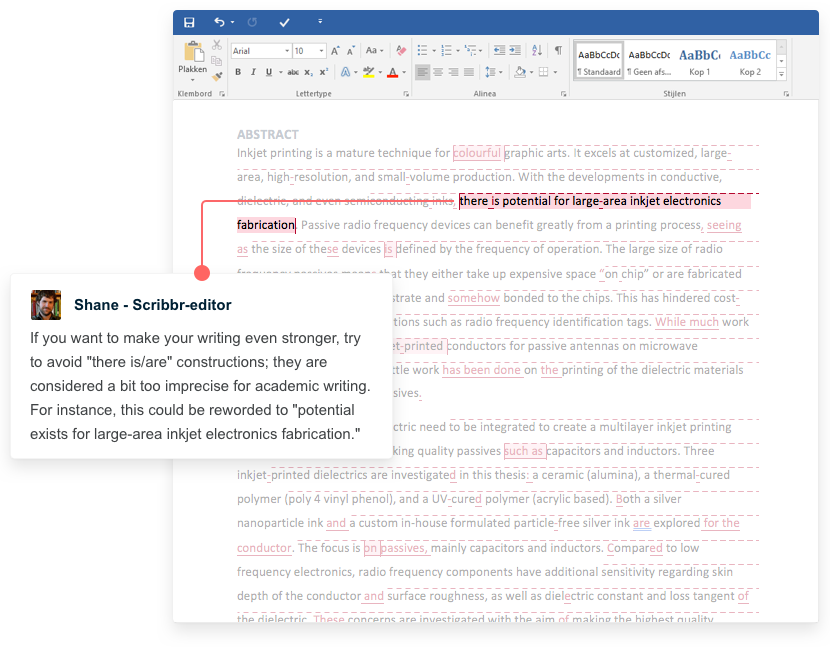
A common frustration for teachers is students’ use of Wikipedia as a source in their writing. Its prevalence among students is not exaggerated; a survey found that the vast majority of the students surveyed used Wikipedia (Head & Eisenberg, 2010). An article in The Guardian stresses a common objection to its use: “a reliance on Wikipedia can discourage students from engaging with genuine academic writing” (Coomer, 2013). Teachers are clearly not mistaken in viewing Wikipedia usage as ubiquitous among their students; but the claim that it discourages engagement with academic sources requires further investigation. This point is treated as self-evident by many teachers, but Wikipedia itself explicitly encourages students to look into other sources. Its articles often provide references to academic publications and include warning notes where citations are missing; the site’s own guidelines for research make clear that it should be used as a starting point, emphasizing that users should always “read the references and check whether they really do support what the article says” (“Wikipedia:Researching with Wikipedia,” 2020). Indeed, for many students, Wikipedia is their first encounter with the concepts of citation and referencing. The use of Wikipedia therefore has a positive side that merits deeper consideration than it often receives.
Here's why students love Scribbr's proofreading services
Discover proofreading & editing
An argumentative essay ends with a conclusion that summarizes and reflects on the arguments made in the body.
No new arguments or evidence appear here, but in longer essays you may discuss the strengths and weaknesses of your argument and suggest topics for future research. In all conclusions, you should stress the relevance and importance of your argument.
Hover over the following example to see the typical elements of a conclusion.
The internet has had a major positive impact on the world of education; occasional pitfalls aside, its value is evident in numerous applications. The future of teaching lies in the possibilities the internet opens up for communication, research, and interactivity. As the popularity of distance learning shows, students value the flexibility and accessibility offered by digital education, and educators should fully embrace these advantages. The internet’s dangers, real and imaginary, have been documented exhaustively by skeptics, but the internet is here to stay; it is time to focus seriously on its potential for good.
If you want to know more about AI tools , college essays , or fallacies make sure to check out some of our other articles with explanations and examples or go directly to our tools!
- Ad hominem fallacy
- Post hoc fallacy
- Appeal to authority fallacy
- False cause fallacy
- Sunk cost fallacy
College essays
- Choosing Essay Topic
- Write a College Essay
- Write a Diversity Essay
- College Essay Format & Structure
- Comparing and Contrasting in an Essay
(AI) Tools
- Grammar Checker
- Paraphrasing Tool
- Text Summarizer
- AI Detector
- Plagiarism Checker
- Citation Generator
An argumentative essay tends to be a longer essay involving independent research, and aims to make an original argument about a topic. Its thesis statement makes a contentious claim that must be supported in an objective, evidence-based way.
An expository essay also aims to be objective, but it doesn’t have to make an original argument. Rather, it aims to explain something (e.g., a process or idea) in a clear, concise way. Expository essays are often shorter assignments and rely less on research.
At college level, you must properly cite your sources in all essays , research papers , and other academic texts (except exams and in-class exercises).
Add a citation whenever you quote , paraphrase , or summarize information or ideas from a source. You should also give full source details in a bibliography or reference list at the end of your text.
The exact format of your citations depends on which citation style you are instructed to use. The most common styles are APA , MLA , and Chicago .
The majority of the essays written at university are some sort of argumentative essay . Unless otherwise specified, you can assume that the goal of any essay you’re asked to write is argumentative: To convince the reader of your position using evidence and reasoning.
In composition classes you might be given assignments that specifically test your ability to write an argumentative essay. Look out for prompts including instructions like “argue,” “assess,” or “discuss” to see if this is the goal.
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the “Cite this Scribbr article” button to automatically add the citation to our free Citation Generator.
Caulfield, J. (2023, July 23). How to Write an Argumentative Essay | Examples & Tips. Scribbr. Retrieved September 9, 2024, from https://www.scribbr.com/academic-essay/argumentative-essay/
Is this article helpful?


Jack Caulfield
Other students also liked, how to write a thesis statement | 4 steps & examples, how to write topic sentences | 4 steps, examples & purpose, how to write an expository essay, "i thought ai proofreading was useless but..".
I've been using Scribbr for years now and I know it's a service that won't disappoint. It does a good job spotting mistakes”

Choose Your Test
- Search Blogs By Category
- College Admissions
- AP and IB Exams
- GPA and Coursework
3 Key Tips for How to Write an Argumentative Essay
General Education

If there’s one writing skill you need to have in your toolkit for standardized tests, AP exams, and college-level writing, it’s the ability to make a persuasive argument. Effectively arguing for a position on a topic or issue isn’t just for the debate team— it’s for anyone who wants to ace the essay portion of an exam or make As in college courses.
To give you everything you need to know about how to write an argumentative essay , we’re going to answer the following questions for you:
- What is an argumentative essay?
- How should an argumentative essay be structured?
- How do I write a strong argument?
- What’s an example of a strong argumentative essay?
- What are the top takeaways for writing argumentative papers?
By the end of this article, you’ll be prepped and ready to write a great argumentative essay yourself!
Now, let’s break this down.

What Is an Argumentative Essay?
An argumentative essay is a type of writing that presents the writer’s position or stance on a specific topic and uses evidence to support that position. The goal of an argumentative essay is to convince your reader that your position is logical, ethical, and, ultimately, right . In argumentative essays, writers accomplish this by writing:
- A clear, persuasive thesis statement in the introduction paragraph
- Body paragraphs that use evidence and explanations to support the thesis statement
- A paragraph addressing opposing positions on the topic—when appropriate
- A conclusion that gives the audience something meaningful to think about.
Introduction, body paragraphs, and a conclusion: these are the main sections of an argumentative essay. Those probably sound familiar. Where does arguing come into all of this, though? It’s not like you’re having a shouting match with your little brother across the dinner table. You’re just writing words down on a page!
...or are you? Even though writing papers can feel like a lonely process, one of the most important things you can do to be successful in argumentative writing is to think about your argument as participating in a larger conversation . For one thing, you’re going to be responding to the ideas of others as you write your argument. And when you’re done writing, someone—a teacher, a professor, or exam scorer—is going to be reading and evaluating your argument.
If you want to make a strong argument on any topic, you have to get informed about what’s already been said on that topic . That includes researching the different views and positions, figuring out what evidence has been produced, and learning the history of the topic. That means—you guessed it!—argumentative essays almost always require you to incorporate outside sources into your writing.

What Makes Argumentative Essays Unique?
Argumentative essays are different from other types of essays for one main reason: in an argumentative essay, you decide what the argument will be . Some types of essays, like summaries or syntheses, don’t want you to show your stance on the topic—they want you to remain unbiased and neutral.
In argumentative essays, you’re presenting your point of view as the writer and, sometimes, choosing the topic you’ll be arguing about. You just want to make sure that that point of view comes across as informed, well-reasoned, and persuasive.
Another thing about argumentative essays: they’re often longer than other types of essays. Why, you ask? Because it takes time to develop an effective argument. If your argument is going to be persuasive to readers, you have to address multiple points that support your argument, acknowledge counterpoints, and provide enough evidence and explanations to convince your reader that your points are valid.

Our 3 Best Tips for Picking a Great Argumentative Topic
The first step to writing an argumentative essay deciding what to write about! Choosing a topic for your argumentative essay might seem daunting, though. It can feel like you could make an argument about anything under the sun. For example, you could write an argumentative essay about how cats are way cooler than dogs, right?
It’s not quite that simple . Here are some strategies for choosing a topic that serves as a solid foundation for a strong argument.
Choose a Topic That Can Be Supported With Evidence
First, you want to make sure the topic you choose allows you to make a claim that can be supported by evidence that’s considered credible and appropriate for the subject matter ...and, unfortunately, your personal opinions or that Buzzfeed quiz you took last week don’t quite make the cut.
Some topics—like whether cats or dogs are cooler—can generate heated arguments, but at the end of the day, any argument you make on that topic is just going to be a matter of opinion. You have to pick a topic that allows you to take a position that can be supported by actual, researched evidence.
(Quick note: you could write an argumentative paper over the general idea that dogs are better than cats—or visa versa!—if you’re a) more specific and b) choose an idea that has some scientific research behind it. For example, a strong argumentative topic could be proving that dogs make better assistance animals than cats do.)
You also don’t want to make an argument about a topic that’s already a proven fact, like that drinking water is good for you. While some people might dislike the taste of water, there is an overwhelming body of evidence that proves—beyond the shadow of a doubt—that drinking water is a key part of good health.
To avoid choosing a topic that’s either unprovable or already proven, try brainstorming some issues that have recently been discussed in the news, that you’ve seen people debating on social media, or that affect your local community. If you explore those outlets for potential topics, you’ll likely stumble upon something that piques your audience’s interest as well.
Choose a Topic That You Find Interesting
Topics that have local, national, or global relevance often also resonate with us on a personal level. Consider choosing a topic that holds a connection between something you know or care about and something that is relevant to the rest of society. These don’t have to be super serious issues, but they should be topics that are timely and significant.
For example, if you are a huge football fan, a great argumentative topic for you might be arguing whether football leagues need to do more to prevent concussions . Is this as “important” an issue as climate change? No, but it’s still a timely topic that affects many people. And not only is this a great argumentative topic: you also get to write about one of your passions! Ultimately, if you’re working with a topic you enjoy, you’ll have more to say—and probably write a better essay .
Choose a Topic That Doesn’t Get You Too Heated
Another word of caution on choosing a topic for an argumentative paper: while it can be effective to choose a topic that matters to you personally, you also want to make sure you’re choosing a topic that you can keep your cool over. You’ve got to be able to stay unemotional, interpret the evidence persuasively, and, when appropriate, discuss opposing points of view without getting too salty.
In some situations, choosing a topic for your argumentative paper won’t be an issue at all: the test or exam will choose it for you . In that case, you’ve got to do the best you can with what you’re given.
In the next sections, we’re going to break down how to write any argumentative essay —regardless of whether you get to choose your own topic or have one assigned to you! Our expert tips and tricks will make sure that you’re knocking your paper out of the park.

The Thesis: The Argumentative Essay’s Backbone
You’ve chosen a topic or, more likely, read the exam question telling you to defend, challenge, or qualify a claim on an assigned topic. What do you do now?
You establish your position on the topic by writing a killer thesis statement ! The thesis statement, sometimes just called “the thesis,” is the backbone of your argument, the north star that keeps you oriented as you develop your main points, the—well, you get the idea.
In more concrete terms, a thesis statement conveys your point of view on your topic, usually in one sentence toward the end of your introduction paragraph . It’s very important that you state your point of view in your thesis statement in an argumentative way—in other words, it should state a point of view that is debatable.
And since your thesis statement is going to present your argument on the topic, it’s the thing that you’ll spend the rest of your argumentative paper defending. That’s where persuasion comes in. Your thesis statement tells your reader what your argument is, then the rest of your essay shows and explains why your argument is logical.
Why does an argumentative essay need a thesis, though? Well, the thesis statement—the sentence with your main claim—is actually the entire point of an argumentative essay. If you don’t clearly state an arguable claim at the beginning of your paper, then it’s not an argumentative essay. No thesis statement = no argumentative essay. Got it?
Other types of essays that you’re familiar with might simply use a thesis statement to forecast what the rest of the essay is going to discuss or to communicate what the topic is. That’s not the case here. If your thesis statement doesn’t make a claim or establish your position, you’ll need to go back to the drawing board.
Example Thesis Statements
Here are a couple of examples of thesis statements that aren’t argumentative and thesis statements that are argumentative
The sky is blue.
The thesis statement above conveys a fact, not a claim, so it’s not argumentative.
To keep the sky blue, governments must pass clean air legislation and regulate emissions.
The second example states a position on a topic. What’s the topic in that second sentence? The best way to keep the sky blue. And what position is being conveyed? That the best way to keep the sky blue is by passing clean air legislation and regulating emissions.
Some people would probably respond to that thesis statement with gusto: “No! Governments should not pass clean air legislation and regulate emissions! That infringes on my right to pollute the earth!” And there you have it: a thesis statement that presents a clear, debatable position on a topic.
Here’s one more set of thesis statement examples, just to throw in a little variety:
Spirituality and otherworldliness characterize A$AP Rocky’s portrayals of urban life and the American Dream in his rap songs and music videos.
The statement above is another example that isn’t argumentative, but you could write a really interesting analytical essay with that thesis statement. Long live A$AP! Now here’s another one that is argumentative:
To give students an understanding of the role of the American Dream in contemporary life, teachers should incorporate pop culture, like the music of A$AP Rocky, into their lessons and curriculum.
The argument in this one? Teachers should incorporate more relevant pop culture texts into their curriculum.
This thesis statement also gives a specific reason for making the argument above: To give students an understanding of the role of the American Dream in contemporary life. If you can let your reader know why you’re making your argument in your thesis statement, it will help them understand your argument better.

An actual image of you killing your argumentative essay prompts after reading this article!
Breaking Down the Sections of An Argumentative Essay
Now that you know how to pick a topic for an argumentative essay and how to make a strong claim on your topic in a thesis statement, you’re ready to think about writing the other sections of an argumentative essay. These are the parts that will flesh out your argument and support the claim you made in your thesis statement.
Like other types of essays, argumentative essays typically have three main sections: the introduction, the body, and the conclusion. Within those sections, there are some key elements that a reader—and especially an exam scorer or professor—is always going to expect you to include.
Let’s look at a quick outline of those three sections with their essential pieces here:
- Introduction paragraph with a thesis statement (which we just talked about)
- Support Point #1 with evidence
- Explain/interpret the evidence with your own, original commentary (AKA, the fun part!)
- Support Point #2 with evidence
- Explain/interpret the evidence with your own, original commentary
- Support Point #3 with evidence
- New paragraph addressing opposing viewpoints (more on this later!)
- Concluding paragraph
Now, there are some key concepts in those sections that you’ve got to understand if you’re going to master how to write an argumentative essay. To make the most of the body section, you have to know how to support your claim (your thesis statement), what evidence and explanations are and when you should use them, and how and when to address opposing viewpoints. To finish strong, you’ve got to have a strategy for writing a stellar conclusion.
This probably feels like a big deal! The body and conclusion make up most of the essay, right? Let’s get down to it, then.

How to Write a Strong Argument
Once you have your topic and thesis, you’re ready for the hard part: actually writing your argument. If you make strategic choices—like the ones we’re about to talk about—writing a strong argumentative essay won’t feel so difficult.
There are three main areas where you want to focus your energy as you develop a strategy for how to write an argumentative essay: supporting your claim—your thesis statement—in your essay, addressing other viewpoints on your topic, and writing a solid conclusion. If you put thought and effort into these three things, you’re much more likely to write an argumentative essay that’s engaging, persuasive, and memorable...aka A+ material.
Focus Area 1: Supporting Your Claim With Evidence and Explanations
So you’ve chosen your topic, decided what your position will be, and written a thesis statement. But like we see in comment threads across the Internet, if you make a claim and don’t back it up with evidence, what do people say? “Where’s your proof?” “Show me the facts!” “Do you have any evidence to support that claim?”
Of course you’ve done your research like we talked about. Supporting your claim in your thesis statement is where that research comes in handy.
You can’t just use your research to state the facts, though. Remember your reader? They’re going to expect you to do some of the dirty work of interpreting the evidence for them. That’s why it’s important to know the difference between evidence and explanations, and how and when to use both in your argumentative essay.
What Evidence Is and When You Should Use It
Evidence can be material from any authoritative and credible outside source that supports your position on your topic. In some cases, evidence can come in the form of photos, video footage, or audio recordings. In other cases, you might be pulling reasons, facts, or statistics from news media articles, public policy, or scholarly books or journals.
There are some clues you can look for that indicate whether or not a source is credible , such as whether:
- The website where you found the source ends in .edu, .gov, or .org
- The source was published by a university press
- The source was published in a peer-reviewed journal
- The authors did extensive research to support the claims they make in the source
This is just a short list of some of the clues that a source is likely a credible one, but just because a source was published by a prestigious press or the authors all have PhDs doesn’t necessarily mean it is the best piece of evidence for you to use to support your argument.
In addition to evaluating the source’s credibility, you’ve got to consider what types of evidence might come across as most persuasive in the context of the argument you’re making and who your readers are. In other words, stepping back and getting a bird’s eye view of the entire context of your argumentative paper is key to choosing evidence that will strengthen your argument.
On some exams, like the AP exams , you may be given pretty strict parameters for what evidence to use and how to use it. You might be given six short readings that all address the same topic, have 15 minutes to read them, then be required to pull material from a minimum of three of the short readings to support your claim in an argumentative essay.
When the sources are handed to you like that, be sure to take notes that will help you pick out evidence as you read. Highlight, underline, put checkmarks in the margins of your exam . . . do whatever you need to do to begin identifying the material that you find most helpful or relevant. Those highlights and check marks might just turn into your quotes, paraphrases, or summaries of evidence in your completed exam essay.
What Explanations Are and When You Should Use Them
Now you know that taking a strategic mindset toward evidence and explanations is critical to grasping how to write an argumentative essay. Unfortunately, evidence doesn’t speak for itself. While it may be obvious to you, the researcher and writer, how the pieces of evidence you’ve included are relevant to your audience, it might not be as obvious to your reader.
That’s where explanations—or analysis, or interpretations—come in. You never want to just stick some quotes from an article into your paragraph and call it a day. You do want to interpret the evidence you’ve included to show your reader how that evidence supports your claim.
Now, that doesn’t mean you’re going to be saying, “This piece of evidence supports my argument because...”. Instead, you want to comment on the evidence in a way that helps your reader see how it supports the position you stated in your thesis. We’ll talk more about how to do this when we show you an example of a strong body paragraph from an argumentative essay here in a bit.
Understanding how to incorporate evidence and explanations to your advantage is really important. Here’s why: when you’re writing an argumentative essay, particularly on standardized tests or the AP exam, the exam scorers can’t penalize you for the position you take. Instead, their evaluation is going to focus on the way you incorporated evidence and explained it in your essay.

Focus Area 2: How—and When—to Address Other Viewpoints
Why would we be making arguments at all if there weren’t multiple views out there on a given topic? As you do research and consider the background surrounding your topic, you’ll probably come across arguments that stand in direct opposition to your position.
Oftentimes, teachers will ask you to “address the opposition” in your argumentative essay. What does that mean, though, to “ address the opposition ?”
Opposing viewpoints function kind of like an elephant in the room. Your audience knows they’re there. In fact, your audience might even buy into an opposing viewpoint and be waiting for you to show them why your viewpoint is better. If you don’t, it means that you’ll have a hard time convincing your audience to buy your argument.
Addressing the opposition is a balancing act: you don’t want to undermine your own argument, but you don’t want to dismiss the validity of opposing viewpoints out-of-hand or ignore them altogether, which can also undermine your argument.
This isn’t the only acceptable approach, but it’s common practice to wait to address the opposition until close to the end of an argumentative essay. But why?
Well, waiting to present an opposing viewpoint until after you’ve thoroughly supported your own argument is strategic. You aren’t going to go into great detail discussing the opposing viewpoint: you’re going to explain what that viewpoint is fairly, but you’re also going to point out what’s wrong with it.
It can also be effective to read the opposition through the lens of your own argument and the evidence you’ve used to support it. If the evidence you’ve already included supports your argument, it probably doesn’t support the opposing viewpoint. Without being too obvious, it might be worth pointing this out when you address the opposition.

Focus Area #3: Writing the Conclusion
It’s common to conclude an argumentative essay by reiterating the thesis statement in some way, either by reminding the reader what the overarching argument was in the first place or by reviewing the main points and evidence that you covered.
You don’t just want to restate your thesis statement and review your main points and call it a day, though. So much has happened since you stated your thesis in the introduction! And why waste a whole paragraph—the very last thing your audience is going to read—on just repeating yourself?
Here’s an approach to the conclusion that can give your audience a fresh perspective on your argument: reinterpret your thesis statement for them in light of all the evidence and explanations you’ve provided. Think about how your readers might read your thesis statement in a new light now that they’ve heard your whole argument out.
That’s what you want to leave your audience with as you conclude your argumentative paper: a brief explanation of why all that arguing mattered in the first place. If you can give your audience something to continue pondering after they’ve read your argument, that’s even better.
One thing you want to avoid in your conclusion, though: presenting new supporting points or new evidence. That can just be confusing for your reader. Stick to telling your reader why the argument you’ve already made matters, and your argument will stick with your reader.

A Strong Argumentative Essay: Examples
For some aspiring argumentative essay writers, showing is better than telling. To show rather than tell you what makes a strong argumentative essay, we’ve provided three examples of possible body paragraphs for an argumentative essay below.
Think of these example paragraphs as taking on the form of the “Argumentative Point #1 → Evidence —> Explanation —> Repeat” process we talked through earlier. It’s always nice to be able to compare examples, so we’ve included three paragraphs from an argumentative paper ranging from poor (or needs a lot of improvement, if you’re feeling generous), to better, to best.
All of the example paragraphs are for an essay with this thesis statement:
Thesis Statement: In order to most effectively protect user data and combat the spread of disinformation, the U.S. government should implement more stringent regulations of Facebook and other social media outlets.
As you read the examples, think about what makes them different, and what makes the “best” paragraph more effective than the “better” and “poor” paragraphs. Here we go:
A Poor Argument
Example Body Paragraph: Data mining has affected a lot of people in recent years. Facebook has 2.23 billion users from around the world, and though it would take a huge amount of time and effort to make sure a company as big as Facebook was complying with privacy regulations in countries across the globe, adopting a common framework for privacy regulation in more countries would be the first step. In fact, Mark Zuckerberg himself supports adopting a global framework for privacy and data protection, which would protect more users than before.
What’s Wrong With This Example?
First, let’s look at the thesis statement. Ask yourself: does this make a claim that some people might agree with, but others might disagree with?
The answer is yes. Some people probably think that Facebook should be regulated, while others might believe that’s too much government intervention. Also, there are definitely good, reliable sources out there that will help this writer prove their argument. So this paper is off to a strong start!
Unfortunately, this writer doesn’t do a great job proving their thesis in their body paragraph. First, the topic sentence—aka the first sentence of the paragraph—doesn’t make a point that directly supports the position stated in the thesis. We’re trying to argue that government regulation will help protect user data and combat the spread of misinformation, remember? The topic sentence should make a point that gets right at that, instead of throwing out a random fact about data mining.
Second, because the topic sentence isn’t focused on making a clear point, the rest of the paragraph doesn’t have much relevant information, and it fails to provide credible evidence that supports the claim made in the thesis statement. For example, it would be a great idea to include exactly what Mark Zuckerberg said ! So while there’s definitely some relevant information in this paragraph, it needs to be presented with more evidence.
A Better Argument
This paragraph is a bit better than the first one, but it still needs some work. The topic sentence is a bit too long, and it doesn’t make a point that clearly supports the position laid out in the thesis statement. The reader already knows that mining user data is a big issue, so the topic sentence would be a great place to make a point about why more stringent government regulations would most effectively protect user data.
There’s also a problem with how the evidence is incorporated in this example. While there is some relevant, persuasive evidence included in this paragraph, there’s no explanation of why or how it is relevant . Remember, you can’t assume that your evidence speaks for itself: you have to interpret its relevance for your reader. That means including at least a sentence that tells your reader why the evidence you’ve chosen proves your argument.
A Best—But Not Perfect!—Argument
Example Body Paragraph: Though Facebook claims to be implementing company policies that will protect user data and stop the spread of misinformation , its attempts have been unsuccessful compared to those made by the federal government. When PricewaterhouseCoopers conducted a Federal Trade Commission-mandated assessment of Facebook’s partnerships with Microsoft and the makers of the Blackberry handset in 2013, the team found limited evidence that Facebook had monitored or even checked that its partners had complied with Facebook’s existing data use policies. In fact, Facebook’s own auditors confirmed the PricewaterhouseCoopers findings, despite the fact that Facebook claimed that the company was making greater attempts to safeguard users’ personal information. In contrast, bills written by Congress have been more successful in changing Facebook’s practices than Facebook’s own company policies have. According to The Washington Post, The Honest Ads Act of 2017 “created public demand for transparency and changed how social media companies disclose online political advertising.” These policy efforts, though thus far unsuccessful in passing legislation, have nevertheless pushed social media companies to change some of their practices by sparking public outrage and negative media attention.
Why This Example Is The Best
This paragraph isn’t perfect, but it is the most effective at doing some of the things that you want to do when you write an argumentative essay.
First, the topic sentences get to the point . . . and it’s a point that supports and explains the claim made in the thesis statement! It gives a clear reason why our claim in favor of more stringent government regulations is a good claim : because Facebook has failed to self-regulate its practices.
This paragraph also provides strong evidence and specific examples that support the point made in the topic sentence. The evidence presented shows specific instances in which Facebook has failed to self-regulate, and other examples where the federal government has successfully influenced regulation of Facebook’s practices for the better.
Perhaps most importantly, though, this writer explains why the evidence is important. The bold sentence in the example is where the writer links the evidence back to their opinion. In this case, they explain that the pressure from Federal Trade Commission and Congress—and the threat of regulation—have helped change Facebook for the better.
Why point out that this isn’t a perfect paragraph, though? Because you won’t be writing perfect paragraphs when you’re taking timed exams either. But get this: you don’t have to write perfect paragraphs to make a good score on AP exams or even on an essay you write for class. Like in this example paragraph, you just have to effectively develop your position by appropriately and convincingly relying on evidence from good sources.

Top 3 Takeaways For Writing Argumentative Essays
This is all great information, right? If (when) you have to write an argumentative essay, you’ll be ready. But when in doubt, remember these three things about how to write an argumentative essay, and you’ll emerge victorious:
Takeaway #1: Read Closely and Carefully
This tip applies to every aspect of writing an argumentative essay. From making sure you’re addressing your prompt, to really digging into your sources, to proofreading your final paper...you’ll need to actively and pay attention! This is especially true if you’re writing on the clock, like during an AP exam.
Takeaway #2: Make Your Argument the Focus of the Essay
Define your position clearly in your thesis statement and stick to that position! The thesis is the backbone of your paper, and every paragraph should help prove your thesis in one way or another. But sometimes you get to the end of your essay and realize that you’ve gotten off topic, or that your thesis doesn’t quite fit. Don’t worry—if that happens, you can always rewrite your thesis to fit your paper!
Takeaway #3: Use Sources to Develop Your Argument—and Explain Them
Nothing is as powerful as good, strong evidence. First, make sure you’re finding credible sources that support your argument. Then you can paraphrase, briefly summarize, or quote from your sources as you incorporate them into your paragraphs. But remember the most important part: you have to explain why you’ve chosen that evidence and why it proves your thesis.
What's Next?
Once you’re comfortable with how to write an argumentative essay, it’s time to learn some more advanced tips and tricks for putting together a killer argument.
Keep in mind that argumentative essays are just one type of essay you might encounter. That’s why we’ve put together more specific guides on how to tackle IB essays , SAT essays , and ACT essays .
But what about admissions essays? We’ve got you covered. Not only do we have comprehensive guides to the Coalition App and Common App essays, we also have tons of individual college application guides, too . You can search through all of our college-specific posts by clicking here.
Trending Now
How to Get Into Harvard and the Ivy League
How to Get a Perfect 4.0 GPA
How to Write an Amazing College Essay
What Exactly Are Colleges Looking For?
ACT vs. SAT: Which Test Should You Take?
When should you take the SAT or ACT?
Get Your Free

Find Your Target SAT Score
Free Complete Official SAT Practice Tests
How to Get a Perfect SAT Score, by an Expert Full Scorer
Score 800 on SAT Math
Score 800 on SAT Reading and Writing
How to Improve Your Low SAT Score
Score 600 on SAT Math
Score 600 on SAT Reading and Writing
Find Your Target ACT Score
Complete Official Free ACT Practice Tests
How to Get a Perfect ACT Score, by a 36 Full Scorer
Get a 36 on ACT English
Get a 36 on ACT Math
Get a 36 on ACT Reading
Get a 36 on ACT Science
How to Improve Your Low ACT Score
Get a 24 on ACT English
Get a 24 on ACT Math
Get a 24 on ACT Reading
Get a 24 on ACT Science
Stay Informed
Get the latest articles and test prep tips!

Ashley Sufflé Robinson has a Ph.D. in 19th Century English Literature. As a content writer for PrepScholar, Ashley is passionate about giving college-bound students the in-depth information they need to get into the school of their dreams.
Ask a Question Below
Have any questions about this article or other topics? Ask below and we'll reply!

- Get started with computers
- Learn Microsoft Office
- Apply for a job
- Improve my work skills
- Design nice-looking docs
- Getting Started
- Smartphones & Tablets
- Typing Tutorial
- Online Learning
- Basic Internet Skills
- Online Safety
- Social Media
- Zoom Basics
- Google Docs
- Google Sheets
- Career Planning
- Resume Writing
- Cover Letters
- Job Search and Networking
- Business Communication
- Entrepreneurship 101
- Careers without College
- Job Hunt for Today
- 3D Printing
- Freelancing 101
- Personal Finance
- Sharing Economy
- Decision-Making
- Graphic Design
- Photography
- Image Editing
- Learning WordPress
- Language Learning
- Critical Thinking
- For Educators
- Translations
- Staff Picks
- English expand_more expand_less
Internet Safety - Introduction to Internet Safety
Internet safety -, introduction to internet safety, internet safety introduction to internet safety.

Internet Safety: Introduction to Internet Safety
Lesson 1: introduction to internet safety, introduction to internet safety.
There's almost no limit to what you can do online. The Internet makes it possible to access information quickly, communicate around the world, and much more. Unfortunately, the Internet is also home to certain risks , such as malware , spam , and phishing . If you want to stay safe online, you'll need to understand these risks and learn how to avoid them.
Adopting a safer mindset
Computers can often give us a false sense of security . After all, no one can physically harm you through a computer screen. But to stay safe online, you'll want to take a more cautious approach. Here's one way to think about it: Treat the Internet as you would a shopping mall .
Most people don't consider a mall to be an especially dangerous place. You can go there to shop and meet up with friends. But there are also small things you may do to stay safe, even if you don't think about them very often. For example, you probably wouldn't leave your car unlocked or give your credit card number to a stranger.
Apply this same mindset whenever you're online. You shouldn't be afraid to use the Internet, but remember that it comes with many of the same risks you'd face in the real world. Throughout this tutorial, we'll show you how to prepare for these risks so you can be online without putting yourself in danger.
So what are you waiting for? Let's get started!
/en/internetsafety/creating-strong-passwords/content/
The Internet: Arguments Against and for It Essay
- To find inspiration for your paper and overcome writer’s block
- As a source of information (ensure proper referencing)
- As a template for you assignment
Introduction
Has the internet brought the death of literacy.
In the early twentieth century, information could only be accessed by purchasing a piece of literature physically. There was a straight forward way of exchanging ideas because things were done manually. The internet has brought a lot of changes to the information industry. It has increased the number of people accessing writings. Initially, this was received with a lot of enthusiasm as readers thought that writers could transfer their ideas across to readers who were half way across the world. It has enabled individuals to gain knowledge in fields which were previously thought to be inaccessible. Despite all these benefits, the internet has been blamed for the death of literacy, reading and writing skills. It is quite important to look at both sides of the coin in order to come up with a fair conclusion (Malecki, 2002).
Arguments against the internet
The most important aspect to look for in a piece of literature is its creativity. One should ask themselves whether ideas reflected in a piece of writing are original and imaginative. Sadly, this is a very rare picture in most writings found on the net. It is quite common to find pieces of writing that are almost identical on different websites (Graham, 2001).
Serious literature must also be well thought out. It must be accompanied by painstaking research and articulation. Online writing is impulsive and some of the writings displayed are quite shallow. The so-called online debates are often characterized by views that don’t even hold water.
Language is another aspect that has gone down the drain after introduction of the internet. Most writers no longer pay attention to their grammar because this can be done for them through the spell checker. This does not mean that the word processor solves everything. It may not be able to detect wrong sentence order, noun and verb agreement etc. these are crucial aspects of writing that will be eliminated thanks to the internet.
The internet also makes it quite hard for professional writers to earn a decent living.
Arguments for the internet
The internet has the ability to reach any corner of the world. This means that audiences have been expanded and books that would only have been read by a small category of people can now be accessed by a higher number. More reading equates to better literacy.
Secondly, the internet makes research easier. Thanks to search engines like Google, Amazon and others. Information regarding any topic can be accessed by the touch of a button (Batty, 1997).
How the existence of the internet threatens existence of libraries
Despite all the disadvantages that have been addressed above, it is highly unlikely that real libraries will be replaced by the internet. This is because there are a number of deficiencies found on the net that leave it wanting. First of all, searching for information requires use of certain ‘keywords’. If these words are not specified, a search engine will ignore all the literary works that do not have them (Shane, 2007).
In order to access a book fully, Google or other search engines require payment through online systems. This means that individuals have to part with a lot of money just to view information. Sometimes, this information may be necessary for a short time only. Real libraries allow members to read information for a fixed duration and then books can be returned i.e. one does not have to pay for temporary access to information if they are library members (Quah, 2007).
The internet has brought many wonderful things to readers. But too much quantity has compromised on quality. Literary works have deteriorated because online editing is not serious. However, this does not mean that libraries will become extinct; they offer services which the internet cannot (Zvi, 1994).
- Zvi, G. (1994): Productivity, R&D, and the Data Constraint; journal of American Economic Review
- Shane, G. (2007): The Diffusion of the Internet and the Geography of the Digital Divide; a journal by Man sell
- Quah (2007): ICTs; Oxford University Press
- Batty, M. (1997): Virtual Geography; Melbourne Printing Press
- Graham, S. (2001): Splintering urbanism, Rout ledge Publishers
- Malecki, E. (2002): The economic geography of the Internet’s Infrastructure; a journal by Economic Geography
- Internet vs. Books: Main Source of Information
- The Internet: Introduction to Networking
- Should the Campus Library Be Always Opened?
- Harold Washington Library: The Largest Library in Midwest
- Google Does No Evil
- Network Management Importance Analysis
- The Role of Internet in Formation of Popular Culture
- Effects of Files Sharing to the Sale of CDs
- Dark Web: Criminal Activity or Dissident Communication
- Threats of the Internet
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2021, September 10). The Internet: Arguments Against and for It. https://ivypanda.com/essays/the-internet-arguments-against-and-for-it/
"The Internet: Arguments Against and for It." IvyPanda , 10 Sept. 2021, ivypanda.com/essays/the-internet-arguments-against-and-for-it/.
IvyPanda . (2021) 'The Internet: Arguments Against and for It'. 10 September.
IvyPanda . 2021. "The Internet: Arguments Against and for It." September 10, 2021. https://ivypanda.com/essays/the-internet-arguments-against-and-for-it/.
1. IvyPanda . "The Internet: Arguments Against and for It." September 10, 2021. https://ivypanda.com/essays/the-internet-arguments-against-and-for-it/.
Bibliography
IvyPanda . "The Internet: Arguments Against and for It." September 10, 2021. https://ivypanda.com/essays/the-internet-arguments-against-and-for-it/.
IvyPanda uses cookies and similar technologies to enhance your experience, enabling functionalities such as:
- Basic site functions
- Ensuring secure, safe transactions
- Secure account login
- Remembering account, browser, and regional preferences
- Remembering privacy and security settings
- Analyzing site traffic and usage
- Personalized search, content, and recommendations
- Displaying relevant, targeted ads on and off IvyPanda
Please refer to IvyPanda's Cookies Policy and Privacy Policy for detailed information.
Certain technologies we use are essential for critical functions such as security and site integrity, account authentication, security and privacy preferences, internal site usage and maintenance data, and ensuring the site operates correctly for browsing and transactions.
Cookies and similar technologies are used to enhance your experience by:
- Remembering general and regional preferences
- Personalizing content, search, recommendations, and offers
Some functions, such as personalized recommendations, account preferences, or localization, may not work correctly without these technologies. For more details, please refer to IvyPanda's Cookies Policy .
To enable personalized advertising (such as interest-based ads), we may share your data with our marketing and advertising partners using cookies and other technologies. These partners may have their own information collected about you. Turning off the personalized advertising setting won't stop you from seeing IvyPanda ads, but it may make the ads you see less relevant or more repetitive.
Personalized advertising may be considered a "sale" or "sharing" of the information under California and other state privacy laws, and you may have the right to opt out. Turning off personalized advertising allows you to exercise your right to opt out. Learn more in IvyPanda's Cookies Policy and Privacy Policy .
- Kaspersky Premium
- Kaspersky Plus
- Kaspersky Standard
- Kaspersky Safe Kids
- Kaspersky VPN Secure Connection
- Kaspersky Password Manager
- Renew Licence
- Trials & Downloads
- KSOS Portal
- Renew SMB licence
- Find a partner
- Company Account
- Kaspersky TIP
- Cloud Console
- Product Training & Certification
- Find a reseller
- Find a distributor
- Partnership with Kaspersky
- Get to know us
- Company overview
- Transparency
- Corporate News
- Awards & Recognitions
- Top 3 Rankings
- Press center
- Sponsorships
- Policy blog
Top 15 internet safety rules and what not to do online

So much of our daily life revolves around the internet, from work to education and even talking with friends. A 2021 survey found that the average US household had around 25 internet-connected devices, up from 11 in 2019. The more online accounts and devices you have, the greater the scope for cybercriminals to cause you harm. That’s why it's now ever more essential to understand internet safety rules which protect you and your family from threats that may harm your data and devices. Read on to find out about key internet dangers and the ways to stay safe online.
The Key Dangers of the Internet
When you and your family use the internet, you are (often unknowingly) exposing yourself to a wide range of potential online threats. Digital landscapes as we know them are constantly evolving as cybercriminals devise new ways to target internet users. Here is a list of just some of the biggest internet dangers you and your family need to watch out for:
- Identity theft.
- Data breaches.
- Malware and viruses.
- Phishing and scam emails.
- Fake websites.
- Online scams.
- Romance scams.
- Inappropriate content.
- Cyberbullying.
- Faulty privacy settings.
Essential Internet Safety Tips
To avoid all of these dangers, we recommend following our essential internet safety tips when you or your family are online:
1. Make sure you’re using a secure internet connection
Although using public Wi-Fi is not recommended, it’s sometimes unavoidable when you are out and about. However, when you go online in a public place and use a public Wi-Fi connection, you have no direct control over its security, which could leave you vulnerable to cyberattacks. So, if you are using public Wi-Fi, avoid carrying out personal transactions that use sensitive data, such as online banking or online shopping.
If you need to do any one of these, use a Virtual Private Network or VPN . A VPN will protect any of the data you send over an unsecured network via real-time encryption. If you don't use a VPN, we recommend saving any personal transactions until you can use a trusted internet connection. You can find out more about what a VPN is here .
2. Choose strong passwords
Passwords are one of the biggest weak spots when it comes to cybersecurity. People often choose passwords that are easy to remember and, therefore, easy for hackers to crack with hacking software. In addition to this, using the same password for multiple sites puts your data at further risk. If hackers obtain your credentials from one site, they can potentially access other websites which use the same login details.
Select strong passwords that are harder for cybercriminals to crack. A strong password is:
- Long – made up of at least 12 characters (ideally more).
- A mix of characters – upper-case and lower-case letters plus symbols and numbers.
- Avoids the obvious – such as using sequential numbers (“1234”) or personal information that someone who knows you might guess (or that might already be online), such as your date of birth or a pet’s name.
- Avoids memorable keyboard paths.
Using a password manager can help. Password managers help users create strong passwords, store them in a digital vault (which is protected by a single master password) and retrieve them when logging into accounts online.
3. Enable multi-factor authentication where you can
Multifactor authentication (MFA) is an authentication method that asks users to provide two or more verification methods to access an online account. For example, instead of simply asking for a username or password, multifactor authentication goes further by requesting additional information, such as:
- An extra one-time password that the website's authentication servers send to the user's phone or email address.
- Answers to personal security questions.
- A fingerprint or other biometric information, such as voice or face recognition.
Multifactor authentication decreases the likelihood of a successful cyberattack. To make your online accounts more secure, it’s a good idea to implement multifactor authentication where possible. You can also consider using a third-party authenticator app, such as Google Authenticator or Authy, to help with your internet security.
4. Keep software and operating systems updated
Developers are constantly working to make products safe, monitoring the latest threats and rolling out security patches in case of vulnerabilities in their software. By using the latest versions of your operating systems and apps, you will benefit from the latest security patches. This is especially important for apps that contain payment, health or other sensitive information about a user.
5. Check that websites look and feel reliable
For any website you visit, especially ones you transact with (such as e-commerce sites), it's crucial that they are reliable. A key element to look out for is an SSL/security certificate . This means, lookout for URLs that start with “HTTPS” rather than “HTTP” (the “S” stands for “secure”) and have a padlock icon in the address bar. Other trust signals include:
- Text which is free from spelling and grammar mistakes – reputable brands will make an effort to ensure their websites are well-written and proofread.
- Images that are not pixelated and fit the screen's width correctly.
- Ads that feel organic and are not too overpowering.
- No sudden changes in color or theme. In some cases, where users have interacted with a particular website and returned to a familiar page from a link, subtle color or design changes might indicate forgery.
- The accepted standards of online payments – legitimate ecommerce websites use credit or debit card portals or PayPal, only. If a website is using another form of digital money transfer to accept payments, it is probably fraudulent.
6. Review your privacy settings and understand privacy policies
Marketers love to know all about you, and so do hackers. Both can learn a lot from your browsing and social media usage. But you can take charge of how much information third-parties can access. Both web browsers and mobile operating systems have settings to protect your privacy online. Social media sites, such as Facebook, Twitter, Instagram, LinkedIn, amongst others, have privacy-enhancing settings that you can activate. It’s worth taking a while to review your privacy settings across the board and make sure they are set to a level you are comfortable with.
Many of us accept privacy policies without reading them, but with so much data used for marketing and advertising (and hacking) purposes, it's a good idea to review the privacy policies of websites and apps you use, in order to understand how your data is collected and analyzed. However, bear in mind that even if your settings are set to private, very little data online is totally private. Hackers, website administrators and law enforcement could still have access to the information you regard as private.

7. Be careful of suspicious links and where you click
A careless click can expose your personal data online or infect your device with malware . That’s why it's essential to browse consciously and avoid certain types of online content – such as links from untrusted sources and spam emails, online quizzes, clickbait, ‘free’ offers or unsolicited ads.
If you receive an email that you're not sure about, avoid clicking on any links in it or opening any attachments.
In fact, it's best to avoid opening untrusted emails at all. If you’re not sure whether an email is legitimate or not, go directly to the source. For example, if you receive a suspicious email from your “bank”, call your bank and ask them if the email is genuine.
When you’re on a website, make sure links click through to relevant or expected topics. For example, if you click on a link that you think is about safaris in Africa, but instead you're taken to a clickbait-style page about celebrity weight loss or a “where are they now?” style piece, then quickly close the page.

8. Make sure your devices are secure
With up to 60% of people using mobile devices for shopping and finding information online, instead of a desktop, it’s important that they are secured correctly. With all your devices – phones, computers, tablets, smartwatches, smart TVs, etc. – it's good practice to use passwords or passcodes and other security options like fingerprint readers or face-scanning technology. These measures will reduce the likelihood of a cyberattack or your personal data being stolen by hackers.
9. Backup data regularly
It's important to backup important personal information on external hard drives and regularly create new backups. Ransomware – a type of malware – involves cybercriminals locking your computer so you can’t access valuable files. Backing up your data – and your family’s data – helps mitigate the impact of a ransomware attack. You can protect yourself further with appropriate security software. Other forms of malware deny you access to your personal data by overwhelming your system or simply deleting files, so be careful.
10. Close unused accounts
Over the years, many of us accumulate old accounts that we no longer use. These can be a weak link in terms of safety when using the internet – not only are old accounts more likely to have weaker passwords, but some of those sites may have poor data protection policies. In addition, cybercriminals could piece together the information you have left in them, for example, old social media profiles – such as your date of birth or location, etc. – to build up a picture of your identity in an attempt to hack you later. As a result, we recommend closing your old online accounts and requesting that your data be deleted from the relevant third-party servers.
11. Be careful what you download
A top goal of cybercriminals is to trick you into downloading malware, which can be used to open a “backdoor” to your machine. Malware might be disguised as an app – anything from a popular game to something that checks traffic or the weather. Or, it could be hidden on a malicious website that attempts to install malware on your device.
Malware causes damage – such as disrupting how your device operates, stealing your personal data or allowing unauthorized access to your machine. This usually requires some action on your part, but there are also drive-by downloads , where a website attempts to install software on your computer without asking for permission first. Think carefully before visiting a new website or downloading anything onto your device, and only download content from trusted or official sources. Regularly check your download folders and if unknown files appear on your system (potentially, from a drive-by), delete them immediately.
12. Be careful what you post and where
The internet does not have a delete key. Any comment or image you post online may stay online forever because removing the original won’t remove any copies that other people may have made. There is no way for you to ‘take back’ a comment you wish you hadn't made or remove an embarrassing image you posted. So, don't put anything online that you would not want a parent or prospective employer to see.
Similarly, be careful about disclosing personal information about yourself online. For example, avoid disclosing your social security number, address or date of birth in social media bios. You wouldn't hand personal information out to strangers individually, so don't hand it out to millions of people online.
Be careful about where you display or submit your email address. It's good to have a secondary, throwaway email account that you use solely for email sign-ups and subscriptions, separate from the one you use for friends and family, and separate from the one you use for work.
13. Be careful who you meet online
People you meet online are not always who they claim to be. Indeed, they may not even be real. Fake social media profiles are a popular way for hackers to groom unwary internet users and pick their cyber pockets. Apply the same caution in your online social life as you would for your in-person social life. This is particularly true with the rise of online dating scams in recent years .
14. Double check online information
Sadly, fake news, misinformation and disinformation are all present on the internet. It's easy to feel lost with the flood of information we're exposed to every day. If you read something you are unsure of, do your own research to establish the facts. Reliable websites will have references to the original information and source materials. Suspicious pages won’t offer any references at all. Read our guide to spotting fake news here .
15. Use a good antivirus and keep it updated
As well as following safety tips for online behavior, it's essential to use a good quality antivirus provider . Internet security software guards your devices and data and blocks common threats like viruses and malware (plus complex ones like spy apps, “cryptolockers” and XSS attacks). As with all operating systems and apps, it's essential to keep your antivirus updated to stay ahead of the latest cyberthreats.
3 Online safety rules for the kids
Although many of the tips to stay safe online are the same for adults and children, they are not easy or straightforward to explain. Often, children can accidentally be a gateway for malicious actors to gain access to your digital systems. It is therefore important to teach your kids the essentials of staying safe online in order to protect your home network from any unwanted accidents. Here are 3 areas that you should cover:
Digital Footprint
Your digital footprint, what exists of you online after usage, is an important concept that children need to know about. When teaching children about this, it’s important to focus on how information is readily available and how others could interact with this data (for example, email addresses and usernames that contain identifying information, which could be used for criminal activity). Wider discussions can also come from this, such as sharing content online (through social media, gaming accounts and emails). Make sure to clearly state what content is not allowed on the internet (photos, address, phone numbers and middle names).
Strong passwords are integral to modern cybersecurity measures today. Instructing children from a young age about the importance of strong passwords (ones that consists of at least 12 characters and are a mixture of letters, numbers and symbols) and their appropriate storage is one of the simplest ways to make the internet safer for your family. This is also why it can be very useful to have a password management system that can automatically fill in password credentials for different websites.
Communication
One of the most accessed routes for all manner of cybercriminal, online messaging and communication is a “must-have” conversation for your children’s safety. Primarily, it is important to explain how to identify and avoid messages, suspicious links, downloads or emails from strangers asking for identifying information online. This can also lead to a wider discussion about how to detect phishing scams and fake websites. The second most important part of safe online communication is correct engagement with others. Much like the real world, staying safe can sometimes depend on staying vigilant, engaging in polite communication and learning how to identify and not engage with bullying. Educate your child on what cyberbullying looks like and how to act kindly to others online.
Recommended products:
- Kaspersky Home Security
Further reading:
- Do’s and don’ts for teaching internet safety to kids
- What is a security breach and how to avoid one?
- What is a Digital Footprint?
- Spam & Phishing | Phishing Scam Threats
Related articles
We use cookies to make your experience of our websites better. By using and further navigating this website you accept this. Detailed information about the use of cookies on this website is available by clicking on more information .
Home — Essay Samples — Information Science and Technology — Internet — The Advantages of the Internet
The Advantages of The Internet
- Categories: Internet
About this sample

Words: 804 |
Published: Jan 30, 2024
Words: 804 | Pages: 2 | 5 min read
Table of contents
Introduction, personal benefits, educational benefits, societal benefits, counterargument and refutation.
- Access to information: The internet offers a wide range of resources that provide individuals with access to a wealth of information. Research materials, academic papers, journals, and educational videos are readily available and can be accessed without leaving the comfort of one's home.
- Communication opportunities: Instant messaging and video calls have allowed individuals to connect with friends, family, and loved ones worldwide. Social media platforms have also provided new and exciting ways for people to communicate and share with one another.
- Entertainment and leisure options: Streaming services offer a plethora of movies and TV shows at one's convenience. Online gaming has allowed individuals to play and connect with gamers from all around the world, providing an avenue for socialization and entertainment.
- E-Learning and online education: The internet has made education available to anyone with a computer and access to the internet. E-learning has provided an avenue for individuals to gain knowledge and skills, irrespective of geographical barriers.
- Promotes collaborative learning: With online forums and discussion boards, learners can collaborate with others to discuss and share ideas. Virtual classrooms have facilitated group activities and project discussions, providing an avenue for interaction and knowledge sharing.
- Provides equal educational opportunities: The internet has created opportunities for those living in underprivileged areas to access quality education. It has also provided accessibility for disabled individuals who would otherwise be limited in their access to education.
- Economic growth and job opportunities: The internet has created numerous business and job opportunities for individuals, especially in the online space and freelancing. The global market reach has been particularly helpful in expanding businesses beyond geographical barriers.
- Enhanced communication and networking: The internet has facilitated international collaborations and provided an avenue for individuals and organizations to connect. Social media platforms have allowed individuals to create and maintain relationships with others, irrespective of geographical locations.
- Democratization of information: The internet has provided an avenue for citizen journalism and online activism, promoting awareness and participation in societal issues.
- Privacy concerns and cybercrime: The internet has made individuals' personal information vulnerable to hacking, which could lead to identity theft and other cybercrimes.
- Misinformation and fake news: The internet has made it easy for individuals to create and spread misinformation, which could have dire consequences on individuals and society.
References:
- Anderson, C. (2018). Advantages and Disadvantages of the Internet. Toopics. Retrieved from https://toopics.com/advantages-and-disadvantages-of-internet/.
- Greenhow, C., Robelia, B., & Hughes, J. E. (2009). Learning, teaching, and scholarship in a digital age : Web 2.0 and classroom research: What path should we take now?. Educational researcher, 38(4), 246-259.
- Walter, S. G., & Su, F. (2011). E-learning 2.0: Social networking and collaboration in learning and teaching. Journal of educational technology development and exchange, 4(1), 1-14.
- Yang, D., & Chen, C. C. (2018). Play, knowledge, and learning: Gaming cultures and the learning society. Peter Lang.
- Taiwo, A. A., & Downe, A. G. (2013). E-learning in Nigeria: bridging the knowledge divide. Journal of education and practice, 4(8), 94-101.
- Hong, Y. Y., & Chan, K. F. (2019). The role of Internet technology in shaping and facilitating international business growth. Journal of International Business Research and Marketing, 4(4), 60-70.
- Moorthy, K., Kong, H. J., & Thatcher, M. (2017). Globalization, networked society , and cultural software: The emergence of a new social order. Routledge.
- Smith, M. A. (2014). Politics, Democracy and the New Media. Routledge.
- Boyd, D. (2019). Media literacy in the digital age. Routledge.

Cite this Essay
To export a reference to this article please select a referencing style below:
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Verified writer
- Expert in: Information Science and Technology

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
2 pages / 864 words
1 pages / 675 words
1 pages / 544 words
4 pages / 1815 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online
Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Internet
The Internet has become one of the best inventions in the modern world .it is even difficult to imagine how life would be in the absence of the internet. the internet is a viewed to be the current trend that everyone should fit [...]
The Internet has become an integral part of modern life, shaping the way we access information, interact with others, and process knowledge. It has revolutionized the way we think and make decisions. In this essay, we will [...]
The excessive use of the internet has become a prevalent concern in today's digital age. The internet, once a revolutionary tool for communication and information, has now transformed into an integral part of our daily lives. [...]
The internet has revolutionized the way we communicate and has become an essential tool in the modern world. Before its advent, communication was limited to small radius networks, but with the laying of the first cable in the [...]
As an ambitious student in the end of my 17 years of age, I am aware of the idea about IoT as it is very possible that in the near future we would all start using this concept of connecting devices that exchange information and [...]
Everyone is unique. We all have our own set of traits, DNA, and fingerprints. Each individual possesses their own unique characteristics, interests, and talents to make up a unique identity. Our identity combines all of these [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free

IMAGES
VIDEO
COMMENTS
Equally, we should not want an internet that is less global, is insecure, or where basic human rights are not respected. The problem is not with the term internet safety, per se. It is more about ...
35 Excellent Internet Essay Topics. Internet Essay Topics and Ideas (Inspired by Safer Internet Day)— Many people today begin using a variety of electronic devices as toddlers and are often interacting online on various social networks by the time they start school. Indeed, internet use has touched nearly every corner of the world.
500 Words Essay on Internet Safety Understanding Internet Safety. Internet safety is about being protected online. When we use the internet, we share information about ourselves, sometimes without knowing it. It's like leaving the door to your house open; if you're not careful, someone you don't want inside might come in.
As Internet use by children and teenagers increases, so do concerns about their online safety. In this paper, Adina Farrukh, Rebecca Sadwick, and John Villasenor discuss the online risks young ...
Get custom essay. Ultimately, the importance of internet privacy extends beyond individual convenience; it is a fundamental right that underpins our freedom, security, and individuality in the digital age. By recognizing the significance of internet privacy and taking meaningful steps to protect it, we can ensure that the digital landscape ...
It has increased the research abilities of various professionals therefore contributing to the development of our society. Knut asserts that the internet has served as an enabler for all forms of innovation in the society (1). This positive attributes of the internet are all true and the prevalence of the internet has greatly affected societies ...
Another negative aspect that raises opposition to COPPA and CIPA is the impossibility of controlling children in places other than home or a school library.
Harmful effects on cognitive development: Empirical evidence suggests that internet use can have both positive and negative impacts on cognitive development, depending on the person and the circumstances. There is evidence that children's cognitive development can be damaged by prolonged internet use, including the development of memory ...
In conclusion, the case for providing free internet access to everyone is a compelling one. The internet has become an integral part of modern life, impacting education, employment, social connections, and global progress. Ensuring universal access to the internet aligns with the principles of equality, social inclusion, and economic opportunity.
History of the Internet. In the late 1960s, some proponents of the internet conducted research to find out the likelihood of interconnection between systems using the ARPANET. Using the Internet to Solve a Crime. The purpose of my research is to highlight some of the uses of the internet in solving crime.
If we talk about the major advantage of computers, it is the Internet. The Internet is the human successful invention. For humans it has made to do a lot of things quickly and effortlessly. For example, people can contact and communicate with anyone in the world, and also, sitting at home, they can shop, and they can also earn money.
Print/Save as PDF. Internet safety is the practice of following actionable guidelines, understanding modern technology, and protecting your digital devices so you can defend against malicious parts of the online world. It's one of the main parts of a strong digital citizenship program in any school. That's because the internet provides near ...
Online safety, otherwise termed as internet safety, involves the prevention and protection from security risks associated with using the internet as well as deterring any computer crime that may be posted online (Scheff, 2017). Institute's report on how parents viewed the safety of their children online, only 37% of the parent's felt that ...
Cyber Security Essay. Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today's world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software.
Make a claim. Provide the grounds (evidence) for the claim. Explain the warrant (how the grounds support the claim) Discuss possible rebuttals to the claim, identifying the limits of the argument and showing that you have considered alternative perspectives. The Toulmin model is a common approach in academic essays.
Focus Area #3: Writing the Conclusion. It's common to conclude an argumentative essay by reiterating the thesis statement in some way, either by reminding the reader what the overarching argument was in the first place or by reviewing the main points and evidence that you covered.
Introduction to Internet safety. There's almost no limit to what you can do online. The Internet makes it possible to access information quickly, communicate around the world, and much more. Unfortunately, the Internet is also home to certain risks, such as malware, spam, and phishing.
Essay On Internet Safety. 1064 Words5 Pages. It sounds like the complaint of an adult: children these days are narrow-minded, just not as creative or social as they used to be because of the internet; but the American Psychiatric Association think that childrens digital journey makes them well-informed, happy, social and lets them keep up with ...
Internet Safety Essay. 777 Words4 Pages. In today's fast-paced world of technology, the World Wide Web has become a fascinating world of wonder for not only adults but for kids too. With the wide array of electronics - smart phones, tablets, internet-bound game devices, and digital televisions - found in most homes, a child's access to the ...
The internet has the ability to reach any corner of the world. This means that audiences have been expanded and books that would only have been read by a small category of people can now be accessed by a higher number. More reading equates to better literacy. Secondly, the internet makes research easier.
It's good to have a secondary, throwaway email account that you use solely for email sign-ups and subscriptions, separate from the one you use for friends and family, and separate from the one you use for work. 13. Be careful who you meet online. People you meet online are not always who they claim to be.
The internet has revolutionized the way individuals access information. The following are some of the personal benefits of the internet: Access to information: The internet offers a wide range of resources that provide individuals with access to a wealth of information. Research materials, academic papers, journals, and educational videos are ...
Persuasive Essay On Internet Safety Thesis Statement On Internet Usage Importance Of Internet In Education Essay The Internet and the Future of Language Essays. ... smythe then goes on to say that we need tighter legislation around the internet. Balkam furthers this argument with ideas from the non-profit FOSI (Family Online Safety Institute ...