Computer Network
- Introduction
- Architecture
- Computer Network Types
- Transmission Modes
- TCP/IP Model

Physical Layer
- Digital Transmission
- Transmission Media
- Guided Media
- UnGuided Media
- Multiplexing
- Switching Modes
- Switching Techniques
- Data Link layer
- Error Detection
- Error Correction
- Data Link Controls
- Network Layer
- Network Addressing
- Network Layer Protocols
- Routing Algorithm
- Distance Vector
- Link State Routing
- Transport Layer
- Transport Layer Protocols
- Application Layer
- Client & Server Model
Application Protocols
Network security.
- Digital Signature
- What is Router
- OSI vs TCP/IP
- IPv4 vs IPv6
- ARP Packet Format
- Working of ARP
- FTP Commands
- I2P Protocol
- Sliding Window Protocol
- SPI Protocol
- ARP Commands
- ARP Request
- ARP - Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN Protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT Protocol
- OSPF Protocol
- Stop & Wait Protocol
- IMAP Protocol
- POP Protocol
- Go-Back-N ARQ
- Connection-Oriented vs Connectionless Service
- CDMA vs GSM
- What is MAC Address
- Modem vs Router
- Switch vs Router
- USB 2.0 vs USB 3.0
- CSMA CA vs CSMA CD
- Multiple Access Protocols
- IMAP vs. POP3
- SSH Meaning
- Status Code 400
- MIME Protocol
- What is a proxy server and how does it work
- How to set up and use a proxy server
- What is network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology vs Ring topology
- Bus topology vs Star topology
- Circuit Switching vs Packet switching
- star vs ring topology
- Router vs Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- ASA features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID) in Computer Network
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM) in Computer Network
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- How does BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Functions, Advantages and Disadvantages of the Physical Layer
- Types of Internet Connection
- Noisy and Noiseless Channel
- Advantages and Disadvantages of Bus Topology
- Advantages and Disadvantages of Ring Topology
- Advantages and Disadvantages of Star Topology
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security and Software security
- Information security and Network security
- Security Engineer and Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
- Difference Between Infrastructure and Infrastructure Less Network
- Collision Avoidance in Wireless Networks
- Difference Engine and Analytical Engine
- Hotspot 2.0
- Intrusion Prevention System (IPS)
- Modes of Connection Bluetooth
- Noisy Channel protocols
- Parzen Windows density Estimation Technique
- Principle of Information System Security
- What are Bots, Botnets, and Zombies
- Windows Memory Management
- Wireless dos attack on Wifi
- Design Principles of Security in Distributed Systems
- MAC Filtering
- Principles of Network Applications
- Time-to-Live (TTL)
- What is 1000 BASE-T
- What is the difference between 802.11ac and 802.11ax
- Differentiate between Circuit Switching, Message Switching, and Packet Switching
- What is Web 3.0
- Collision Detection in CSMA/CD
- Ipv4 Header in Computer Networks
- Layered Architecture in Computer Networks
- Define URL in Computer Networks
- MAN in Computer Networks
- Routing Protocols in Computer Networks
- Flooding in Computer Network
- CRC in Computer Network
- Application of Computer Network
- Computer Network Architect
- Design Issues for the Layers of Computer Networks
- What is AMD (Advanced Micro Devices)
- Protocol in Computer Network
- Computer Network Projects
- Different Types of Routers
- Wireless Distribution System (WDS)
- Network Time Protocol
- Address Resolution Protocol (ARP) and its types in Computer Network
- Automatic Repeat ReQuest (ARQ) in Computer Networks
- Bluetooth in Computer Networks
- Circuit Switching in Computer Network
- Computer Hardware and Networking Course
- Ring Topology in a Computer Network
- Token Ring in Computer Networks
- Medium Access Control in Computer Network
- Need for Computer Network
- Repeater in Computer Network
- Computer Networking: a Top Down Approach
- What is Multiplexing in Computer Network
- Body Area Network (BAN)
- INS AND OUT OF DATA STREAMING
- Streaming stored video
- Cellular Network
- How can devices on a Network be identified
- How Does the Internet Work
- Authentication Server
- What is Cloud Backup and How does it Work
- Communication Protocols In System Design
- Extensible Authentication Protocol (EAP)
- Role-Based Access Control (RBAC)
- Network Enumeration Tools
- Network Protocol Testing
- Windows Networking Commands
- Advantages and Disadvantages of WLAN
- Anonymous File Transfer Protocol (AFTP)
- Automatic Private IP Addressing
- What is Deep Web
- USB-C (USB Type C)
- User Authentication
- What is a vCard
- ipv4 Headers
- Difference between Token ring and Ethernet Token Ring
- Server Message Block protocol (SMB protocol)
- Session Border Controllers (SBC)
- Short Message Service Center (SMSC)
- What is a Mail Server
- What are Communication Networks
- Initialization Vector
- What is Fiber Optics
- Open Networking
- Access Ports Vs Trunk Ports
- Edge Routers
- IPTV (Internet Protocol Television)
- Wireless Internet Service Provider (WISP)
- Wireless Backhaul
- Define Protocol in Computer Network
- Virtual Network Adapter
- Virtual Routing and Forwarding
- Virtual Switches(vSwitches)
- VLAN (Virtual LAN)
- Wireless Mesh Network (WMN)
- What is Gateway in Computer Network
- Radio Access Network (RAN)
- What is File Sharing
- Passive Optical Network (PON)
- Private IP address
- Public Key Certificate
- What is Bridge in Computer Network
- Ping Sweep (ICMP Sweep)
- Print Server
- WIFI Pineapple
- Walled Garden
- Wireless ISP (wireless Internet service provider or WISP)
- Bridge vs Repeater
- Hardware Security Module (HSM)
- Public Switched Telephone Network
- Analog Telephone Adapter (ATA)
- Host Bus Adapter (HBA)
- ISCSI initiator
- Simplest Protocol
- Telecommunication Networks
- What is WPS in Wi-Fi
- What are the Most Important Email Security Protocols
- What is Data Governance and Why does it Matter
- Carrier Network
- Most Secure Network Protocol
- Network SMB
- BGP vs. EIGRP: What's the Difference
- Wireless Security: WEP, WPA, WPA2 and WPA3 differences
- Cloud Radio Access Network (C-RAN)
- Bits Per Second (bps or bit/sec)
- Blade Server
- command-and-control server (C&C server)
- Computer Network MCQ
- Computer Network MCQ Part2
Interview Questions
- Networking Questions
Latest Courses
We provides tutorials and interview questions of all technology like java tutorial, android, java frameworks
Contact info
G-13, 2nd Floor, Sec-3, Noida, UP, 201301, India
[email protected] .
Latest Post
PRIVACY POLICY
Online Compiler
- Artificial Intelligence
- Generative AI
- Cloud Computing
- CPUs and Processors
- Data Center
- Edge Computing
- Enterprise Storage
- Virtualization
- Enterprise Buyer’s Guides
- Internet of Things
- Network Management Software
- Network Security
- United States
- Spotlight: AI in Enterprise
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Copyright Notice
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld

What is the OSI model? How to explain and remember its 7 layers
A tutorial on the open systems interconnection (osi) networking reference model plus tips on how to memorize the seven layers..

The Open Systems Interconnect (OSI) model is a conceptual framework that describes networking or telecommunications systems as seven layers, each with its own function.
The layers help network pros visualize what is going on within their networks and can help network managers narrow down problems (is it a physical issue or something with the application?), as well as computer programmers (when developing an application, which other layers does it need to work with?). Tech vendors selling new products will often refer to the OSI model to help customers understand which layer their products work with or whether it works “across the stack”.
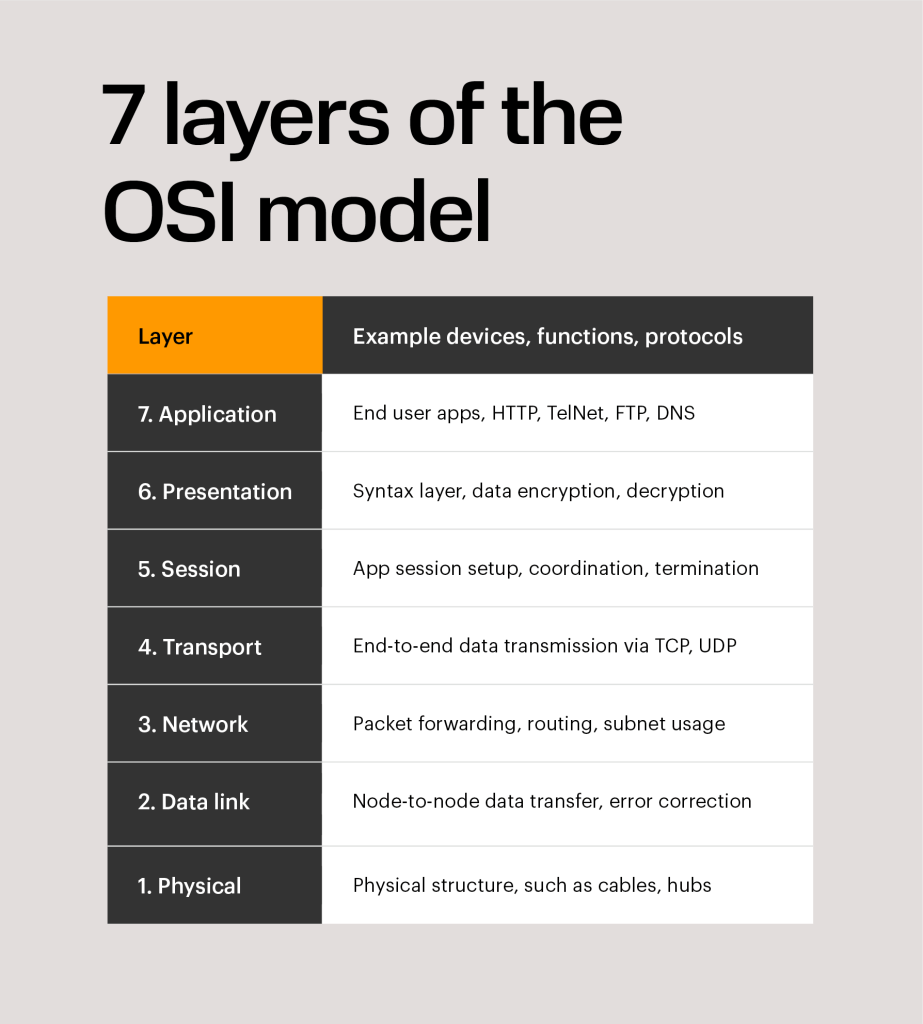
The 7 layers of the OSI model
The layers (from bottom to top) are: Physical, Data Link, Network, Transport, Session, Presentation, and Application.
It wasn’t always this way. Conceived in the 1970s when computer networking was taking off, two separate models were merged in 1983 and published in 1984 to create the OSI model that most people are familiar with today. Most descriptions of the OSI model go from top to bottom, with the numbers going from Layer 7 down to Layer 1.
The layers, and what they represent, are as follows:
Layer 7: Application
The Application Layer in the OSI model is the layer that is the “closest to the end user”. It receives information directly from users and displays incoming data to the user. Oddly enough, applications themselves do not reside at the application layer. Instead the layer facilitates communication through lower layers in order to establish connections with applications at the other end. Web browsers (Google Chrome, Firefox, Safari, etc.) TelNet, and FTP, are examples of communications that rely on Layer 7.
Layer 6: Presentation
The Presentation Layer represents the area that is independent of data representation at the application layer. In general, it represents the preparation or translation of application format to network format, or from network formatting to application format. In other words, the layer “presents” data for the application or the network. A good example of this is encryption and decryption of data for secure transmission; this happens at Layer 6.
Layer 5: Session
When two computers or other networked devices need to speak with one another, a session needs to be created, and this is done at the Session Layer . Functions at this layer involve setup, coordination (how long should a system wait for a response, for example) and termination between the applications at each end of the session.
Layer 4: Transport
The Transport Layer deals with the coordination of the data transfer between end systems and hosts. How much data to send, at what rate, where it goes, etc. The best known example of the Transport Layer is the Transmission Control Protocol (TCP), which is built on top of the Internet Protocol (IP), commonly known as TCP/IP. TCP and UDP port numbers work at Layer 4, while IP addresses work at Layer 3, the Network Layer.
Layer 3: Network
Here at the Network Layer is where you’ll find most of the router functionality that most networking professionals care about and love. In its most basic sense, this layer is responsible for packet forwarding, including routing through different routers . You might know that your Boston computer wants to connect to a server in California, but there are millions of different paths to take. Routers at this layer help do this efficiently.

Layer 2: Data Link
The Data Link Layer provides node-to-node data transfer (between two directly connected nodes), and also handles error correction from the physical layer. Two sublayers exist here as well–the Media Access Control (MAC) layer and the Logical Link Control (LLC) layer. In the networking world, most switches operate at Layer 2. But it’s not that simple. Some switches also operate at Layer 3 in order to support virtual LANs that may span more than one switch subnet, which requires routing capabilities.
Layer 1: Physical
At the bottom of our OSI model we have the Physical Layer, which represents the electrical and physical representation of the system. This can include everything from the cable type, radio frequency link (as in a Wi-Fi network), as well as the layout of pins, voltages, and other physical requirements. When a networking problem occurs, many networking pros go right to the physical layer to check that all of the cables are properly connected and that the power plug hasn’t been pulled from the router, switch or computer, for example.
Why you need to know the 7 OSI layers
Most people in IT will likely need to know about the different layers when they’re going for their certifications, much like a civics student needs to learn about the three branches of the US government. After that, you hear about the OSI model when vendors are making pitches about which layers their products work with.
In a Quora post asking about the purpose of the OSI model, Vikram Kumar answered this way: “The purpose of the OSI reference model is to guide vendors and developers so the digital communication products and software programs they create will interoperate, and to facilitate clear comparisons among communications tools.”
While some people may argue that the OSI model is obsolete (due to its conceptual nature) and less important than the four layers of the TCP/IP model, Kumar says that “it is difficult to read about networking technology today without seeing references to the OSI model and its layers, because the model’s structure helps to frame discussions of protocols and contrast various technologies.”
If you can understand the OSI model and its layers, you can also then understand which protocols and devices can interoperate with each other when new technologies are developed and explained.
The OSI model remains relevant
In a post on GeeksforGeeks, contributor Vabhav Bilotia argues several reasons why the OSI model remains relevant, especially when it comes to security and determining where technical risks and vulnerabilities may exist.
For example, by understanding the different layers, enterprise security teams can identify and classify physical access, where the data is sitting, and provide an inventory of the applications that employees use to access data and resources.
“Knowing where the majority of your company’s data is held, whether on-premises or in cloud services, will help define your information security policy,” writes Bilotia. “You can invest in the correct solutions that provide you data visibility within the proper OSI layers once you have this knowledge.”
In addition, the OSI model can be used to understand cloud infrastructure migrations, particularly when it comes to securing data within the cloud.
And because the model has been around for so long and understood by so many, the uniform vocabulary and terms helps networking professionals understand quickly about the components of the networking system “While this paradigm is not directly implemented in today’s TCP/IP networks, it is a useful conceptual model for relating multiple technologies to one another and implementing the appropriate technology in the appropriate way,” Bilotia writes. We couldn’t agree more.
How to remember the OSI Model 7 layers: 8 mnemonic tricks
If you need to memorize the layers for a college or certification test, here are a few sentences to help remember them in order. The first letter of each word is the same as the first letter an OSI layer.
From Application to Physical (Layer 7 to Layer 1):
- All People Seem To Need Data Processing
- All Pros Search Top Notch Donut Places
- A Penguin Said That Nobody Drinks Pepsi
- A Priest Saw Two Nuns Doing Pushups
From Physical to Application (Layer 1 to Layer 7):
- Please Do Not Throw Sausage Pizza Away
- Pew! Dead Ninja Turtles Smell Particularly Awful
- People Don’t Need To See Paula Abdul
- Pete Doesn’t Need To Sell Pickles Anymore
Related content
Network jobs watch: hiring, skills and certification trends, first combined ai-ran network from nvidia and softbank supports inferencing, claims return of $5 for every $1 invested, versa unveils versaone converged security, networking platform, how network startups could win over enterprises, from our editors straight to your inbox.

The first gadget Keith Shaw ever wanted was the Merlin, a red plastic toy that beeped and played Tic-Tac-Toe and various other games. A child of the '70s and teenager of the '80s, Shaw has been a fan of computers, technology and video games right from the start. He won an award in 8th grade for programming a game on the school's only computer, and saved his allowance to buy an Atari 2600.
Shaw has a bachelor's degree in newspaper journalism from Syracuse University and has worked at a variety of newspapers in New York, Florida and Massachusetts, as well as Computerworld and Network World. He won an award from the American Society of Business Publication Editors for a 2003 article on anti-spam testing, and a Gold Award in their 2010 Digital Awards Competition for the "ABCs of IT" video series.
Shaw is also the co-creator of taquitos.net , the crunchiest site on the InterWeb, which has taste-tested and reviewed more than 4,000 varieties of snack foods.
More from this author
What is a network router how ai networking driving its evolution, bgp: what is border gateway protocol, and how does it work, what is a virtual machine, and why are they so useful, what is a network switch and how does it work, what is zero trust network access, what is sd-wan, and what does it mean for networking, security, cloud, what is beamforming and how does it make wireless better, colleges expand vpn capacity, conferencing to answer covid-19, show me more, nvidia blackwell chips face serious heating issues.

How Trump’s appointment of Brendan Carr as FCC chairman will affect enterprises

El Capitan bumps Frontier to claim world’s fastest supercomputer title

Has the hype around ‘Internet of Things’ paid off? | Ep. 145

Episode 1: Understanding Cisco’s Converged SDN Transport

Episode 2: Pluggable Optics and the Internet for the Future

How to use the W diff command

2-Minute Linux Tips: How to use the sdiff command

How to use the diff3 command


IMAGES
VIDEO