Salesforce , Python , SQL , & other ways to put your data where you need it
Need event music 🎸, azure rbac role assignment faq.
03 Feb 2024 🔖 security tutorial 💬 EN

Table of Contents
The 3 components of an azure rbac role assignment, create an azure rbac role assignment, target scopes, source principal identities, combining several azure rbac role assignments to fulfill a task.
Below are a few frequently asked questions about Azure RBAC Role Assignments.
Many thanks to colleagues who helped me a lot with editing the wording when I wrote a similar document for internal training.
What is an Azure RBAC Role Assignment?
An Azure RBAC Role Assignment , not to be confused with an Entra RBAC Role Assignment , grants a given identity (that is, one that exists within Microsoft Entra ID) permission to perform specific types of actions against a specific “scope” of Azure resource(s).
In the model of access control where authentication (“proving a nonhuman is who it says it is”) and authorization (“proving a given, authenticated nonhuman is permitted to do what it is trying to do”) , an Azure RBAC Role Assignment helps solve problems related to authorization . 🔐
Microsoft Entra ID , or “Entra” for short, is the new name for what was known as “Azure Active Directory” or “AAD.”
An Azure RBAC Role Assignment is a named Azure resource whose purpose is to describe a junction of three other Azure or Entra resource IDs:
- An Azure RBAC “role” (whether “built-in” and maintained by Microsoft or “custom” and maintained by your company) that authorizes actions such as “write files to Azure Blob Storage.”
- (Often simply set to “/” to represent the entire Entra tenant.)
- Usually, the “principal” with Azure RBAC would represent a non-human.
- Protecting the human’s Azure RBAC Role Assignment with Entra Privileged Identity Management (“PIM”) is an excellent practice in this case.
- Consult with colleagues before requesting resource locks, because locking resources may impede productivity in unexpected ways .
- Also note that if you are having trouble performing actions you expected to be able to perform, given your existing Azure RBAC Role Assignments, check if existing resource locks might be the obstacle.
See “ Assign Azure roles ” on Microsoft Learn.
In a corporate environment, you might not be allowed to do it yourself. Hopefully, your help desk ticketing system has a ticket type that you can open to request that an Azure RBAC Role Assignment be created/edited/deleted on your behalf.
Best practices
Follow the principle of least privilege when requesting the creation of Azure RBAC Role Assignments when choosing all 3 components (role, target scope, and principal) .
When in doubt, create more role assignments, not broader Role Assignments.
Carefully look through Microsoft’s “built-in” Azure RBAC roles to find the least-powerful role that can perform a necessary task. For example:
- “Website Contributor” instead of the more powerful “Contributor” for deployment automations that need to deploy code onto Azure App Service, Azure Static Web Apps, Azure Functions, etc.
- “Data Factory Contributor” instead of the more powerful “Contributor” for deployment automations that need to deploy Azure Data Factory configuration from a “lower” nonproduction environment into a “higher” nonproduction or production environment.
- “Storage Blob Data Reader” instead of the more powerful “Reader” for Azure resources, deployment automations, or humans that need to read files out of Azure Blob Storage resources.
- “Storage Blob Data Contributor” instead of the more powerful “Contributor” for Azure resources, deployment automations, or humans that need to perform “write” operations against Azure Blob Storage resources.
Once an appropriately capable Azure RBAC role has been selected, it can be assigned to work against the following scopes in Azure:
- Preferred when resources are stable.
- As long as capabilities are tightly scoped – e.g. “Website Contributor” – this might provide a good balance between safety and convenience if a resource group encapsulates a single workload where appropriate target Azure resources – such as Azure Functions – are constantly being added and/or removed, and waiting for RBAC role assignment against each new function would critically impede productivity.
- With a slow rate of change, however, individual resource-by-resource assignment may still be preferred for the comfort of knowing explicitly which Azure resources are targets of which Entra identities’ capabilities, rather than guessing based on each RBAC role’s documentation.
- Questions about infosec tradeoffs between the context of “least privilege” and “ease of maintenance” / “governance?” Colleagues helping you design your solution, and staff on your company’s infosec team, are excellent resources for striking the correct balance amongst various infosec concerns.
- By default, avoid this. “Subscription” is likely far too broad for common corporate approaches to grouping Azure resources .
Once an appropriately capable RBAC role and narrow target scope has been chosen, the assignment must be attached to a specific Entra identity. Examples include:
- A single Azure resource’s System-Assigned Managed Identity (“SMI”)
- (Only when SMI is not available, and preferably using Federated Identity Credentials to log into it over OIDC if being used with Azure DevOps Pipelines or GitHub Actions code deployment automations.)
- (Either way, preferably only allowed while privileges are elevated through PIM.)
To adhere to the security principle of least privilege, more than one Azure RBAC Role Assignment may need to be created to fulfill the permissions requirements of a given workload.
For example, a workload’s design may require the creation of:
- A “ Website Contributor ” Azure RBAC Role Assignment allowing the Entra App Registration representing a code deployment automation to deploy code onto a nonproduction Azure App Service resource.
- A “ Storage Blob Data Contributor ” Azure RBAC Role Assignment allowing the SMI of a nonproduction Azure App Service resource to read and write against a nonproduction Storage Blob’s files.
- A “ Storage Blob Data Contributor ” Azure RBAC Role Assignment allowing the Entra group ID representing humans in a certain department to manually read and write a nonproduction Storage Blob’s files.
- 3 more Azure RBAC Role Assignments as listed above but scoped for production target resources .
AZ-104: How to understand role definitions in Azure
By: Author Alex Lim
Posted on February 28, 2024
Categories Exam
Home » AZ-104: How to understand role definitions in Azure
Learn how to understand role definitions in Azure and the difference between role definitions, role assignments, and security principals.
Table of Contents
Explanation
What is a role definition in Azure?
A. A collection of permissions with a name that is assignable to a user, group, or application B. The collection of users, groups, or applications that have permissions to a role C. The binding of a role to a security principal at a specific scope, to grant access
A. A collection of permissions with a name that is assignable to a user, group, or application
A role definition in Azure is a collection of permissions with a name that you can assign to a user, group, or application.
- A role definition is a collection of permissions that can be performed, such as read, write, and delete. It’s typically just called a role. Azure role-based access control (Azure RBAC) has several Azure built-in roles or you can create your own custom roles.
- The collection of users, groups, or applications that have permissions to a role is called a role assignment. A role assignment is the binding of a role to a security principal at a specific scope, to grant access. A security principal is an object that represents a user, group, service principal, or managed identity that is requesting access to Azure resources.
- Therefore, option A is the correct definition of a role definition in Azure.
B is incorrect because you can view role assignments to see the list of users, groups, or applications that have permissions to a role. C is incorrect because a role assignment is the process of binding a role to a security principal at a particular scope, for the purpose of granting access.
Microsoft Azure Administrator AZ-104 certification exam practice question and answer (Q&A) dump with detail explanation and reference available free, helpful to pass the Microsoft Azure Administrator AZ-104 exam and earn Microsoft Azure Administrator AZ-104 certification.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Assign Azure roles using the Azure portal
- 4 contributors
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope. This article describes how to assign roles using the Azure portal.
If you need to assign administrator roles in Microsoft Entra ID, see Assign Microsoft Entra roles to users .
Prerequisites
To assign Azure roles, you must have:
- Microsoft.Authorization/roleAssignments/write permissions, such as Role Based Access Control Administrator or User Access Administrator
Step 1: Identify the needed scope
When you assign roles, you must specify a scope. Scope is the set of resources the access applies to. In Azure, you can specify a scope at four levels from broad to narrow: management group , subscription, resource group , and resource. For more information, see Understand scope .
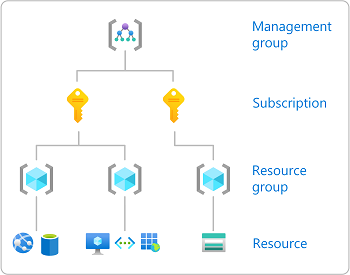
Sign in to the Azure portal .
In the Search box at the top, search for the scope you want to grant access to. For example, search for Management groups , Subscriptions , Resource groups , or a specific resource.
Click the specific resource for that scope.
The following shows an example resource group.

Step 2: Open the Add role assignment page
Access control (IAM) is the page that you typically use to assign roles to grant access to Azure resources. It's also known as identity and access management (IAM) and appears in several locations in the Azure portal.
Click Access control (IAM) .
The following shows an example of the Access control (IAM) page for a resource group.

Click the Role assignments tab to view the role assignments at this scope.
Click Add > Add role assignment .
If you don't have permissions to assign roles, the Add role assignment option will be disabled.

The Add role assignment page opens.
Step 3: Select the appropriate role
To select a role, follow these steps:
On the Role tab, select a role that you want to use.
You can search for a role by name or by description. You can also filter roles by type and category.

If you want to assign a privileged administrator role, select the Privileged administrator roles tab to select the role.
For best practices when using privileged administrator role assignments, see Best practices for Azure RBAC .

In the Details column, click View to get more details about a role.

Click Next .
Step 4: Select who needs access
To select who needs access, follow these steps:
On the Members tab, select User, group, or service principal to assign the selected role to one or more Microsoft Entra users, groups, or service principals (applications).

Click Select members .
Find and select the users, groups, or service principals.
You can type in the Select box to search the directory for display name or email address.

Click Select to add the users, groups, or service principals to the Members list.
To assign the selected role to one or more managed identities, select Managed identity .
In the Select managed identities pane, select whether the type is user-assigned managed identity or system-assigned managed identity .
Find and select the managed identities.
For system-assigned managed identities, you can select managed identities by Azure service instance.

Click Select to add the managed identities to the Members list.
In the Description box enter an optional description for this role assignment.
Later you can show this description in the role assignments list.
Step 5: (Optional) Add condition
If you selected a role that supports conditions, a Conditions tab will appear and you have the option to add a condition to your role assignment. A condition is an additional check that you can optionally add to your role assignment to provide more fine-grained access control.
The Conditions tab will look different depending on the role you selected.
Delegate condition
If you selected one of the following privileged roles, follow the steps in this section.
- Role Based Access Control Administrator
- User Access Administrator
On the Conditions tab under What user can do , select the Allow user to only assign selected roles to selected principals (fewer privileges) option.

Click Select roles and principals to add a condition that constrains the roles and principals this user can assign roles to.
Follow the steps in Delegate Azure role assignment management to others with conditions .
Storage condition
If you selected one of the following storage roles, follow the steps in this section.
- Storage Blob Data Contributor
- Storage Blob Data Owner
- Storage Blob Data Reader
- Storage Queue Data Contributor
- Storage Queue Data Message Processor
- Storage Queue Data Message Sender
- Storage Queue Data Reader
Click Add condition if you want to further refine the role assignments based on storage attributes.

Follow the steps in Add or edit Azure role assignment conditions .

Step 6: Select assignment type
If you have a Microsoft Entra ID P2 or Microsoft Entra ID Governance license, an Assignment type tab will appear for management group, subscription, and resource group scopes. Use eligible assignments to provide just-in-time access to a role. Users with eligible and/or time-bound assignments must have a valid license.
If you don't want to use the PIM functionality, select the Active assignment type and Permanent assignment duration options. These settings create a role assignment where the principal always has permissions in the role.
This capability is being deployed in stages, so it might not be available yet in your tenant or your interface might look different. For more information, see Eligible and time-bound role assignments in Azure RBAC .
On the Assignment type tab, select the Assignment type .
- Eligible - User must perform one or more actions to use the role, such as perform a multifactor authentication check, provide a business justification, or request approval from designated approvers. You can't create eligible role assignments for applications, service principals, or managed identities because they can't perform the activation steps.
- Active - User doesn't have to perform any action to use the role.

Depending on your settings, for Assignment duration , select Permanent or Time bound .
Select permanent if you want member to always be allowed to activate or use role. Select time bound to specify start and end dates. This option might be disabled if permanent assignments creation is not allowed by PIM policy.
If Time bound is selected, set Start date and time and Start date and time to specify when user is allowed to activate or use role.
It's possible to set the start date in the future. The maximum allowed eligible duration depends on your Privileged Identity Management (PIM) policy.
(Optional) Use Configure PIM Policy to configure expiration options, role activation requirements (approval, multifactor authentication, or Conditional Access authentication context), and other settings.
When you select the Update PIM policy link, a PIM page is displayed. Select Settings to configure PIM policy for for roles. For more information, see Configure Azure resource role settings in Privileged Identity Management .
Step 7: Assign role
Follow these steps:
On the Review + assign tab, review the role assignment settings.

Click Review + assign to assign the role.
After a few moments, the security principal is assigned the role at the selected scope.

If you don't see the description for the role assignment, click Edit columns to add the Description column.
Edit assignment
If you have a Microsoft Entra ID P2 or Microsoft Entra ID Governance license, you can edit your role assignment type settings. For more information, see Eligible and time-bound role assignments in Azure RBAC .
On the Access control (IAM) page, click the Role assignments tab to view the role assignments at this scope.
Find the role assignment that you want to edit.
In the State column, click the link, such as Eligible time-bound or Active permanent .
The Edit assignment pane appears where you can update the role assignment type settings. The pane might take a few moments to open.

When finished, click Save .
Your updates might take a while to be processed and reflected in the portal.
Related content
- Assign a user as an administrator of an Azure subscription
- Remove Azure role assignments
- Troubleshoot Azure RBAC
Was this page helpful?
Additional resources

- Adding or removing role assignments using Azure Portal
Go back to AZ-304 Tutorials
In this article you will learn about assigning roles using Azure portal and the process of adding and removing role assignments.
However, Azure’s role-based access control (RBAC) refers to the authorization system for managing access to Azure resources. And, to grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope.
Prerequisites
For adding or removing role assignments, you must have:
- Firstly, Microsoft.Authorization/roleAssignments/write
- Secondly, Microsoft.Authorization/roleAssignments/delete permissions, such as User Access Administrator or Owner
Access control (IAM)
Access control (IAM) is the page that is for assigning roles to grant access to Azure resources. It’s also known as identity and access management and appears in several locations in the Azure portal. There are questions for assigning roles to help in understanding about the Access control (IAM) page.
- Who needs access? This refers to a user, group, service principal, or managed identity.
- What role do they need? Permissions are grouped together into roles, so you can select from a list of several built-in roles orcan use custom roles.
- Where do they need access? This refers to the set of resources that the access applies to. However, “where” can be a management group, subscription, resource group, or a single resource such as a storage account.
Adding a role assignment
- Firstly, in the Azure portal, click All services and then select the scope that you want to grant access to.
- Secondly, click the specific resource for that scope.
- Then, Click Access control (IAM).
- Fourthly, click the Role assignments tab for viewing the role assignments at this scope.
- After that, click Add > Add role assignment. However, if you don’t have permissions to assign roles, the Add role assignment option will be disabled.
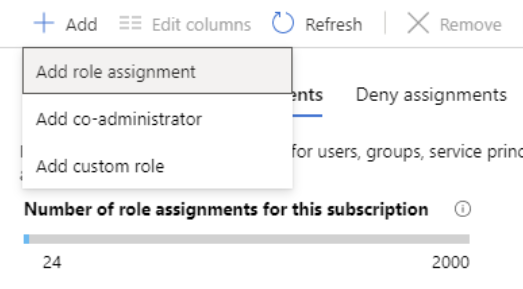
- Then, in the Role drop-down list, select a role such as Virtual Machine Contributor.
- There in the Select list, select a user, group, service principal, or managed identity. And, if you don’t see the security principal in the list, you can type in the Select box to search the directory for display names, email addresses, and object identifiers.
- Lastly, click Save to assign the role.
Assigning a user as an administrator of a subscription
For giving users the role of an administrator of an Azure subscription, first assign them the Owner role at the subscription scope. As the Owner role gives the user full access to all resources in the subscription, including the permission to grant access to others. However, these steps are the same as any other role assignment.
- Firstly, in the Azure portal, click All services and then Subscriptions.
- Then, click the subscription where you want to grant access.
- Thirdly, click Access control (IAM).
- After that, click the Role assignments tab to view the role assignments for this subscription.
- Then, click Add > Add role assignment. However, if you don’t have permissions to assign roles, the Add role assignment option will be disabled.
- And, in the Role drop-down list, select the Owner role.
- Then, in the Select list, select a user.

Adding a role assignment for a managed identity
For adding role assignments for a managed identity use the Access control (IAM) page. However, when you use the Access control (IAM) page, you start with the scope and then select the managed identity and role. In this section, you will learn about an alternate way to add role assignments for a managed identity. Using these steps, you start with the managed identity and then select the scope and role.
System-assigned managed identity
- Use these steps for assigning a role to a system-assigned managed identity by starting with the managed identity.
- Firstly, in the Azure portal, open a system-assigned managed identity. Then, in the left menu, click Identity.
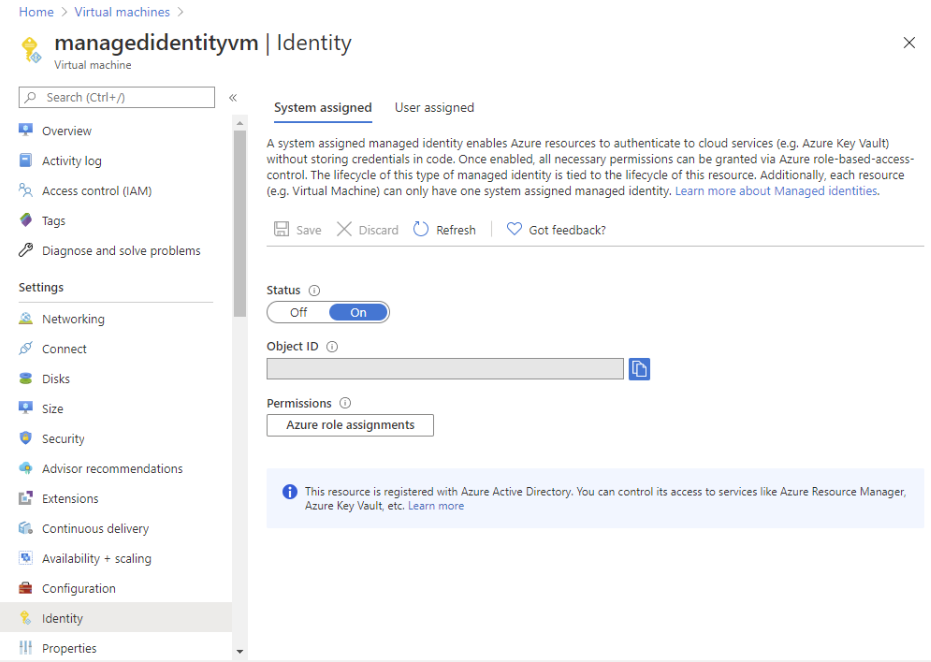
- After that, under Permissions, click Azure role assignments. However, if roles are already assigned to the selected system-assigned managed identity then you will see the list of role assignments.
- For changing the subscription, click the Subscription list. Then, click Add role assignment.
- Then, use the drop-down lists to select the set of resources that the role assignment applies to such as Subscription, Resource group, or resource. And, if you don’t have role assignment write permissions for the selected scope, an inline message will be displayed.
- After that, in the Role drop-down list, select a role such as Virtual Machine Contributor.
User-assigned managed identity
- Use these steps for assigning a role to a user-assigned managed identity by starting with the managed identity.
- Firstly, in the Azure portal, open a user-assigned managed identity. Then, in the left menu, click Identity.
- After that, under Permissions, click Azure role assignments. However, if roles are already assigned to the selected user-assigned managed identity then you will see the list of role assignments.
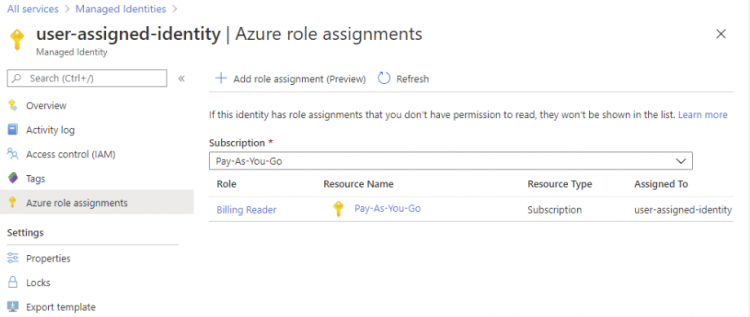
Removing a role assignment
In Azure RBAC, for removing access from an Azure resource, you first remove a role assignment. Use these steps to remove a role assignment.
- Firstly, Open Access control (IAM) at a scope, such as management group, subscription, resource group, or resource, where you want to remove access.
- Then, click the Role assignments tab to view all the role assignments for this subscription.
- After that, in the list of role assignments, add a checkmark next to the security principal with the role assignment you want to remove.
- Then, Click Remove.
- Lastly, in the remove role assignment message that appears, click Yes.
However, if you see a message that inherited role assignments cannot be removed, then you are trying to remove a role assignment at a child scope. So, you should open Access control (IAM) at the scope where the role was assigned and try again.

Reference: Microsoft Documentation
Prepare for Assured Success

COMMENTS
A role assignment's resource name must be a globally unique identifier (GUID). Role assignment resource names must be unique within the Microsoft Entra tenant, even if the scope of the role assignment is narrower.
Azure role-based access control (Azure RBAC) has several Azure built-in roles that you can assign to users, groups, service principals, and managed identities. Role assignments are the way you control access to Azure resources. If the built-in roles don't meet the specific needs of your organization, you can create your own Azure custom roles.
If you have a Microsoft Entra ID Free or Microsoft Entra ID P1 license, your Role assignments tab is similar to the following screenshot. If you have a Microsoft Entra ID P2 or Microsoft Entra ID Governance license, your Role assignments tab is similar to the following screenshot for management group, subscription, and resource group scopes.
Assigned roles are Azure AD administrator roles, for accessing Azure AD and other Microsoft 365 platforms such as Exchange and SharePoint.
An Azure RBAC Role Assignment, not to be confused with an Entra RBAC Role Assignment, grants a given identity (that is, one that exists within Microsoft Entra ID) permission to perform specific types of actions against a specific "scope" of Azure resource (s).
The collection of users, groups, or applications that have permissions to a role is called a role assignment. A role assignment is the binding of a role to a security principal at a specific scope, to grant access.
The way you control access to resources using RBAC is to create role assignments. This is a key concept to understand - it's how permissions are enforced. A role assignment consists of three elements: security principal, role definition, and scope.
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope. This article describes how to assign roles using the Azure portal.
Adding a role assignment. Firstly, in the Azure portal, click All services and then select the scope that you want to grant access to. Secondly, click the specific resource for that scope. Then, Click Access control (IAM). Fourthly, click the Role assignments tab for viewing the role assignments at this scope. After that, click Add > Add role ...
Role assignment conditions can also be used in conjuction with Custom security attributes in Azure Entra ID to make role assignment easier by reducing the number of individual role assignments.